Whether it's everyday dining, or a wine tasting for 20, matching embroidered coasters add a festive flair to any occasion. Watch this instructional embroidery video to learn how to make your own custom coasters. Wonderful gift or party decoration, so embroider away!

Whether you hang your embroidered clock in your home, or give as a gift to a friend or family member, you'll have a fun and exciting time creating this project. Any room's decor is not complete without a matching embroidered clock. Hurry, watch this instructional embroidery video - time's a wasting!

Putting wallpaper around windows can be quick and easy with these tips from Tim Carter of AsktheBuilder.com. With his advice about how to hang wallpaper around windows you'll get perfectly matching seams, and your wallpaper will be plumb each time.
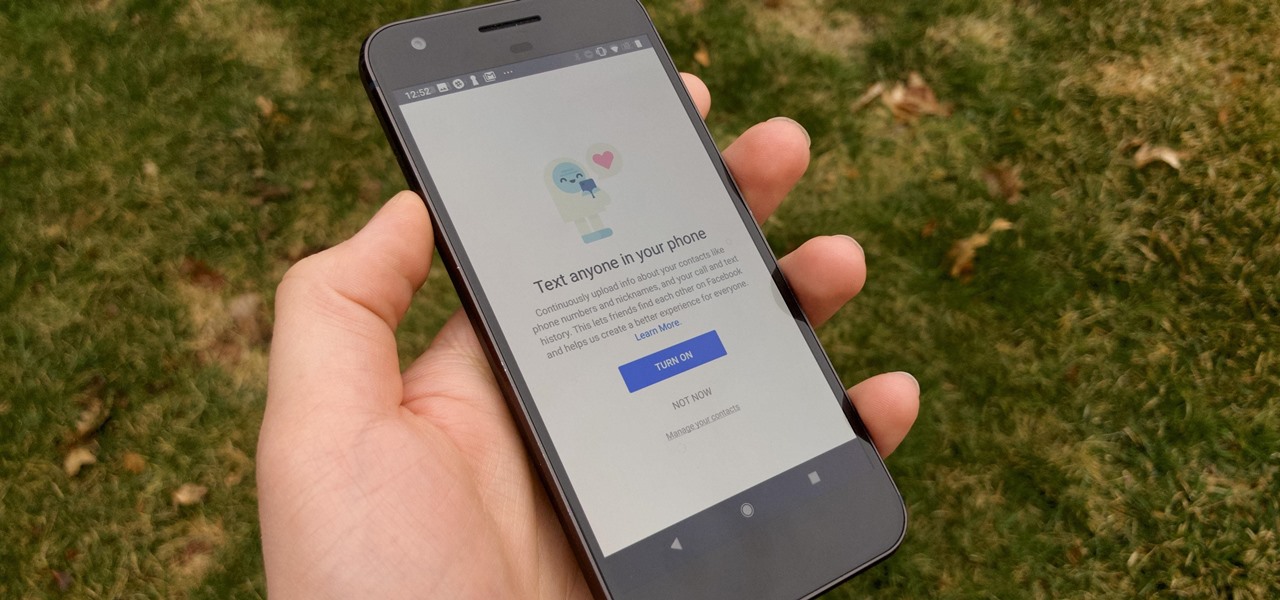
It hasn't been a great year for Facebook. Recently, Android users had to discover on their own that the company was logging their calls and texts in Messenger. However, according to Facebook, all users did approve of the data collection, and as such, all affected users can disable logging as well.
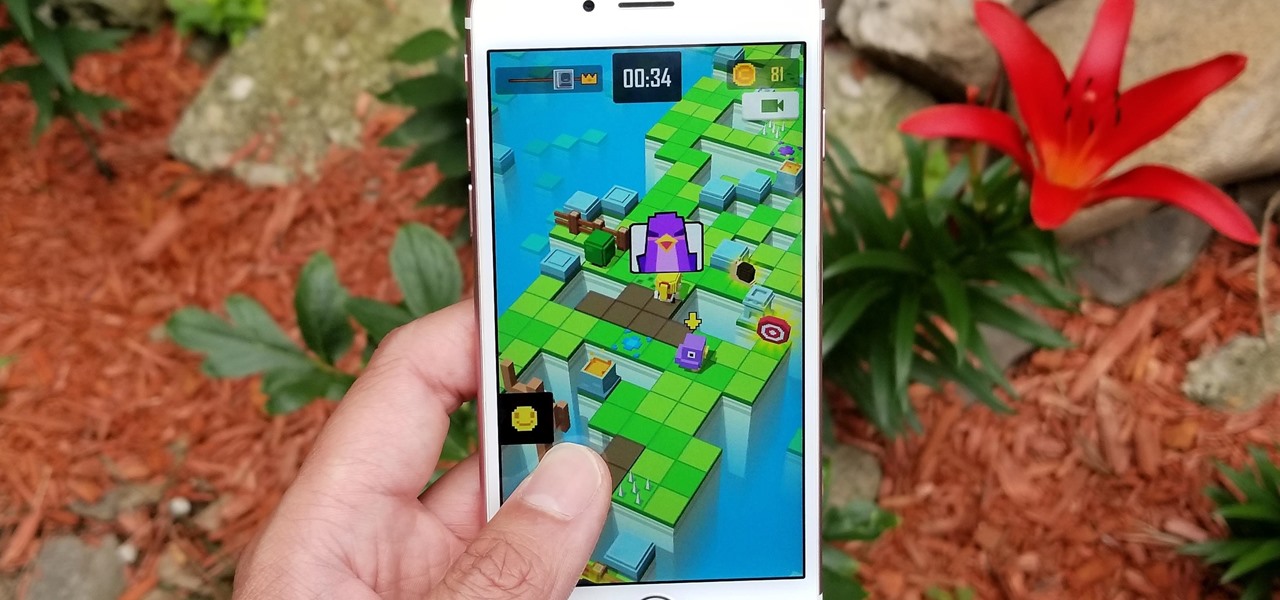
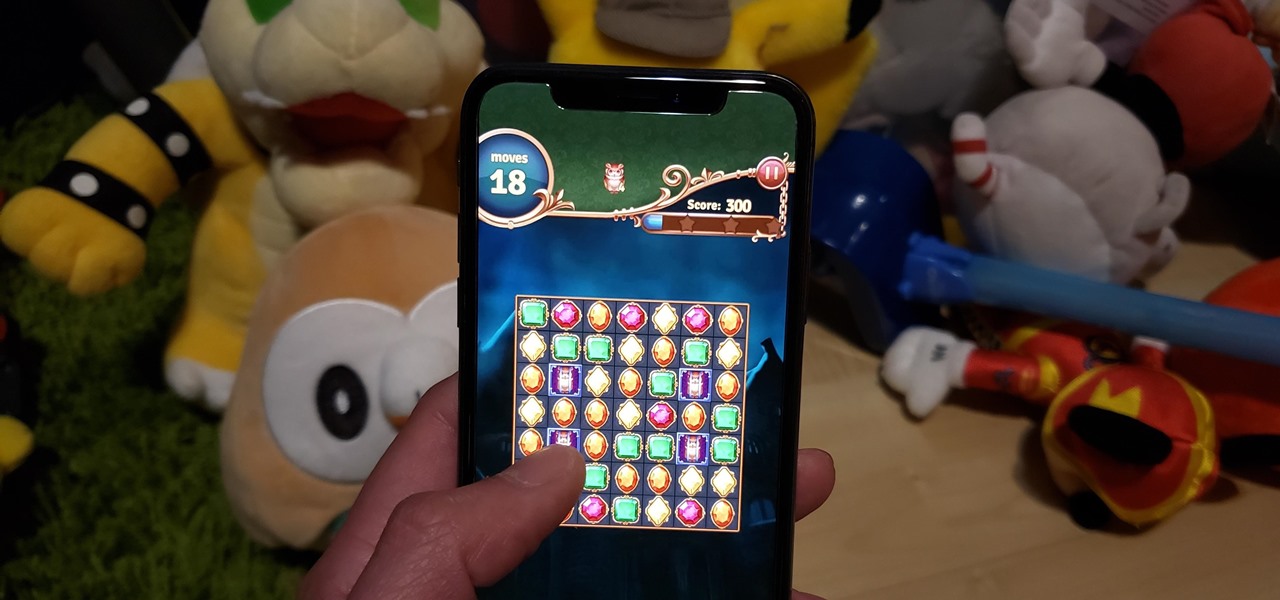
Puzzle games are a great way to kill time and exercise your brain in one fell swoop. They challenge you to think strategically and plan ahead, whether that's to create killer chain combinations for maximum points, or to plain old keep from getting killed.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

A simple video tutorial that teaches how to make these cute hemp earrings. Make a hemp bracelet and necklace to go with them for a matching set!

Okay, so you probably weren't looking at Lady Gaga's makeup so much as her dress made out of raw meat at the recent 2010 VMAs. After all, the singer had a designer stitch together cheap cuts of meat into a dress with matching boots and a hat (basically a meat flank she slapped onto her head).

Applying foundation is one of the most basic and most important makeup skills a girl needs to know, yet for many women this is the hardest step. Problems with application, such as not matching the foundation color with your skin color, not choosing the right formulation, and not applying correctly result in foundation that looks fake and caked on.

In this Home & Garden video tutorial you will learn how to install kitchen tile and apply grout. Take measurement of the area that is to be tiled. If you want to make a mosaic with the tiles, cut the tiles as per the design and layout the mosaic on a flat surface. Apply setting compound on the surface and fix the tiles as per the design. If there are diagonal cut, use a speed square to establish 45 degree angle. To bridge the thickness difference between glass and ceramic tiles, use the lamin...

Ashley Victoria teaches the secrets of using neutral shades & hot pink lips like Kim Kardashian. First use cream shadow paint in "Secretive" to apply the base on your eyelids. Apply a concealer with an angled brush right under your brow line. Apply off white color using a 239 brush all over your eyelids. With a fluffy brush take a color matching your skin tone and apply it on your crease. Apply a carbon black eyeliner to your upper lashes. Apply a light pink blush color to your face using 168...

With Jen from Beauty and Bedlam, we learn not only how to tie a scarf for women, but a variety of interesting ways in which a scarf can be worn. Matching a simple solid color scarf against a black or other solid dark top, being the easiest way to touch up an otherwise average outfit. From there, Jen teaches us a simple knot, and then more elaborate things like double or triple wrapping the scarf around the neck. For an extra touch, Jen says, we could also add a flower or other additional acce...

Hemming a pair of dress pants is no longer a mystery. Karen Schmidt demonstrates step-by-step what is needed to get professional looking results. Measure the length that you would like to trim and pin the new hemline in place. Use an iron to mark the new pant length with a crease. Then unfold and rip the seam out of the original hemline. Cut away excess fabric sew a protective zigzag seam along the trimmed fabric. Refold the new creased hemline. With a matching thread, sew a single line to ho...

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.

You've had pumpkin bags and you've had ghost bags, now you can have a Halloween colored duct tape bag to collect candy in this year. This bag is fun to use and just as much fun to make. Plus, by adding some reflective tape your bag will help keep you safe.

It doesn't have to be freezing out to wear a scarf. You can wear a lighter scarf even in the summer to achieve a fun and fashionable look. Scarves are a great and versatile accessory that will add interest to any outfit.

If you think that card counting is only a thing in the movies then think again. You too can try a couple of methods to help you count cards. Like anything, the more you work on it the better you will be.

Take a pumpkin that is round and not oblong, to make the arrangement look its best. Cut the pumpkin strait across at the top, below the stem but far enough down so you have a wide opening. Clean all the seeds out and guts in pumpkin so that the pumpkin will not decompose. Cut your floral foam piece to fit snugly inside the pumpkin so it won't move. Take it out, and soak it for a few minutes in water so it will absorb lots of water. Choose fresh flowers that would look nicely in pumpkin arrang...

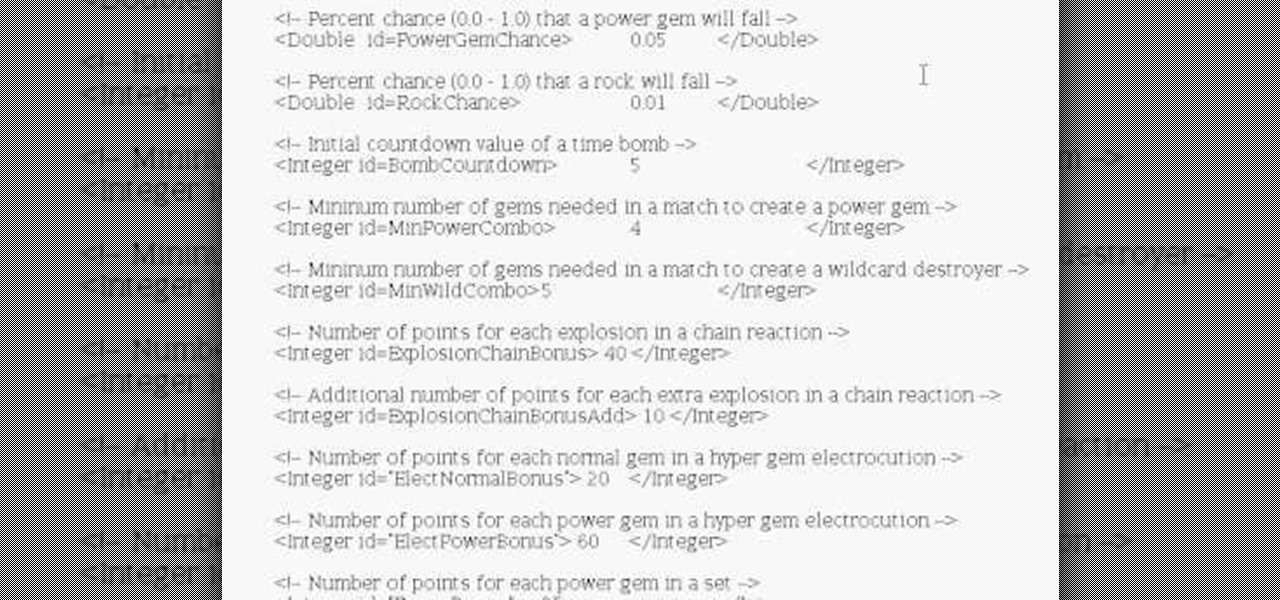
Bejeweled 2 is a famous web-based free game. Bejewel 2 Deluxe is not free and is available for PC, Xbox 360, Apple's iPod and iPhone, PlayStation 2, smartphones, and Macs. Learn how to hack Bejeweled with tricks, cheats, hacks. This video tutorial will show you how to unlock all game modes in Bejeweled 2 (12/17/08). This is a method in which it is possible to speedily obtain the game modes Hyper, Twilight, and Finity on Bejeweled 2 Deluxe without ruining your status or the high scores.

Bejeweled 2 is a famous web-based free game. Bejewel 2 Deluxe is not free and is available for PC, Xbox 360, Apple's iPod and iPhone, PlayStation 2, smartphones, and Macs. Learn how to hack Bejeweled with tricks, cheats, hacks. This video tutorial will show you how to change preference values in Bejeweled 2 to get very high scores, making a boring game even more boring!

It's been nearly two months since Samsung kicked off the official Galaxy S8 beta program for Android Oreo. The Korean manufacturer recently announced that the beta is ending on January 15, so it's time to move on to the official build. Today, an official (non-beta) build of Oreo for the S8 has leaked.

This gorgeous card is so easy to make and here I show you how, using some fabulous floral papers, however you could use any on hand, this card is a showstopper. Step 1: Items Used

This card demonstrations shows how I have used the Creative Expressions Die from the Sue Wilson Gemini range, this one is called Corvus. This is Part2 of a mini series. .

This card tutorial shows you how to make a floral lattice card that is based on a previous lattice card that was made with Poinsettias. This demonstration shows you how to use lattice die cuts with frames and making it a gorgeous floral delight. Step 1: Items Used

In this cardmaking tutorial I make a gorgeous card using cut out decoupage from a sheet of 12x12inch paper from Anna Griffins range of fabulous papers. I finish off the card with the matching leaves and paper curls. This looks like a time consuming card but apart from the cutting out of the flowers, it is quite quick & easy and all from 1 sheet of paper. Step 1: Items Used

This tutorial shows you how to create something to give as a gift or keep for yourself that can be used and cherished as a handmade keepsake. I show you how I stamp and foil the bookmark, then ink it to give it a real distressed and vintage feel, finishing off with ribbon. Step 1: Items Used

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

Trying to build a wardrobe? Get tips for mixing and matching outfits and fashions in this free video series from a professional image consultant.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Though not as flashy as other mobile gaming genres like first-person shooters, puzzle games continue to glue players to their phones. Puzzlers are perfect companions while out and about or on a commute, and they're also a great way to stimulate your brain and hand-eye coordination in a fun, relaxing way.

The Pixel 2 is a solid upgrade when compared to the 2016 model, but we've reached a point where the latest generation of a smartphone is never leaps and bounds better than the last. It's hard to justify dropping nearly a grand on a phone when it doesn't improve your situation much — especially when a few software tweaks will give you most of the upgrade for free.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A tool called ffuf comes in handy to help speed things along and fuzz for parameters, directors, and more.

Whatever it is you're into, Facebook Groups are a great way to connect with others that share your interests. And beyond matching you up with like-minded people, Groups also give you access to deals on items, help you organize play dates with families in the same area, and so much more.