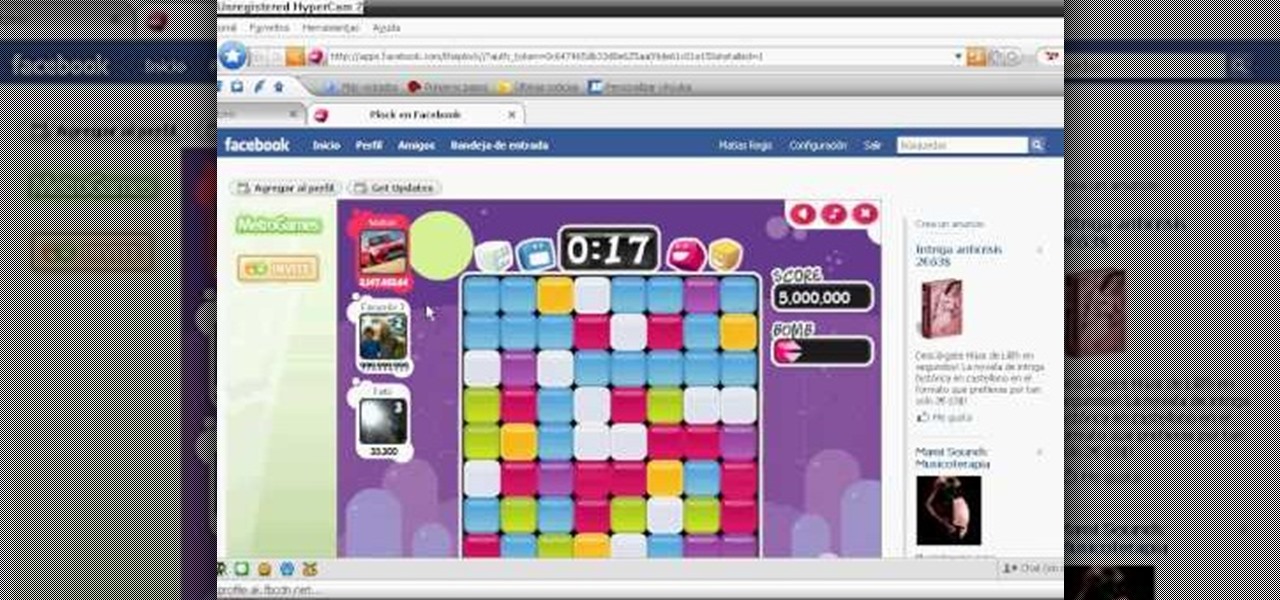
How To: Hack Plock with Cheat Engine (09/08/09)
Want to learn about hacking Plock? You've come to the right video. Using Cheat Engine to hack Plock, you can do just about anything.


Want to learn about hacking Plock? You've come to the right video. Using Cheat Engine to hack Plock, you can do just about anything.

Tired of eating a boring ceasar salad? Impress your guests with this tasty Indian dish. Check out this video for a tutorial on how to make Raita!

Watch and learn how to solve the Hanayama Cast Chain metal puzzle in this video tutorial. The Hanayama Cast Chain is a 6 out of 6 for difficulty.

Learn how to solve the Hanayama Cast Quartet metal puzzle. Hanayama cast iron puzzles are the perfect solution to being bored. This video tutorial will show you exactly how to solve this mind boggling Cast Quartet puzzle, which is rated a 6 out of 6 in difficulty by Hanayama.

Rugby is a popular sport in the United Kingdom, descending from soccer and resembling American football. Learn how to play rugby, including rules and skills, in this video rugby lesson.

The ukulele is a beautiful and unique stringed instrument that is perfect for the traveling musician because it is so portable and relatively inexpensive. The ukelele is a version of a small guitar that originated in Hawaii. In this tutorial you will learn how to play "Tricky Fingers," an old Hawaiian song in the key of F. The chord progression in this song is F E Eflat D F C F C and the bridge is A D G7 C. Once you get a hang of this beginner song you can impress your friends with this rendi...

The ukulele is a beautiful and unique stringed instrument that is perfect for the traveling musician because it is so portable and relatively inexpensive. The ukelele is a version of a small guitar that originated in Hawaii. In this tutorial you will learn how to play "C-A-T, Popoki Spells Cat," an old Hawaiian song in the key of A. The chord progression in this song is A B7 A E7 A B7 E7 A. Once you get a hang of this beginner song you can impress your friends with this rendition of "C-A-T, P...

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

Wish your violin were bigger? This brief tutorial video describes basic left-hand cello technique for violinists. The key tips are as follows: (1) reduce pronation; (2) keep your thumb to the left side of the neck; (3) watch the base of your knuckles; and (4) try to avoid curving your fingers overly. For further details watch this how-to!

Watch to learn how to play an arrangement of the Beatles song "Yesterday" in the key of F. Includes the melody, so no singing required.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Software issues occur more frequently on jailbroken iPhones, though, they're usually minor bugs that can be fixed easily with a respring. But if your device freezes up, restarting is the only way to get back to normal, which also means having to re-enable your jailbreak. There is one way, however, to respring without interacting with the touchscreen and having to re-jailbreak.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

The recent industry whispers in augmented reality are mostly about Apple and its rumored fashion-friendly smartglasses, but one company isn't waiting for the iPhone heavyweight to enter the fray.

When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general public. Since then, the mega-hit Stardew Valley has made its way to the mobile world of Android and iOS.
Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

When BlackBerry first announced the KEY2 back in June, the biggest gripe we heard was about the price. It was reasonable criticism, as BlackBerry was asking a lot of its consumers at $650. Knowing this, BlackBerry went back, made some downgrades, and cut the price, creating the KEY2 LE.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.
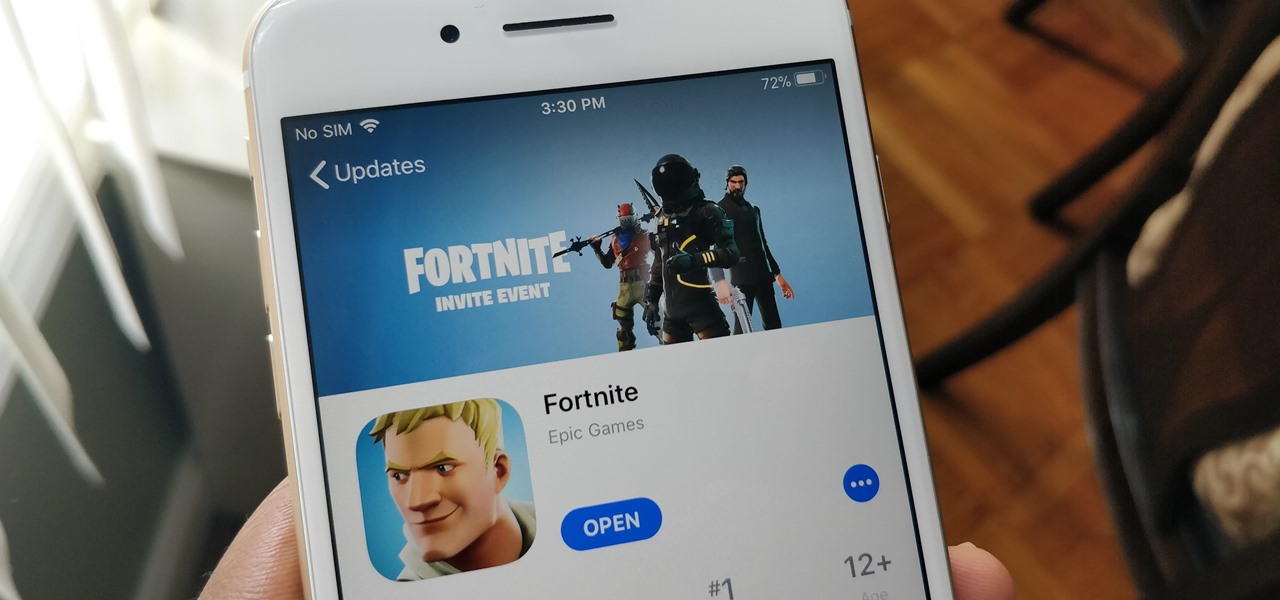
If you're a console or PC gamer, you may be quick to ignore the mobile version of Fortnite Battle Royale. The lower graphics and the switch to touchscreen controls may be enough reason to dismiss this version of the game. But don't be so quick to judge — there are actually some clear advantages to playing on mobile.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

When it comes to playing videos from your personal media library, VLC is hard to beat. But let's say you want to play videos from an Android device by connecting it to your TV — what app should you use then? VLC is still the answer, particularly once you've enabled its TV-friendly UI.

Lenovo, the company that now owns Motorola, just announced two new entries in their wildly successful midrange Moto G series. The Moto G5, and its bigger brother, the Moto G5 Plus, were both shown off in detail at Mobile World Congress 2017 in Barcelona, Spain.

The iPhone has a handy feature called AssistiveTouch that lets you quickly adjust volume, lock your screen, rotate your display, and even navigate through the phone's interface using a virtual home button. In a way, it's a lot like the on-screen navigation bar that you'll find on some Android devices, but with a lot more functionality, and bundled together in a floating bubble interface.

Students from Carnegie Mellon University's Entertainment Technology Center have been working on an augmented reality system to help teach music in a project called Music Everywhere.

Google has a habit of starting on new projects for Android, then hiding them away if they didn't quite complete them in time for a major release. We saw this with multi-window mode last year (which is now an official Nougat feature), and this year, there was the hidden night mode setting that was easily activated.

As exciting as it can be to crack open a beer, there's nothing fun about wandering around a party and asking other partygoers for a bottle opener.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.
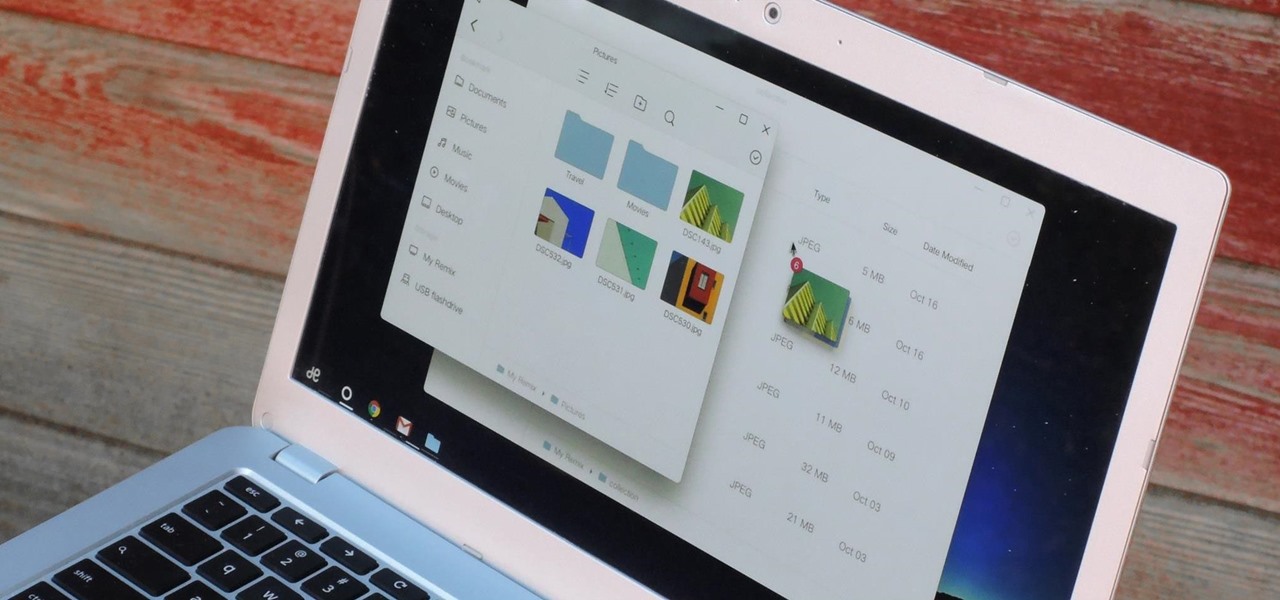
If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android with proper multitasking support and a UI optimized for the mouse and keyboard.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Samsung's Galaxy series of devices have one common design theme that ties them all together—the physical home button at the bottom of the phone. This button can wake the phone, take you to your home screen, and even scan your fingerprint to securely unlock your device.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

If you need to control a software like Ableton Live while you play guitar then you need a foot switch. In that video I will show you how it is easy to build a foot switch with an old keyboard. Then you will need to configure your software to map the keys to specifics functions like Play, Next, Pause, etc. Enjoy !

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

It's Friday night, nail polish, makeup, wine and girlfriends at the ready! But what do you wear? Here's a little number for all the brunettes out there :)

iTunes 12 was released alongside Yosemite this year, but it didn't pack quite the punch that the operating system did. Instead, iTunes received a minor facelift, with few new features and somehow lacking the intuitive feel of its predecessor. If you're not thrilled with iTunes 12, we've got a few tips to help you feel like you've got iTunes 11 back on your computer!

Losing important data is the modern-day equivalent of misplacing your wallet or keys. We have tons of vital information stored in our digital worlds, and losing any of it can be devastating. But if you've accidentally deleted something important from your Android device, there's still hope.

How to build a Hall Table from recycled wood pallets. I love pallet furniture and this wooden pallet project is no exception. It's easy to build and costs very little money. The hall stand is made entirely from old pallets and hardwood fence palings. Hall tables are very practical and are suited for those narrow areas where a normal table would be to big. My hall table, or hall stand also includes drawers which makes it a handy spot to put your car keys or mail.