
News: All New Samsung Galaxy S5 Active Leaked (Updated)
With rumors of the Active and Prime versions on the immensely popular Galaxy S5 circling the web for the past few weeks, today, we've got some clear proof of the upcoming Active variant.


With rumors of the Active and Prime versions on the immensely popular Galaxy S5 circling the web for the past few weeks, today, we've got some clear proof of the upcoming Active variant.

Let's say you're watching a video and everything's going great, but you feel the need to raise the volume a tiny bit. You hit the volume button on your Nexus 5, and all of a sudden, a giant volume slider appears that obscures half of your video for 3 seconds.

As an added functionality to the S Pen, the Pen Window enables you to create floating application windows on your Samsung Galaxy Note 3—a tool that's extremely useful when it comes to multitasking.

Ever wonder why when you defrost meat, there's all that pink liquid at the bottom of the plastic bag? That liquid is called "purge," and it's not good.

Some of my favorites hacks are the ones that speed up the process of accessing my favorite and most-used apps. So, in this softModder guide, I'll be showing you a super fast way to open those apps straight from your Samsung Galaxy Note 3's lock screen.

So, you find an interesting article online, but there’s something you don’t quite understand about it and instinct kicks in. Open new tab. Go to Google. Enter keywords. Search. Find information. Understand.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Apple has released the third beta of its iOS 7.1 software to developers, just a few weeks after their second beta introduced us to button shapes, a new calendar list view toggle, a hidden Car Display control and several other tweaks and performance improvements.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

While the new Android 4.4 KitKat is only available on one device at the moment (damn you Nexus 5), it doesn't mean that we can't enjoy some of the features it has to offer on our non-KitKat devices right now.

I'm constantly browsing the web, taking pictures, and playing games on my Samsung Galaxy Note 2, but there's one thing that I'm always doing—playing music. No matter what I'm doing on my smartphone, I'm always playing my music in the background at the same time.

If you have an iPhone, you probably already updated to iOS 6.1, which was released earlier this week. The new release came with some very subtle updates, including LTE support for more carriers, the ability to purchase movie tickets from Fandango via Siri, some security patches, and more.

For the most part, keyboard shortcuts are great. They save you some time and make it easier to do everything right from the push of a button. But like most things in life, there is always a caveat, and in this case, for me—it's a huge one.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Microsoft products, this tutorial will show you how to install the Windows 8 preview to try it out on your MacBook. First things first, you'll want to download the Release Preview on Microsoft's website (make sure to save ...

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...

Ever lock your keys in your car? In this how-to video, find out how to safely get into your car if you lock your keys inside, just using a pole and wooden wedge. Don't call a locksmith, that's going to cost you a fortune and might take a long time too. Watch this video tutorial and learn how to break into a car.

Congradulations, you've reached the point in Dragon Age 2 where you can start your first sidequest! Simply look on Gamlen's desk for the 'Bait and Switch' letter to start it. Thisvideo series will give you a full walkthrough of this important early quest that may even net you a new companion...

Are you addicted to Google Reader? If so, you may be looking for an even faster way to scroll through all of your favorite RSS feeds. Well, Matt Richardson has the solution…

The Motorola Droid is getting a little long in the tooth, but it is still a remarkably capable phone with full keyboard, which makes it almost unique among it's Android-based competition. If you've rooted your phone (good for you!) and for some reason want to go back to the stock configuration that your phone was in when you took it out of the box, this video will show you how to do it. One good reason is if you want to update your phone's firmware, which will not work if you phone is rooted ...

Fallout 3 is one of the first, if not the first, game to allow yourself to play your character when they are but a 1-year-old infant. The player is meant to be confined in a small area for this portion of the game, but need not be! This two-part video with instructions will show you how to escape the confines of your father's apartment and wander the games entire world map while still a baby! You will not be able to do many of the game's essential functions (you are a baby) but this is still ...

If you want to play 'Tell Me Why' by Neil Young on acoustic guitar you should first tune your guitar down a whole step for every string. First, the chords are in a Key of G. The chords you will play with are G, D, C, Am7, Gmaj7 and a Bm. Also on certain parts of the song you should lift up your index finger on the C. The verse will be C, D, Am7 and G. This is a boom-chucka rhythm which means you play the root note and go down up on the chord. You can throw in licks by lifting up your index fi...
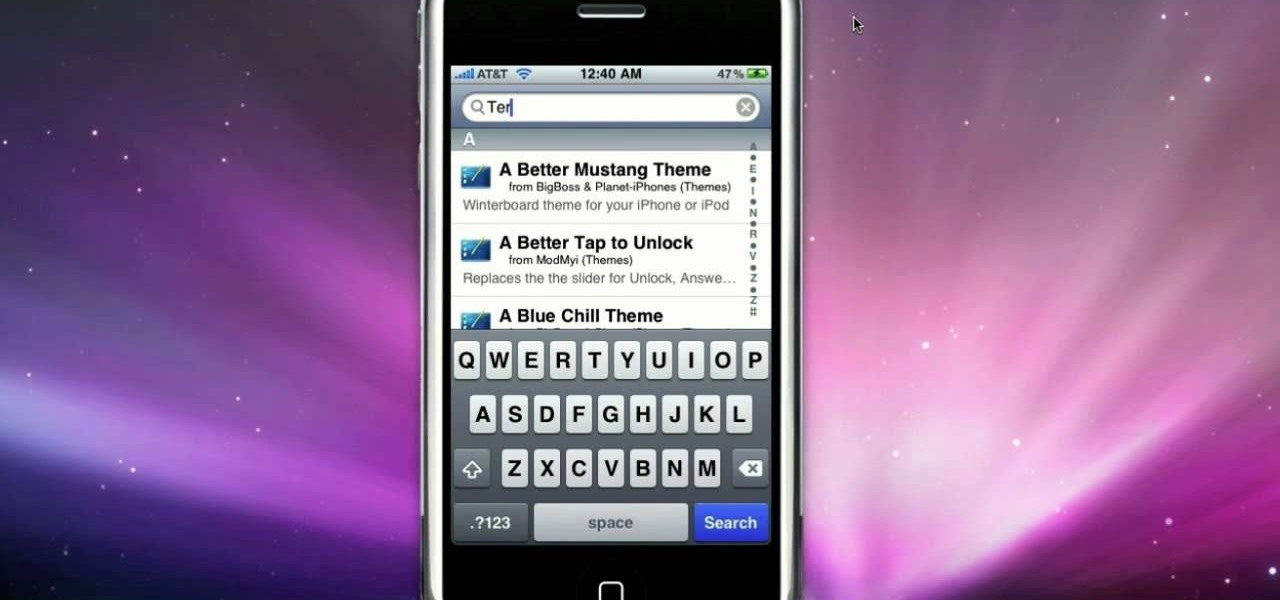
This video tutorial from iDeviceTutz shows how to change the SSH root password for iPhone or iPod.When iPhone or iPod is jailbroken it sets its password to default - alpine.Thus your device becomes vulnerable from a network attack that could steal your information or identity. So you need to change your password as soon as possible when your device is jailbroken.For this you'll need Mobile Terminal program on your device and SSH client (Cyberduck or WinSCP) on your computer.First download and...

Here is a very crafty and cute way to create a wind chime out of old salt and pepper shakers that can be found either around your house or bought at second hand stores and a small tin tray or plate to hang your shakers from. A bit of out door or water-proof glue and some colorful string or twine, scissors and a nail or awl will finish out all the supplies you need.

If you have to change a tire out on the highway make sure that you are well out of the flow of traffic. If you have materials to help people see you put them out and make sure that you only use the jack if you are on a hard flat surface. Using a jack on a soft surface such as sand can lead to the car falling off of the jack. Set your emergency brake and turn on your emergency flashers. Check the owners manual for step by step directions and safety tips for changing the tire. Take out the spar...

If you're having difficulty dispatching any of the Corrupted from 2008's Prince of Persia, this helpful battle guide from IGN might be just what you need. If forewarned is forearmed, this video tutorial will arm you to the teeth with the necessary knowledge to beat each of Ahriman's four lieutenants – the Hunter, Warrior, Alchemist & Concubine.

Watch this tutorial to learn how to build up tones with cross hatching when drawing. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Bringing your back foot up after you hit the tennis ball puts you in position to recover back to the middle of the tennis court. The key, as we explain in this video, is to get your body facing the net after you hit (similar to the ready position). This will let you side shuffle back to the middle of the tennis court.

This series of ping pong / table tennis videos demonstrate how to master the backhand drive. Jim Clegg, a Level 4 Coach with the English Table Tennis Association and Head Coach of the Preston Table Tennis Association, explains and demonstrates how you play a backhand drive correctly.

This video is for true beginners with no hip hop dance experience. People with no dance skills come to me all the time wanting to learn how to dance. In addition to classes, I teach private lessons, mostly to guys who don't want to look dumb when they go to a dance with a girl. The key is to learn how to feel the music and move to it like a hip hop dancer does.

This video is about removing sticky keys. The video begins with clicking on start in Windows XP, clicking on settings, control panel, accessibility options. In accessibility options you will see three key options which are unchecked. Click on settings of the first option which is the Use StickyKeys option and you will see five options of which the first three should be checked. In the second option which is the Use FilterKeys option ,there are five options which should be checked except for t...
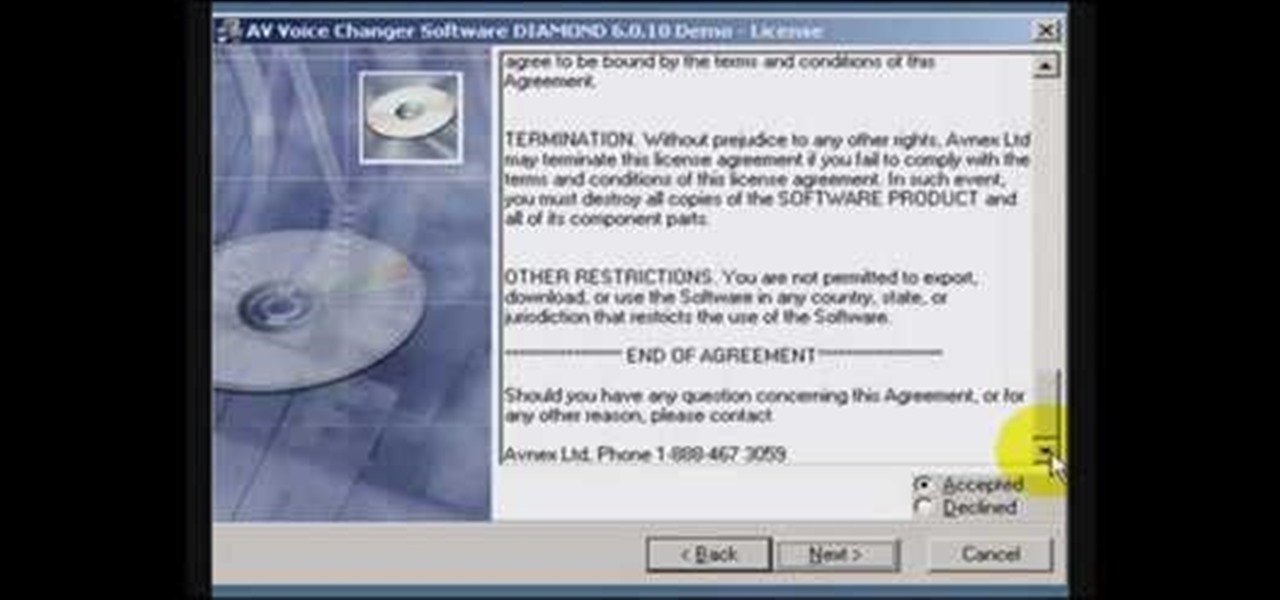
Learn how to install the voice changing software AV Voice Changer onto your desktop. The video will show you how to download VCS Diamond 6.0, how to install it, and gives you a free key so you can actually use it to start editing voices.

With tips from this video, play "Aloha Oe" in the key of G on the ukulele.

Check out this video to see how to make a box style weave lanyard key chain from start to finish.

Check out this video to see how to paint Buddha meditating in Sumi-e style of ink painting. The key three lines are, 1)shoulder outline, 2)inside line to abdomen, 3)slanted down line from abdomen.

With Adobe Photoshop on your computer, it's super easy to change or adjust the skin tone of somebody in a digital photo. The process uses some basic selection and color adjustment tools, and it's a fun way to make a friend's face nauseously green or lessen the effects of overly strong, sometimes even orange, makeup.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.