Each flavor of sake, the national spirit of Japan, comes with its own fans, not unlike whiskey aficionados here in the States. While sake is often called "rice wine," it is more akin to a malted beverage like beer.

What type of person are you in group settings? Are you the social butterfly, eager to get to know everyone and interested in the people more than the setting? Or are you a wallflower, afraid to catch anyone's eye out of fear?

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.

Welcome back, my nascent hackers!

We've all heard the cliches: always look at the glass as half full; a smile can change your entire day; and there's always a silver lining.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

On-screen navigation buttons offer many distinct advantages over physical buttons—they can change orientation along with your device, they're capable of visually morphing to indicate secondary functionality, and the user experience is more consistent when buttons and app elements require the same amount of force to press. Add to that the fact that they're far less likely to fail and can be themed or even switched out altogether, and it's hard to come up with an argument in favor of physical b...

Many Nexus 6 owners, myself included, have already started to experience the dreaded burn-in issues that often come with AMOLED display technology. These displays are different than your typical LCD screen in that each pixel emits its own light instead of using a backlight, so this leaves AMOLED screens more susceptible to issues with dim or unresponsive pixels.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Finding the motivation to make a change can be tricky. It's difficult to resist the urge to procrastinate, or even give up when goals seem distant and difficult. If you wish you could stick to your New Year's resolutions, or maybe even just commit to pursuing smaller goals, you might want to consider making a small change to start: just create a new password.

Our workdays are typically filled with one thought: get as much completed as possible. Whether you face an inbox filled with tasks or just a project or two, both our bosses and our inner workhorses encourage us to knock out as many tasks as we can each day. But is being super-productive the best course of action for our minds and our employers?

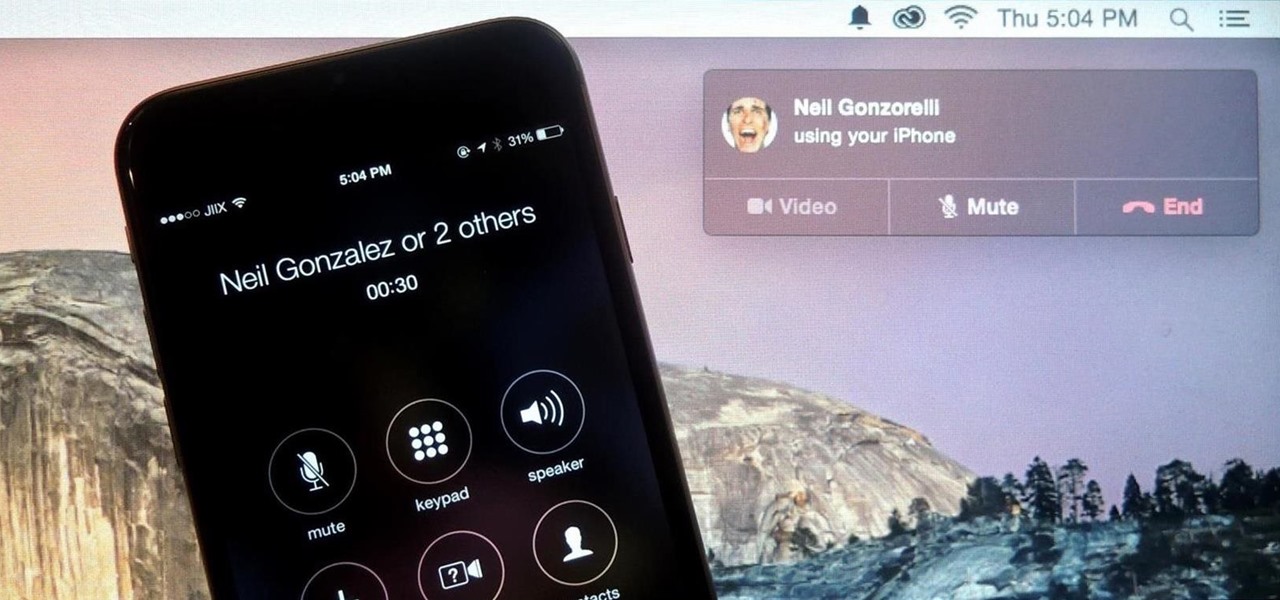
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

The importance of body language is stressed from an early age: watch those around you, and you'll know what they're thinking. While you might be skilled at deciphering the messages of crossed arms, slouched sitting, eye movements, and hand gestures, the key to understanding those around you is a little less obvious.

Whenever a new Android device is realized, the first thing I figure out how to do is to get it root access. Generally speaking, rooting has never been easier, with many one-touch methods like Stump and Towelroot available. But as manufacturers and carriers increase security with each new product, there is one tried-and-true root method that continues to work on most Samsung devices—Chainfire's CF Auto Root.

Ah, the age-old problem of sharing pictures with friends and family. Ten years ago, the best method available to us was passing around duplicate photos printed out at the local drug store. As easy as smartphones have made this act, you'd think we'd be satisfied by now.

As soon as third-party keyboard compatibility was announced for iOS 8, Apple loyalists and the newly curious both looked to the popular Android third-party keyboard developer, SwiftKey, to see if they'd be offering their services to iOS.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Many game developers have finally realized that in order for their games to be successful, they have to support Android. To really win Android users over, they should also accommodate us hardcore gamers who have OTG cables with the ability to hook up controllers to our devices.

With a 13 megapixel camera that can record in full 4K, there's a lot to love about the Samsung Galaxy Note 3 from a photographer's perspective. The image quality in my photos and videos are top-notch and nothing to complain about, but as with all things tech, things could always get better.

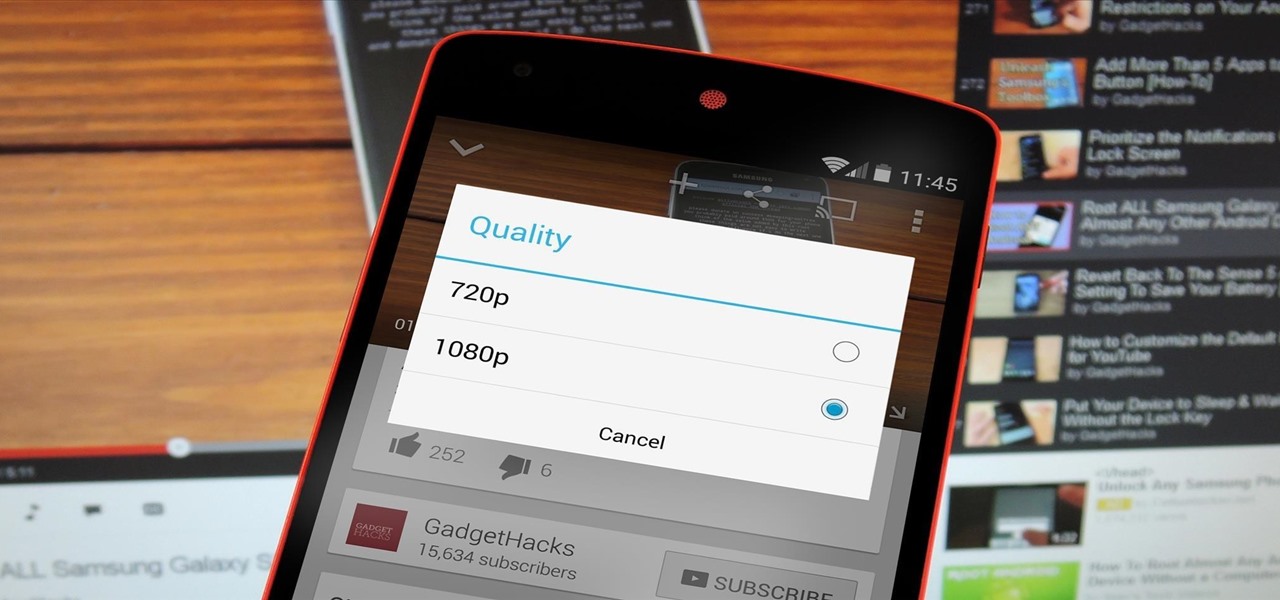
The Nexus 5 and Nexus 7 (2013 edition) boast beautiful 1080p screens that are capable of displaying images and videos in ultra-sharp high definition. But for some strange reason, the YouTube app only allows for streaming of 720p content on these devices. It's not a limitation of YouTube for Android, since other devices support 1080p playback out of the box, and some, like the LG G3, even support higher resolutions.

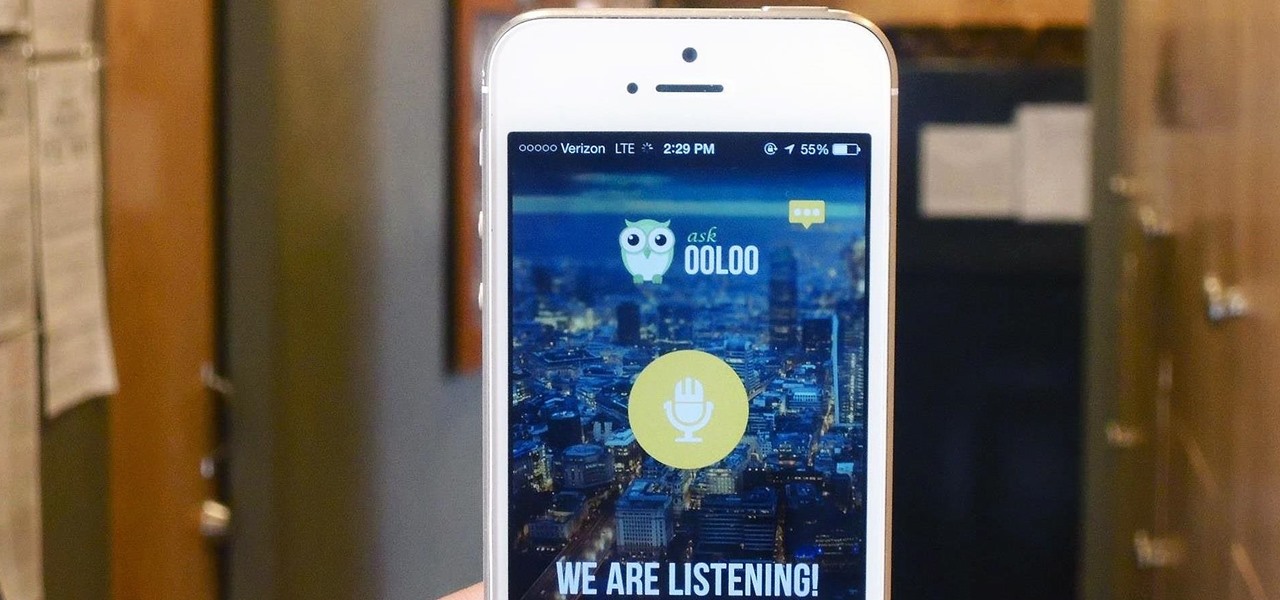
Apple has Siri, Google has its Now service, and Microsoft has Cortana. All of these voice-activated services can bring you information quickly and easily without having to type anything into your smartphone. Speak and within seconds you're provided with either an answer or somewhere you can find it.

Baking soda is a powdery miracle. Not only is it the secret ingredient to making mashed potatoes fluffy, it can help you make authentic-tasting soft pretzels at home and caramelize onions in half the time. It's actually got lots of surprising uses you might not know about, and one of them is that a pinch or two can correct sour and bitter tastes in your food.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

Unless you've been living under a rock for the past few weeks, you're probably well aware that the Android world has been buzzing with excitement over the recently debuted Android L preview build that was released for the Nexus 5 and Nexus 7 at Google's I/O conference.

Due to its constant delays and lack of public invites, the OnePlus One is the equivalent of a unicorn in the Android community. I was lucky enough to win an invite in the OnePlus Storm of Invites promotion and have loved every minute with my new Nexus Killer since receiving it.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

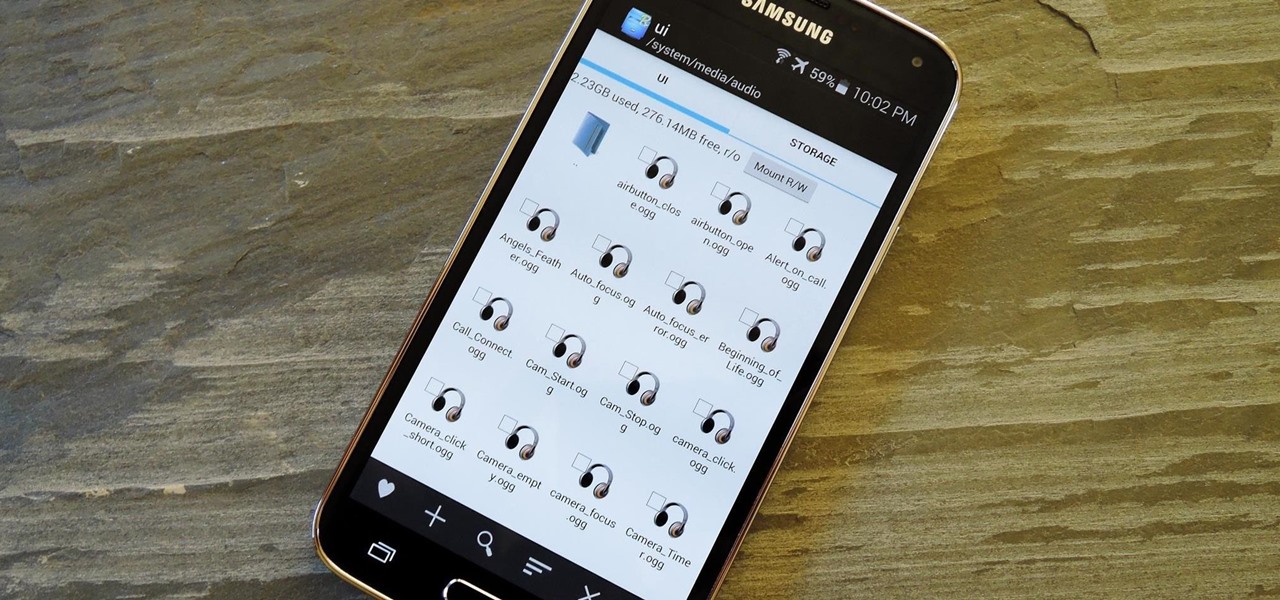
I have the AT&T version of the Galaxy S5, so every time I start my phone I get the pleasure of hearing AT&T's lovely jingle. Actually, that's sarcasm—I absolutely abhor this sound. I haven't had the chance to play around with a Sprint, T-Mobile, or Verizon variants of this phone, but I imagine they have some sort of equally annoying boot sound.

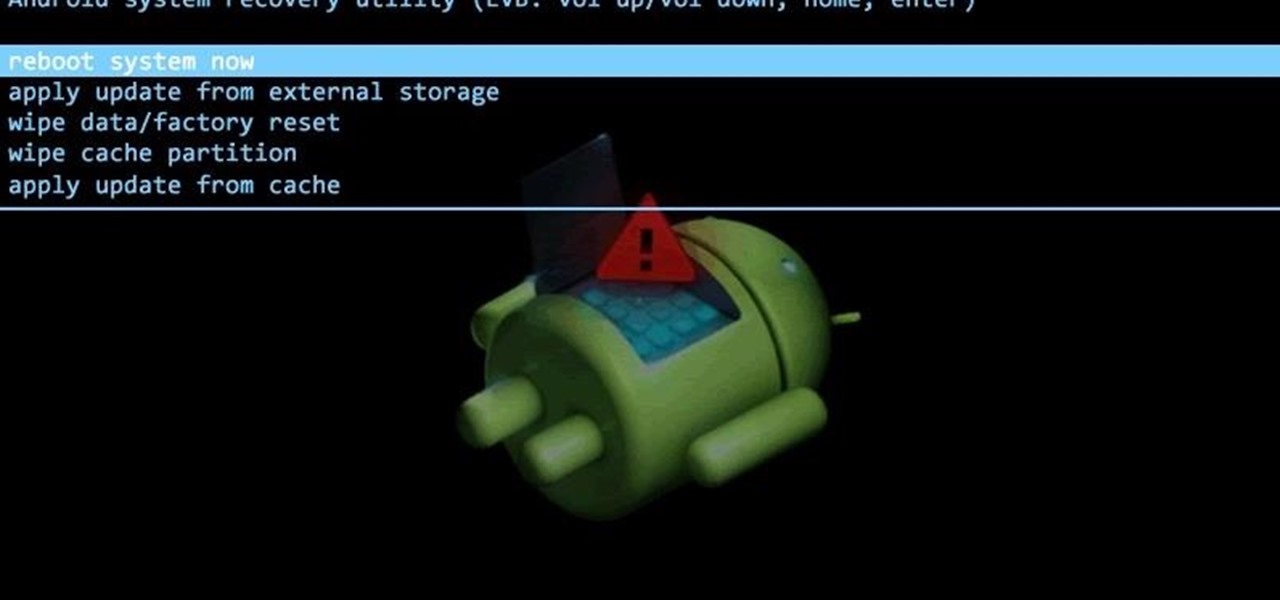
It is really quite easy to flash a custom recovery to your Nexus, and there are many excellent tutorials on how to do so (see the How-To below): The Easiest Way to Install a Custom Recovery on Your Nexus 7 Tablet « Nexus 7.

Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

If you have a hard time remembering what you've just read on your iPad or Kindle, try changing the font next time. The typeface you use to read books, newspapers, and online articles is either hurting or helping your memory, and you'll be surprised which ones are killing your brain cells.

While their merger with Microsoft has lead to a seemingly complete halt of new device development, some Nokia employees are still hard at work to bring new software to the table.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

When we look back on it, 2014 may be remembered as the Summer of Android Wear. With two new flagship smartwatches due out soon, Google's been readying its mobile OS for the wearables sector.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Someone does't really like you. I don't know who or where they are, but they exist. If you want to change that, simply ask them to do you a favor.

The way you use your camera just got a bit more interesting. Phogy, a brand new camera app for Android, allows you to capture pictures with a 3D effect that comes alive when shifting your phone from side to side.

Apple is very tight lipped about their products, and their iPhone is certainly no exception, but when products depend on global manufacturing, it's nearly impossible to keep good secrets contained.

As fellow softModders, I'm sure you strive to find any and every way to make your phone unique. Wallpapers and icon packs are great to get started, but to really stand out from the rest, try changing your HTC One's boot animation.

I don't like a lot of app icons on my home screen. It makes everything on my Nexus 7 feel dense and congested. As a minimalist, I like a simple and well-organized home screen, which is why I regularly utilize my app drawer to launch apps.