
News: Google Assistant's 'April Foolproof' Command Will Help You Avoid Getting Pranked
Google Assistant is a handy little feature at most of the time, but it's upping the ante in honor of April Fools' Day this year.


Google Assistant is a handy little feature at most of the time, but it's upping the ante in honor of April Fools' Day this year.

Experts from the World Health Organization just expressed concern for the rising number of measles outbreaks across Europe. Despite a perfectly capable existing vaccine, "immunization coverage has dropped below the necessary threshold of 95%," causing the measles to spread throughout the European region.

In case we haven't beaten the '90s revival to death enough, now Nokia is coming back to the US market. The three Android midrange devices that made their debut at Mobile World Congress last month are set for a global release, meaning they will also make their way stateside.

The rumors have been confirmed by Samsung themselves: Samsung has developed a virtual assistant of their own, named Bixby.

Both the US and UK seem to be leaning toward requiring level 3 autonomous cars to train their "eyes" not just on the outside world, but even on the driver itself.
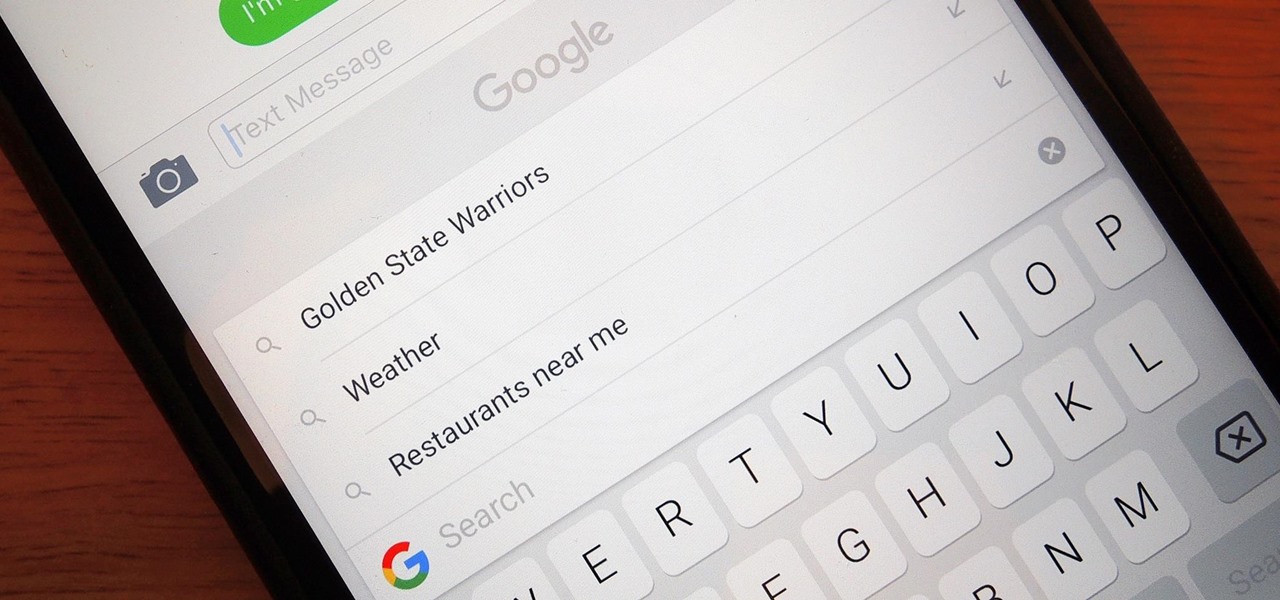
Google just made searching the web on your iPhone a whole lot easier with its new GBoard keyboard for iOS. It has a built-in Google icon so that you can search directly from whatever app you're in, making it a cinch to add images, GIFs, directions, videos, and more.

Welcome back my friends !! Today we'll go through the second part of this C# series
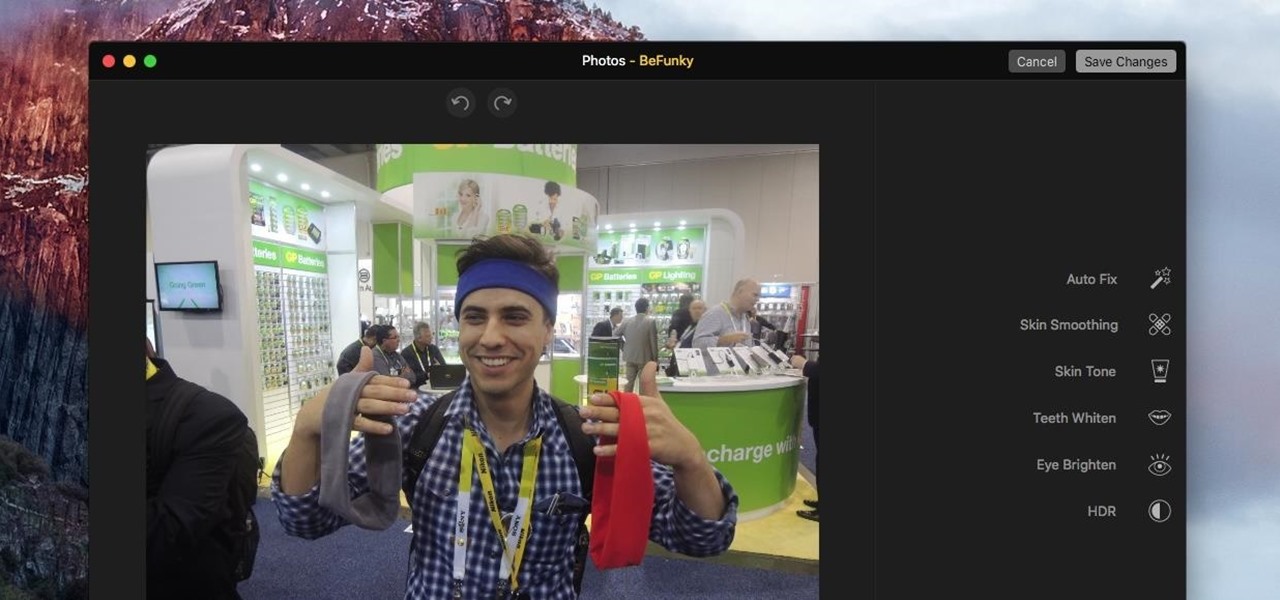
For minor adjustments and color-correction, the Photos app is extremely useful, but its capabilities are limited to just the basics. Now, with Mac OS X El Capitan, Apple is opening the door for third-party extensions, meaning we can utilize additional, unique tools when editing pictures in Photos.

Whether it's delivery drones or getting the U.S. Postal Service to ship packages on Sundays, Amazon continues to remain innovative and ahead of the game, as further evidenced with their mobile app, Amazon Underground.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.
Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.
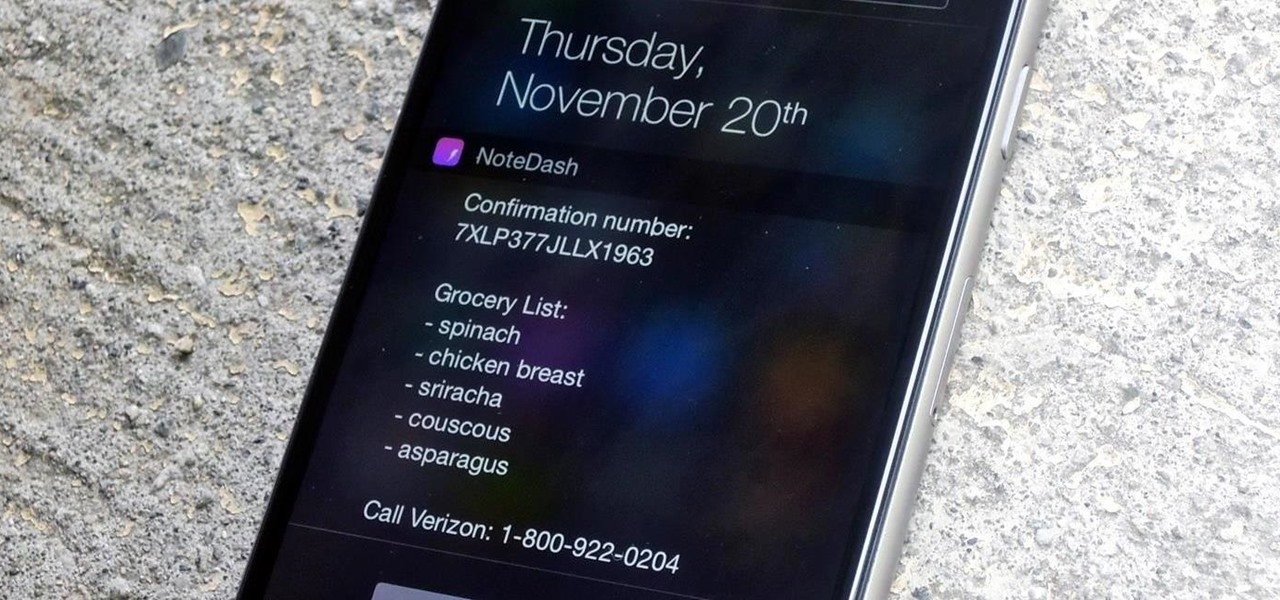
Confirmation numbers, grocery lists, addresses, and phone numbers are all things we need to quickly jot down on our phones, but the thing is, they're never extremely easy to access later. You have to figure out which app you wrote them in, meaning lots of needless searching and scrolling. Even if you use a dedicated note-taking app, those extra steps of actually opening the app to find a UPS tracking number can be an unnecessary pain.

The OnePlus One comes with CyanogenMod 11S built in, but there are certainly some traditional CyanogenMod features missing from this version. One of the most obvious missing ingredients is the lack of a native SuperUser app, most likely to prevent inexperienced users from causing unintentional damage to their device's software.
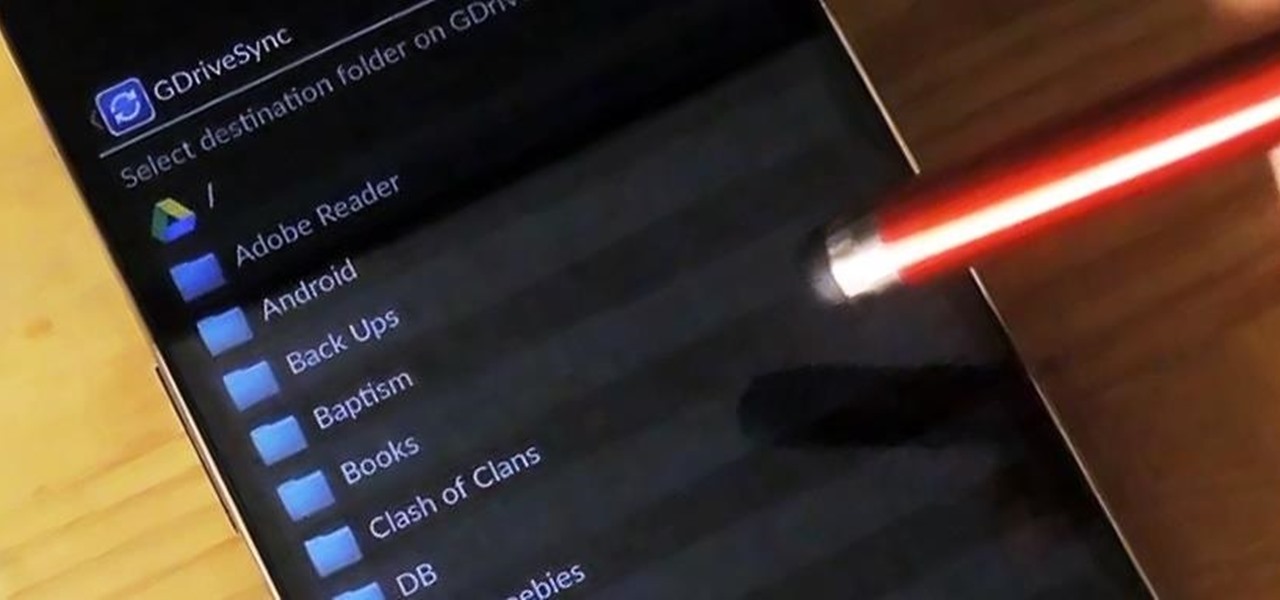
Google makes backing up your contacts, messages, and Wi-Fi passwords extremely easy, but leaves you out in the cold when it comes the data on your internal storage. With most Android devices now lacking SD card support, when you unlock your bootloader or do a factory reset, you're stuck having to back up everything to your computer beforehand.

My OnePlus One easily gets over a day of battery life without a problem, but when I try to charge it, it seems to take just as long. For some reason, no matter what charger you plug your OPO into, it never gets more than USB-level power, meaning that charging times are more than double when compared to traditional AC-charging.

Personally, I know life would be a lot easier if the people in it could just read my mind. Since that technology is currently unavailable, it's comforting to know that your air conditioner can be your personal telepathist with Sensibo.

With Google's latest version of their mobile OS, Android L, the most notable aesthetic difference is the newly introduced Material Design concept that will soon be ever-present through the interface. The objective of this bold design is to create "hierarchy, meaning, and focus," as described by Google, and the deliberate choices of color and white space "to create immersion and clarity."

Greetings, my friend. Welcome to Null Byte. I am Dr. Crashdump. Linux will be talked about a lot in Null Byte. It's used in most tutorials on this site, actually. You should learn how to use Linux as soon as possible, but where do you start? No worries. Let's figure that out.
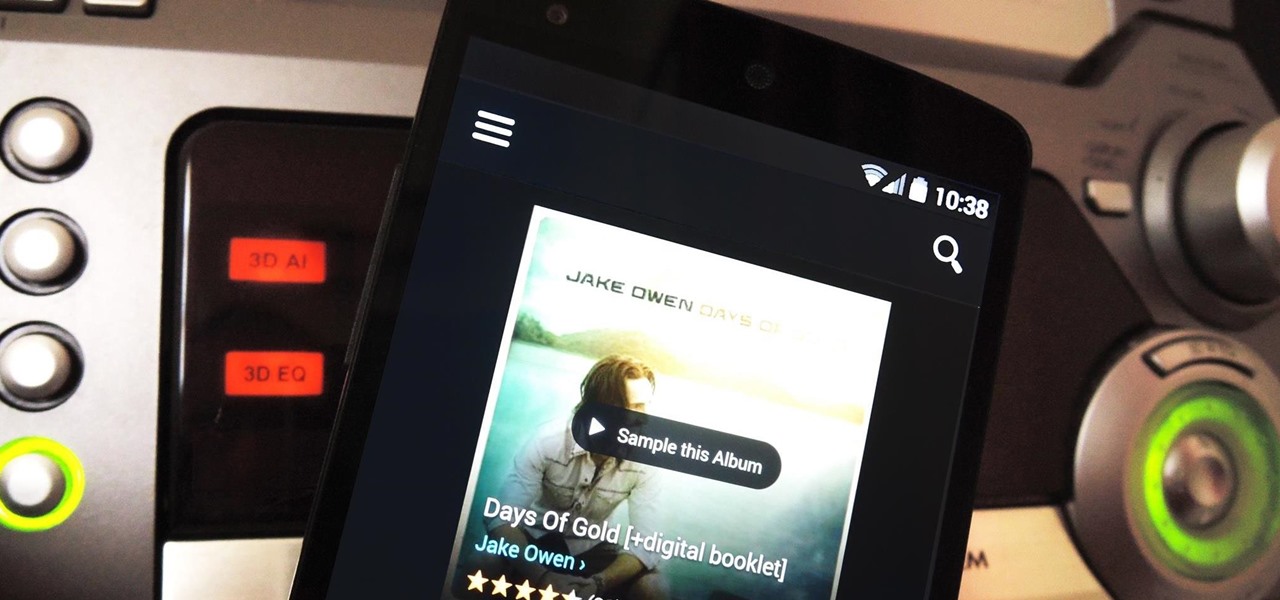
For $100 each year (unless you used Faisal's workaround to save yourself twenty bucks), Amazon Prime membership gives you access to all the best that Amazon has to offer. From free 2-day shipping to Prime Instant Video, there's a lot to like about the service.

Just short of a week after its release, the new HTC One has been rooted thanks to Android devs beaups and jcase, the same guys that brought us S-OFF for the original HTC One (M7).

The new Xbox One has yet to implement compatibility with third-party headsets, meaning for now, you're stuck using one of the official Xbox One headsets available. However, many have run into problems with the included wired headsets, and would much rather use the expensive third-party ones they already have for the Xbox 360.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

Hey dolls! I love my new infrared hair straightening iron by MUK. I thought it was a gimmick but really, the technology makes sense. I love that you can adjust the temperature unlike GHD straighteners. So if you if have fine hair you can turn it down and if you have thick crazy hair like me you can turn the bad boy up!
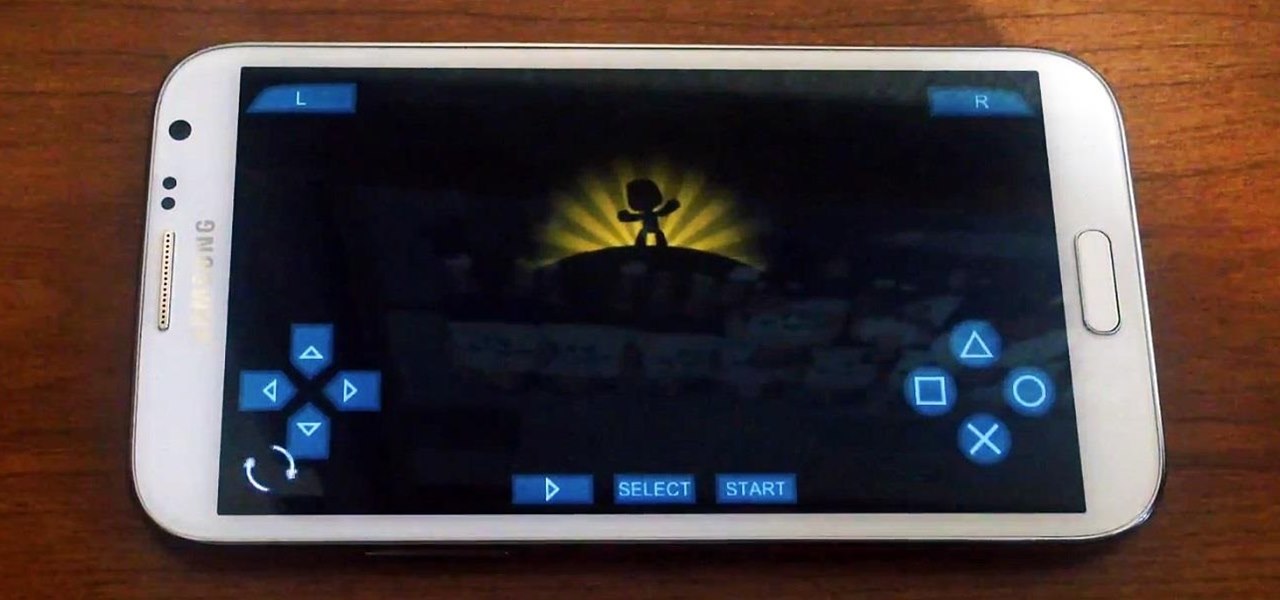
If smartphone video games have a weakness, it's probably their inability to emulate the riveting and immersive experience that consoles offer.

Last week, Instagram stopped supporting media Cards on Twitter, meaning that in order to view a full photo shared in a tweet, you have to click through to Instagram rather than seeing it on your Twitter feed. Otherwise, the photo will appear to be cropped.

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...

Most of us have traded our desktop systems for laptops, tablets, and mobile devices, meaning there's a lot of outdated hardware sitting in attics. Want to give your old computer a new purpose? Matthew Chappee turned his iMac G4 into an HDTV using the guide by Dremel Junkie. One thing to note before you take on this project yourself is that if you want to use it to watch cable, you'll need a converter box to get around the MPAA's HDCP restriction. But, a converter box is considerably less expe...

André Broessel of rawlemon has developed a solar energy generator that can use both sun and moonlight to create usable power. Oh... and it's gorgeous. The device is essentially a huge glass sphere filled with water that uses a ball lens to refract light in a way that increases energy efficiency by 35 percent. It's completely weatherproof and has an optical tracking device, meaning that it can be incorporated into architecture. Here's a concept design of how it could be used to power buildings...

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

"Unfortunately, no one can be told what the matrix is, you have to see it for yourself." That's the line just before Morpheus gives Thomas Anderson (aka Neo) the red pill, finally opening his eyes to the tapestry of code that has veiled his eyes for his entire life.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

There are a lot of Android phones out there, and chances are that someone in your life is looking for one this holiday season. Well, there also happens to be a lot of Black Friday deals on Android phones this year. So we've rounded up the best deals taking place on Black Friday weekend to help you save big.

Codenamed "Nougat" after the sugary stuff that fills your Snickers bar, Android 7.0 is living up to its name with tons of sweet features. There's almost too many changes over Marshmallow to cover in one go, with new functionality ranging from a revamped Doze Mode for battery saving, to split-screen apps, and even an easier update process. All told, the Nougat update has a lot in store for your phone or tablet.