d-CON is here to help identify and remedy rodent problems in your home. Watch this video tutorial on how to use d-CON Ready Mixed Baitbits to kill mice in the home. Signs of a mouse in the home include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your bathroom. Watch this video tutorial on how to use d-CON Bait Wedges to kill mice in the bathroom. Signs of a mouse in the bathroom include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your living room. Watch this video tutorial on how to use d-CON No View No Touch Traps to kill mice in the living room. Signs of a mouse in the living room include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your kitchen. Watch this video tutorial on how to use d-CON Bait Paste Pouches to kill mice in the kitchen. Signs of a mouse in the kitchen include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.
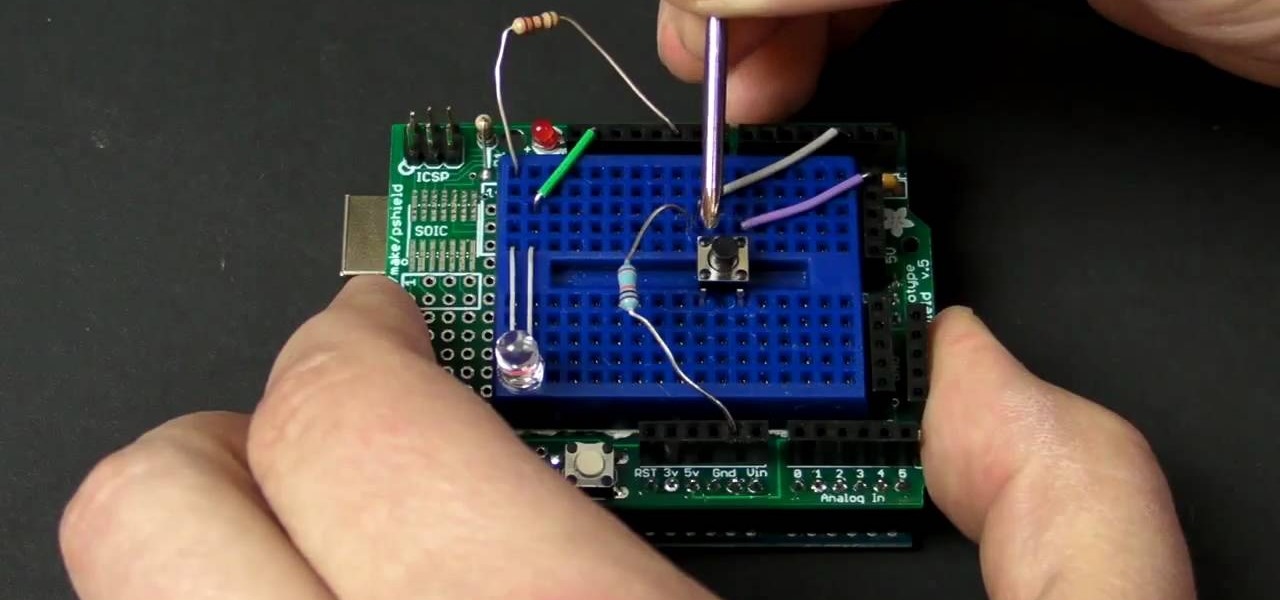
See how to a a button with Arduino with MAKE Magazine! This is a video tutorial on a favorite little micro-controller, the Arduino. This is a really informal how-to, and is meant to show you just how fast and easy it is to work with the Arduino.

See how to control an LED with Arduino with MAKE Magazine! This is a video tutorial on a favorite little micro-controller, the Arduino. This is a really informal how-to, and is meant to show you just how fast and easy it is to work with the Arduino.

In this video tutorial, you'll learn how to change a damaged belt or brushbar on the Vax V-026 Rapide Deluxe carpet washer.

In this video tutorial, you'll learn how to change a damaged belt/brushbar on the V-006 Turboforce vacuum cleaner

In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt explains how he teaches the BEEF method of shooting. The work BEEF is an acronym for a ball shooting concept in basketball. The B stand for balance, the E for eyes, the second E for elbows, and the F for follow-through. To have good balance it is important to have you feet about shoulder width apart. Your eyes should always be focused on a target, and your elbows should be in line. Finally follow through means it sh...

Willow can be woven into many shapes or to form a living boundary fence. The reason they are called living is because some of the stems used to create the structure root in the soil and grow to form new shoots. This does mean that annual trimming is needed to maintain the shape, but at the same time it adds interest to the garden. Creating a living structure is very simple to do and all you need is a few pruning tools and a bundle of willow sticks in various thicknesses. With this tutorial yo...

Check out this how to video on carnival games. Some of the local carnies offer tips on how to win the games along the midway at the Lorain County Fair. That doesn't mean you have to go to Lorain though, this applies to all carnival games, including One In Wins, Bust One, The Guesser, 100 Shots, Skee-Ball, and much, mcuh more. Don't know these games? I'm sure you do, just watch and learn, so you can fill your house with large, cuddly, stuffed animals.

You have a webcam, right? Nowadays, who doesn't? But just because you all have webcams doesn't mean you're using them the same way. And a great way to take full advantage of your peripheral or built-in webcam is by turning it into a security camera. This video will show you how to turn it into a security cam by accessing the video feed remotely over the internet. And it's a really simple solution—you just need to sign up for a USTREAM account, which allows you to stream webcam footage live!

Learn how to play "Poison Oak" by Bright Eyes on the acoustic guitar. VERSE: Read from left to right

Your gynecologist has recommended that you undergo surgery to remove vaginal fibroids. But what does that actually mean?

In this video, Matt explores a gambit line for Black in the Four Knight's English: 1.c4 e5 2.Nc3 Nf6 3.Nf3 Nc6 4.g3 Nd4!?

For the average consumer, augmented reality is a fun way of dressing up photos and videos for social media. However, AR is also gaining momentum as a medium for storytelling, particularly in sharing powerful messages.

If you're one of the many professionals transitioning to working from home amidst the current pandemic, there's a good chance you're now realizing how far behind your at-home setup is compared to what you had at the office.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

The legal drama surrounding Chinese startup Nreal and Magic Leap continues, and now we finally have an update.

After months of waiting, the iPhone 11 is here. At an event in Cupertino, Apple unveiled the iPhone 11, 11 Pro and 11 Pro max. You probably have a lot of questions after reviewing the specs sheet, including wanting to know more about the IP68 rating that all three phones have. We're here to clarify.

For years, Samsung has been behind the curve when it comes to fast charging. Up to the Galaxy S10, most of their phones used the very slow Adaptive Fast Charging system. Whether it was the Galaxy Note 7 fiasco or some other reason, Samsung has been reluctant to push the charging envelope. Until now.

The ability to shift between virtual reality and augmented reality seamlessly on one device is a dream of many AR fanatics, but the execution is usually fairly buggy or underwhelming.

WhatsApp, like other popular messengers on iOS and Android, shows when recipients have read your sent messages with a blue double check mark indicator. On the flip side, for those of you who are bad at replying promptly or don't feel like replying at all, you can disable "read receipts" so the senders won't know when or if you even read their messages.

Sileo is an ideal marketplace for developers to showcase apps, tweaks, and themes that Apple would never allow in the App Store. While a majority of these packages are free to try out, there are jailbreak apps that cost money for your iPhone. But actually paying for mods can be a bit tricky.

In a leaked company memo, Snap CEO (and NR30 member) Evan Spiegel has made it clear that the future of the company lies not only augmented reality but also hardware that enables those AR experiences.

The S9 and S9+ are both fantastic phones. However, there's no getting around the fact that the S9+ has its advantages. In fact, it's an objectively better smartphone than its smaller counterpart — Samsung has given the S9+ features not found in the S9, meaning you'll be missing out if you choose the 5.8" Galaxy over the 6.2".

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

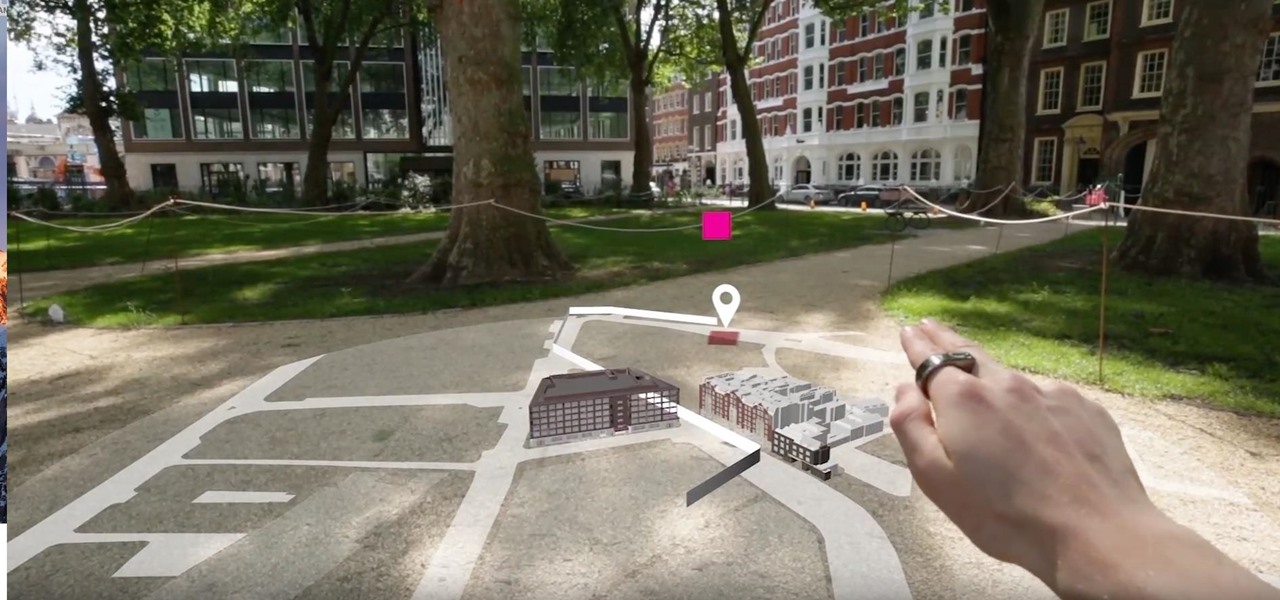
Forget what you know about controlling augmented reality experiences. "Scroll" lets you interact with augmented reality using a much more subtle approach: A ring.

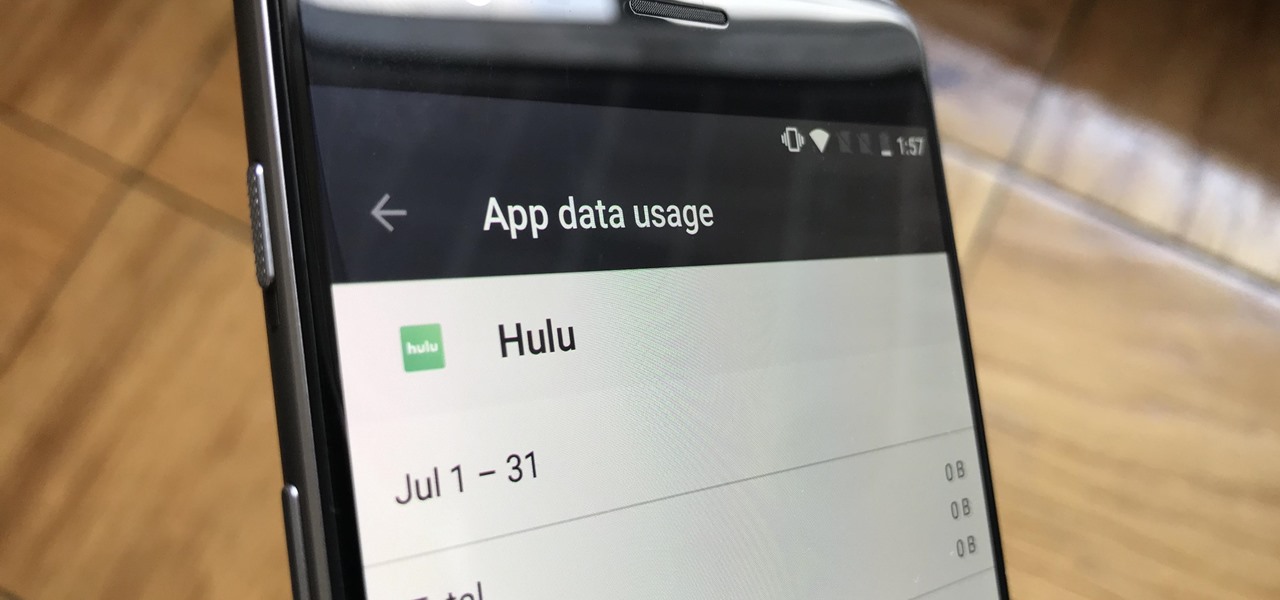
It seems almost every carrier now has an unlimited data plan, and free Wi-Fi is now available in more places than ever before. If you want to be connected, it has never been easier — but that still doesn't mean that everyone can stream as much as they please.

With the release of Apple's ARKit comes endless possibilities for education and learning. One of those possibilities is an AR rotating model of our solar system in your room, another is using AR to instantly know the nutritional value of food items.

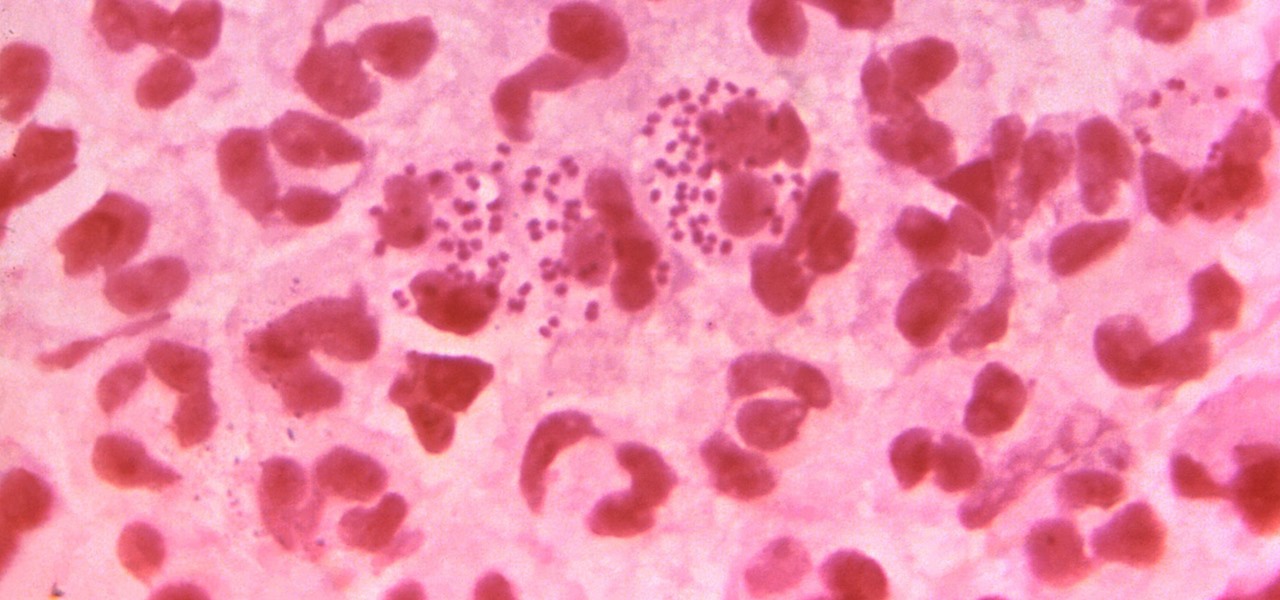
In the race to outsmart "untreatable" antibiotic-resistant gonorrhea, one of the three new treatments on the track is about to enter Phase 3 clinical trials. Hopefully, it'll be widely accessible sooner rather than later, for the 78 million people who are diagnosed with gonorrhea each year.

YouTube is a giant platform — over 300 hours of video are uploaded every minute. It can be difficult to keep track of your favorite videos in such a chaotic sea of content. Difficult, but certainly not impossible.

It is not just a bad summer for ticks — it has been a bad decade for the spread of tick-borne infections. New surveillance from the CDC reports rapid expansion and increase in cases of babesiosis, a sometimes life-threatening disease, in Wisconsin.

Volvo Cars' claims it will offer Level 4 models by 2021 means the premium carmaker will likely have to finalize the driverless design to meet the aggressive timeline by next year at the latest.

Pokémon GO's augmented reality journey is continuing with Apple's newly announced ARKit. It's no surprise considering Pokémon GO is the largest mainstream augmented reality game, with 500 million downloads.

Do you know what your smartphone is made of? I've had smartphones for years, but if you asked me that question I'd probably respond with "Wi-Fi." For uninformed consumers like myself, it may shock you to know just how much goes into creating a smartphone.

Ride-hailing services are everywhere nowadays and with new companies developing all the time, it is one of the most convenient ways for people to get around. Companies like Uber make it easy for passengers to call a car to pick them up and drive them to their desired location. These services have been especially helpful for commuters as well as those who might need a ride home after a night at the bar. However, ride-hailing services require driving with a total stranger, which means the safet...

Getting support for your mental health is now as easy as opening up Facebook Messenger. By just opening up the Messenger app, you can connect to Woebot, a new chatbot developed at Stanford trained in administering cognitive behavioral therapy (CBT).

Last week, Next Reality wrote about how the Microsoft HoloLens team is partnering with thyssenkrupp. Their mission? To bring mixed reality to the workplace. Now, Microsoft has just confirmed in a blog post that the HoloLens has passed the basic impact tests for protective eyewear in North America and Europe.