
How To: Recognize Crowd Control - Part 2
In the first part we differentiated the two types of control, mental and physical. In part 2 we will dig deeper into Physical crowd control and analyze examples that are present today.


In the first part we differentiated the two types of control, mental and physical. In part 2 we will dig deeper into Physical crowd control and analyze examples that are present today.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

The small size of most indie game development teams is a strength, but also a weakness. It allows them to take risks and explore revolutionary ideas that a larger company could never justify to its shareholders, but also means they must navigate the game development labyrinth with minimal help, taking much longer than those with big development teams. Some of the most exciting indie games currently in development have been so for years, or look like they will be.

Week 01 : 9/31 - 09/06 Read Chapters 1-2 of Creating Motion Graphics with After Effects

A rare textile woven from the silk of more than one million spiders is currently on display at the American Museum of Natural History in New York City. The incredible textile measures 11 by four feet, and is the largest piece of spider-woven textile in the world.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.

I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned how stalkers work.
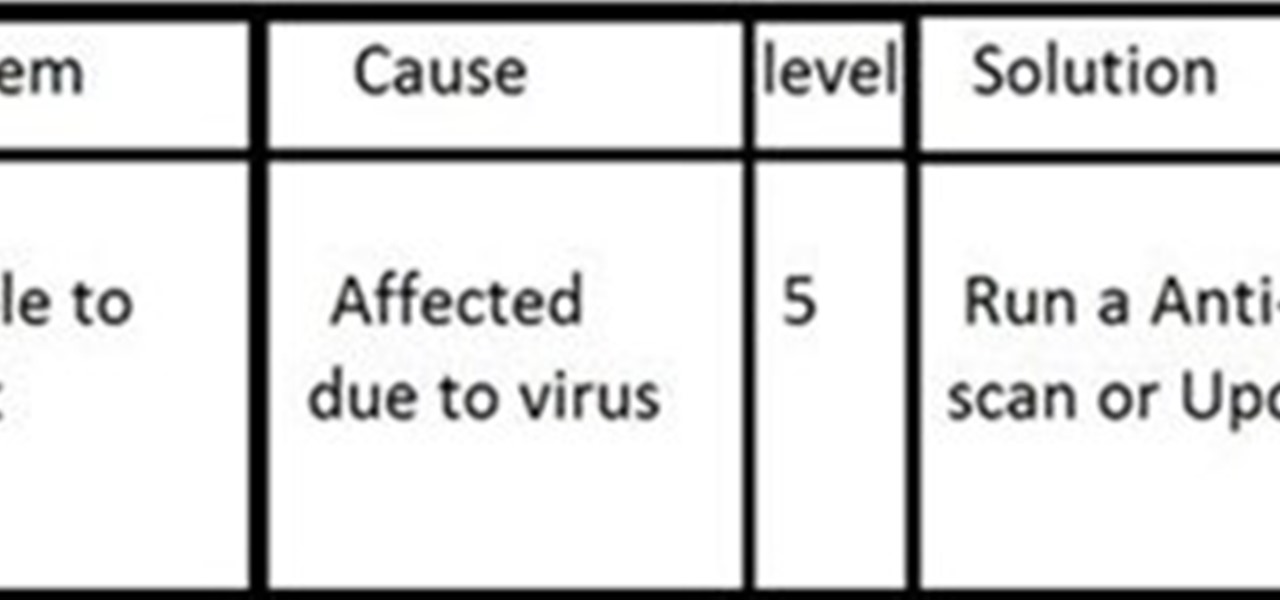
INTRODUCTION The everyday PC user doesn't think much about its PC and problems that can cause critical damage to their data or other stuffs stored on Hard drive and other electronic parts until the problem actually occurs. Once a failure happens, the repairs can be costly and very time-consuming and one also have to sacrifice their data stored on hard drives if the damage is more severe!

Ever wonder why your cat rubs his face on things around your house? We'll tell you why in this segment. We also cover ways to make your cat feel comfortable so he won't feel the need to spray, some measures you can take to prevent your cat from spraying and much more. Keep a cat from spraying.

Weeds are plants that are growing where they’re not wanted. They out-compete other plants for nutrients and can spoil the look of your garden. Weeds can take any form and can vary depending on where they grow.

They can be called wash rags, wash cloths or dish cloths. There are lots of different patterns for them. Here's an easy washcloth that incorporates the Stockinette Stitch with Seed Stitch edging.