
News: Bacteria Turn Off Plant Genes to Help Parasites Destroy Billions of Dollars of Crops Every Year
Before you bite into that beautiful tomato in your garden, the tomato fruitworm, or the Colorado potato beetle, might have beat you to it.


Before you bite into that beautiful tomato in your garden, the tomato fruitworm, or the Colorado potato beetle, might have beat you to it.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back, my greenhorn hackers!

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

Google I/O is like Christmas for Android enthusiasts. Every year, this conference showcases new and upcoming features for the world's leading mobile operating system, and this year's was no different. Shortly after announcing Android M, Google released a preview version of the upcoming firmware for Nexus devices.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Welcome back, my greenhorn hackers! I've been writing these Linux tutorials in an attempt to fill the void in the education of some aspiring hackers into the Linux operating system. There is a lot to know, and in this tutorial, we'll look at Linux file permissions. Step 1: Checking Permissions
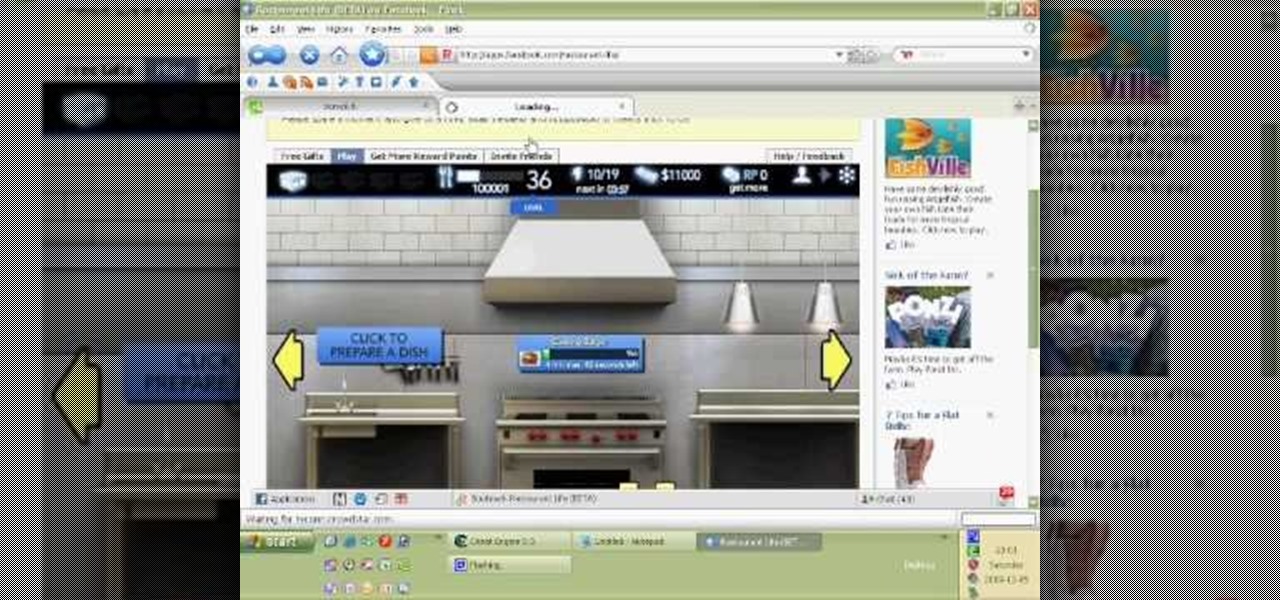
Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

In this video tutorial, you'll learn how to use the Second Copy backup application, for the Windows operating system, to protect your most important data. For step-by-step instructions on installing and using Second Copy, take a look at this backup how-to.

VLC Media Player is one stop shopping for all your music and video playing needs. You can watch any audio or video formats from .flv, .wmv, .mov and more. If you are tired of having multiple softwares for playing different files, consolidate and use VLC Player instead. This tutorial shows you how easy it is to download VLC Media Player for any operating system.

This software tutorial shows you how to convert your Windows Movie Maker projects using conversion software so that they will play on a Mac computer or operating sytem.

Check out this video tutorial on Blender. You'll see how to successfully create a modeled skull in Blender.

Got video files on your computer? Watch them on your big-screen TV – using your Xbox! You Will Need
This step-by-step video tutorial shows you how to install CHDK onto your Canon digital camera. CHDK is a firmware enhancement that operates on a number of Canon cameras. CHDK gets loaded into your camera's memory upon bootup (either manually or automatically). It provides additional functionality beyond that currently provided by the native camera firmware.
Admit, you're curious. You want to know just what does it take to make a virus for the Mac OS X operating system. Check out this video to learn how to write a harmless virus for computers running Mac OS X.

Have access to a Battistella T220P ironing table and, however improbably, wondering how to use it? Well, you're in luck: With this video demonstration, you'll learn how to operate the Battistella T220P ironing table in the service of ironing a shirt. For more, or to get started using your own Battistella T220P ironing table, watch this video tutorial.

General Pipe Cleaners Easy Rooter Junior is the right machine to clear washtubs, small floor drains, roof vents and other medium-size drains. This video will give you a general overview of the operating instructions and safety procedures for the easy Rooter Junior. Take a look.

Cool project to show how a capacitor operates!

A transom window is a traditionally fixed window over a door or an operating sash window. In this how to video, the experts form the DIY network prep and install a transom window in this historic home. Watch this tutorial and you can be installing a transom window into your own home.

The Paslode Framing Gun is operated by a gas cartridge and battery so an air compressor is not needed. The tool also has a large range of nails available for different job requirements from 50mm To 75mm. Watch this video tutorial for a demonstration on how to use a Paslode impulse framing nail gun.

This video tutorial shows how to assemble an automatic Lego crossbow. Learn how to build and operate an automatic toy crossbow made out of Lego bricks.

If you've never heard of Blender, maybe you should get it and watch this video tutorial on how to use the curve tools in it. Great for 3D modeling and animating.

If you're going to do this, be careful, as your fingers get close to operating high voltage devices & potentially fatal current! Remember that TV's can store a lot of energy for a long time, so don't be poking your finger everywhere - even if the TV is off.

The Titan hitch receiver lock is a lock for all 2 inch receiver hitches. This is a simple padlock style lock. What you do to operate it is pull the protective cover off, take the key and give it a little bit of a turn. This video walks you through it.

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.
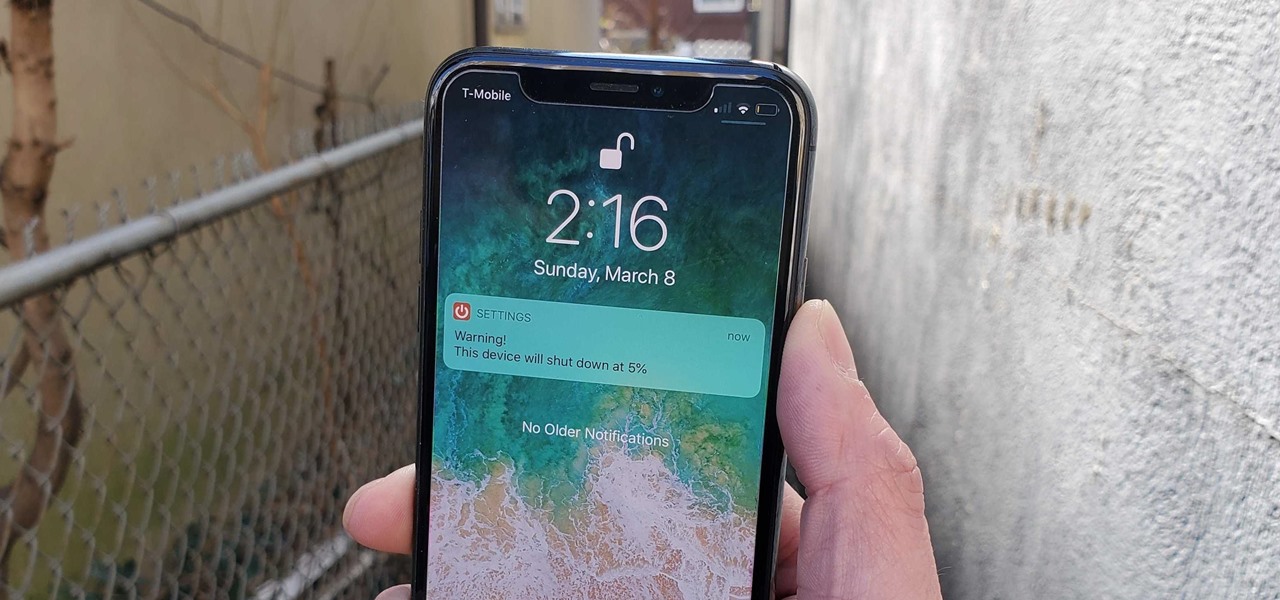
If running out of battery while out and about weren't bad enough, the experience is a lot more painful if your iPhone has a semi-untethered jailbreak. With that kind of jailbreak, when the iPhone dies, all of the mods will be disabled after the device powers back up. Fortunately, instead of restoring your jailbreak and tweaks manually after recovering from a critically low battery, you can avoid it altogether.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.