This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Mobile data is expensive. The internet connection that comes with your cell phone plan is generally limited to a certain amount of gigabytes that can be downloaded before your monthly cap kicks in, at which point you run the risk of incurring costly overage fees.

Android's flexible operating system allows for lots of customization, and one of the most common ways to add personal flair to your smartphone is to set your own ringtones and notification sounds.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

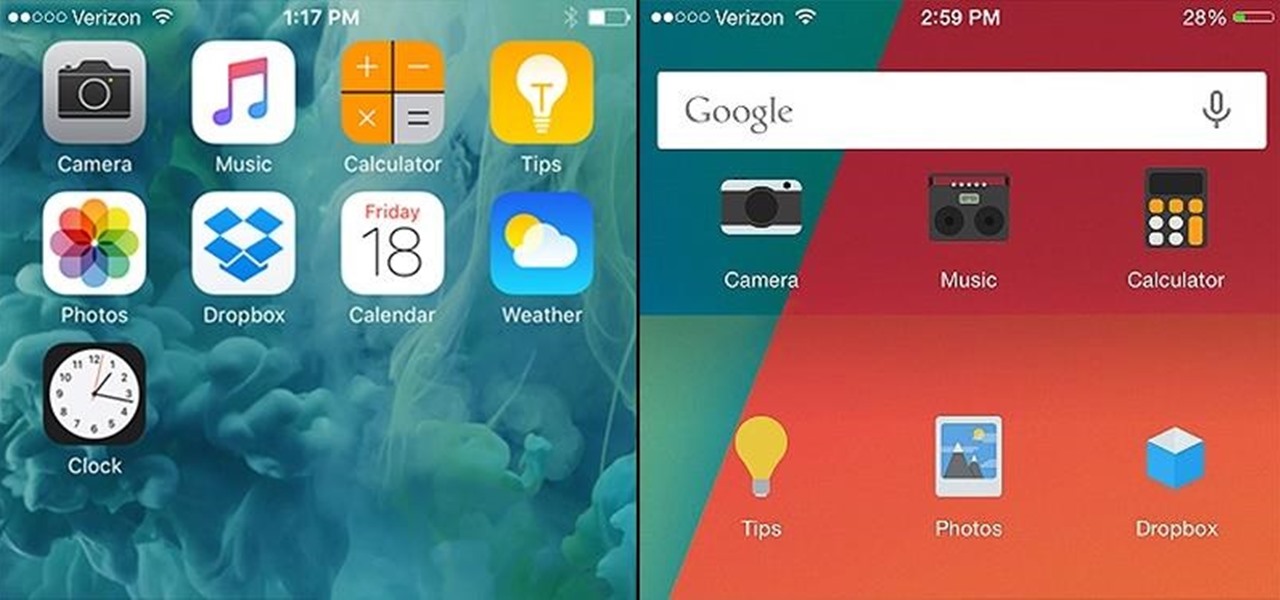
The competition between iOS and Android is fierce. Each operating system offers unique and powerful features, so it can be hard to choose which one you want. However, for iPhone users, a little tweaking and some themes can give your iPhone some of the key features and aesthetics of an Android.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

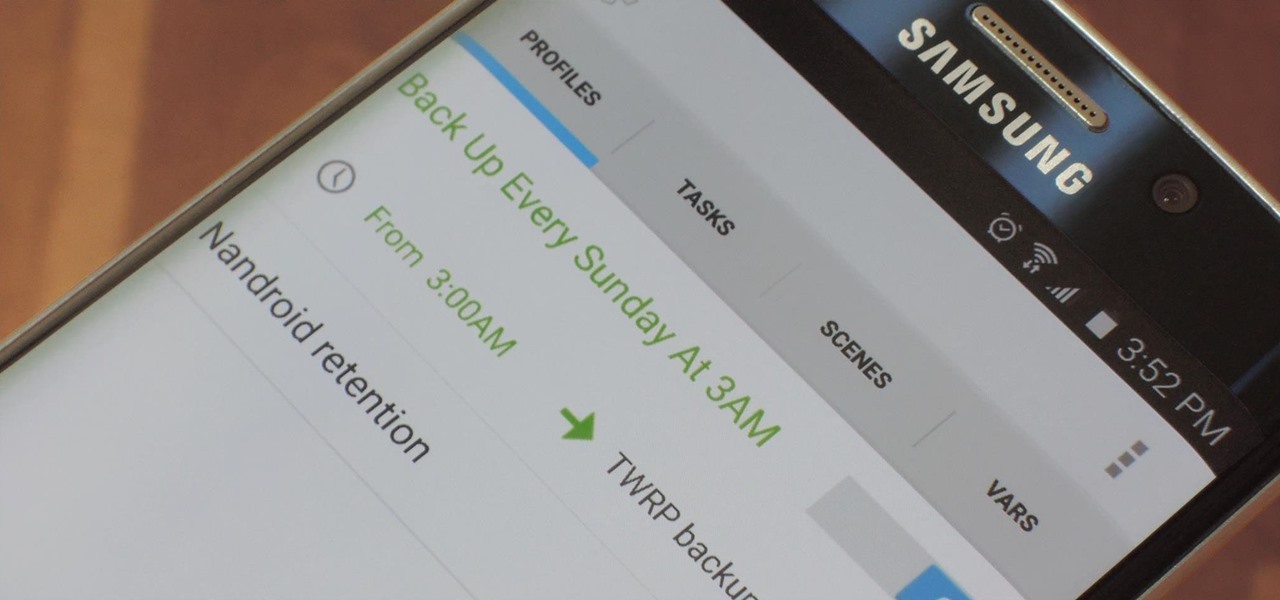
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

Live Photos is exclusive to the iPhone 6S and 6S Plus models, and provides a new dimension to your pictures. When taking a picture, the camera captures moments immediately right before and after you hit the shutter, creating a GIF-like animation that's approximately three seconds long when combined.

Hello! I'm newbie at Null Byte and I want tho share some of my thoughts with you guys, hope you like it. I've been inspired by 3 facts for making this: 1- The post 'How to write better code', 2- A few illegible comments at some posts, 3- I myself have never written such a long text in English, this will be my first one!

Apple's unveiling of the iPhone 6S, iPhone 6S Plus, Apple TV, and iPad Pro dominated the news today, but at the end of their special September 9th event, they quietly released the final version of iOS 9 to developers, called the Gold Master (GM) build.

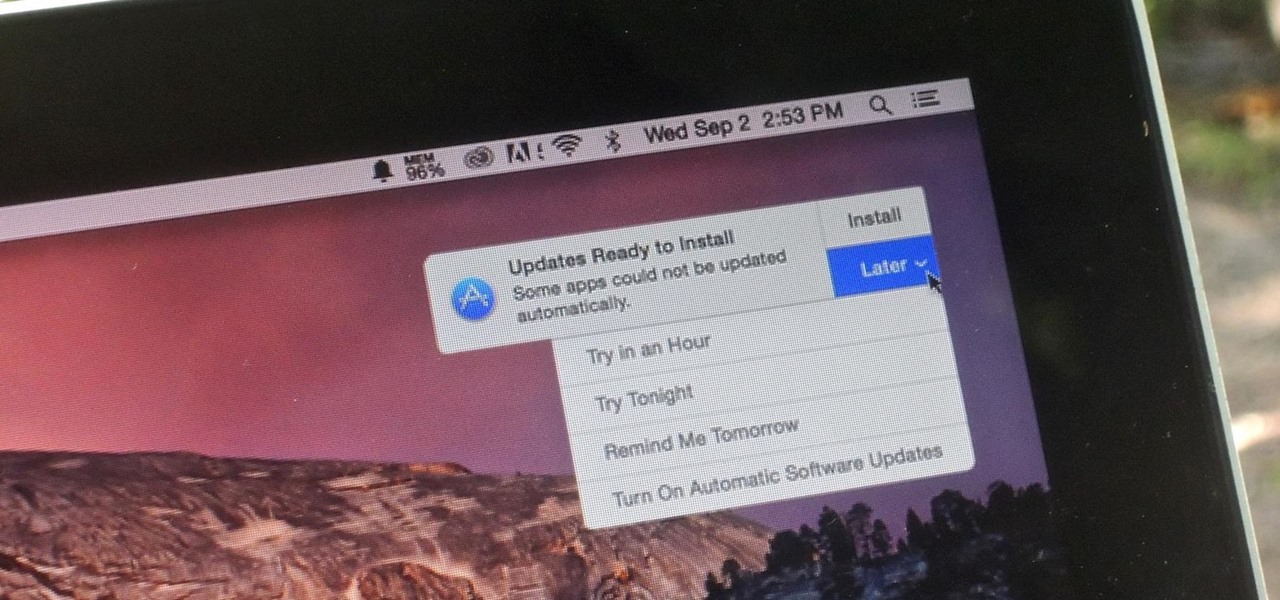
Software update notifications are meant to be a reminder to keep your operating system and apps up to date, but that doesn't mean that they never get annoying.

ADB and Fastboot are probably the most essential tools for any Android aficionado. They can do everything from backing up your device to unlocking your bootloader with a few simple steps. This paves the way for many new tweaks and customizations that weren't possible before. The required platform works with the three most popular computer operating systems, too, which is good news for everyone.

The day has finally come, and after quite a bit of hype and buildup, Windows 10 is now officially available. The update itself is on a staged rollout, which means it will be slowly becoming available to users over the coming weeks and months, so don't panic if you haven't already received an update notification. Besides, you have until July 29th, 2016 to download your free copy of Windows 10 if you're eligible, so there's plenty of time to get your ducks in a row.

All of those keys on your keyboard can do much more than just help to update your Facebook status or fire off a scathing tweet. By learning all of the keyboard shortcuts for apps on your Mac, you can cut back on mouse or trackpad usage to perform actions faster and more efficiently.

If you've updated your iPhone 4S or iPad 2 to a version of iOS 7, iOS 8, or even iOS 9, you've probably noticed that its performance is a little more sluggish than it was back when it had iOS 6 and lower on it.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

I'm an Android fan through and through, but occasionally, I see a feature or two on iOS that makes me a bit jealous. This was the case when I first discovered the useful functionality that lets you scroll to the top of a page by simply tapping the status bar on an iPhone.

With smartphone screens getting bigger by the generation, one-handed mode mods are becoming rather prevalent. Most of these function by shrinking the screen to a more manageable size, but this is actually kind of boring when you think about it.

If you've got a desktop computer, I can almost guarantee that you've got a widescreen monitor set up in landscape mode. It's how just about everyone uses their monitor these days, including myself. Except that it's not always the best way of working.

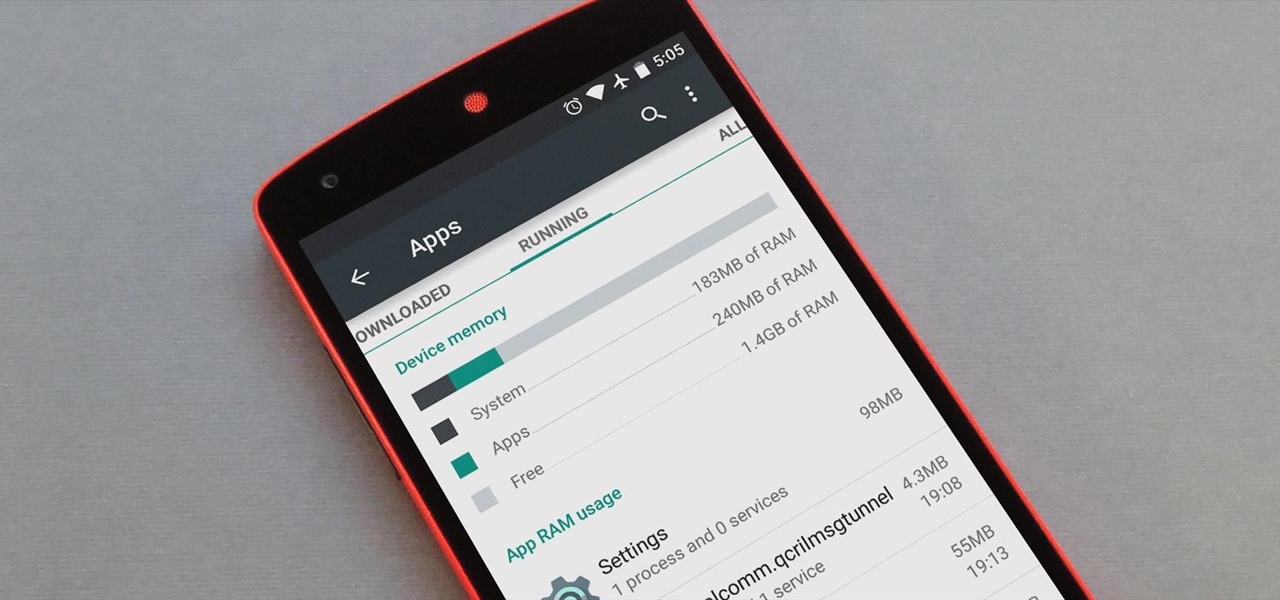
Android version 5.0 Lollipop introduced a ton of changes to the OS—and of course with new features, there's always a new set of bugs. One of the biggest bugs of all was a massive memory leak caused by the new screen-off animation, which loaded its assets into memory but never cleared them away.

Sony has a gorgeous line of smartphones using the moniker "Xperia," and the latest and greatest model is the Z3. The firmware for the Xperia Z3 was just updated to Android Lollipop, and many system apps of course got tweaked and refreshed with this latest version.

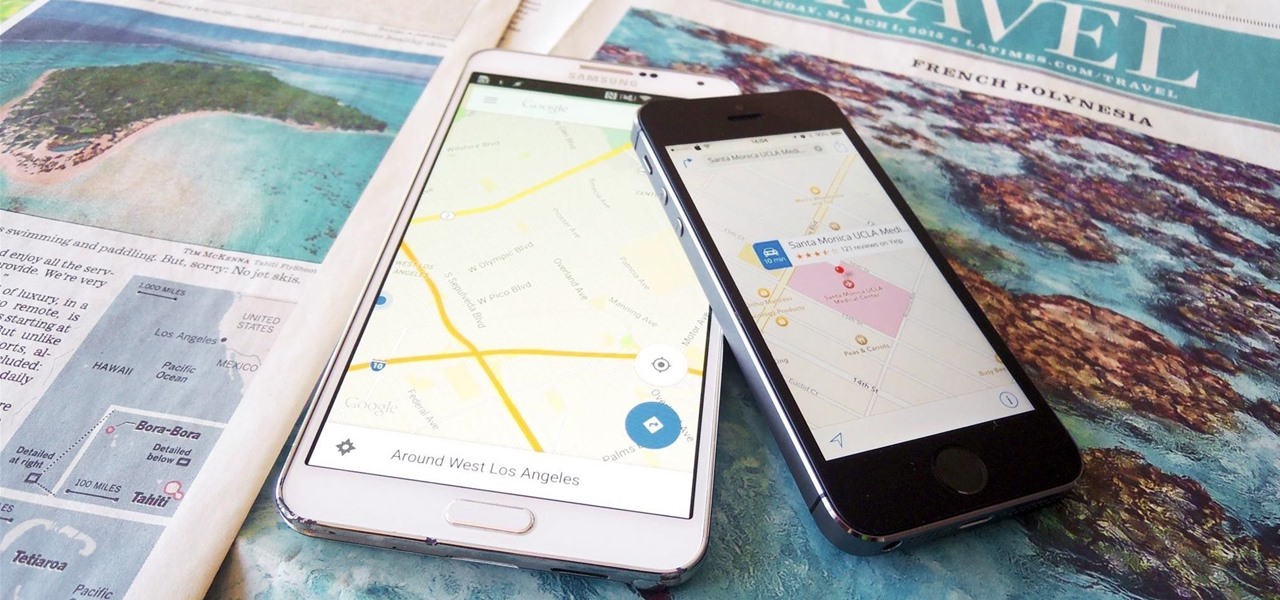
Applications like Apple Maps, Google Maps, and Waze save every location you visit or search for as a way to speed up future searches and to find commonly-frequented places. But what if you go somewhere unsavory and don't want anyone knowing?

Emojis, smilies, emoticons—whatever you prefer to call them, these fun little guys can bring a text-based conversation to life. If you're worried that someone's sarcasm meter might be broken, just toss in a wink at the end of your message. Or perhaps you can't quite put your sentiment into words, but one of these little graphics suits the moment perfectly.

One of the many unique features that sets Android apart from other mobile operating systems is its live wallpaper system. Instead of the same old boring static image, this system lets developers create apps that provide dynamic home screen wallpapers.

If you're an Android fan, you probably made your choice in mobile operating systems based on the insane level of customization options that Google's software offers. Don't like your home screen app? Simply replace it. Not a fan of a particular app's sharing system? No big deal, just share through a third-party app.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

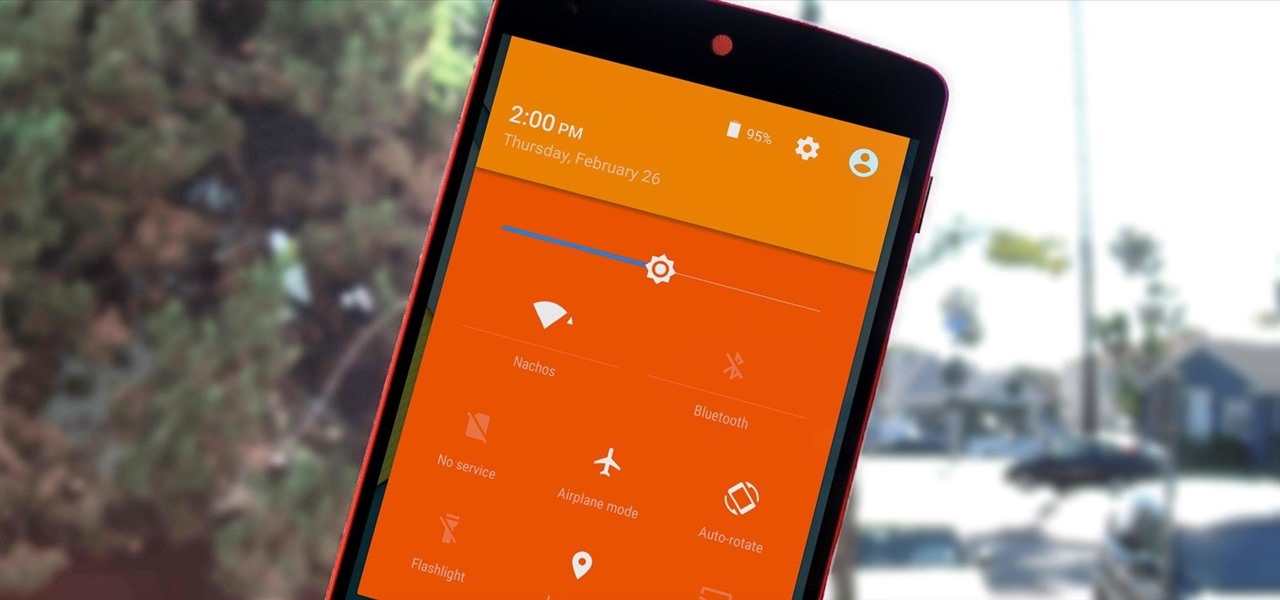
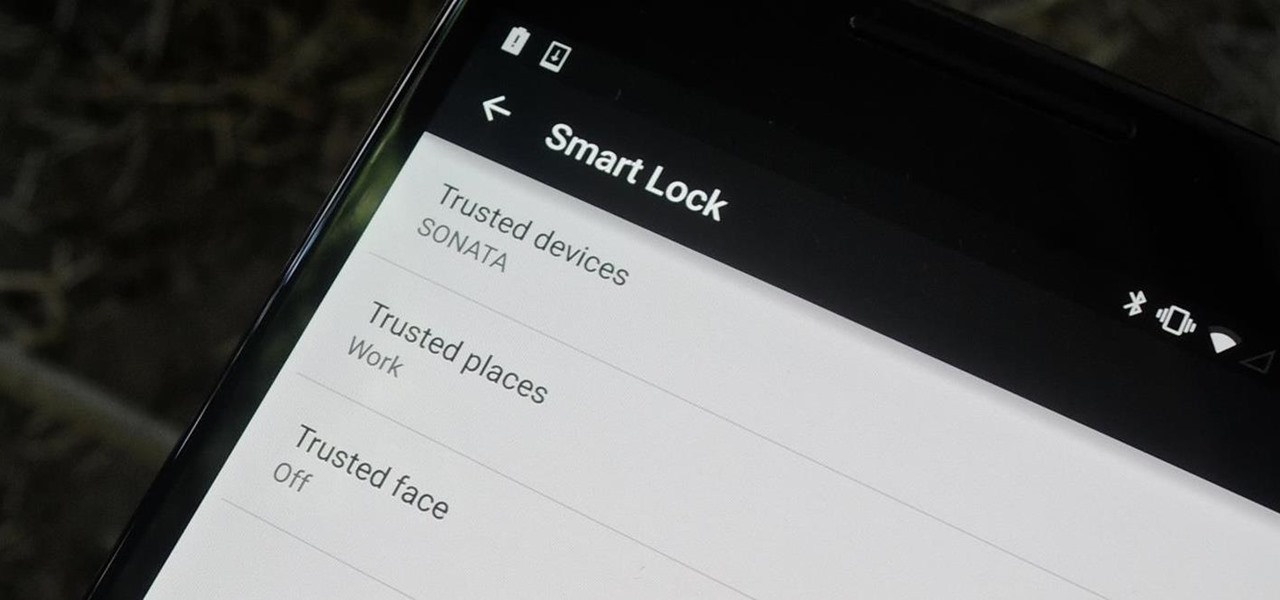
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

2015 is quickly shaping up to be the year of the cord cutter, with various media companies finally warming up to the concept of offering live streaming content. In the wake of Dish Network announcing a streaming cable service called Sling TV and Sony unveiling a similar platform in PlayStation Vue, NBC has decided to stream the Super Bowl and all of its festivities online. Before we get to all of the many ways you can stream Super Bowl 49 between the New England Patriots and Seattle Seahawks ...

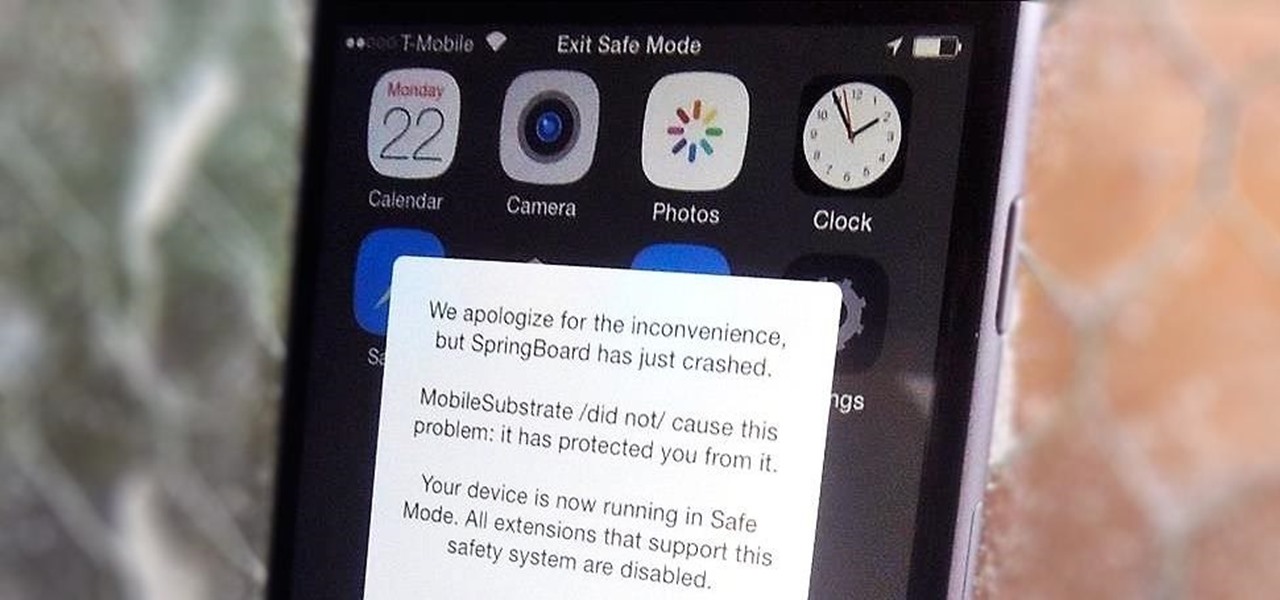
Installing tweaks or themes onto your jailbroken iOS device is a pretty fun and exciting experience, but if you do it for long enough, you're bound to come across a bug that will cause your operating system to crash.

One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issues with voided warranties.

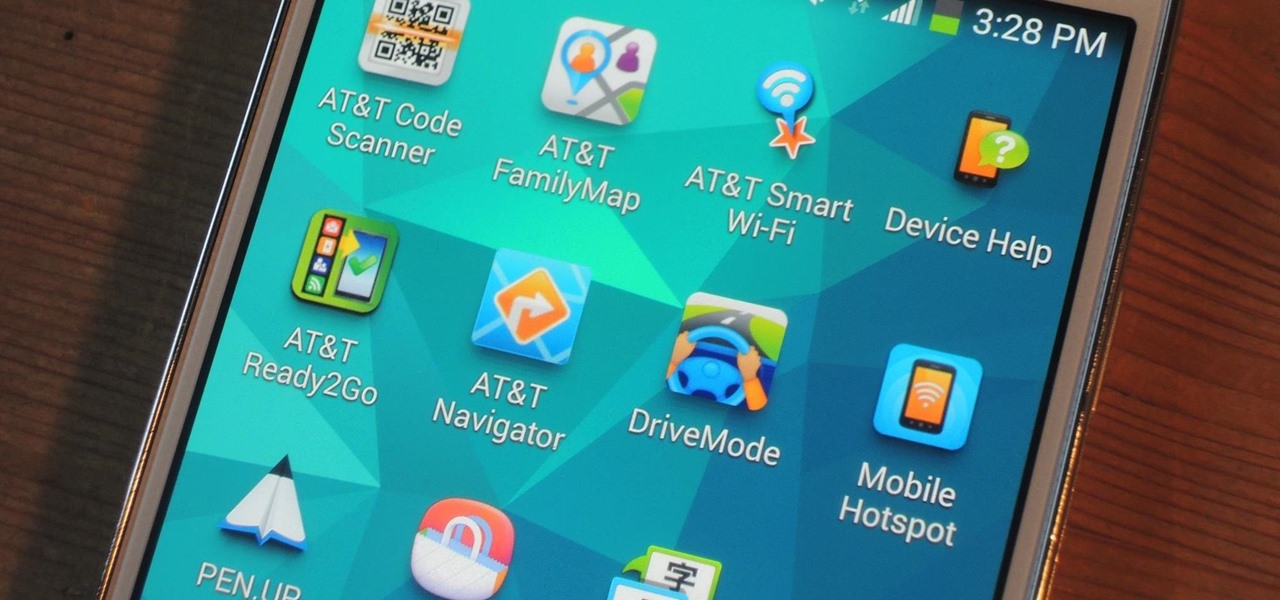
AT&T Code Scanner, DriveMode, and Samsung Hub make up just a sliver of the sea of apps on my Galaxy Note 3 that I'll probably never use in my lifetime. Additionally, there aren't any built-in methods for uninstalling these pre-loaded Android apps (aka bloatware) from carriers and manufacturers.

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.