Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

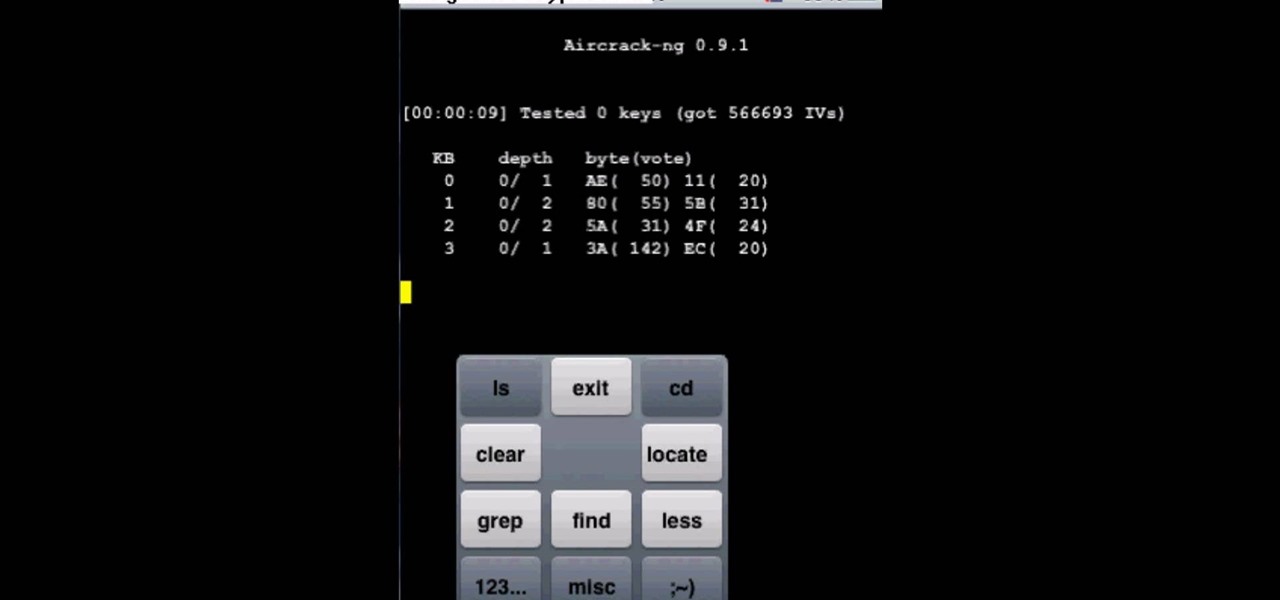
Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

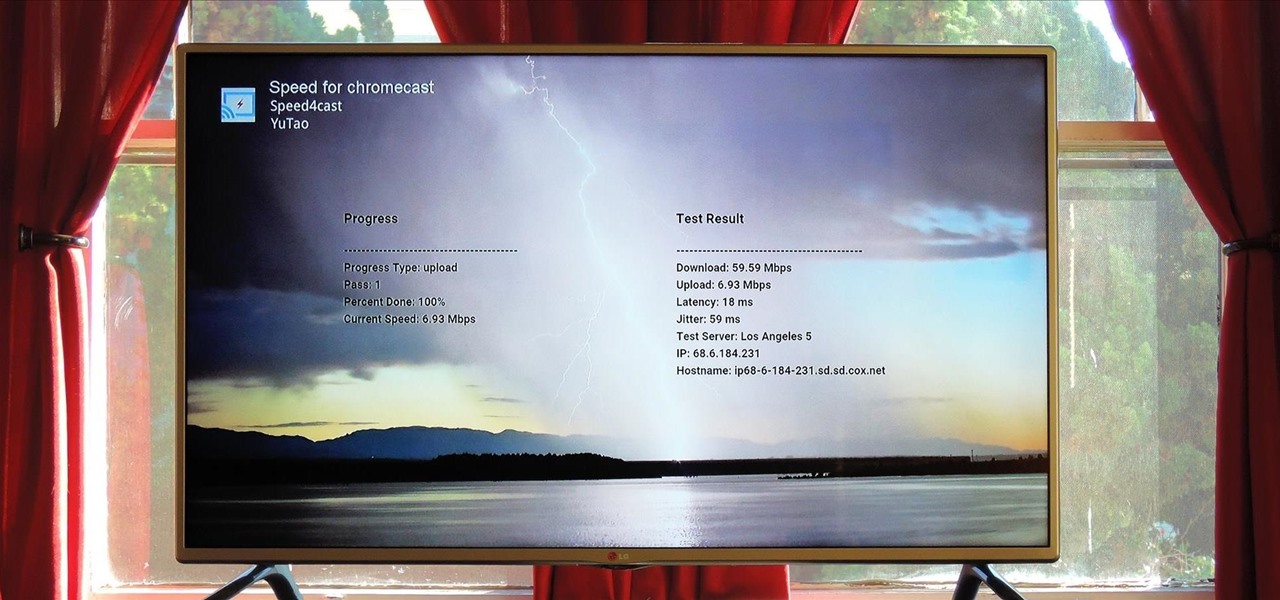
At its core, the Chromecast is essentially a web browser on a stick. When you cast content from your computer or smartphone, all you're really doing is telling the Chromecast which website to load.

One of the more talked-about features of Android Lollipop is a new Priority Mode that allows you to mute all notifications except for those coming from starred contacts. As simple as that sounds, this can still be a bit confusing—or at least lead to some unwanted interruptions.

Apple prides itself on simplicity, but the company makes downloading video and music files onto your iPad or iPhone an overly complicated process, requiring iTunes and/or iCloud.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.

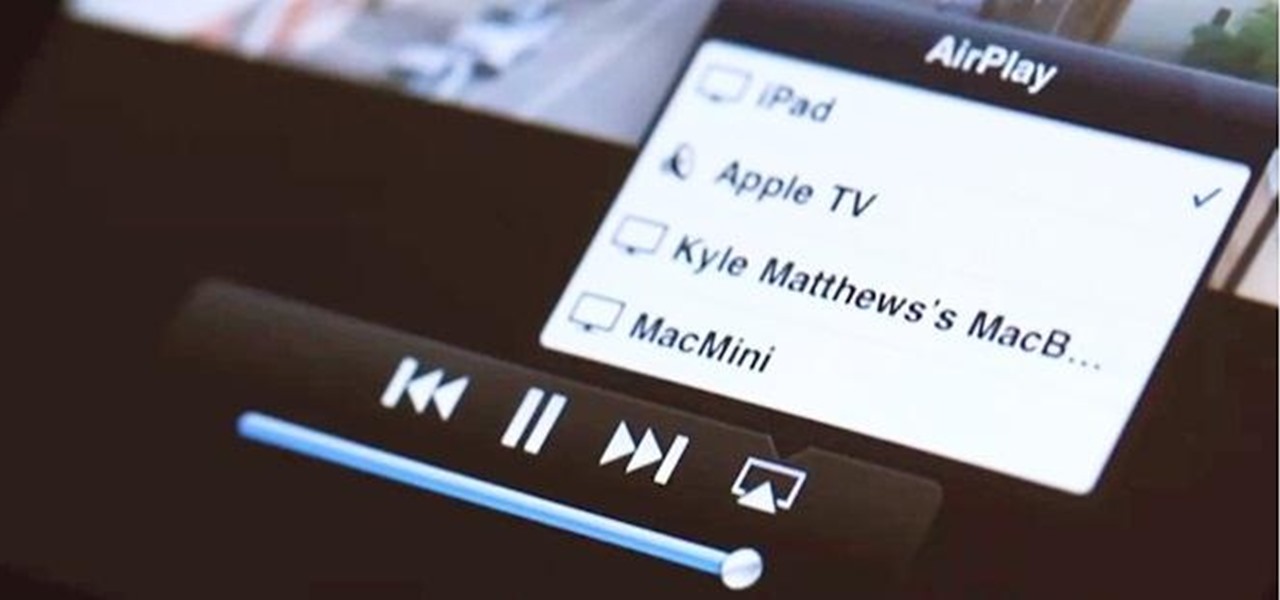
AirPlay is probably one of the most underutilized features in Apple products. It allows users to wirelessly stream photos, music, or video directly from their iPad, iPhone, iPod touch or Mac to their Apple TV or AirPlay-supported speakers. The Apple support page has a complete list of all the supported and needed devices. Mirroring is also available, but only for the iPhone 4S, iPhone 5, and iPad 2, all of which need to be running iOS 5 or later.

Kids have an infamous reputation for thinking vegetables are icky. After all, when compared to more fatty and grease-loaded foods like Hot Cheetos and french fries, it seems veggies just taste too...healthy. Which is apparently not a good thing in the eyes of a sugar and salt-obsessed child.

Step1. Determine the type of job you want. Make sure that you have a detailed and complete profile on ‘linkedin’. You must also have a number of connections. Then decide which job you are looking for and the typical functions and titles. Also choose which type of industry you would like to work in and also choose what locations. You also need to write down specific names of organizations that you want to work for and who are they.

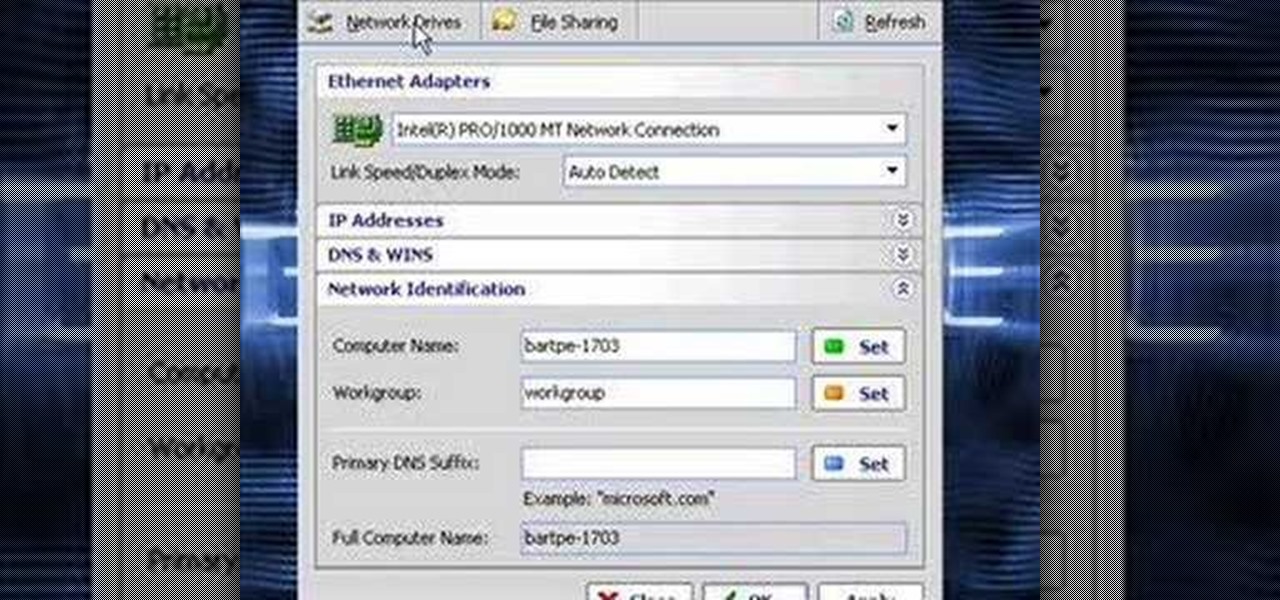
In this video the instructor shows how to clone computers across the Local Area Network using BartPE and Selfimage. To do this first we will have an original computer. Now create the image of the hard drive of the computer and share it on the network drive. Now, using that image from the shared folder you can start the clones of other computers by overriding their hard drive using this image of the main hard drive. Using this technique you can clone multiple computers which are the exact dupl...

Watch this video to learn how to unlock your Samsung phone. Power up the phone. It shows the boot logo. Take the battery out and insert T-Mobile SIM card. Turn phone on. Shows welcome. Confirm T-Mobile by dialing 611. To unlock phone: Take out the battery and SIM card. Put in an AT&T SIM card. Put the battery back into the phone. Turn on the phone. It says," wrong card". Dial *2767*3855#. The phone will reboot after 15 seconds. Screen says, "Welcome to T-Mobile". To keep service dial *7465625...

Growing plants from cuttings is an inexpensive way to expand your garden. With patience and the right technique, it can be done fairly easily.

All you need to remotely access your computer's iTunes library is your iPhone. Control itunes with your iPhone with this Howcast guide.

All you need to remotely access your AppleTV library is your iPhone. Learn how to control Apple TV with your iPhone with this Howcast guide.

Looking for an easy vegetable recipe for the grill? Follow along with this cooking how to video to learn how to make some grilled veggie skewers. Enjoy the bounty of summer by grilling your favorite summer veggies.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

Aloo methi, or potatoes with fenugreek leaves, is a fragrant and flavorful Indian dish with a unique taste. Fenugreek leaves are well known for their many medicinal properties and are a great alternative to spinach as a leafy green vegetable. Watch this how to video and try this wonderful recipe. Turn your plain Jane potatoes into something delicious and healthy with fenugreek leaves.

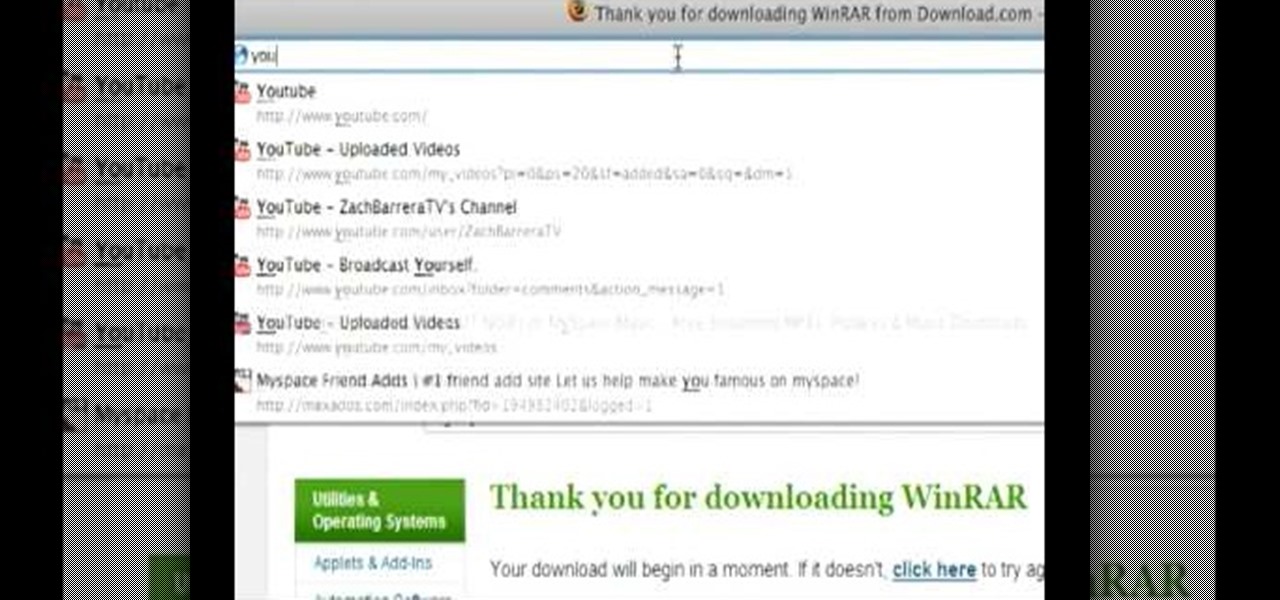
When the amount of memory on your computer sucks, you either have two options: Buy more RAM, or make use of the storage space you've got by compressing your files. One program that will become your new BFF should you choose to do the latter is WinRAR. WinRAR is a compression and packaging software that makes it way easier to store large files on your computer.

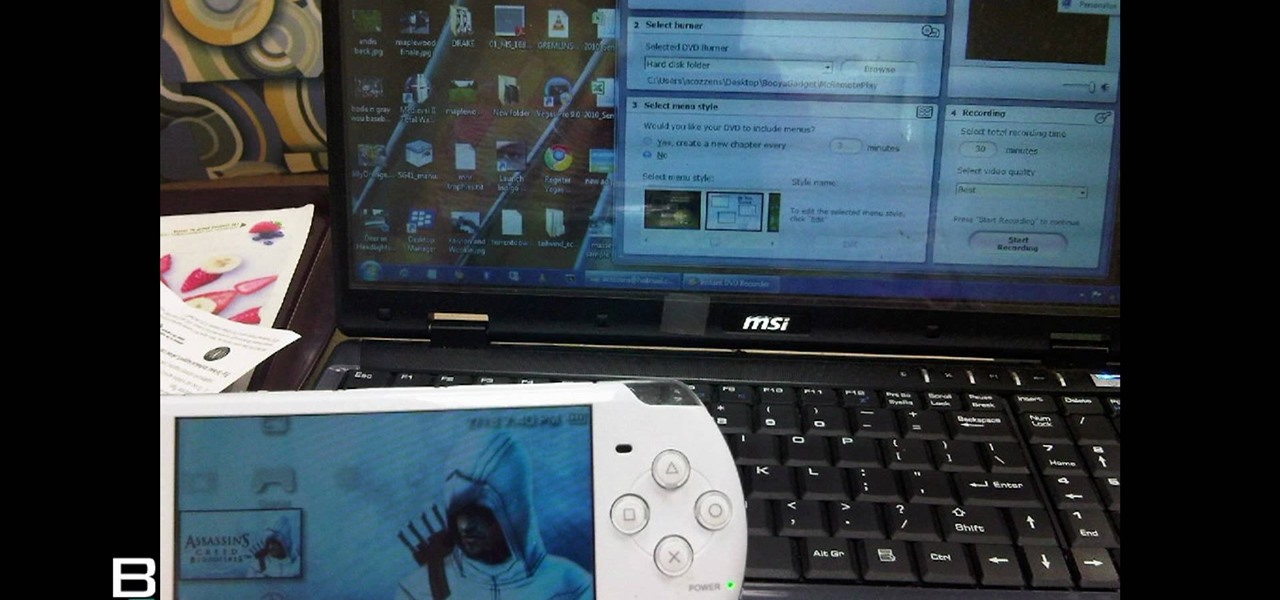
Play remotely with all your friends, stream videos and music from the Internet or even check your Facebook and email - all with your PSP. The PSP has Internet capability, but not every network will be available to you at all times. Here is how you can hack any wifi connection with your PSP.

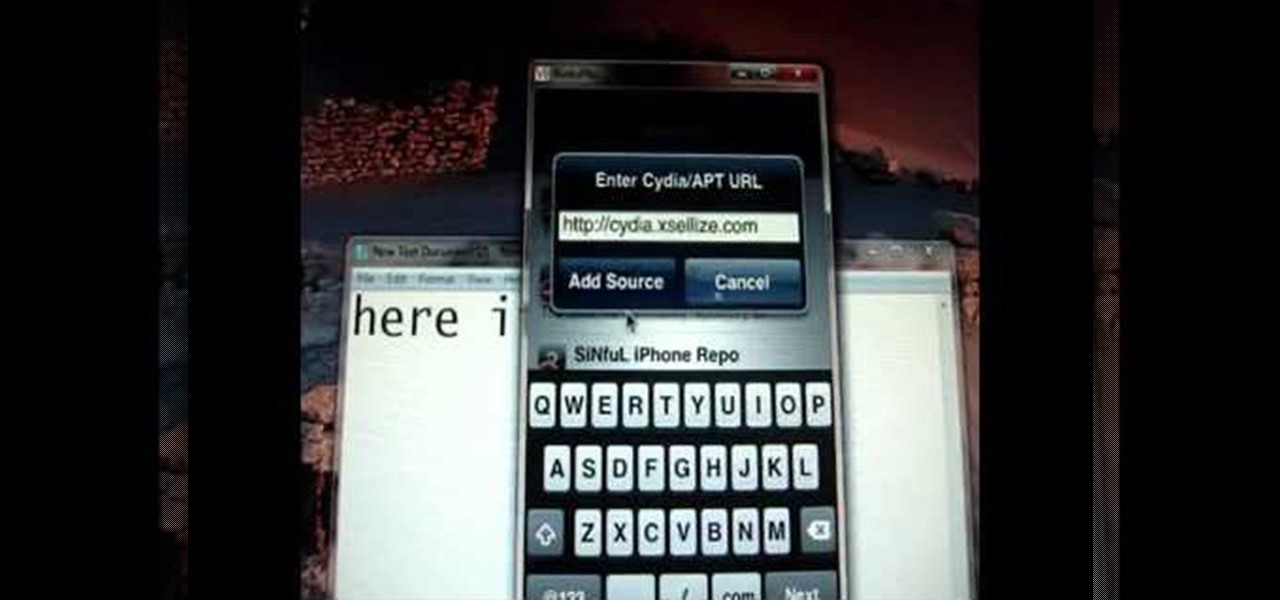
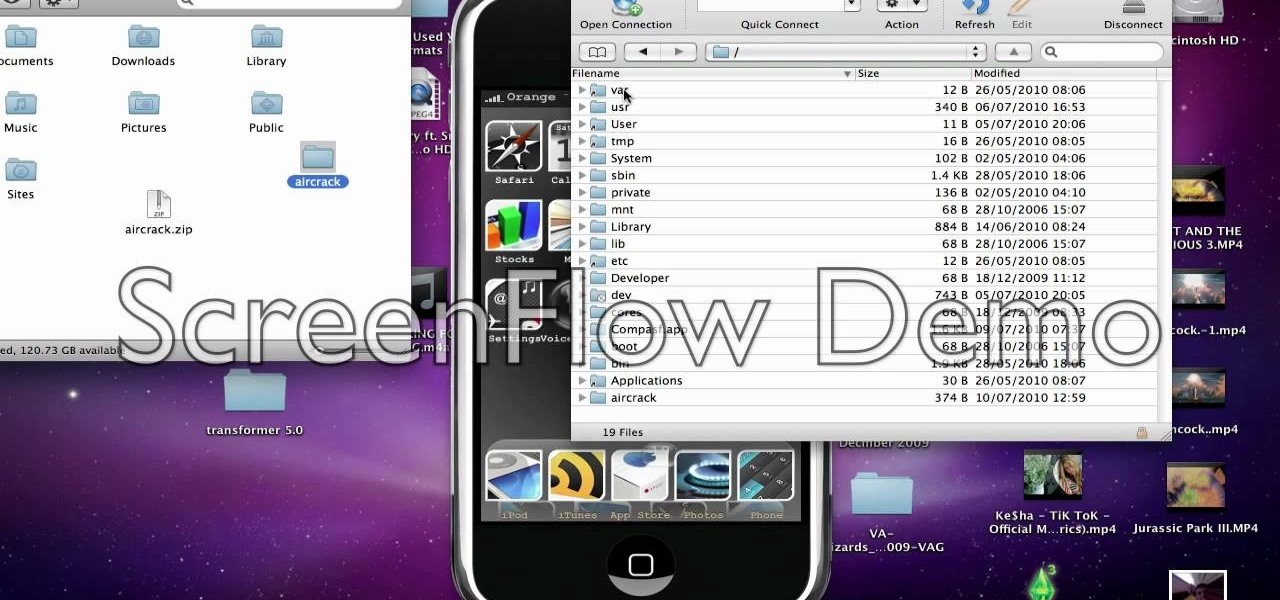
This video will show you how to install Aircrack on your iPod touch. Aircrack is a network suite designed to crack WEP and WPA keys. Though the project was shut down by its creator, you can still follow this video and learn how to do it.

This video will show you how to install Aircrack on your iPod touch. Aircrack is a network suite designed to crack WEP and WPA keys. Though the project was shut down by its creator, you can still follow this video and learn how to do it.

This video will show you how to install Aircrack on your iPod touch. Aircrack is a network suite designed to crack WEP and WPA keys. Though the project was shut down by its creator, you can still follow this video and learn how to do it.

Install this new add-on for Mozilla Firefox and show full-size images from Flickr or Facebook just by hovering over the thumbnail or link. This add-on shows the full-size images in a floating panel without having to open a brand new browser page. Thumbnail Zoom also works on MySpace, Amazon, Picassa, Twitter, LinkedIn, Hi5, Twitpic, deviantART, PhotoBUcket, Tagged, last.fm and Wikipedia. Veronica from Tekzilla Daily demonstrates all the cool features.

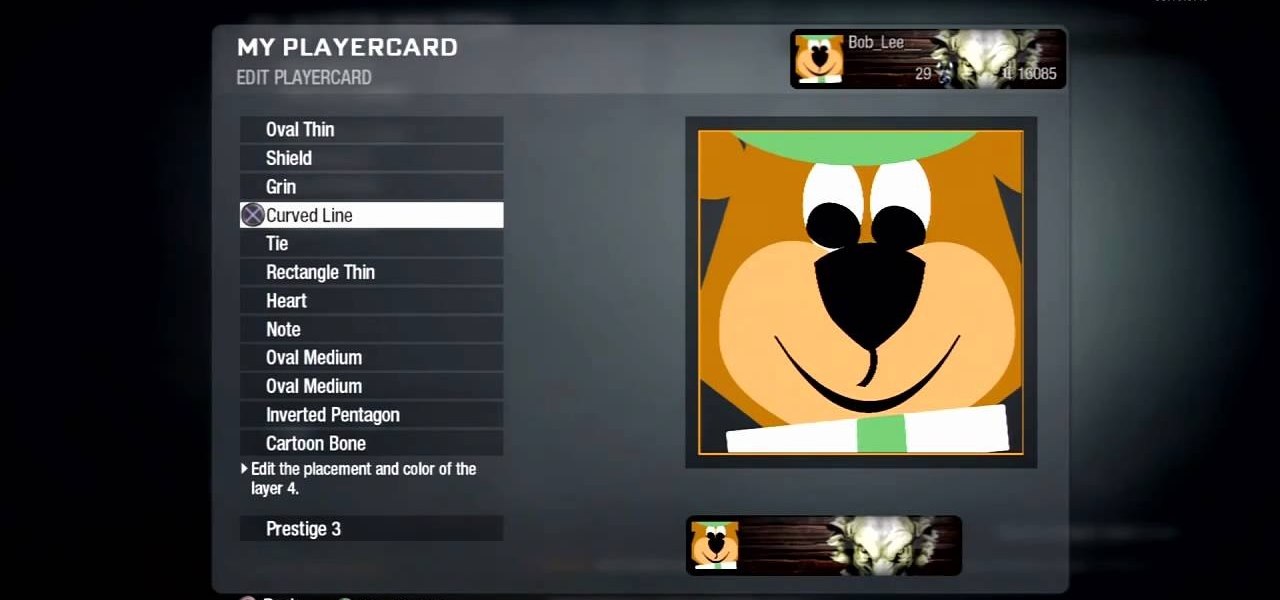
Are you smarter than the average bear? Show the world by using Yogi Bear as your Black Ops playercard emblem. This clip will teach you everything you'll need to know to draw a custom Homer Simpson emblem in the Call of Duty: Black Ops Emblem Editor.

Why run in intervals rather than either slow, medium speed, or fast during your daily jog? Interval training, which alternates between slow, medium, and fast, surprises your body by constantly changing the pace. This makes your body work harder in the same amount of time as your usual run.

In this clip, you'll learn how to jailbreak and unlock an iPhone 3G running iOS 4 for use on the T-Mobile wireless network. For more information, including detailed, step-by-step instructions, and to get started jailbreaking and unlocking your own iOS 4 iPhone 3G, watch this hacker's how-to from Zedomax.

Despite being on the Xbox Live Arcade and PlayStation Network, Scott Pilgrim vs. the World: The Game is actually a pretty hard video game. But, things get a whole lot easier with this cool play modes available with a few secret cheat codes. This video tells you those cheat codes to enable zombie mode, boss rush mode, and two others in the XBLA game.

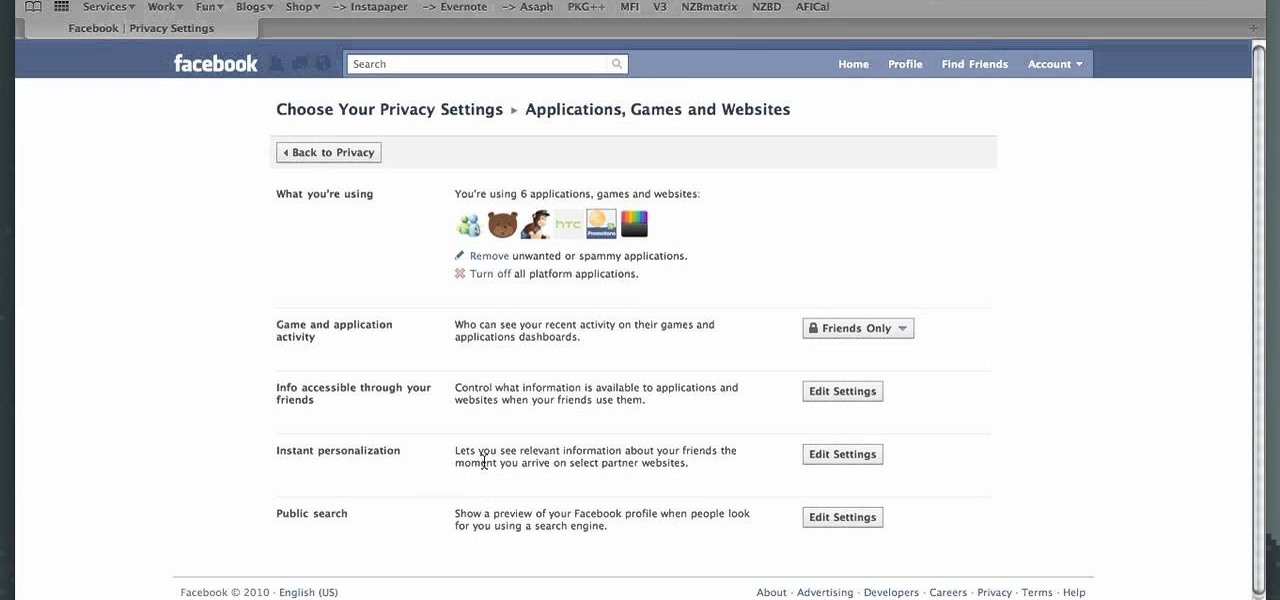
Want to know how to turn off Facebook Places? This quick clip from Lifehacker will teach you everything you'll need to know. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to deal with the Places feature, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

Looking for instructions on how to change your Facebook URL? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

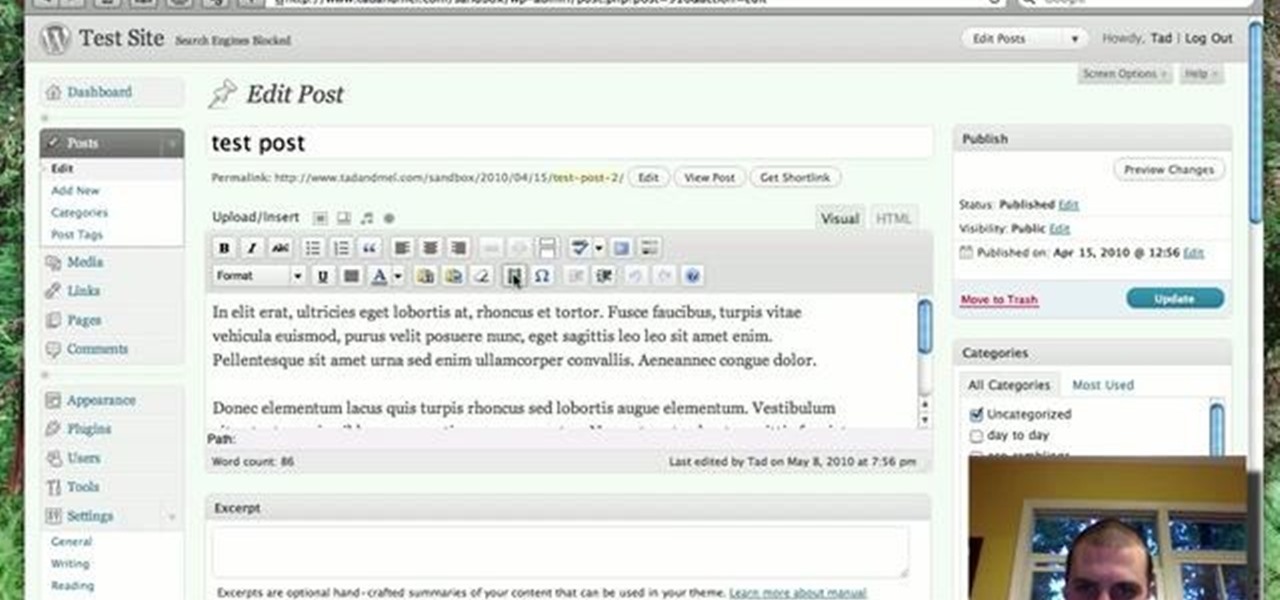
In this clip, you'll learn how to use the "Insert/Edit Embedded Media" and "Insert Special Character" buttons in the WordPress editor. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about the abovesaid things through videos like this one. Take a look.

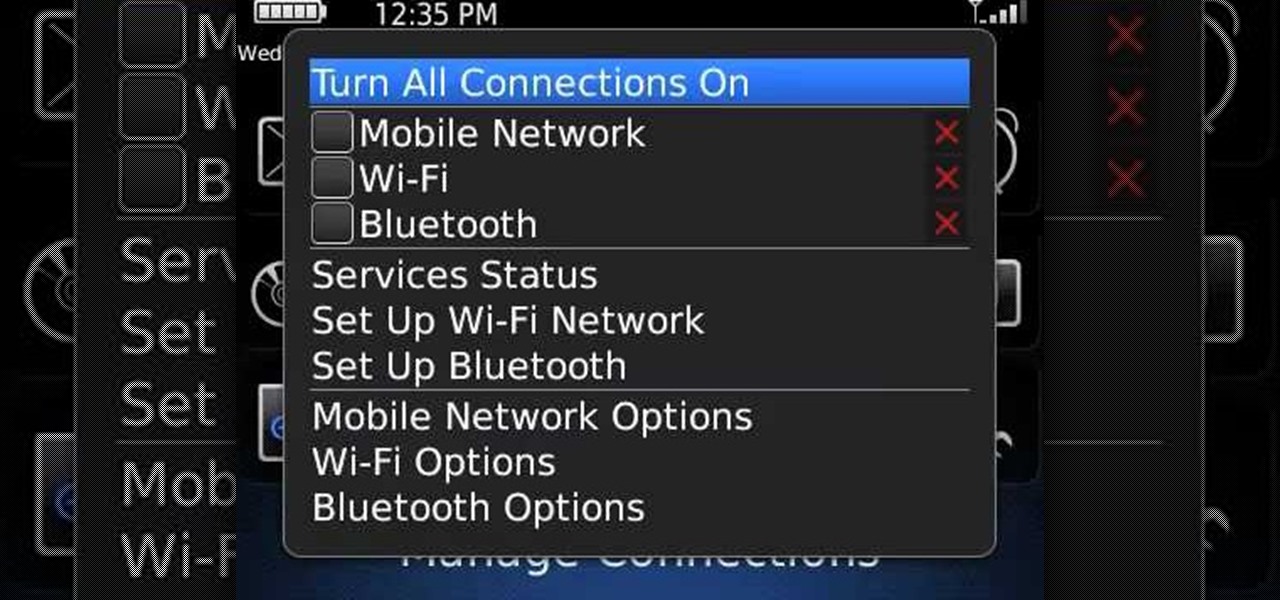
Learn how to use the Manage Connections pane to control mobile network, Wi-Fi and Bluetooth connections on your v5 BlackBerry phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.