Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

The Google Pixel's camera is a status symbol of sorts. When someone sees you with one, you become the photographer of choice for social events. And where do those photos end up? Social media, of course. It's how we share our lives now, and the smartphone camera defines how we approach that.

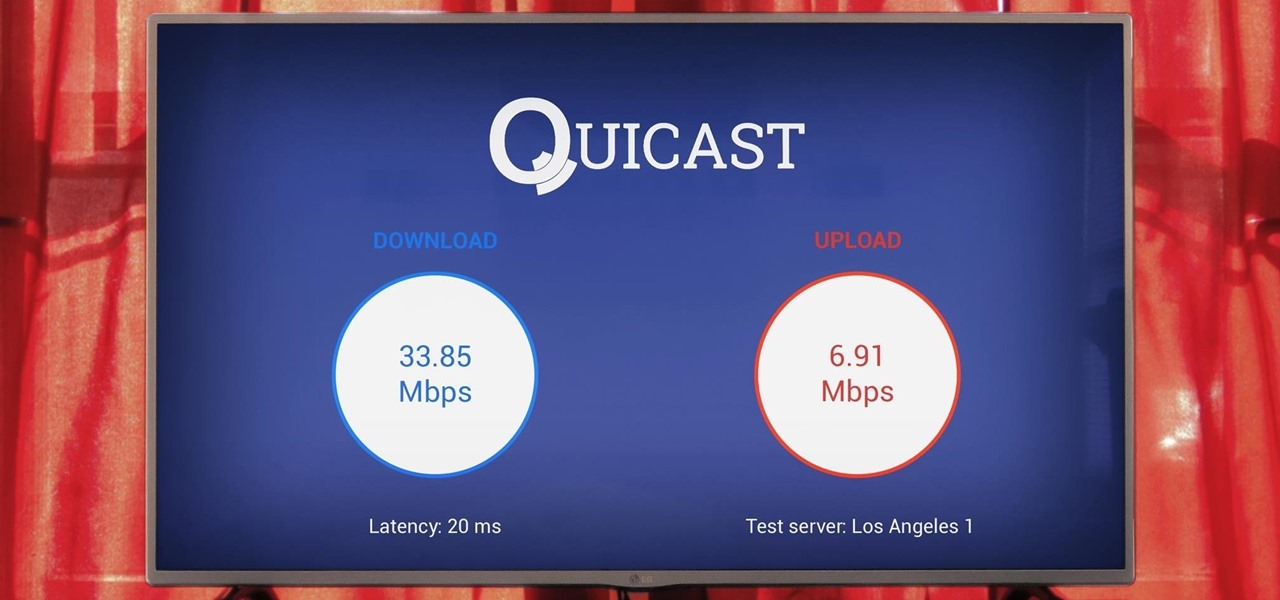
Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

As one of the household brands in creative software, Adobe is now ready to lay its claim to the artistic side of augmented reality.

The augmented reality cloud will probably be one of the most important pieces of digital real estate in the next few years, and China has no intention of being left out of the virtual land grab.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

We recently set out to find the best phones for people whose primary usage revolves around social media apps like Facebook and Instagram. Samsung, Apple, and Google were the three brands that made our top five, and while the latter only had one finalist, the two bigger OEMs had a pair of phones each. What struck us, however, was that Samsung's phones edged out Apple's not once, but twice.

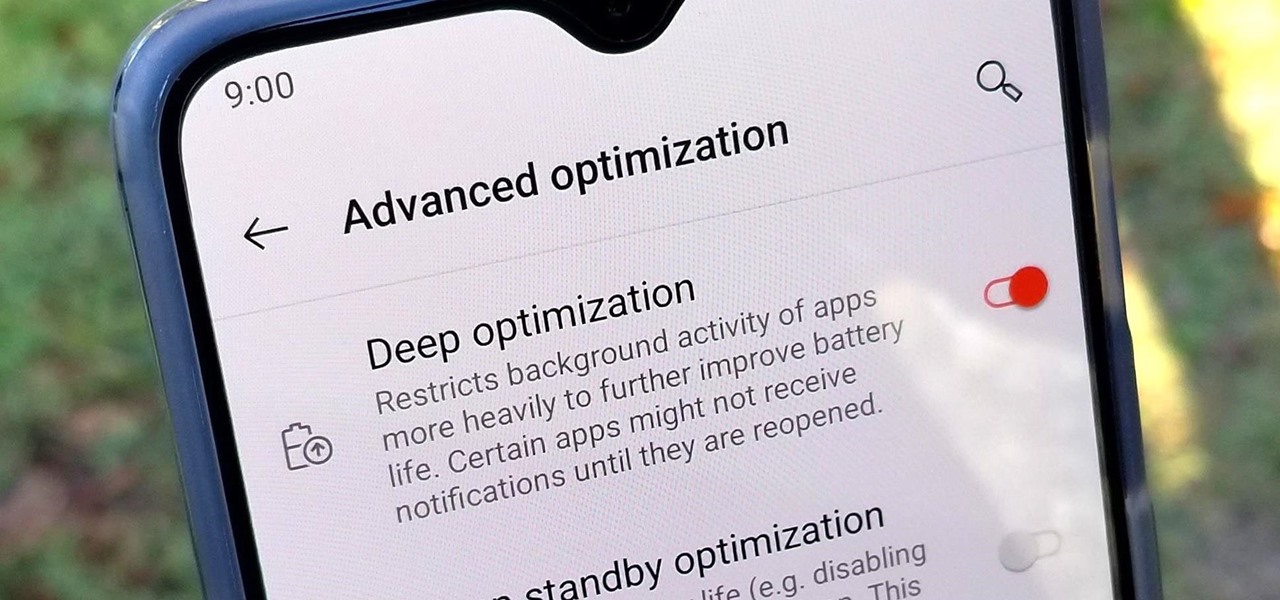
OnePlus is known for pushing the boundaries of what we thought was possible for a mid-range price. One of the best things about OnePlus phones is that their battery life is fantastic in general, but to achieve this, Oxygen OS will disable or delay notifications by default once your phone goes into deep sleep mode. You will not be notified until you wake the phone up — this could be an issue for some.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

A couple of months ago, I got the opportunity to get a sneak peek at a new media interface for ODG's R-9 Smartglasses, and the experience was impressive. Now, after weeks of keeping it under wraps, I can finally show off what I saw.

The research team at Google has found yet another way for machine learning to simplify time-intensive tasks, and this one could eventually facilitate Star Wars-like holographic video.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Social media is kind of depressing. On one hand, we love knowing what's happening in the lives of others. On the other hand, everyone seems happier, better looking, and more successful than you. We're putting on a facade by posting statuses and writing comments that present the person we want others to think we are, rather than truly expressing ourselves. Yes, social media has facilitated movements and miraculous events, but let's be real. For the most part, none of it matters.

When it comes to social media, Google has had it a bit rough. But its next big app in this category is apparently steps away from completion, with a platform that allows small groups of users to edit and organize photos in unison.

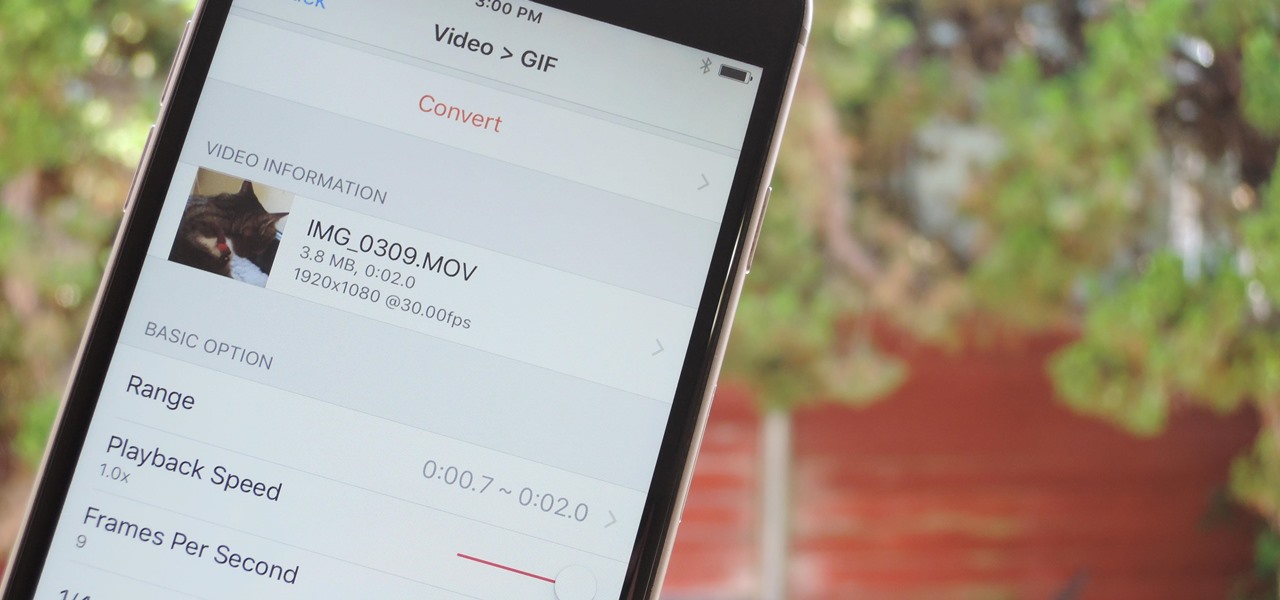
The internet has officially been taken over by GIFs—they're everybody's favorite method of communication these days, and nary a meme would exist without them. But even with the abundance of GIF-sharing websites, and even GIF keyboards, we're still a bit lacking in regard to creating GIFs on a mobile device.

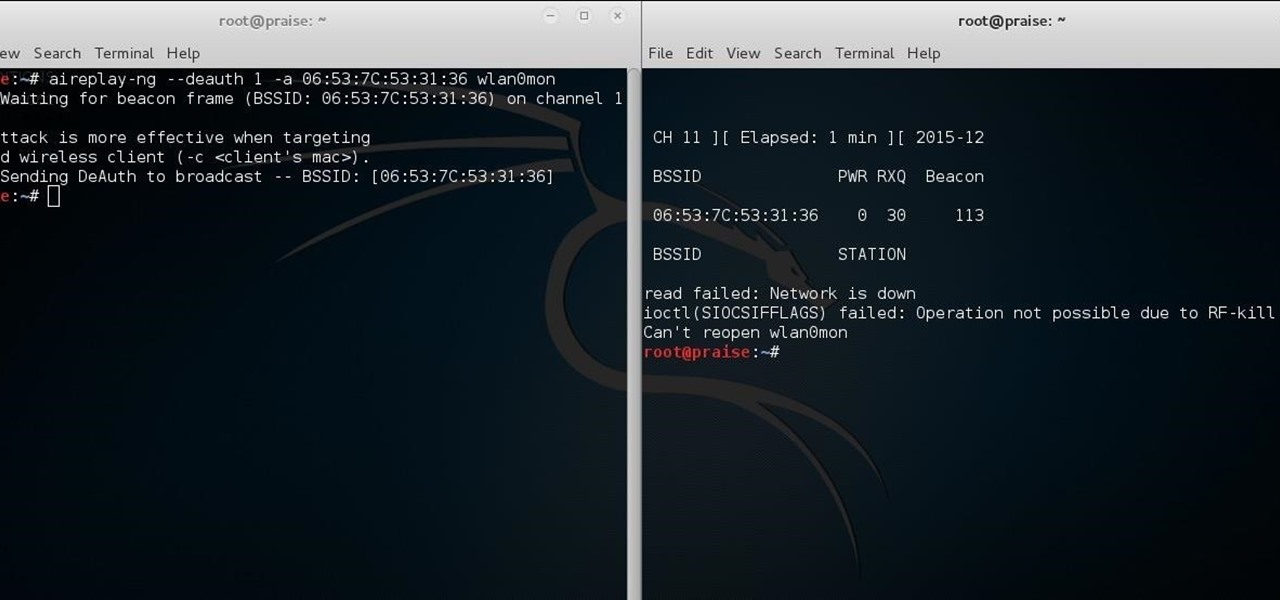
Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords.

The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.

Hello there learners and readers! I figured I'd show you guys my problem and how I solved it, hoping that it would help people who are facing the same issue. Today, we'll be talking about the solution of

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

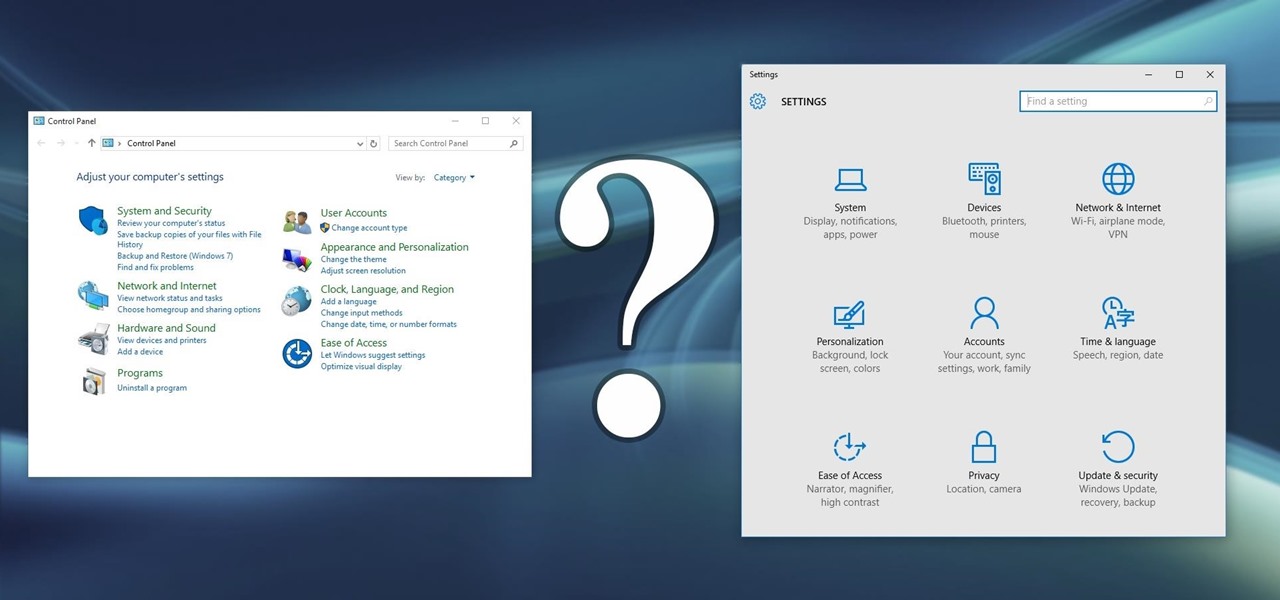
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

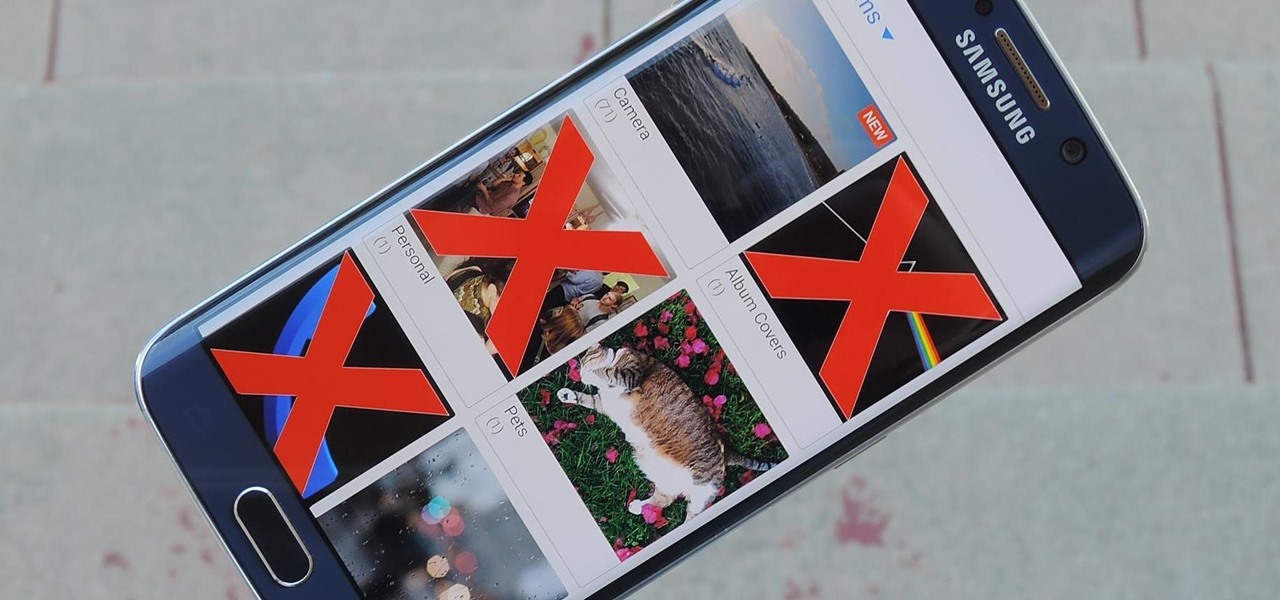
Have you ever noticed that some Android gallery apps display every last photo that you have stored on your device? This is particularly annoying when most stock gallery apps don't provide an option for hiding certain folders from your filmstrip view. Then there are music players that load up ringtones and video players that queue every video on your device, regardless of whether you want them there or not.

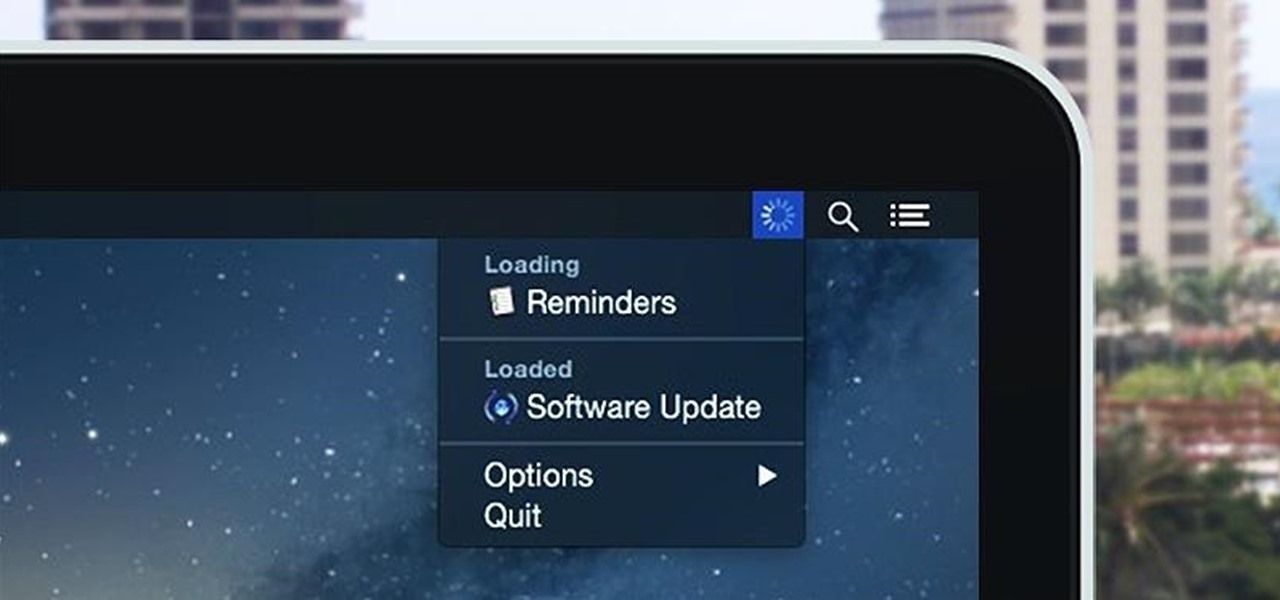
Monitoring your Mac with widgets can be the first step in identifying bandwidth issues, but finding the root of the problem can be a completely different story. Usually you will have to open up Activity Monitor in Mac OS X to look for apps hogging your bandwidth, but with Loading, you can get a detailed data usage report right from your menu bar.

Serving as the primary tool of distribution for many websites, social media is how most of us catch up what's going on around the world. While there is a bunch of clickbait going around on Facebook and Twitter, there are plenty of genuinely interesting articles being shared.

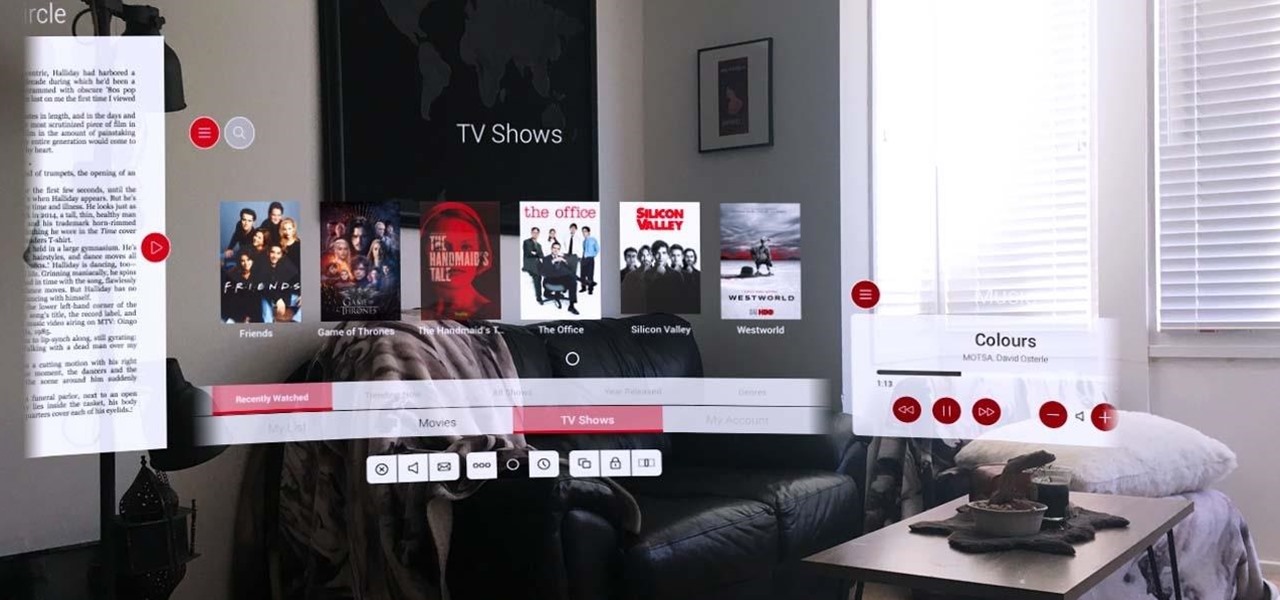
AllCast, from renowned developer Koushik Dutta (better known as Koush), allows users to stream personal media, such as movies, photos, and music from mobile devices to Chromecast and other streaming devices.

Apple's keyboard has a set of media controls to navigate the music playing on iTunes, allowing you to play, pause, skip, and replay songs and videos. Unfortunately, these controls are exclusive to iTunes; if you're playing music from Spotify, Pandora, or the myriad of other online web-based services (Amazon, Rdio, SoundCloud, etc.), you're out of luck.

Social media is constantly evolving, and as a result, we're now capable of sharing much more than we were even just a few years ago. Television, on the other hand, continues to hold strong as one of America's favorite pastimes.

As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...

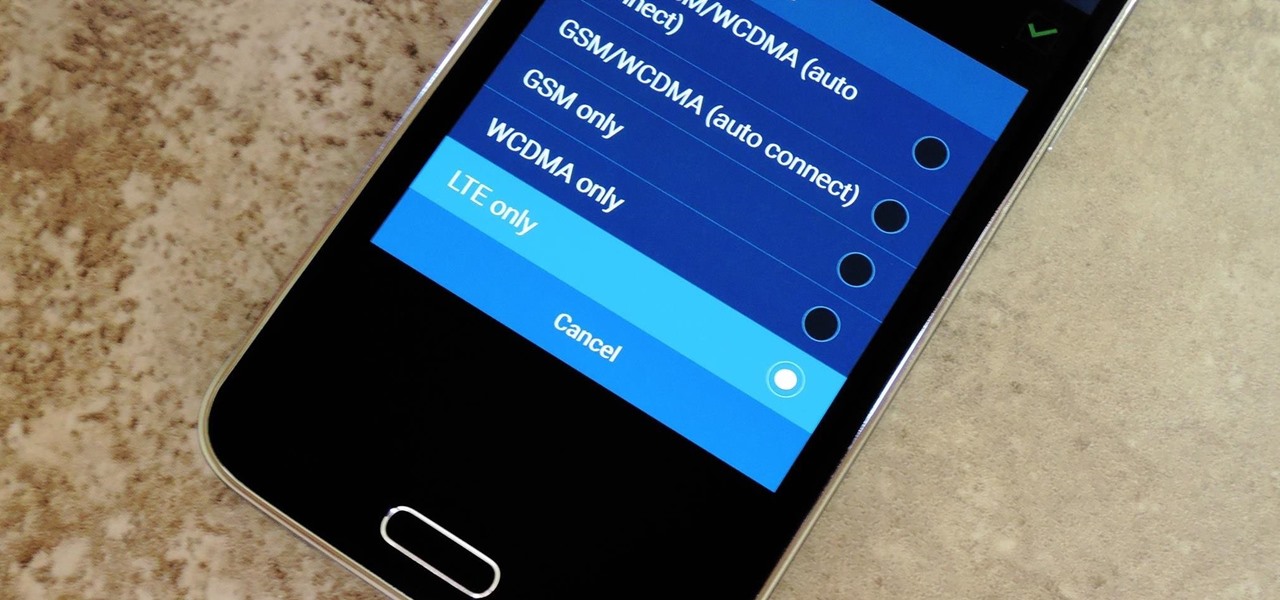
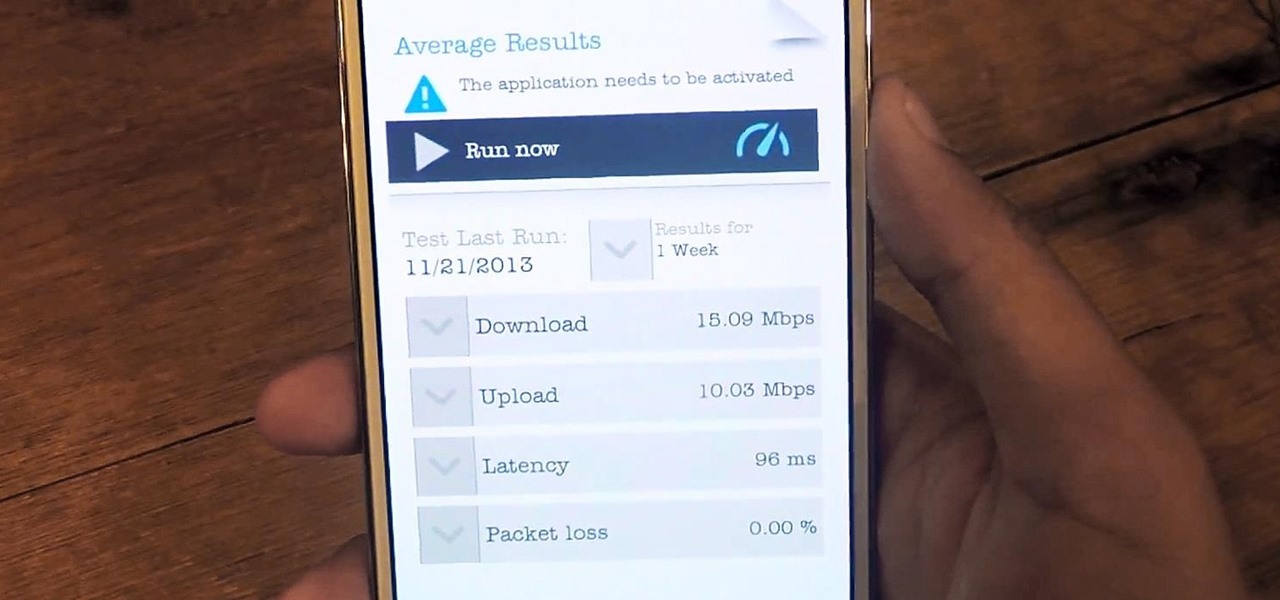
Even with the highest-tiered data plan available, there are times that your phone or your carrier might downgrade your connection to 3G or even lower. This usually occurs when you've made a phone call, or you've switched cell towers while traveling.

Amazon's Fire TV set-top box has been out for over a month now, and the hacks are starting to come together. Sure you can play your Amazon Instant Video, Hulu, and Netflix content without any issue, but what about your personal media, like movies and music?

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

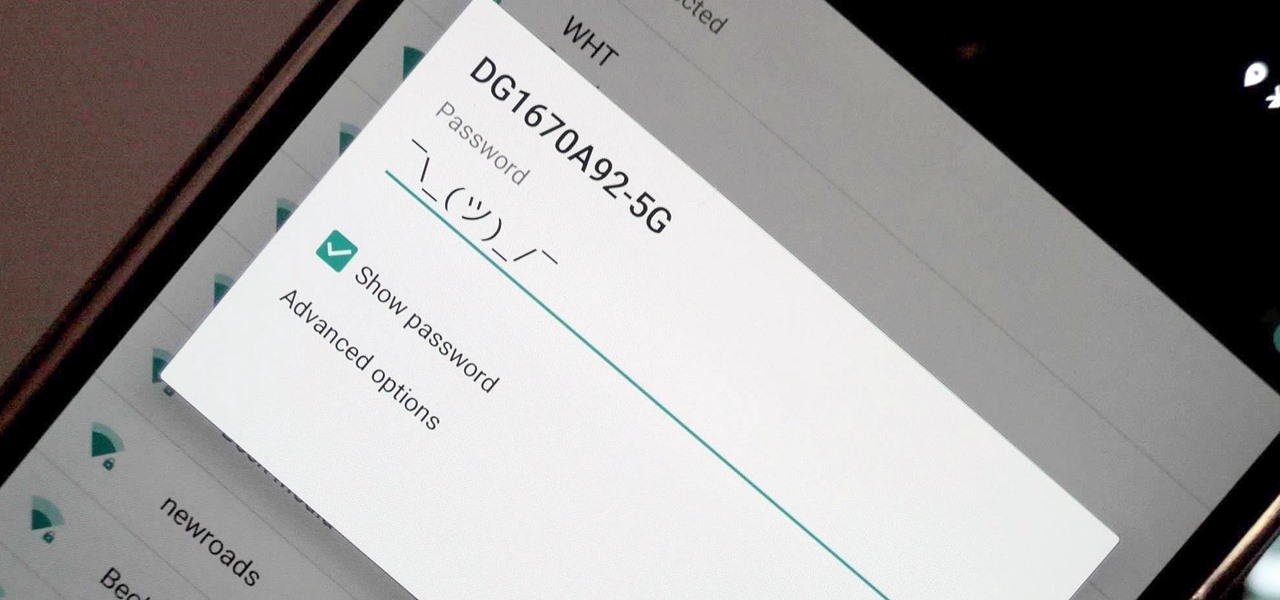
A free Wi-Fi hotspot can be a lifesaver. Whether it's because you have shitty reception, need faster connectivity, or just don't want to go over your monthly data plan, free Wi-Fi in public areas is greatly appreciated. While connecting to these free hotspots is fairly easy, finding them can become a whole nother issue. I've been in plenty of situations where I wasted my data plan instead of taking a few steps to the right, where free Wi-Fi would have been waiting for me and my Samsung Galaxy...

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

In the Windows 8 Enterprise edition, you can use the Windows to Go feature to travel with Windows 8 OS, personal files, documents, settings and many more. All you need is an external hard drive or USB drive of 32 GB space or more and USB 3.0 support or more for fast Windows 8 booting. We need the storage media of above specification to create bootable USB to access the data anytime by plugging the media into different PC running latest version of Windows 8 PRO or Windows 7.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

When you're at work or in class, there's nothing more annoying than sites that automatically play media. One minute you're happily distracting yourself, and the next, you're scrambling to hit pause while everyone stares at you. Not to mention now your boss knows you're slacking off.