This recipe for potatoes in a creamy yogurt sauce is just perfect for those times when you haven’t had a chance to get to the grocery store for fresh vegetables. The hardest part out of the entire recipe is boiling the potatoes. With the red of the tomatoes in the gravy and the green of the cilantro garnish, it is a visual treat. Watch this how to video to learn how to cook Indian style potatoes in a creamy yogurt sauce. This potato dish is also commonly known as dahi wale aloo.

Tandoori roti is another type of Indian unleavened bread which is usually made in a clay oven called a tandoor and commonly enjoyed with chicken, lamb, mutton or other non-vegetarian dishes. Vegetarians out there, don’t worry. It tastes just as fabulous with vegetarian curry dishes as well! Watch this how-to video to and try this easy to make at home recipe and method. You won’t need to run out and buy a tandoor!

Daal makhani has a lot of different names. It is also known as kaali (black) daal or maa ki daal. It is a very typical dhabba dish and has a fantastic flavor. Watch this how to video and learn how to make Indian dall makhani.

How to set up and install a wireless router for your home computer network.

"What's your Wi-Fi password?" That's usually the first thing guests ask for when you have them over. You tell them the network name, then try to explain your complicated hacker-resistant password, which becomes a whole ordeal. But there's a better way to do it, which doesn't rely on using the same mobile OS as your guests.

You're out and about, and nothing on your iPhone will load. A glance at the settings shows a saved Wi-Fi network with full bars that your iPhone had connected to automatically, but you're not getting any internet. If you've experienced this, you're not alone, and there's something you can do about it. You'll even increase privacy and security on your iPhone in the process.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

While Snapchat had a head start in making augmented camera effects popular on smartphones, Facebook has spent the past few years in hot pursuit, with no less than three apps offering mobile AR experiences, plus its Portal hardware lineup of smart home devices.

When it's hard to hear what's being said, subtitles give you clarity where audio falls short. Thanks to Android 10, your Galaxy S20 now lets you enable a live transcription of your phone's internal audio stream, meaning you can get closed captions in virtually any app — even if the app doesn't otherwise support them.

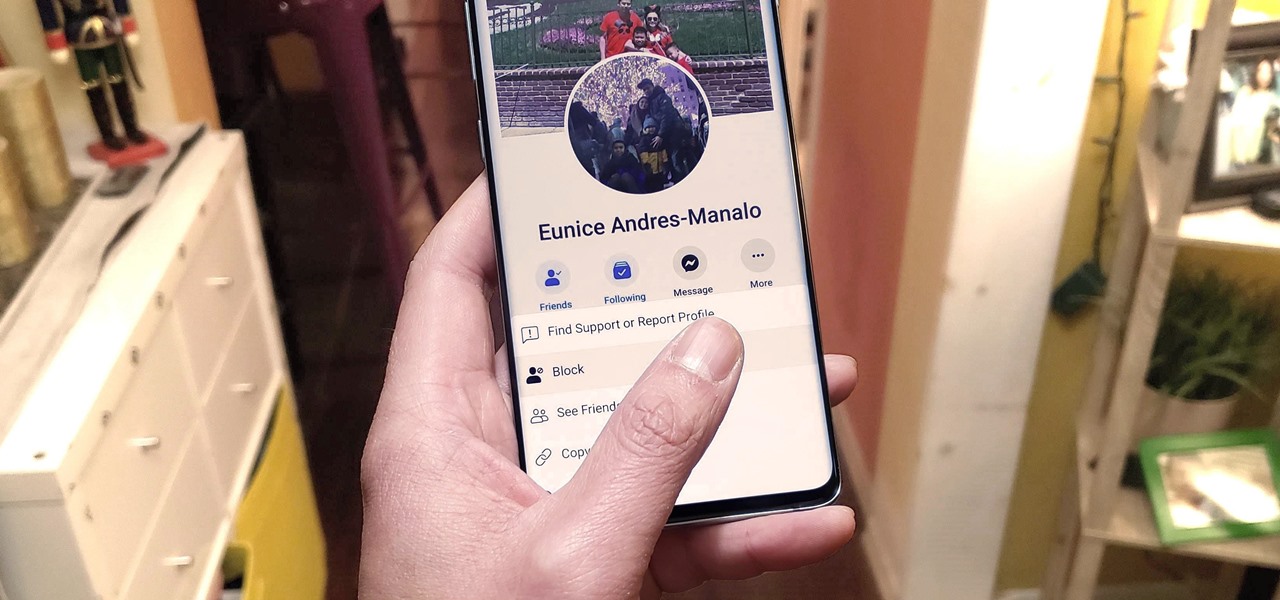
It's easy to block a person or a website from appearing in your Facebook feed, but it isn't as easy to undo that. Thankfully, there are still ways to unblock people directly from your phone.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Bus stops can provide shelter in the event of rain, and now they also protect you from augmented reality squid.

Though more well known for their OLED displays and advanced cameras, Galaxy phones like the S8, Note 10 & 10+ and S10 series are a force to be reckoned with when it comes to audio. In fact, flagships from the S9 on up feature AKG-tuned stereo speakers, along with a slew of software enhancements that make listening to music a truly pleasurable experience.

With the upcoming Memorial Day weekend serving as the unofficial start of summer, Pepsi is turning to Instagram to help sell its soft drinks to quench the thirst of beachgoers and BBQers.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

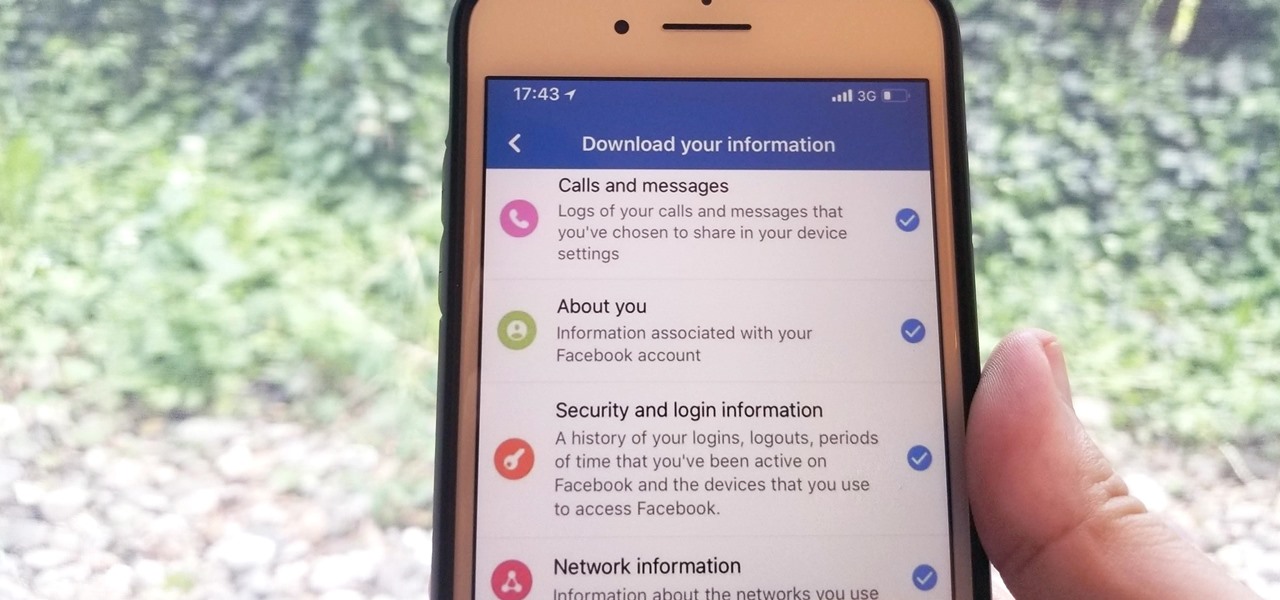
We've been able to download our Facebook data onto our computers for a while now, but now you can do so right from the comfort of your iPhone or Android phone. With it, you'll be able to integrate your data into other apps that support it or even just download it before you deactivate your account.

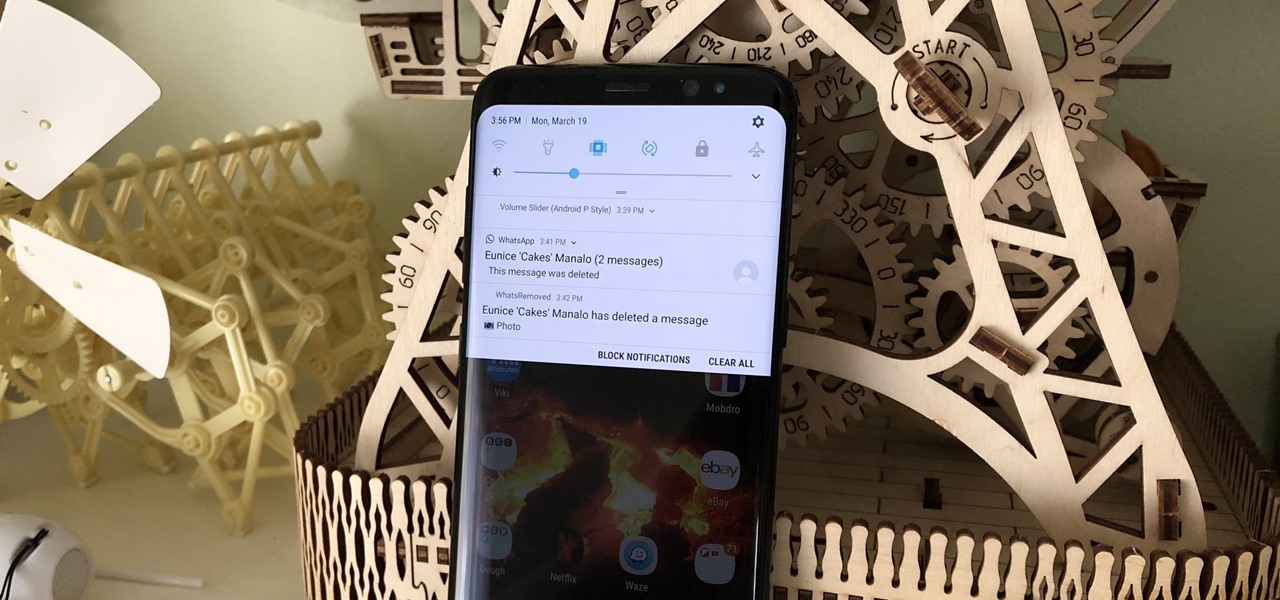
To help keep potential drama at bay, WhatsApp lets you delete questionable messages before the other person even sees them. If you're on the receiving end and you're curious about the deleted text, however, there's an Android app that lets you view erased messages.

Most Android phones don't even have an Oreo beta yet, but that's not stopping Google from releasing the preview to their next big update. Android Pie is here for developers to test, and with it, one of the more controversial additions in the Android world today — the notch.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

From media insiders to the halls of politics, news travels fast on Twitter, making it one of the most powerful social media channels for disseminating or collecting information. Now, for better or for worse, you can immerse yourself in the data firehose of Twitter in augmented reality.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

When most people first become aware of Kodi (formerly known as XBMC), they hear about its ability to stream illegal content. But the real Kodi community knows that it's much more than just a haven for pirated material — it's an all-in-one media player that addresses the majority of home theater needs, particularly for those that decided to cut the cord.

When it comes to streaming your favorite movies and TV shows, there aren't many media players that are better than Kodi. With its fast performance and easy-to-use interface, it is definitely one of the best options. But what really sets it apart is its ability to add functionality.

More prescriptions for antibiotics are written for ear infections than any other type of infection. A new study comparing the incidence and causes of ear infections in children between the ages of six months and three years found that the incidence of ear infections over the last decade has dropped significantly since the 1980s.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

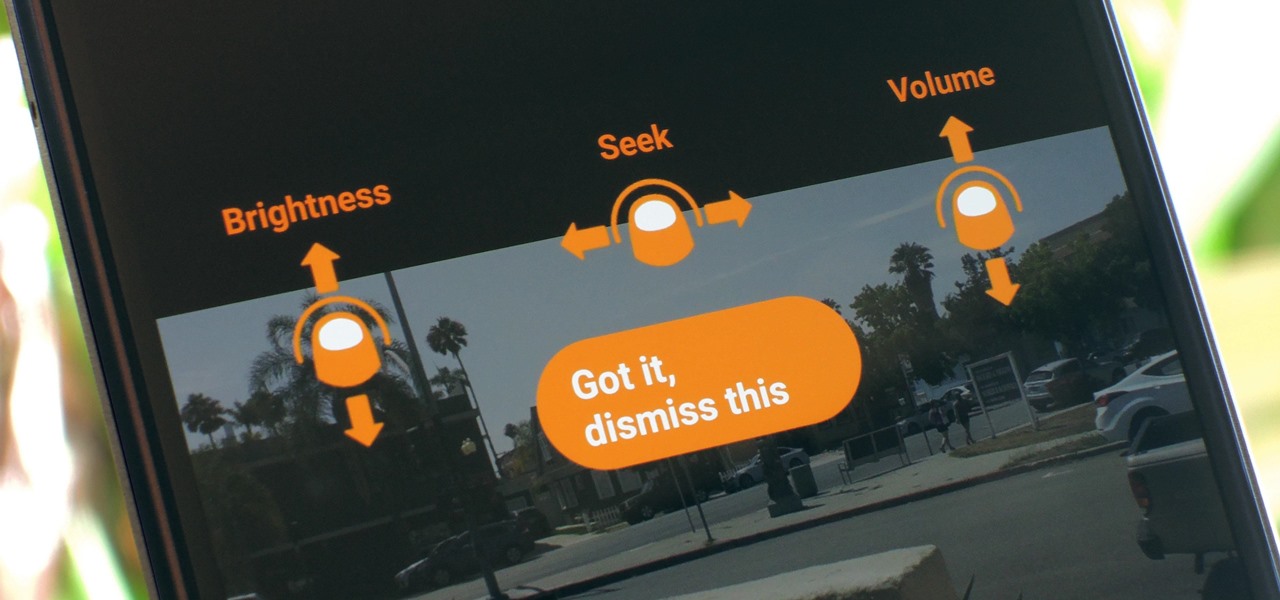
For a long time now, VLC has been the go-to media player for Windows and Mac — but it's fast becoming the best third-party video player on Android and iOS, too. Aside from its ability to play virtually any file type, one of VLC's best features on mobile is the fact that you can control playback using simple swipe gestures.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

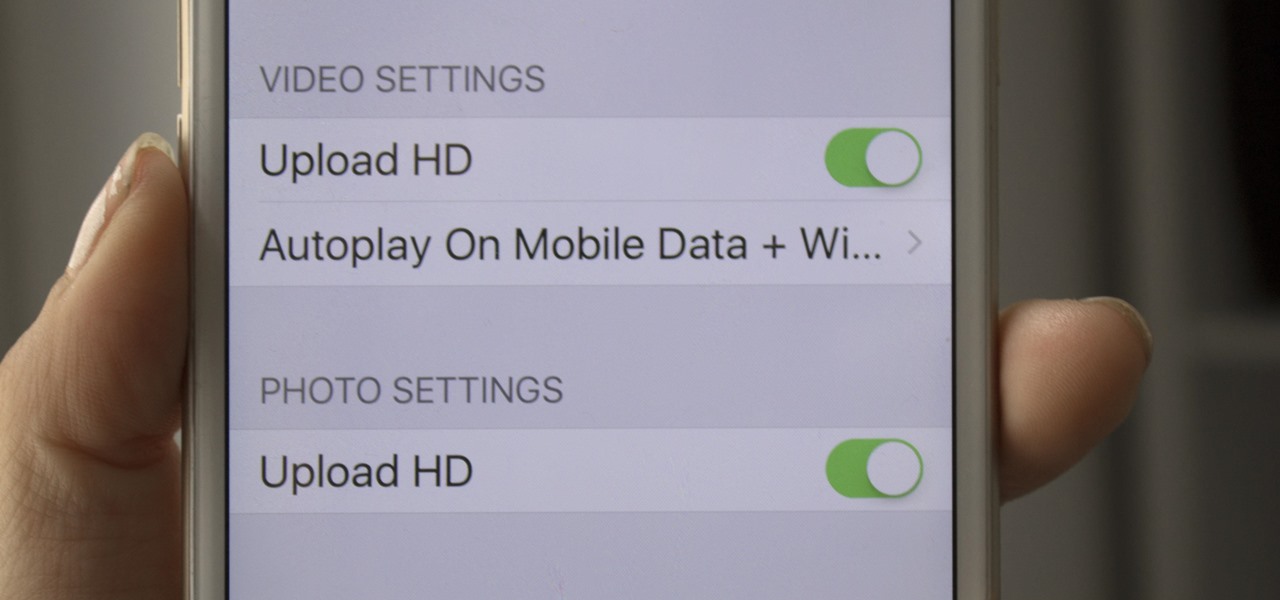
If you are a frequent poster on Facebook, then uploading your photos and videos in HD is essential for your viewers. There's nothing worse than realizing that the Boomerang you just uploaded is grainy and probably won't get any views.

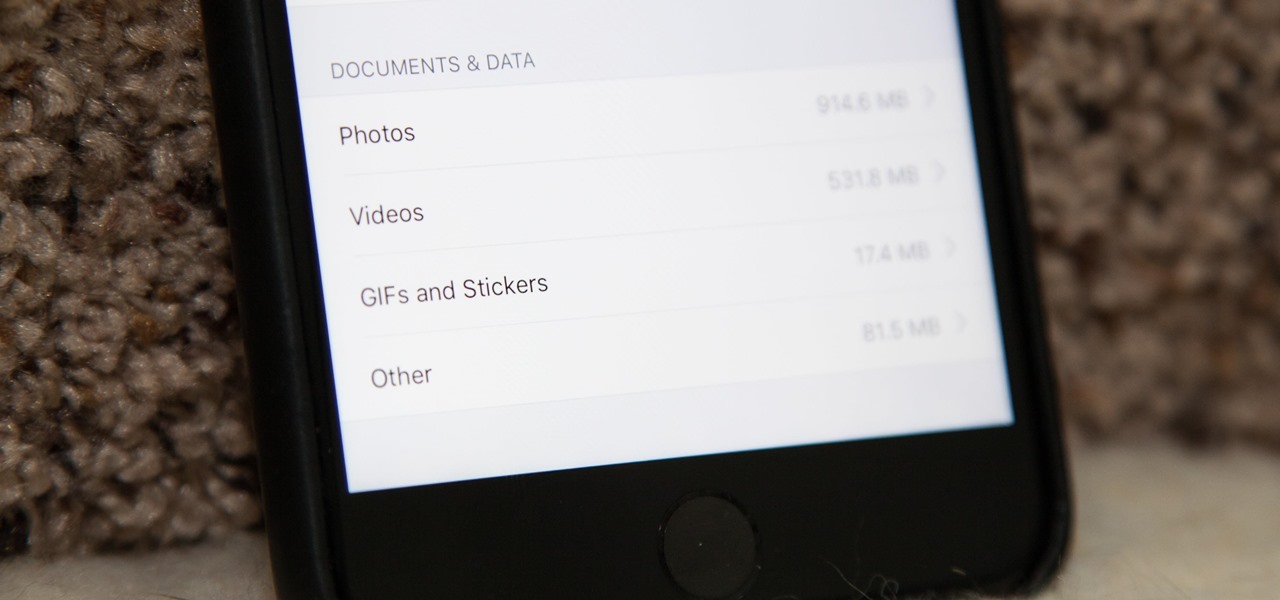
One major iOS 11 improvement that Apple skimped out on during its WWDC presentation was the redesigned storage management system, which makes it easy to view storage consumption in greater detail on your iPhone — and even easier to free up storage space with surgical precision.

What companies do you think have a unique and compelling take on social media? Wendy's is certainly confident, to say the least. But Lufthansa Airlines is taking a different approach than most — and it seems to be working — as they give passengers a look behind the scenes through Snapchat Stories.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

For the past couple of years, random internet dwellers have embarked on an ambitious quest to see just how useless a box can be in hopes of earning sweet, sweet internet points. Welcome to the world of useless machines.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

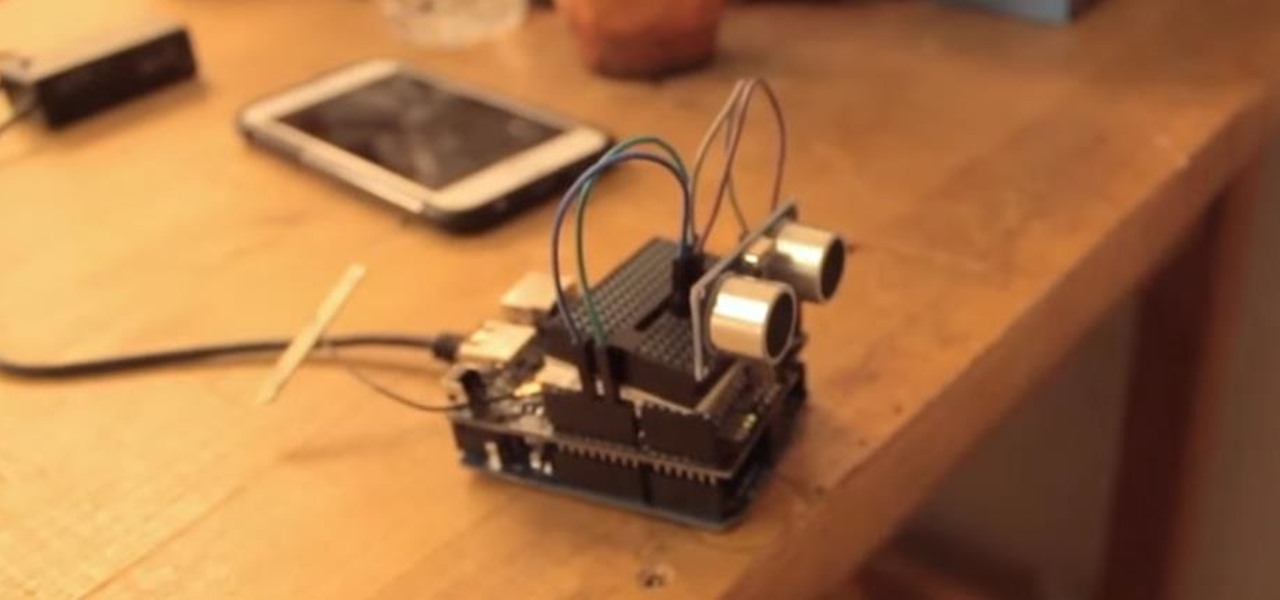
This tutorial shows you how to create an intruder alarm that sends you text message alerts when motion is detected. This may sound complicated but I am pretty confident any beginner with electronics should be able to do this just fine. The range sensor senses motion and tells your Arduino board to send the text (SMS). So you can leave the intruder detector at home, connected to your network, and still receive the SMS alerts, no matter where you are, as long as you have cell phone service.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Managing files can be time consuming on your Mac, for the simple reason that keyboard shortcuts and right-clicks sometimes lack the effectiveness we need. But with a simple third-part app, you can expedite the process of sharing, moving, deleting, and overall managing files on your computer.