
How To: Secure your wireless network
This is a tutorial on how to secure your wireless network. This tutorial shows you how to setup a WEP encryption key for your wireless network.


This is a tutorial on how to secure your wireless network. This tutorial shows you how to setup a WEP encryption key for your wireless network.

There's a seemingly endless list of downsides that come with the coronavirus pandemic — ranging from canceled trips abroad and sunny days spent inside to limited communication with friends and family. But one of the undeniable upsides is that there's simply never been a better time to start your own online business since most people will be working from home for the foreseeable future.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.
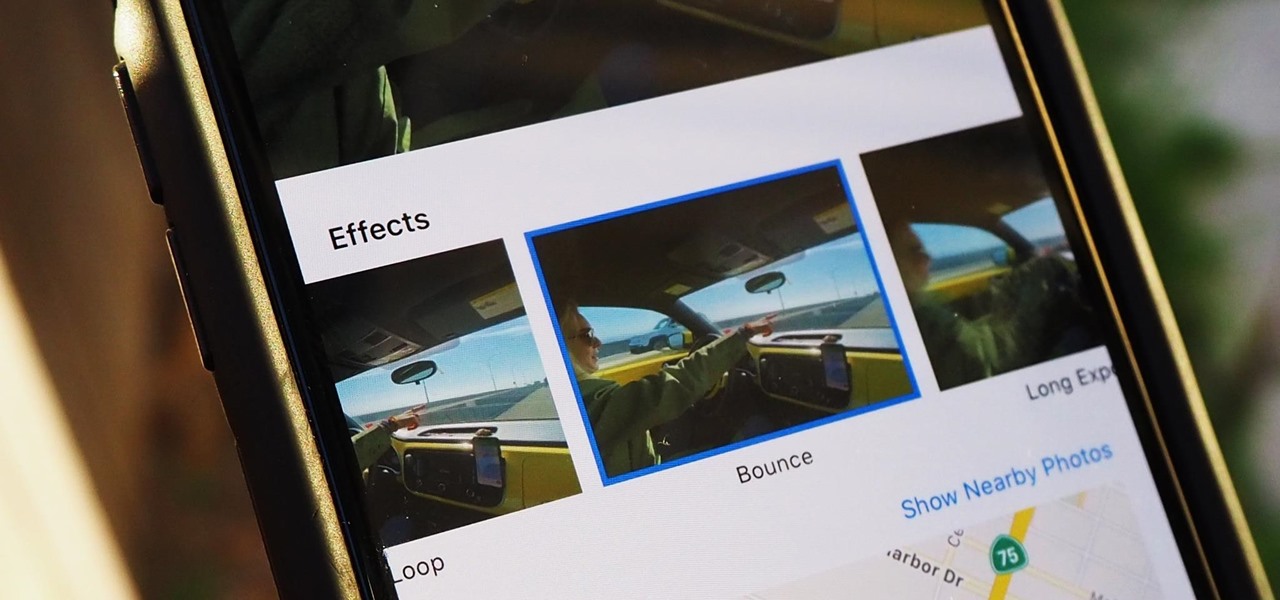
Live Photos haven't caught on as much as Apple probably would like, but they're far from the gimmick that critics initially claimed they were — and things are only getting better as time moves on. Some aspects of the feature are somewhat hidden, however, and you need to find them to unlock Live Photos' full potential.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.
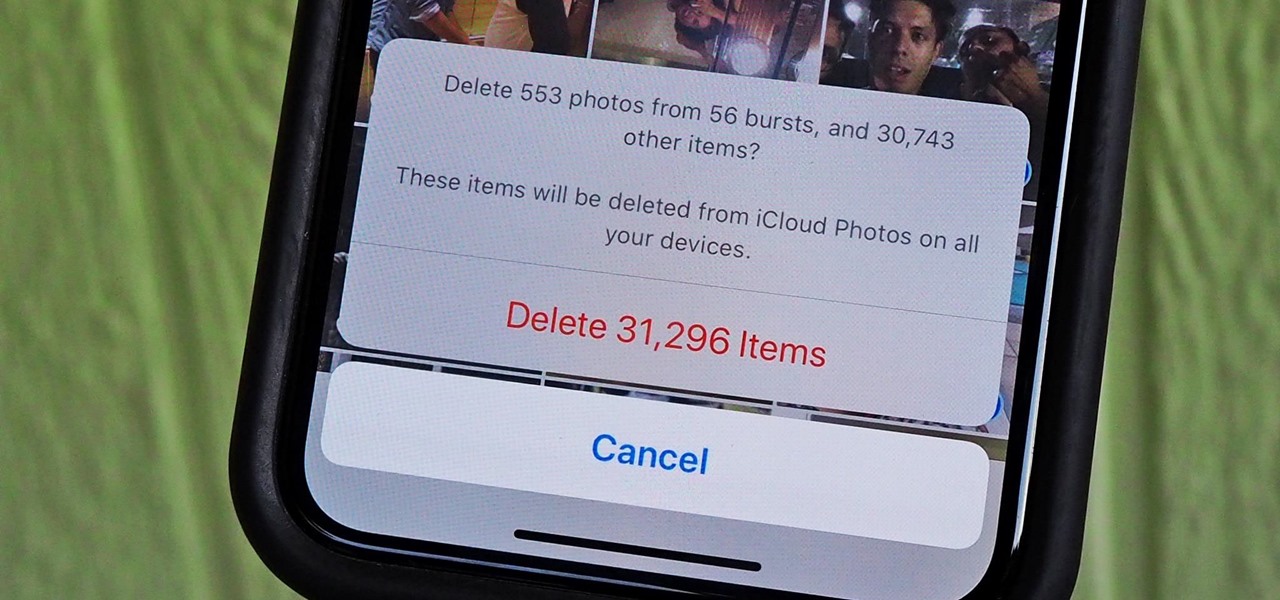
With high-resolution photos and 4K videos being standard these days, it's no surprise that media hogs most of the storage space for many iPhone users. If that's you, there's always iCloud, but you only get 5 GB free, and a paid 50 GB or 200 GB plan can fill up fast. To save money and reclaim storage, you can just delete content from the Photos app, and there's a trick to doing it faster.

With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.
Smartglasses startup Nreal enjoyed some highs and endured some lows this week, as the company landed a product placement with Kevin Bacon but then faced production issues related to the coronavirus outbreak.

In the late nineteenth century, the advent of the motion picture wowed audiences with a new storytelling medium. Nearly a century and a half later, augmented reality is establishing a new frontier in film.

It's time to make some more room at the augmented reality cosmetics counter. This week, social media giant Pinterest unveiled "Try On," a virtual make-up visualization tool running on its Lens visual search tool.
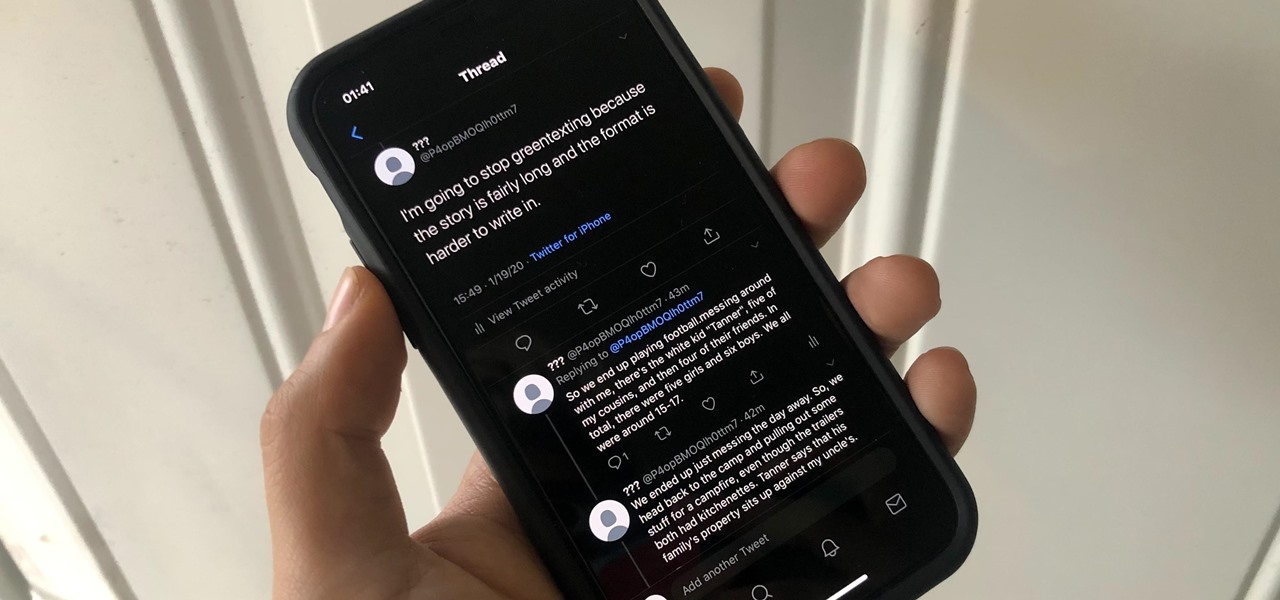
The 280-character limit for tweets on Twitter is double what it used to be back in the day, but it's still not enough to express in-depth thoughts, ideas, commentary, rants, blogs, stories, and the like. These tweetstorms, as they're called, are the reason why Twitter created its threads feature.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.
When you export an image from the Photos app in macOS, you may not be getting the whole deal. In the export menu, you need to select either JPEG, TIFF, or PNG, and if you don't make any adjustments to the quality settings, it'll likely be compressed. If you need the original full-resolution file or want to get the video that's attached to a Live Photo, there's a simple way to do it.

After establishing itself as a leader among media companies in augmented reality in journalism over the course of 2018, The New York Times pulled back from the technology this year.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.
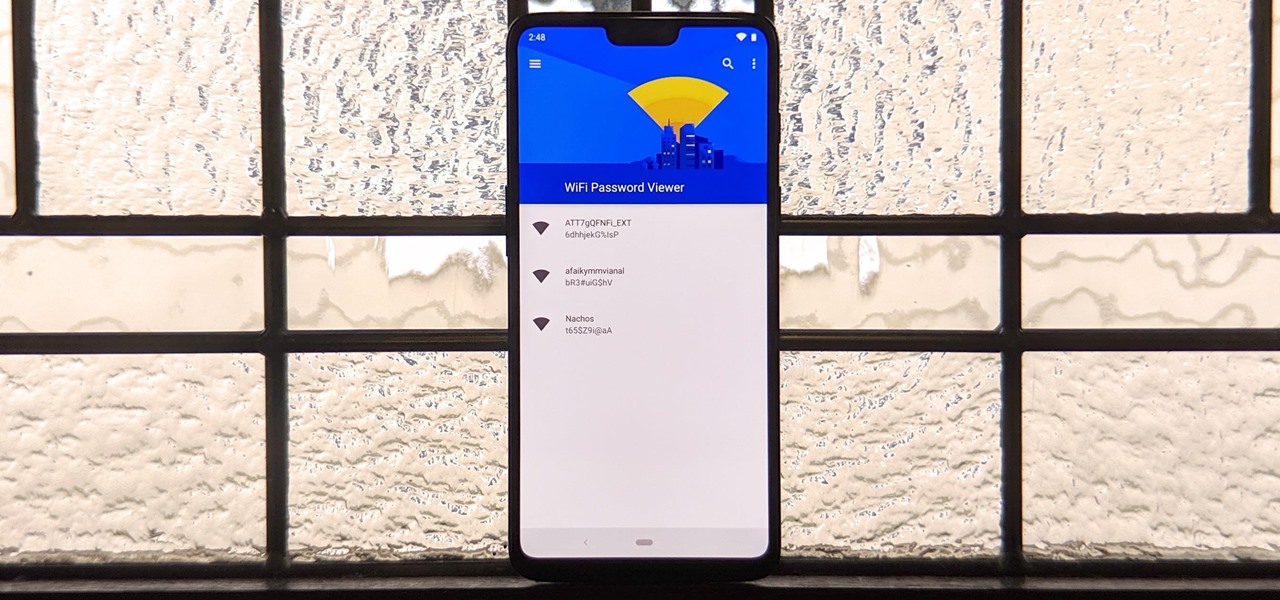
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each time you type in a Wi-Fi password, your Android device saves it for safekeeping and easy access later.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

In 2019, Sony is mixing up its design, attempting to stand out among the sea of familiarity. Instead of emulating Samsung with punch hole cameras, they decided to target a rare section of the market, content consumers. There's the Xperia 1 for those who want the best, and the Xperia 10 and 10 Plus for the budget crowd.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

Whether you've celebrated multiple cake days or you're just now getting your feet wet with Reddit, it's a rite of passage to choose your preferred smartphone client. Quick spoiler: Your best option most certainly is not the official Reddit app.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

With Pokémon GO as its cash cow and the forthcoming Harry Potter: Wizards Unite and Niantic Real World Platform promising future revenue streams, Niantic has convinced investors to bet on its flavor of augmented reality
With YouTube TV and DirecTV Now starting at $40/month, and others like Sling TV offering an eye-catching $25/month plan, streaming cable services may sound like a great way to cut costs while cutting the cord. But when you look at all the factors, the price you pay may very well end up being just as high as your traditional cable bill — if not more.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Magic Leap has already entered the realm of entertainment and enterprise, but on now it has blazed its way into a new augmented reality frontier: fashion.
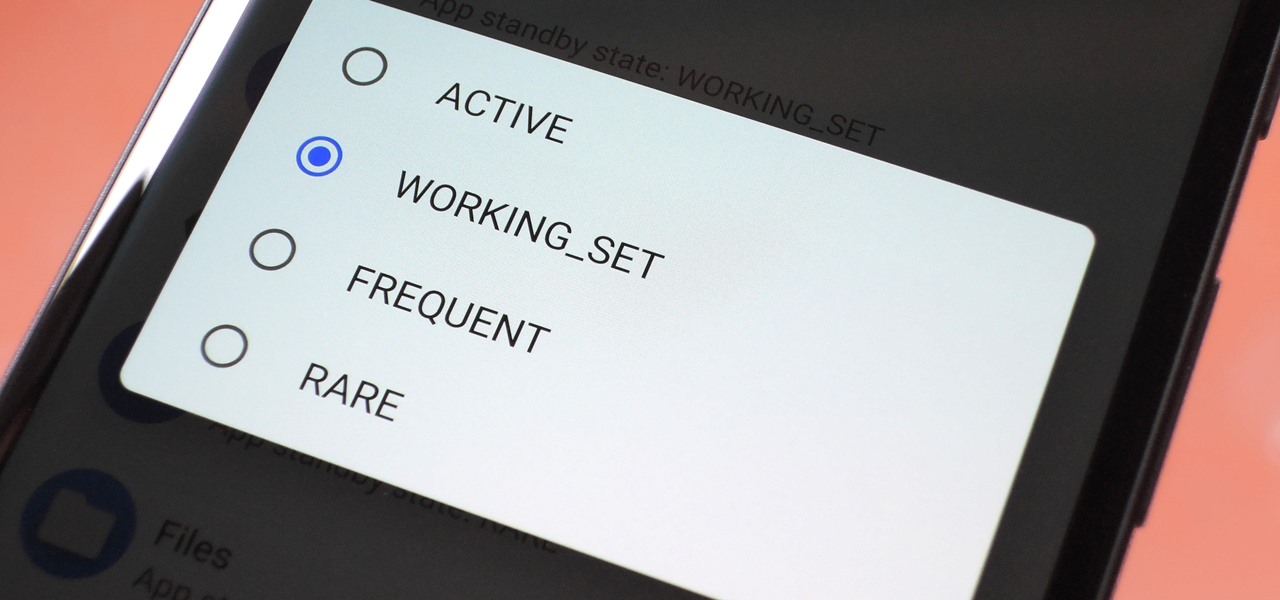
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.