We like to have a variety of cupcakes on hand when we're entertaining, but we don't want to spend too much time making separate recipes. No one has the time or the money for that—especially when you're hosting and you've got a bevy of other dishes to prepare.

Virtual reality headsets like the Oculus Rift and HTC Vive tether to desktop computers with robust GPUs in order to harness their power. The free-roaming, cordless Microsoft HoloLens forgoes those chains but loses a bit of graphical processing power in the mix. However, a recent report suggests we may get the best of both worlds.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

You've likely seen some impressive art carved out of a bush or tree before that looked like it required a lot of work and skill to create. While that may have been the case in the past, software engineer Javier Davalos used the Microsoft HoloLens to turn a bush into a perfect topiarian sphere with no training whatsoever.

The Weather Channel, by virtue of its name, has always been tasked with the difficult problem of making the weather interesting. As Mashable notes, they've turned to augmented reality for a solution and can now render a 3D storm in their studio, as well as help us understand how bad a storm might be with 3D forecasts.

Wait, don't dump that milk! It may have a slightly sour smell and be expiring tomorrow, but you can still put it to good use by making sour milk jam.

Knives are among the most important utensils in any kitchen; it's hard to even conceive of cooking a decent meal without them. However, many different foods can be prepped without a knife, and some are actually better off without one. If you don't believe me, then check out these 10 creative methods for chopping, peeling, mincing, and slicing knifeless.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Knowing if your meat is cooked properly is both the difference between a delicious meal and an inedible one... and the difference between making your guests sick and keeping them safe.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

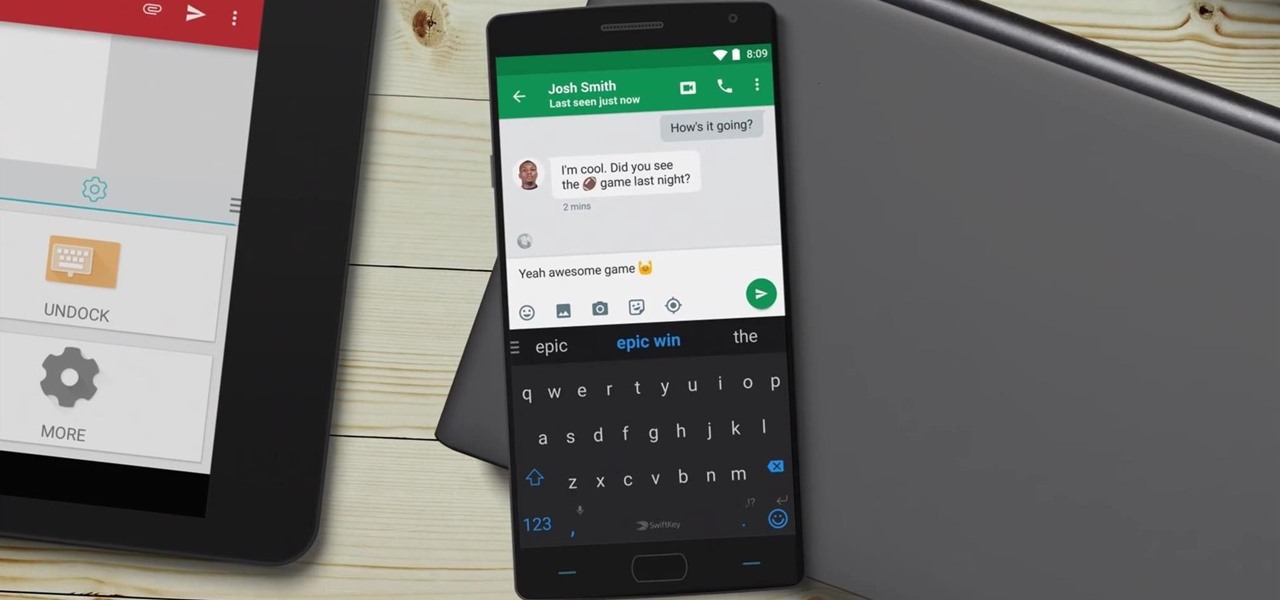
Microsoft announced Wednesday morning that it has entered into an agreement to acquire SwiftKey, makers of the SwiftKey predictive keyboard and its SDK that runs on over 300 million Android and iOS smartphones, for about $250 million.

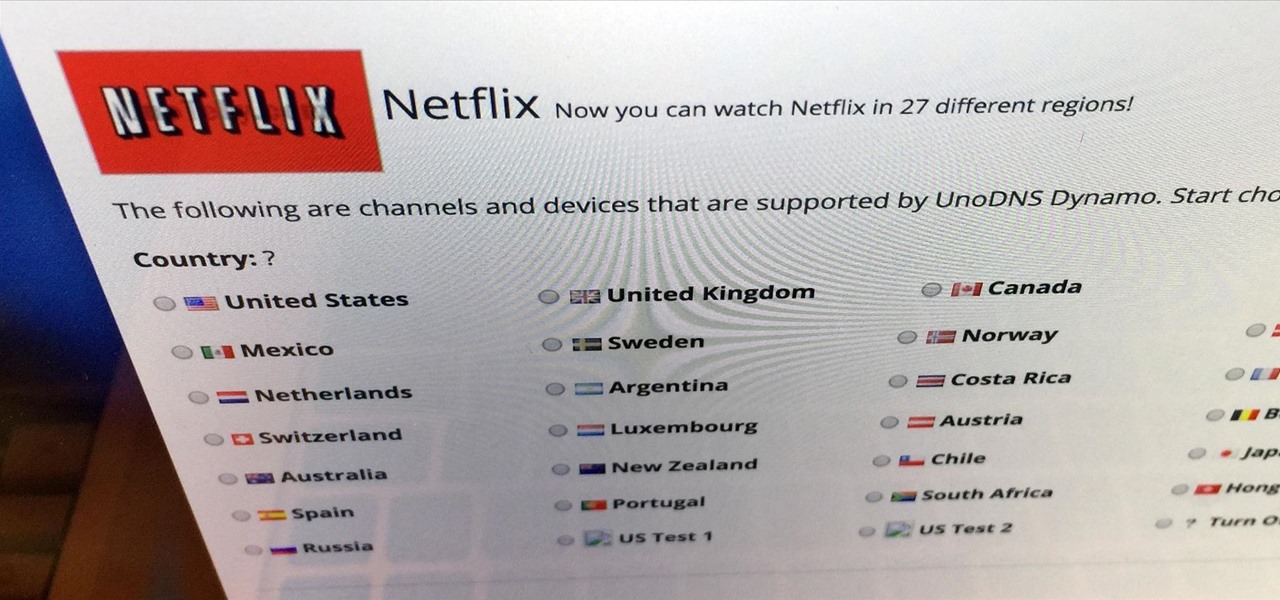
Netflix subscribers (or friends of subscribers) have been able to utilize a virtual private network (VPN) or proxy service to gain access to content in other countries. Unfortunately, the movie and TV streaming service announced today that it will soon block those services so that viewers will only have access to movies and shows that are licensed for the country they're currently in.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

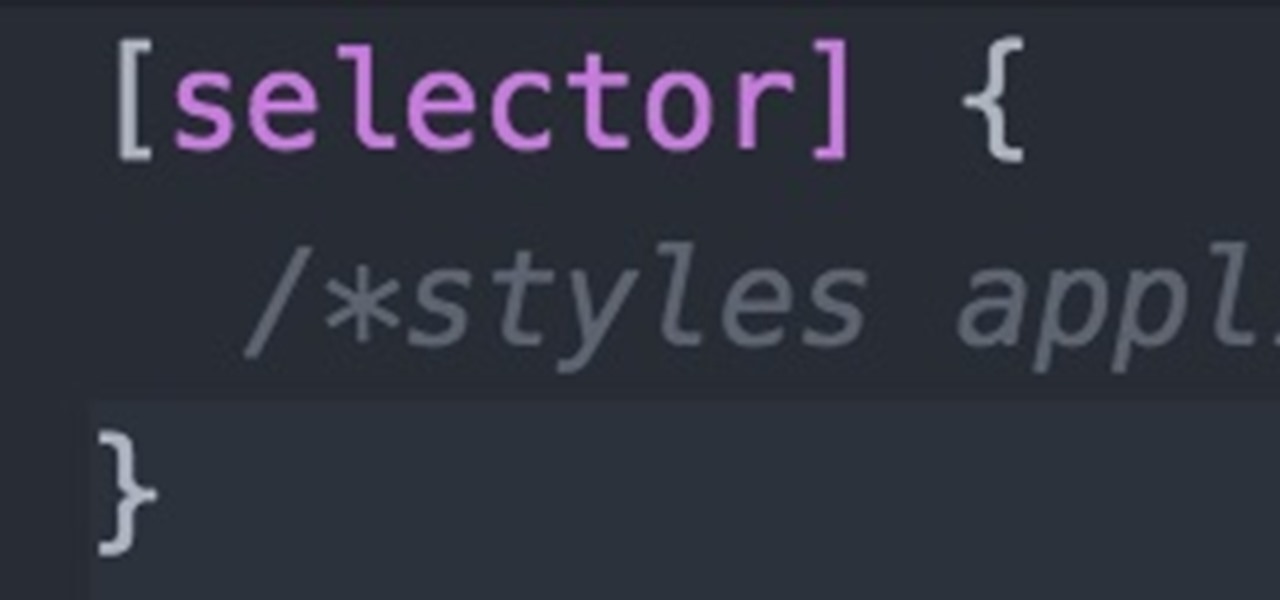
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

I recently had a small gathering of friends over for a quick cookout consisting of mostly burgers on the grill. One of my friends informed me beforehand that she didn't eat red meat, but that she would be perfectly okay with eating a turkey burger.

When I started to go to this site I found it fascinating and found myself coming here all day I have used a lot of the info I have gotten from here in my professional career and on my own. I currently am the VP of RND for a small IT company. I have been pushing toward Penetration Testing as a service for our clients and future clients. For the past 10 years here it has been a very long uphill battle and have hit a lot of road blocks. So I decided to work on this on my own of course as soon as...

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

If you have a ton of photos and videos on your iPhone, backing up to iCloud is probably a no-go since it only provides 5 GB of free storage. Yes, you can buy more storage, but who wants to do that? And what happens if you run out of storage, stop backing up, and your phone gets lost, stolen, or damaged.

Mother Nature's creativity is infinite, especially when it comes to fruit. We've got black sapote, which tastes like chocolate pudding, and Buddha's hand citron, which looks like Freddy Kreuger's digits merged with a lemon. How could she possibly top herself?

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Ever feel like you're receiving notifications way too late on your Android device? Many Android apps use Google's Cloud Messaging service to send and receive notifications, including Hangouts, Gmail, Pushbullet, Facebook, and even WhatsApp to an extent.

Most smartphone games are clichéd and mundane, but every now and then a mobile game will appear with a new concept or idea that sets it apart from all the rest. While other developers continue to regurgitate the same old "winning" formulas, developer Sebastian Goszyla is changing how we play.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

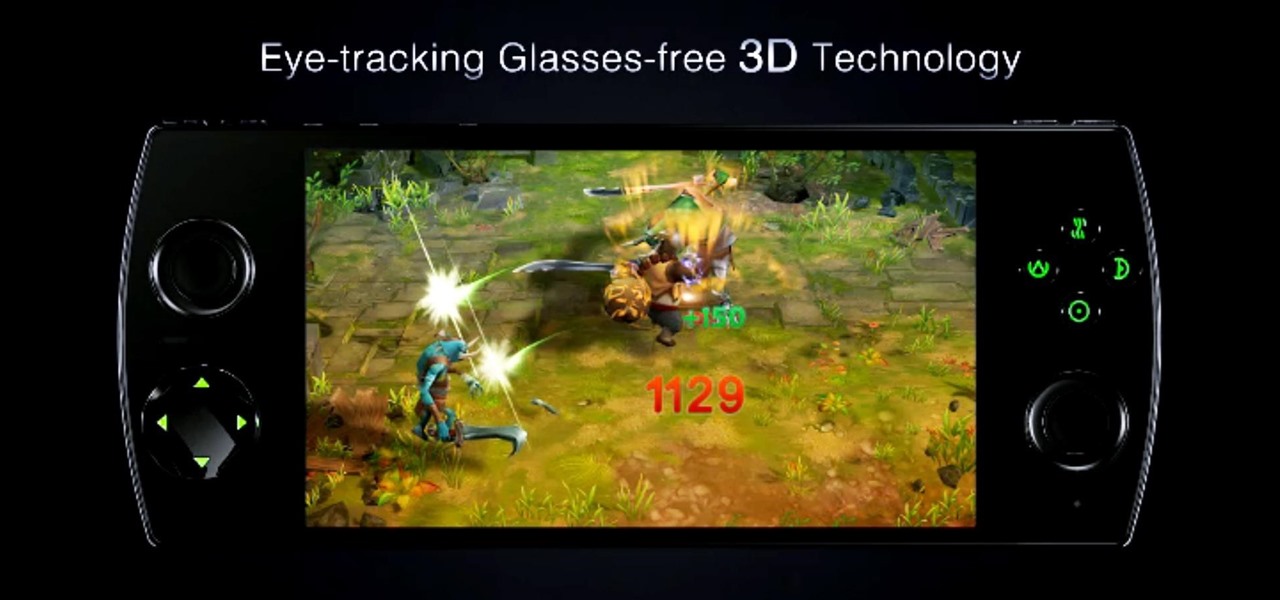
The upcoming W3D gaming smartphone by Snail isn't like anything you've ever seen before. It's pretty much a cross between an Android phone, Nintendo 3DS, and PlayStation Vita. It runs on Android, has a 3D screen similar to the 3DS, and gamepad controls like the Vita, making it one hell of a portable gaming device (that's also a phone).

As competition for Spotify and Pandora, Samsung released Milk Music earlier in 2014, a free music streaming service for their Android devices. While Milk was unique to Galaxy owners only, it was popular enough that we showed you ways to get it on non-Galaxy devices as well.

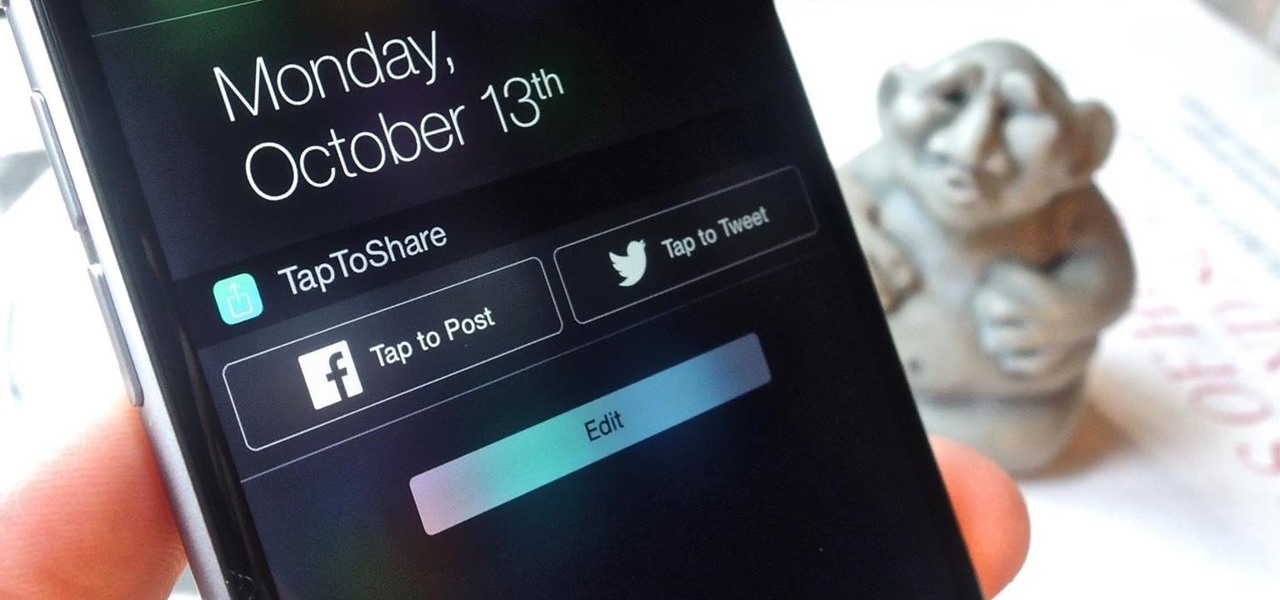
Back in the days of iOS 6, iPhone users were able to send a quick tweet from their notification center, but that has long since been removed. This convenient feature was missed enough on iOS 7 for devs to create a jailbreak tweak in its absence. Thankfully, due to the new widget capabilities of iOS 8, we can have Twitter back in the Notification Center along with Facebook.

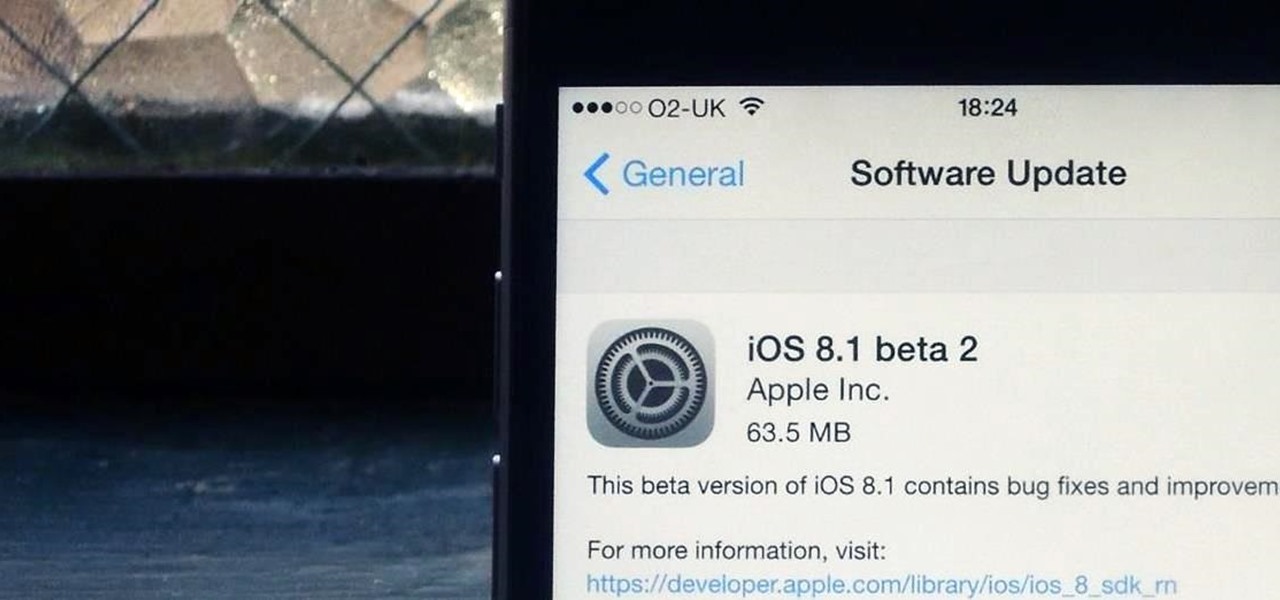
Shortly after Apple's iOS 8.0.1 update fiasco ruined many iPhone users' cellular reception (which was fixed with iOS 8.0.2), developers were treated to the first beta release of iOS 8.1, which will be the next big update for iPad, iPhone, and iPod touch.

Contrary to what you may think, clearing or swiping away apps in the Recent Apps view on your Android device does not necessarily stop app activity or running tasks—and these running processes can actually be eating away at your battery life. Depending on the app or process, it may only be a small percentage, but every little bit helps these days.