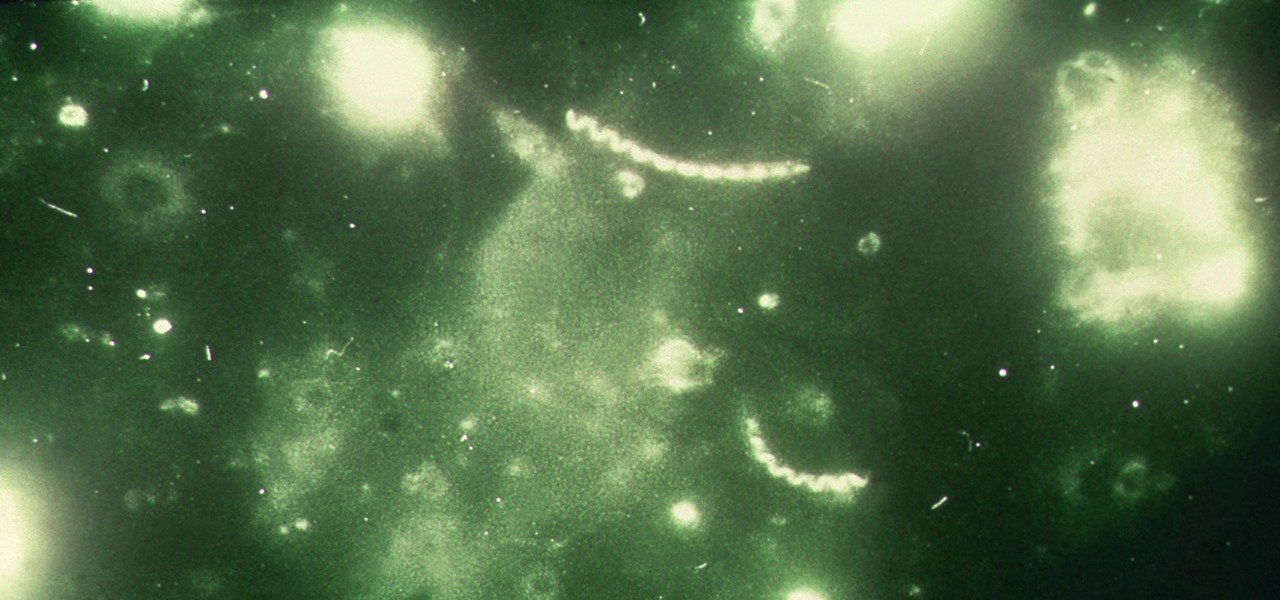
Using extreme time-lapse microscopy, scientists watched a virus take over a bacteria to create a cell that looked and functioned more like a plant or animal cell. True story.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.

Using mathematical modeling, researchers suggest weather and warming created the "perfect storm" that drove the Zika outbreak in 2016.
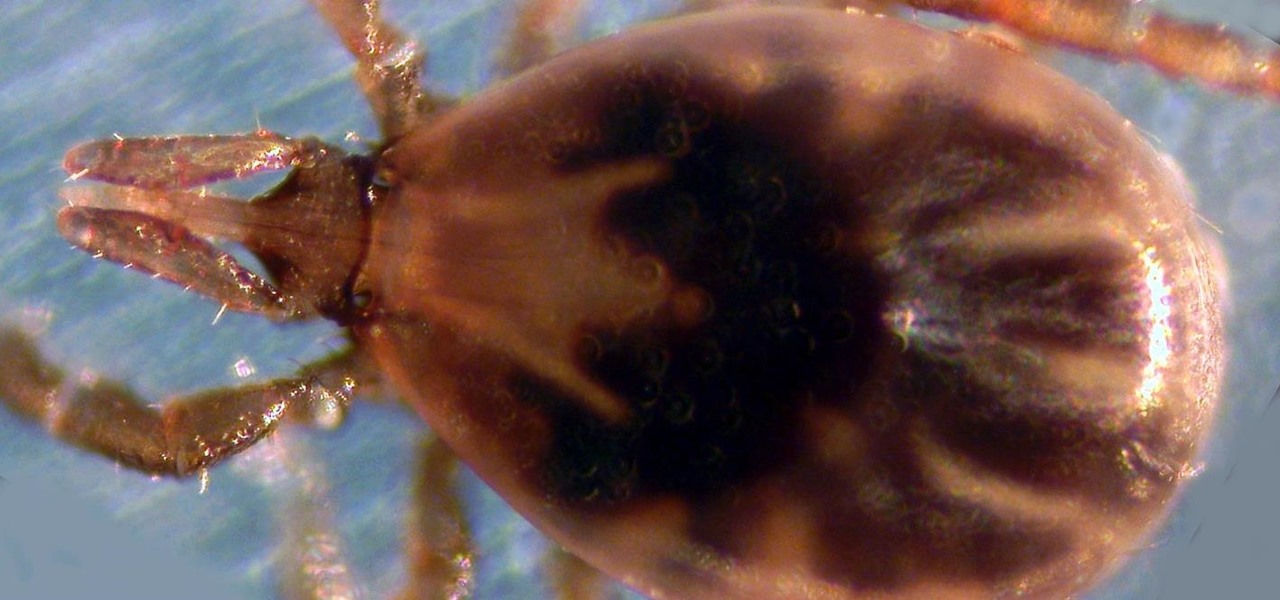
Transmitted by ticks, Lyme disease is a serious infection that is probably headed your way. A recent study confirms the pathogen that causes Lyme disease is now established in nine national parks in the East, including Acadia and Shenandoah National Parks.

What do Leo Tolstoy (writer), Beethoven (composer), Paul Gaugin (artist), and Adolf Hitler (politician) have in common? They are all considered to have suffered from the sexually transmitted disease syphilis.

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

New weapons are needed to combat antibiotic-resistant bacteria. Instead of drugs, scientists have discovered in an animal study that they may be able to harness vampire bacteria to vanquish pneumonia.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

Google's new Pixel and Pixel XL smartphones are available for pre-order right now, but the general public won't start to get their hands on these devices for another week or two. Tech reporters got some hands-on time at Google's launch event on October 4th, but camera testing wasn't allowed, and the Wi-Fi coverage at the event was too flooded for real-world performance reviews.

Fried food is the best. That's not an opinion; that's a fact, Jack. And while fried standards like wings, French fries, and onion rings are all stellar, there's no way you should stop there.

I'll admit it: I ignore expiration dates. No matter if it's a sell-by date, "best if used before" date, or even a use-by date, I don't care. I just check for signs of food decay and keep on eating.

Hummus seems like it should be easy to make, but creating that ideal creamy consistency can be pretty difficult. Often it comes out too chunky, which means your hummus won't be good for dipping into. Luckily, there is one trick that will help you create the creamiest consistency and make you never want to go near store-bought hummus again: add baking soda.

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.

One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like Pushbullet and Join bridge the gap even further by allowing you to share links, files, and messages between all of your devices.

When to throw meat away is a common question, and one I often ask when faced with meat sitting in the fridge after a few days. With vegetables, you can usually tell on sight (or with this guide) when they're past due, but meat is not as simple.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

After seeing the title of this post from me, you might be thinking, "Why did The Joker made another post on a topic on which we already have a nice sticky post?"
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.

One of my favorite things about cocktails is that they're so diverse. They can be sweet or savory, filling or refreshing. And they can take advantage of nearly any ingredient imaginable, including egg whites, smoked ice, flavor cubes, and even beer.

Many people deal with motion sickness on a daily basis, and if you're reading this, chances are you're one of them. Kinetosis can make your stomach roll, your entire body sweat, and make you feel fatigued and dizzy at even the slightest movement, whether it's related to carsickness, seasickness, or airsickness. And let's not forget the worst part—vomiting.

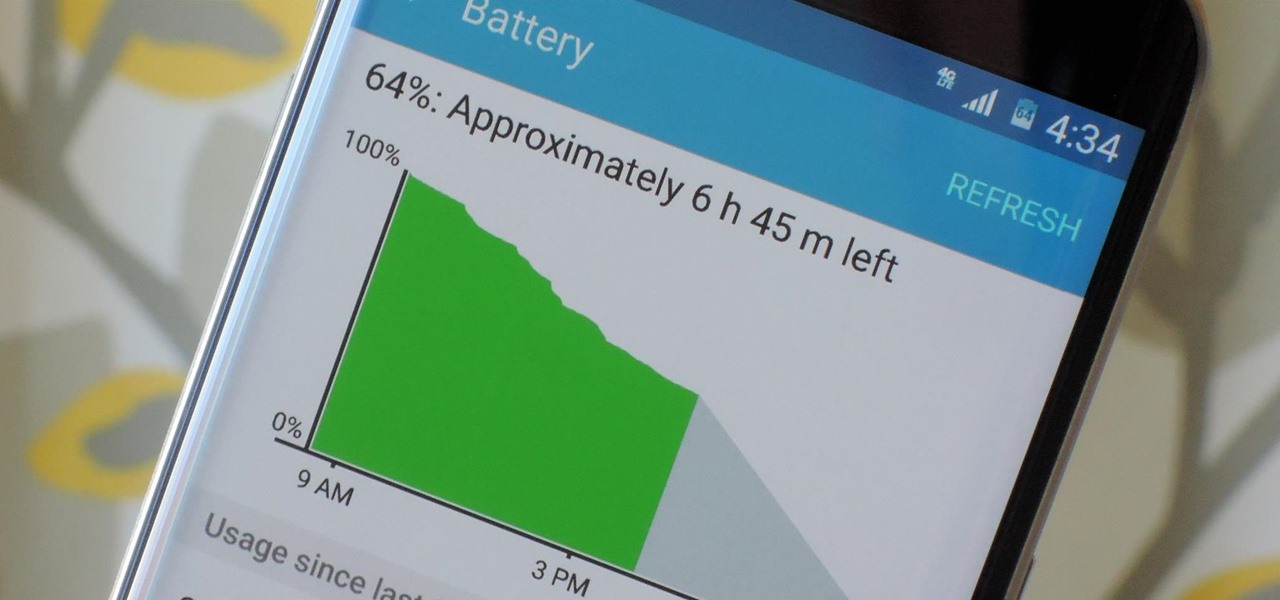
Smartphones have otherworldly specs these days, so it's relatively uncommon that you hear someone complaining about display resolution, build quality, or general speed and performance. At best, these are secondary concerns, with the number 1 issue almost unilaterally being battery life.

Samsung created quite a buzz when it debuted a built-in heart rate sensor on the Galaxy S5 back in 2014, but amazingly, not many other manufacturers decided to follow suit. It's really a shame, too, since data from a heart rate sensor would go perfectly hand in hand with the increasing fitness- and activity-tracking features that most smartphones sport these days.

Not all batteries are created equal, but one thing's for sure—they all lose capacity over time. Thankfully, the advanced lithium-ion batteries in your MacBook and iPhone are meant to last for several years before they begin to lose their overall charge capacity.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Whether it's terrorism or brain-hungry zombies you're neutralizing, first-person shooters are an awesome way to immerse yourself within a new world and kill some time with your iPad or iPhone. And with so many games available in this genre, we wanted to show off ten of our absolute favorites.

Ah, bello risotto. There are few comfort foods in the world that provide the same savory creaminess. Yet for all its simplicity, risotto has gotten a bad rap as a difficult dish to cook. In actuality, nothing is further from the truth.

Modern medicine utilizes cutting-edge technology more than ever, so it would only make sense that the powerful handheld computers we all carry around these days could play a big role in wellness.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.