Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

In recent years, medical professionals have demonstrated how the HoloLens can assist in surgeries, ranging from collarbone repairs to spinal surgeries to cosmetic procedures. Now, the largest children's hospital in the United Kingdom is also ready to deploy the technology.

While the next-generation HoloLens does not have a launch date yet, we now have a better idea of how big a leap the device will take in terms of depth sensor performance.

A peek inside the code of the Snapchat app has revealed that the company is expanding the search capabilities of its augmented reality camera to include visual search that may link to items within Amazon's massive online store.

A new set of APIs for Unity promise to make it easier for developers to publish apps that support both ARKit and ARCore.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

Earlier this year, with the Developer Preview, we got a tantalizing glimpse of Google's upcoming Android 9.0 Pie and a whole slew of new features that comes along with it, such as iPhone X-like gestures and improved security features, to name a few. With its announcement at Google I/O, Android Pie just got a lot more accessible.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

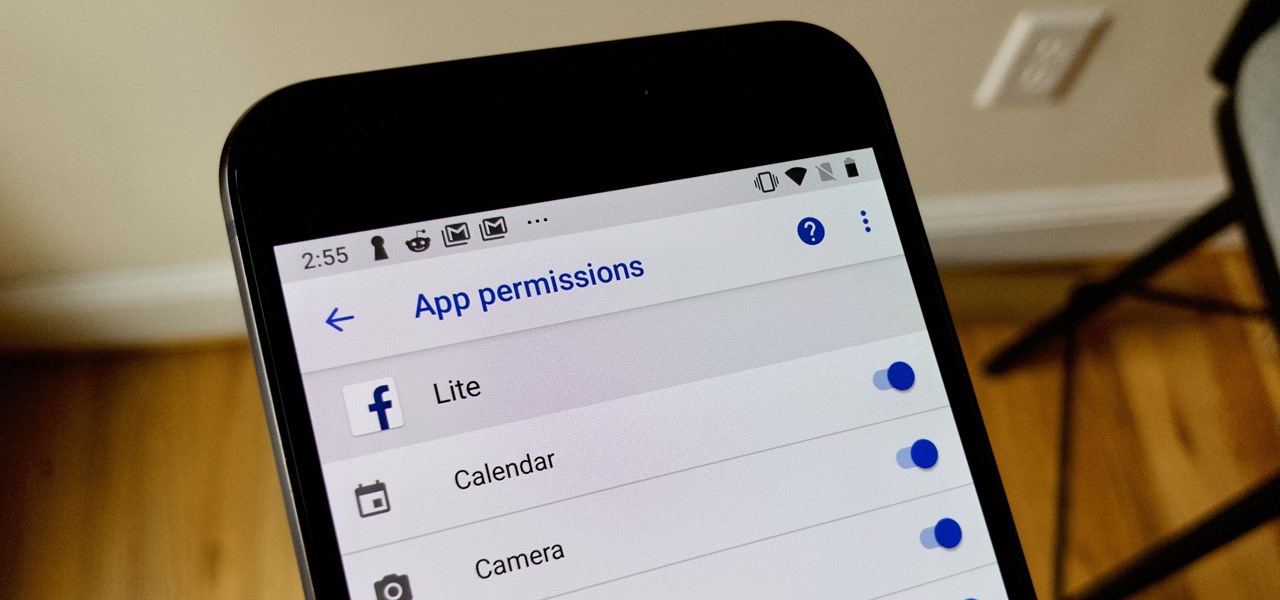
The Android world exploded when it was discovered that Facebook was logging the call and text histories of many of its users, although the company claims those users had explicitly given Facebook permission to log that data. The case remains that many users were unaware of this activity, which occurs on both Messenger and Facebook Lite. Luckily, it's very easy to disable.

Location services provider Mapbox is giving developers a means for building location-based AR apps and multi-user experiences with its new Mapbox AR toolkit.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

Following up on a preview of the deal we reported during last week's CES, Dell has officially announced the details around its role as the first company to resell the Meta 2 augmented reality headset.

Trendy restaurants are fun, but waiting in line isn't. Too often, we arrive at a location to find a queue between us and our dinner. If only we could know when wait times were down so we could go out at the optimal time.

When it comes to Hi-Fi music streaming services, Jay-Z's Tidal is one of your only choices. But as you can imagine, true High Fidelity audio requires faster download speeds than your average music service. So the question becomes, how do you listen to Hi-Fi tracks on Tidal when a speedy internet connection isn't available? Offline music is the answer.

As a long-distance runner off and on for the past, I absolutely detests hills. While there are many apps that can measure elevation and slope for certain routes, understanding spatial data on a line graph or even an elevation map can be difficult.

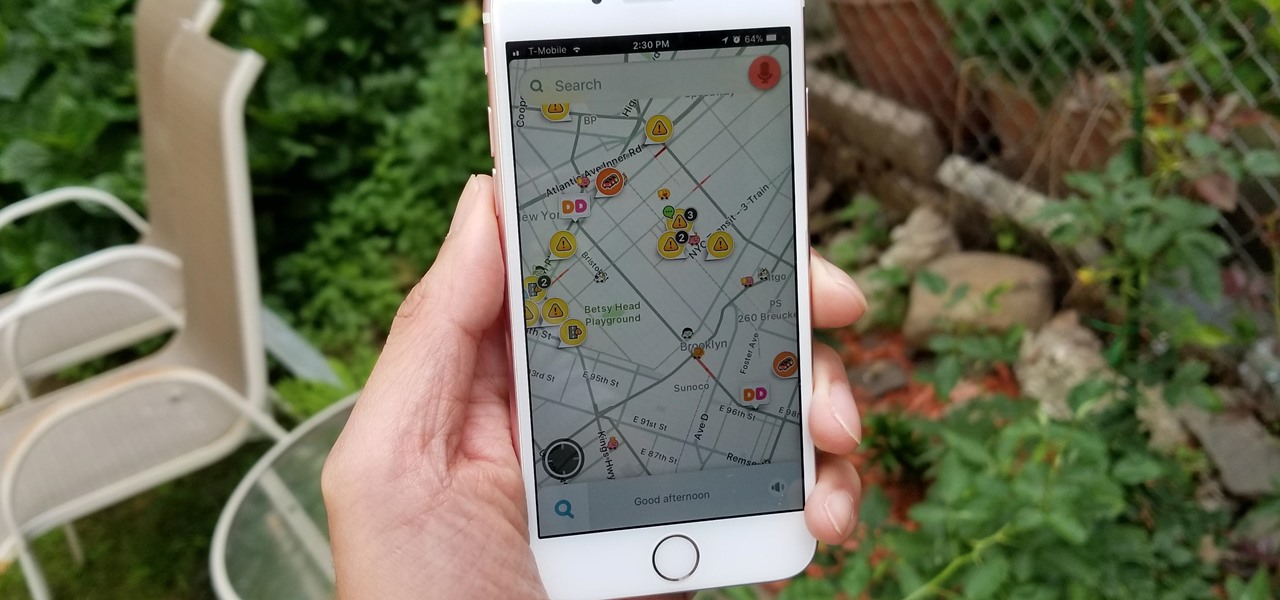
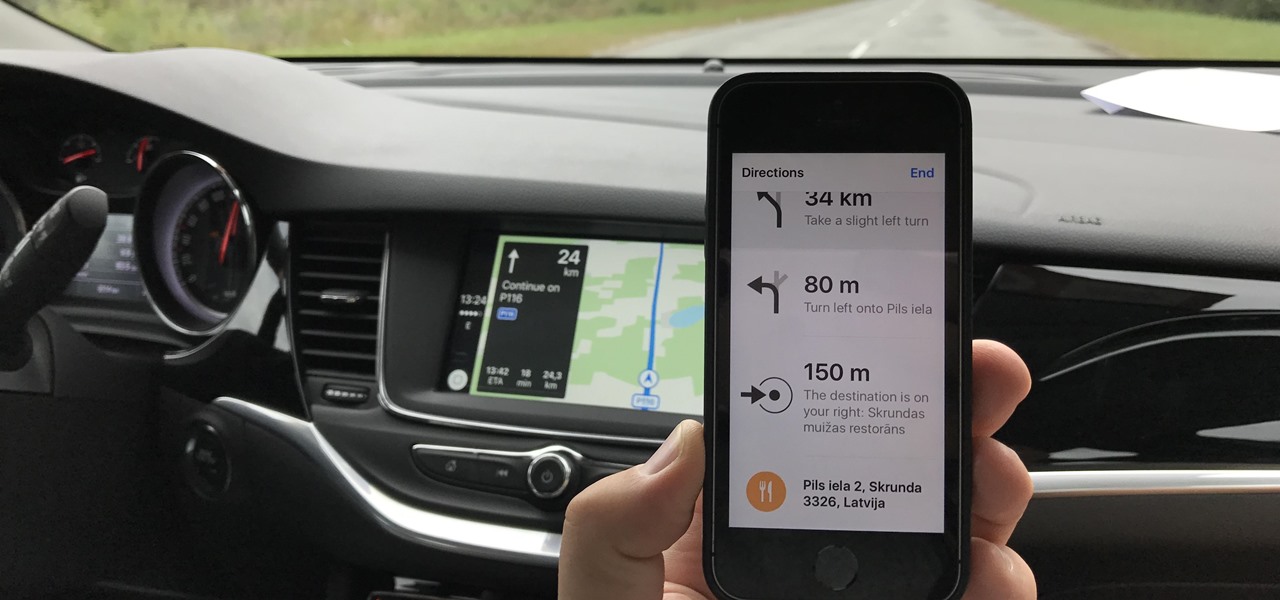
Some of the things that make Waze such a great navigation app are also its biggest downsides. Real-time data shows where individual users are, and the app automatically gathers traffic info that other drivers may encounter. These elements ensure that road conditions are as up-to-date as possible so that everyone gets to their destination safely, but it's certainly not ideal if you're a privacy-minded user.

An older man dies of Zika. A younger man who cares for him catches Zika — but doctors cannot pinpoint how the disease was transmitted. While proximity to the patient is sufficient explanation for the rest of us, for microbe hunters, it is a medical mystery. Why? Zika is not known to transmit from person-to-person casually.

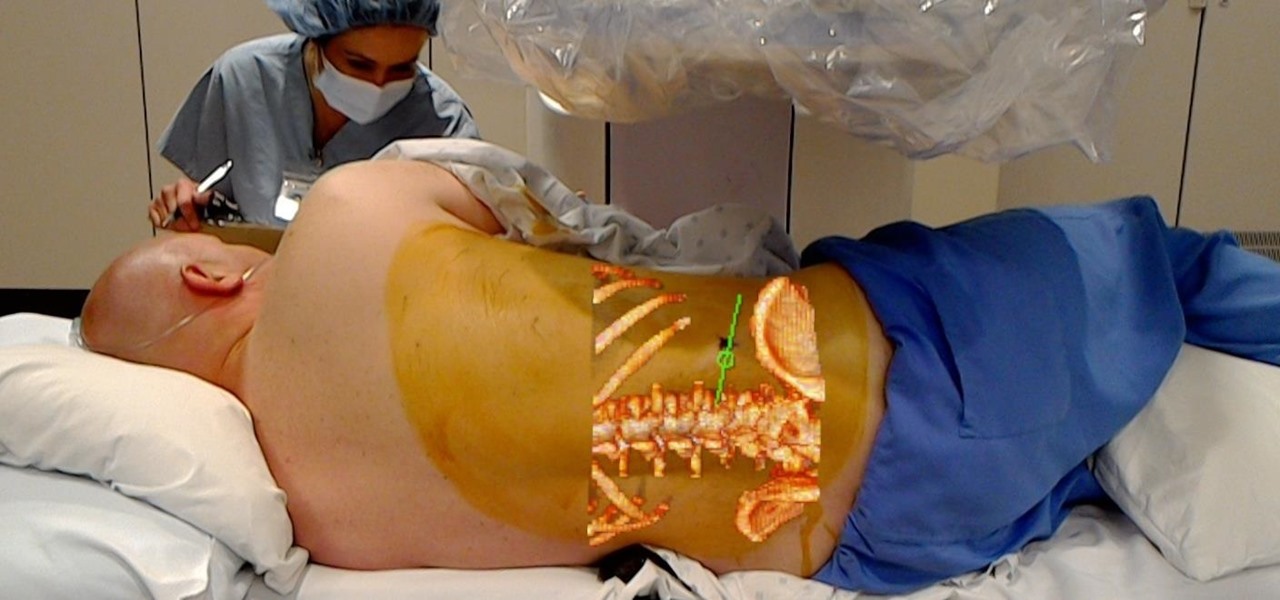
Numerous examples exist of doctors and surgeons using HoloLens to plan surgeries. The device has even been used to view reference images during a procedure and stream it to a remote audience. Until recently, it has not been used to augment the surgeon's view of the patient during a live surgery.

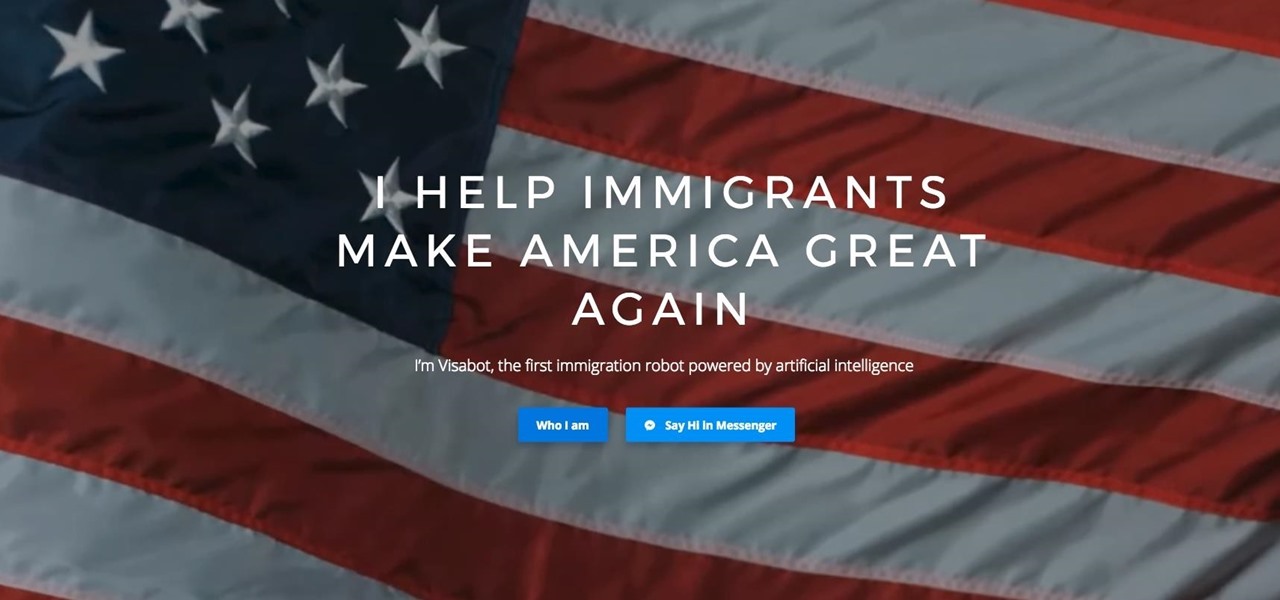
Getting your green card can be an extraordinarily complicated and difficult task. Often times it seems so daunting that it's hard to know where to begin. Thankfully, Facebook Messenger introduced "Visabot" last year, a chatbot in the app that helps with all things immigration. Now including applying for your green card.

According to the French Blog iGeneration, Apple Maps is hoping to get itself back on the map. How? By taking a page out of Google Maps' book and hiring freelancers from TryRating to manually check the accuracy of their locations.

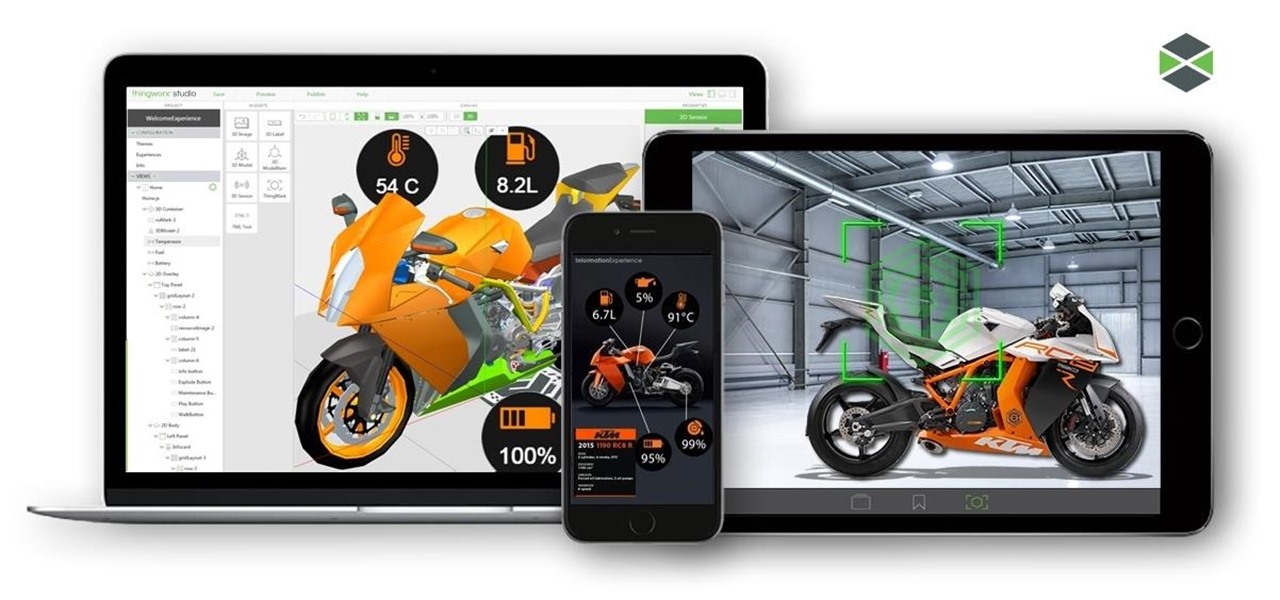
For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

Over the past eight months, ten infants at UC Irvine Medical Center tested positive for the same strand of methicillin-resistant Staphylococcus aureus (MRSA). Despite the danger of this superbug due to its high resistance to most antibiotics, this information was only released to the public on Thursday. Thankfully, all ten babies survived and are currently healthy.

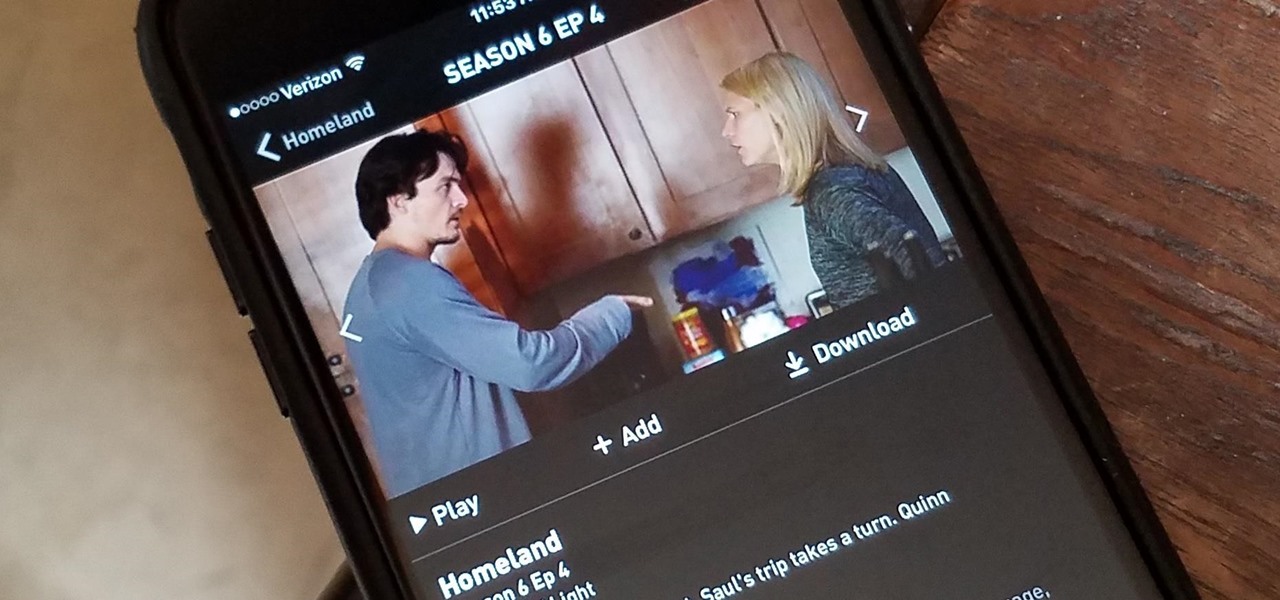
Have you ever wanted to catch up on Homeland or Shameless, but are out and about and don't want to use up your data? Those problems are for days of old now, as Showtime has announced their mobile app will allow titles to be downloaded and viewed without an internet connection.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

Hospitals are places we go to get well, and we don't expect to get sick or sicker there. But a study from researchers at the Cleveland Clinic, Case Western Reserve University School of Medicine, and Cleveland VA Medical Center in Ohio found that hospital floors in patient rooms were frequently contaminated with healthcare-associated pathogens—often dangerous multi-drug resistant bacteria.

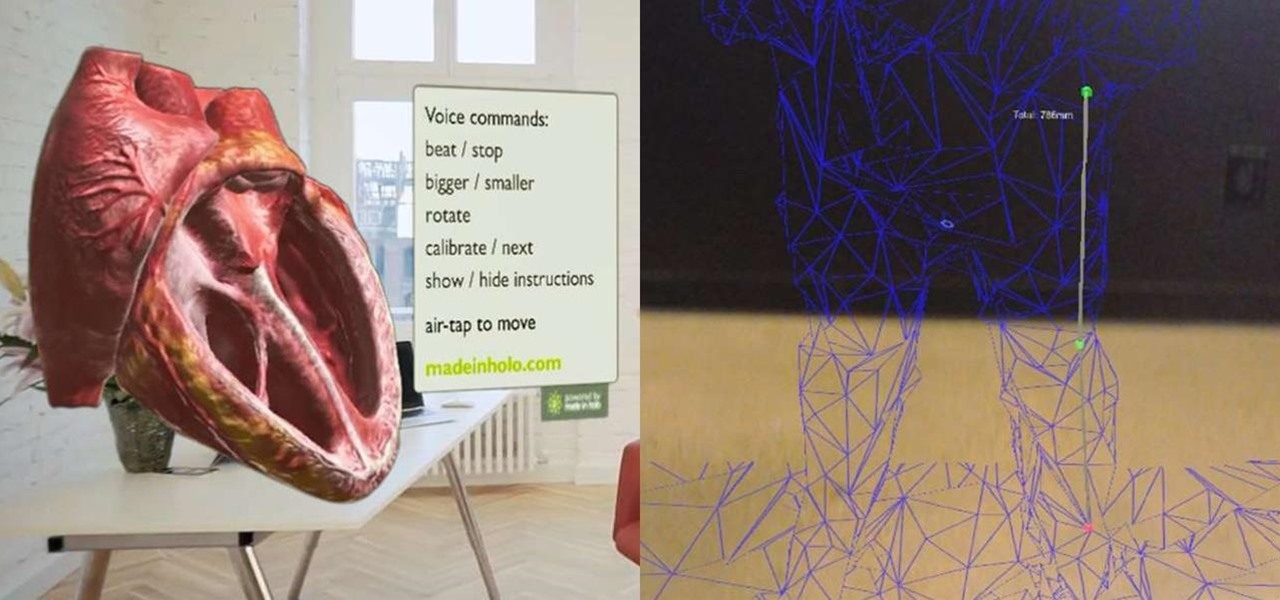
While all of my previous Have You Seen This? posts have all focused on individual HoloLens apps in the Windows Store, this time I'll be sharing a couple at once. These holographic applications are really simple in scope, so there is not a lot to say about them, yet they are interesting enough for me to want to share them with you.

HoloMaps, an application by Seattle-based Taqtile, is available for free on the Windows Store. Taqtile, whose Vice President of Product Management was Microsoft's former Director of Business Development, is one of the few partners currently in the Microsoft HoloLens Agency Readiness Program. This interactive 3D map they have created, powered by Bing, offers more than just a top-down view of the world on the HoloLens.

Lenovo announced at Tech World '16 a slew of new products, and one of them aims to upend the smartphone accessory ecosystem: Moto Mods. Moto Mods are proprietary modular add-ons developed for two new Motorola phones that were also announced in the keynote, the Moto Z and Moto Z Force. Sixteen magnetic nodes align the bottom back of the phones that connect and hold accessories, forming a case appearance. The nodes transfer both data and power at high speeds, a fact that Lenovo hammered home wi...

Android's stock battery menu is pretty decent. You can see which apps have been using the most power, and you can tell when your CPU was awake or asleep, among other things. But a lot of times, battery-sucking services will get lumped under the generic "Android System" header, and even though you can see when your CPU was awake, you can't exactly see why.

The world's first cloud-oriented smartphone, Nextbit Robin, is now available to the masses via Amazon with free one-day shipping for Prime members.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.