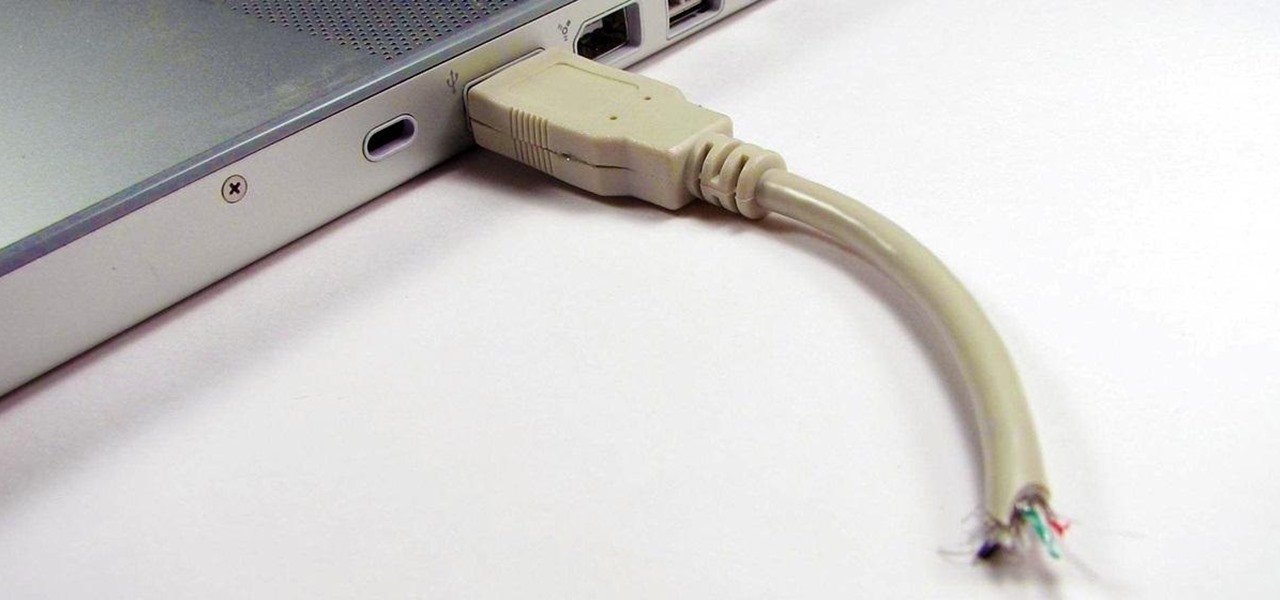
Having a flash drive is more or less a must, but the biggest downside is that they often get stolen, and it's not hard to figure out why. They're small, so they easily fit into pockets, and a lot of people store valuable information on them. Want to pretty much guarantee no one takes yours? Disguise it as a broken USB cable like Windell Oskay of Evil Mad Science Labs so it just looks like a piece of junk to would-be thieves. The materials are pretty simple: a flash drive (the smaller the bett...

Sweating or leaving your feet damp after showers can lead to athlete's foot, a skin rash that targets damp, covered areas. Learn about treating athlete's foot from a doctor in this medical how-to video.

Radio communication is one of the oldest and most effective means of communication via technology, so it's no wonder it's still a popular way to send and receiver signals, especially on the water. Having a Marine radio can be critical when operating a boat on any type of water. There are many uses for a Marine radio, but the most important is to send a distress signal — here’s how to do it.

In elementary school, we all experienced the wonders of papier mâché, that wonderfully malleable mixture of paper and glue (or maybe paper, flour, and water). Once it hardens, it's a homemade work of art. And homemade papier mâché is art on the cheap, allowing your imagination to soar without breaking your budget.

Do you have a lot of anxiety and aren't sure why? Are you just neurotic or do you have a full blown case of OCD? Obsessive-compulsive disorder is nothing to be ashamed of and is more common than you'd think. Check out this video and see if you have a problem.

Maverick Television, from the United Kingdom, explains what stretch marks are, why they are undesirable, and some of the ways doctors treat them. But the more useful part of the video are instructions how to avoid having stretch marks in the first place. The Embarrassing Illness Clinic specializes in medical ailments which sap people's self-confidence. One example is the problem of stretch marks. Using the case of Jasmine Anne Smith, the clinic's physicians explain that stretch marks typicall...

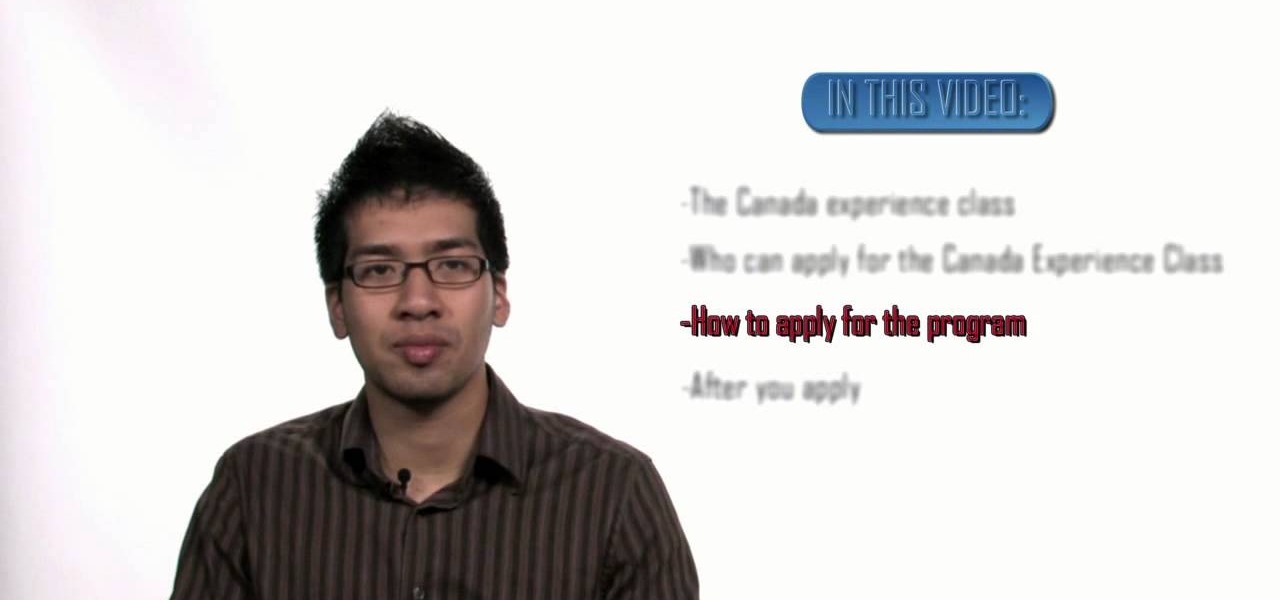
The CEC, Canada Experience Class, is a new program to help a person who has held residency in Canada gain permanent residency status. The program realizes that, by going to school or living in Canada while working, many people have the skills necessary to make the transition to live in Canada permanently. To qualify for CEC, you must be a temporary worker living in Canada for at least two years with two years of skilled working experience. A second way you can qualify is by being a foreign gr...

The purpose of this video is to show how to become a permanent resident in Canada. Some programs are federal and some are for Quebec. The first program is the skilled worker program. The applicant is accessed under a point system and is awarded points for education level, knowledge of English or French, work experience, age, confirmed job offer, and adaptability and you must have sufficient proof of funds. The next program is Family Class Sponsorship. A citizen or permanent resident can spons...

Relieve symptoms of indigestion and hear burn with some simple remedies. You Will Need:

It's not unusual to feel a little down after giving birth. You've been through a major life event, and your mind and body are recovering. Postpartum depression is more serious than the typical “baby blues” that can occur after childbirth. Learn how to identify this condition so you can treat it and spend more time enjoying your baby.

Losing weight can be a battle, but why not be realistic about your goals rather than kill yourself striving for a size 0? A happier alternative to the cycle of weight loss and gain is to achieve a weight you and your doctor can both live with. In this tutorial, learn how to calculate your BMI and ways to figure what your "happy weight" is.

Africanized honeybees, also called killer bees, can be far more aggressive than other types. Here's how to survive when they're on the rampage.

Death by stingray is extremely rare, but getting hit with their barb still hurts like hell – which is why you need to learn how to play footsie safely with these sea creatures.

When it’s that time of the month and a heavy period interferes with your lifestyle, it’s time to take action.

Make your eyes look bigger and brighter by lengthening your lashes. You Will Need

If you have habits that are repetitive, time-consuming, and don't seem to make sense, and they interfere with daily functioning, you may have Obsessive-Compulsive Disorder.

Don't sign any termination papers until you're sure you've made the best deal you can. You Will Need

Watch this video tutorial to learn how to prevent swimmer's ear. Don't let this painful infection of the ear canal keep you out of the water! A few simple precautions can combat the excessive moisture that causes bacteria to fester.

Get luscious, pillowy, kissable lips—with or without injections. You Will Need

If you love coconuts, coconut water or even coconut meat, you should know how to open one up. This HowTo video tutorial shows you an easy way to open a coconut without making a mess.

This pilates how-to video illustrates the Lateral Flexion exercise of the Side Leg Series. It is obviously a great exercise for lateral flexion and balance.

Okay, you've watched the "human skeleton structure" and "human neuroanatomy" videos, the next step is right here in these tutorial videos on the human muscular structure.

No one can escape the wrath of fire. Eery living person will experience some sort of burn during their lifespan, from scalds to third degree burns. Burns and scalds are among the most common injuries requiring emergency treatment in hospitals, but would you know what to do if a friend or family member, maybe even a stranger, burned themselves badly? Could you help?

The most basic and most important aspect of first aid is CPR. It's the one thing that is most likely to save a life. It's stands for cardiopulmonary resuscitation, which is the emergency medical procedure for restoring a person's normal heartbeat and breathing when experiencing heart failure or breathing impairment. But there's a different approach when dealing with and chest massages for babies under one year old.

CPR. It's stands for cardiopulmonary resuscitation, which is the emergency medical procedure for restoring a person's normal heartbeat and breathing when experiencing heart failure or breathing impairment. It's the number one way to save a life, and everyone should know it, whether you're certified or not.

In this video tutorial, viewers learn how to calculate the standard deviation of a data set. The standard deviation of a statistical population, a data set, or a probability distribution is the square root of its variance. To calculate the standard deviation, users will need to follow these steps. 1) Find the mean of the data. 2) Subtract the mean from each data point. 3) Square each of the values you got in step 2. 4) Then find the mean of the values you get from step 3. 5) Finally, square r...

In this video tutorial, viewers learn how to recover lost data using R-Studio. Begin by running R-Studio. Locate the drive that you want to recover. Right click it and select scan. The scan can take up to 45 minutes depending on the size of the drive. Once its finished, there will be a list of hard drives in which data is stored. Green, black, and orange will recover with no problems. Red is not recoverable. Double click on the wanted drive and wait for it to load. You can now see all the dat...

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Feeling someone's forehead when they are sick is an outdated way to check for a fever. Follow along with this video and learn how to take an accurate reading so you know whether or not to seek medical help.

HomePod and HomePod mini are excellent smart speakers if you're entrenched in the Apple ecosystem. They even offer ways to protect your sensitive information from friends and visitors who try to ask Siri to spill your secrets. But there's an extra layer of privacy you can put in place to make sure nobody gains access to any important notes, reminders, and calendar events.

In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.

Apple released the third public beta for iOS 13.5 today, Wednesday, May 6. This latest public beta update comes exactly one week after Apple released iOS 13.5 public beta 2, which, among other things, introduced Apple and Google's joint COVID-19 exposure notification API. Public beta 3 updates that settings page to show a more detailed "Exposure Logging" option instead.

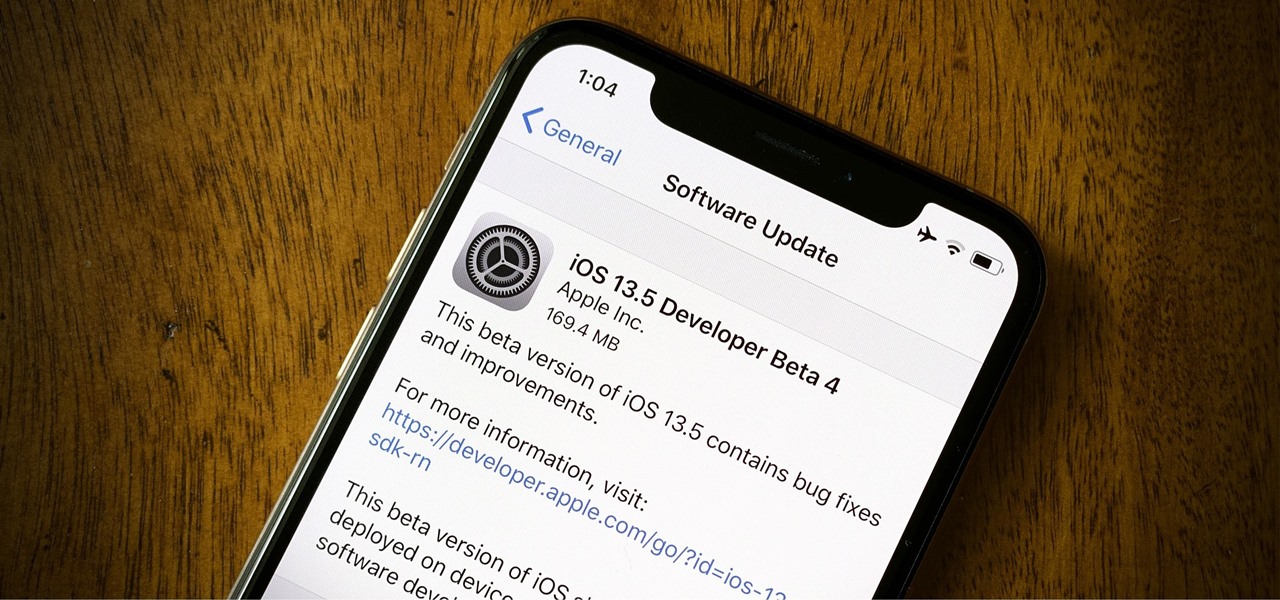
Apple released the fourth developer beta for iOS 13.5 today, Wednesday, May 6. This update comes one week after the release of iOS 13.5 dev beta 3, which introduced Apple and Google's joint COVID-19 exposure notification API to iOS for the first time. Apple updated that settings page to now include an "Exposure Logging" setting instead.

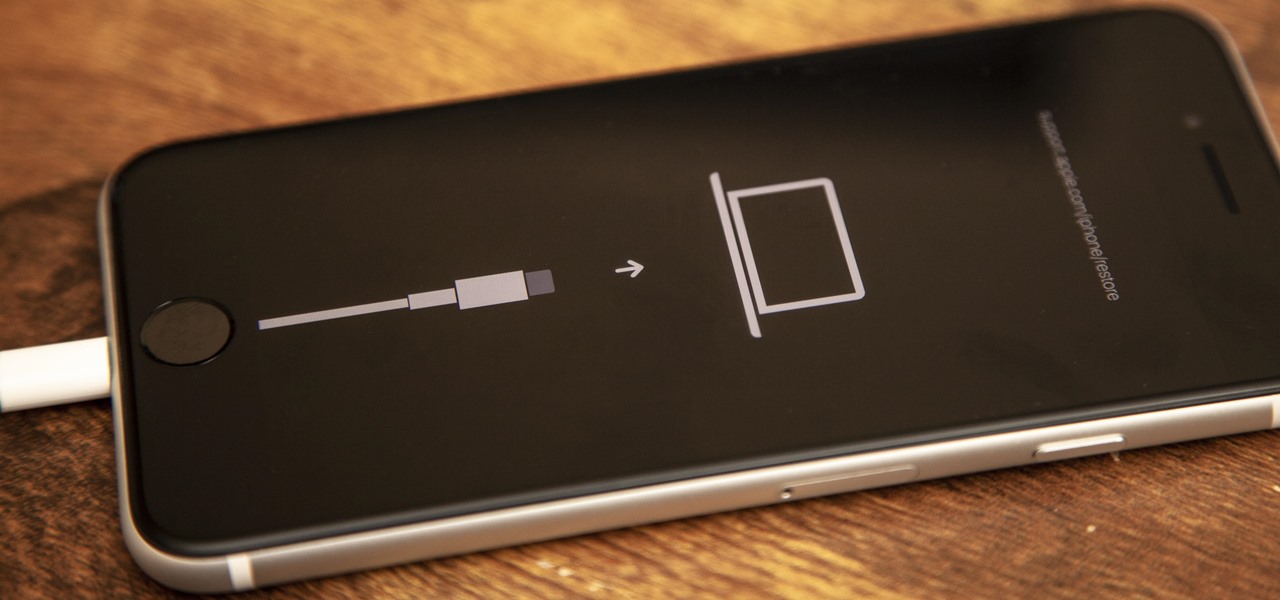
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your fail-safe.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Whether you're used to 3D Touch or Haptic Touch, deleting and rearranging apps and folders on your iPhone is a little bit different in iOS 13.

You've probably heard of RCS messaging. The new standard has been promoted by Google as their answer to iMessage and is the backbone behind the new "Chat" features in Android Messages. With RCS, Android phones will now enjoy enhanced messaging like iPhone users have had for years — but is it really the same?