Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the secrets that are lurking within Apple's newest mobile operating system.
Don't want to shell out the big bucks for some fancy, expensive budgeting software? Well, if you have Excel 2008 for Mac installed, you can manage your budget right there. Personal financing doesn't get easier than this— even business finances are easy to keep track of. The Microsoft Office for Mac team shows you just how to manage your finances with pre-formatted Ledger Sheets in this how-to video.

This session is tailor-made for advanced Studio users aiming to achieve ultimate quality surface creation.

Watch this video for medical care tips regarding minor headaches.
With the TSA's full-body scanners occupying a great deal of airports nationwide, the debate remains as to whether air travelers should continue to be subject to immoral security techniques and possible health risks due to the x-ray scanning devices. The "advanced imaging technology" may help keep obvious weapons out of major airports, but scanning naked bodies seems more voyeuristic than crucial to national security. But while the argument continues, one woman is taking a stand… well, not rea...
Enjoying the many benefits of Facebook Places? But what if you want to check in somewhere you're not? Your smartphone can automatically detect your geographical location, preventing you from just checking in just anywhere, but like all technology… it's a long way from perfect, even Android mobile devices.

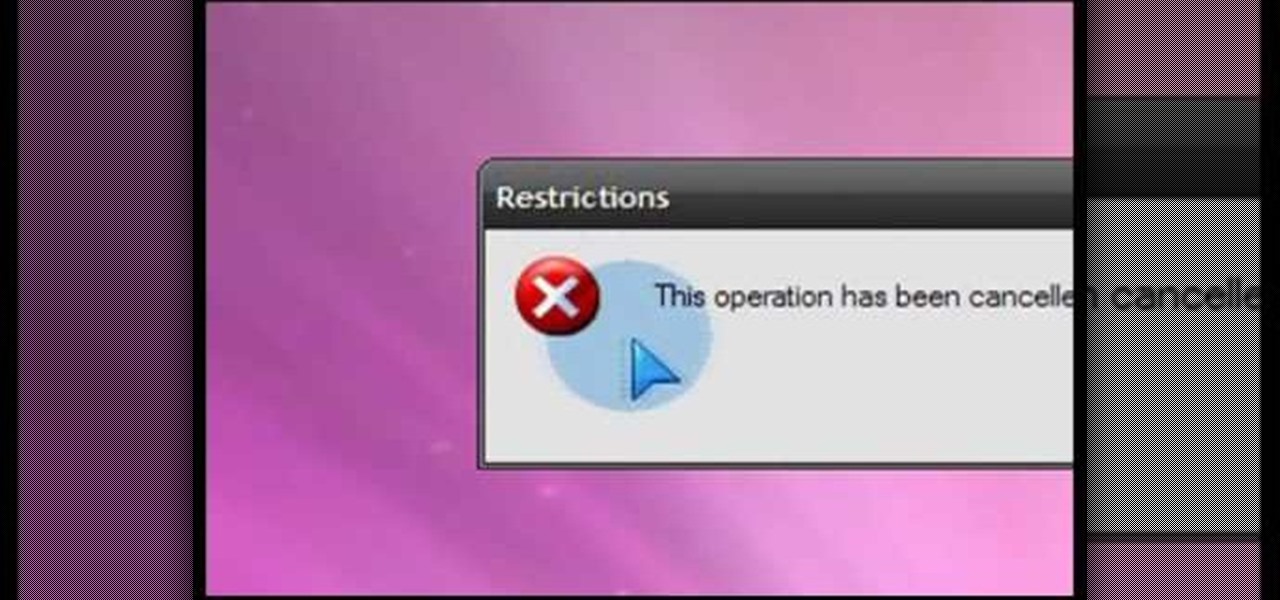
If you love computer pranks, this is one of the easiest ones to pull. This video will show you how to remove the Shut Down button from the start menu in Windows XP. Actually, it does't remove the shutdown button, it just disables it, giving the user a restriction message, stating "This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator."

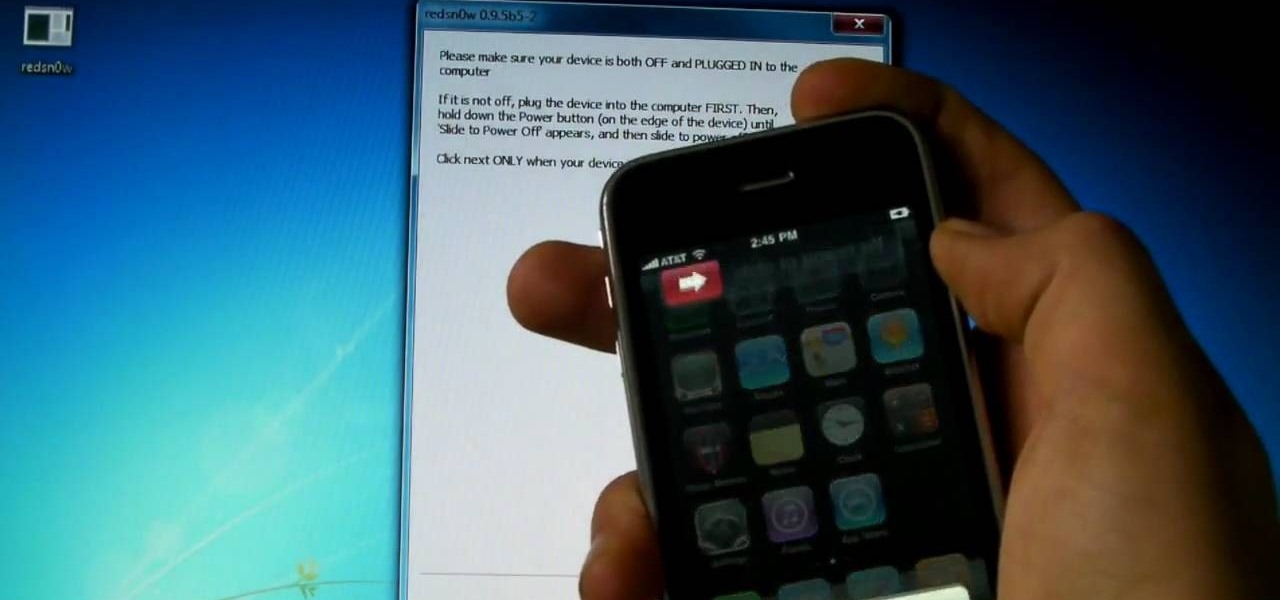
As of today, there are no legal barriers standing between you and jailbreaking your iPhone, iPad, or other mobile device. Hooray! If you were afraid of Apple coming to your house at night if you jailbroke your phone, you can finally let go of the fear and make your iDevice the beast it should have been all along! This video will show you how to jailbreak a iPhone 3G or iTouch 2G with iOS version 4.0 or 4.0.1 using Redsn0w. Now you can fully enjoy your Apple device.

In this how-to video, you will learn how to replace a hard drive in a 2008 Macbook Pro. Make sure you use the proper anti-static precautions before replacing the device. You will need a T6 screwdriver and a Phillips screwdriver. Make sure you transfer your data from the old drive to the new one before installing. Shut down the computer, close the lid and turn the laptop over. Remove the battery cover and battery. The hard drive is held by a plastic retaining bar. Loosen the screw holding the ...

To install a hard drive in a 13" (13 inch) Macbook Pro laptop computer released in 2009 you will make sure to first transfer all data off the drive then discharge any static electricity from your hands making sure your are in a static free work environment. Next you will remove the old hard drive, to do this flip over the laptop and remove the 10 screws around the edge of the device with a #00 Phillips screwdriver starting with the three longer screws on the top right. Next, lift off the bott...

In this how-to video, you will learn how to install a hard drive into a 17" Macbook Pro. Make sure you use the proper anti-static precautions before going on with this procedure. You will need a pry tool, a Phillips screwdriver, and a T6 screwdriver. Make sure you transfer your old data into the new drive before installing. Shut down the computer and flip the laptop over. Unscrew the ten screws around the bottom. Now, remove the cover. You will see the hard drive at the lower right. Loosen th...

In this video from MacOSG we learn how to install a hard drive in a 15" Macbook Pro from around 2009. For this you need a #00 Phillips head screwdriver and a T6 Torx screwdriver. Make sure you use proper anti-static precautions with this. Transfer your data to the new drive before installing. To remove the hard drive, flip over your Macbook. Use your Phillips to remove the 10 screws. Remove the 3 at the right which are longer than the other screws. Then remove the left most screw which is the...

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

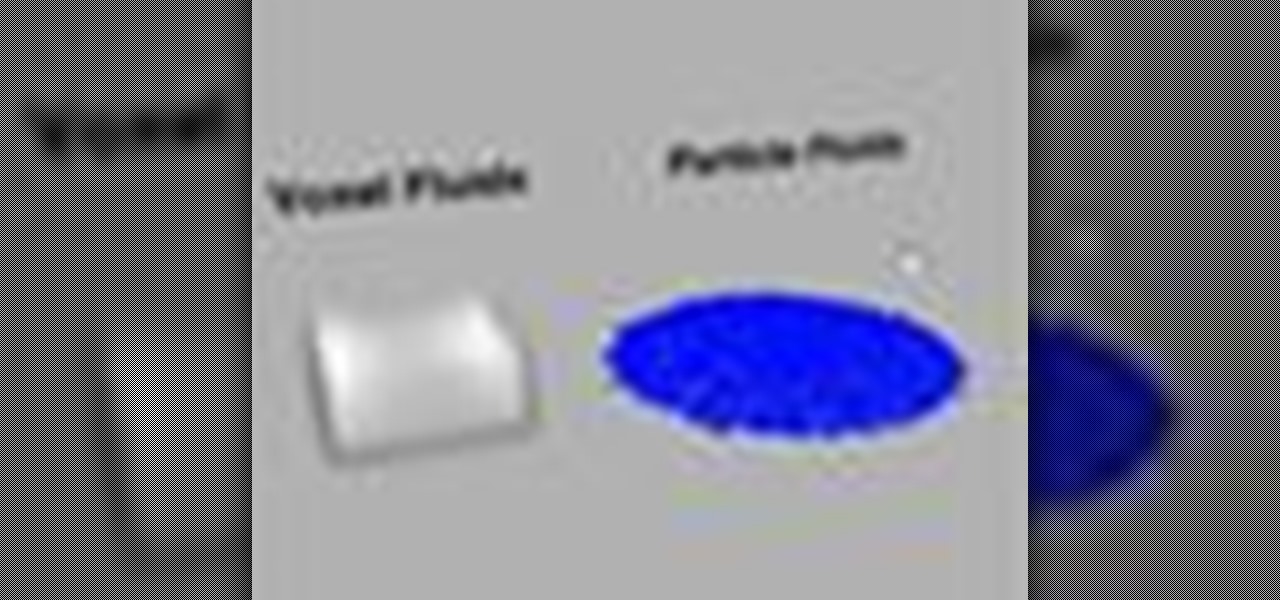
Created by Houdini Product Specialist Stephen Tucker, this crash course series focuses on the concept of fluid dynamics and how they work within Houdini. These videos on Voxel Fluids should help any artist get up in running with the foundation tools available for creating fluid effects in Houdini 9.5. Topics range from how to create a container to how to gain access to fluid attributes for shading, and even passing data from volumes to particles.

This video tutorial from Live Monarch shows you how to fix a live butterfly's broken wing. You can help restore flight to a butterfly in need -- you can be a hero and make a real difference.

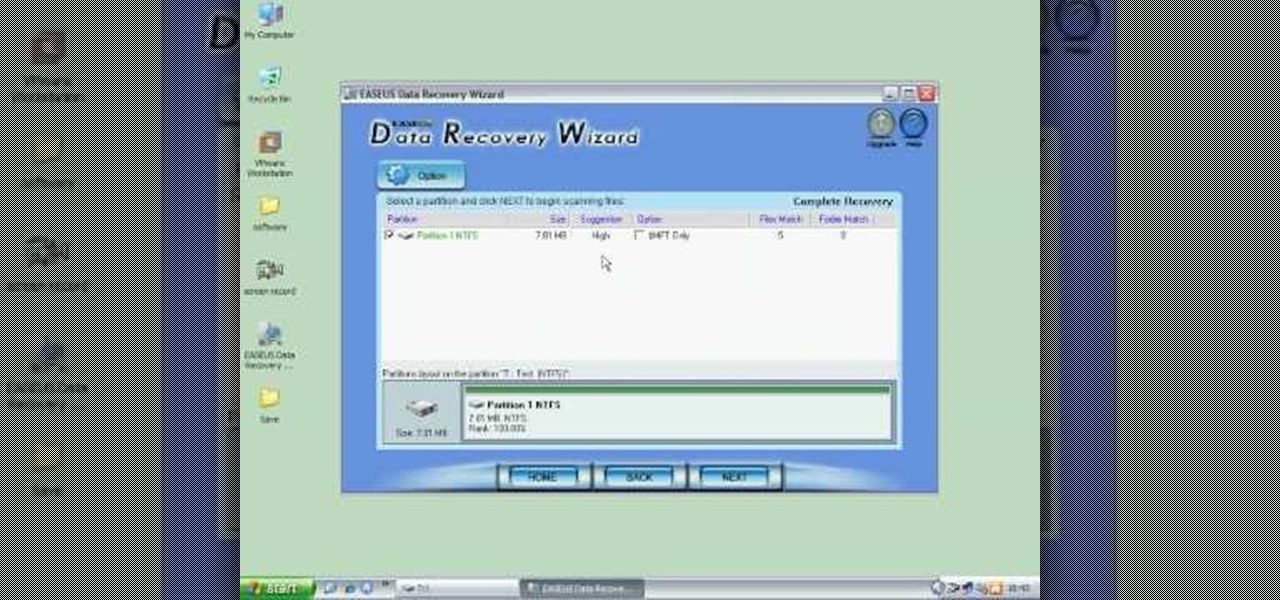
In this video the instructor shows how to restore lost data. When you delete your files you can restore them from the recycle bin. But if a hard drive is formatted all the data is lost and you can not even recover it from recycle bin. In such cases you will need to use data recovery tools to recover that lost data. In this video the instructor uses the Data Recovery Wizard software to recover the data. Start the Data Recovery Wizard. In that there are three options by which you can recover yo...

Roughly half of all Americans believe in extra sensory perception... Are you part of that statistic? Ever get the feeling you have a paranormal ability? You can investigate your psychic abilities and hone your skills with these tips.

If you're new to DreamCoder for Oracle, one of the very first features with which you'll want to acquaint yourself is the data table browser, which will permit you to display entries in a given Oracle database. For a detailed walkthrough of this feature, take a look at this video tutorial.

This video tutorial will walk you, step by step, through the process of importing data directly from an Excel document to a MySQL database server using the smart copy feature available in the DreamCoder for MySQL. For more information, press play!

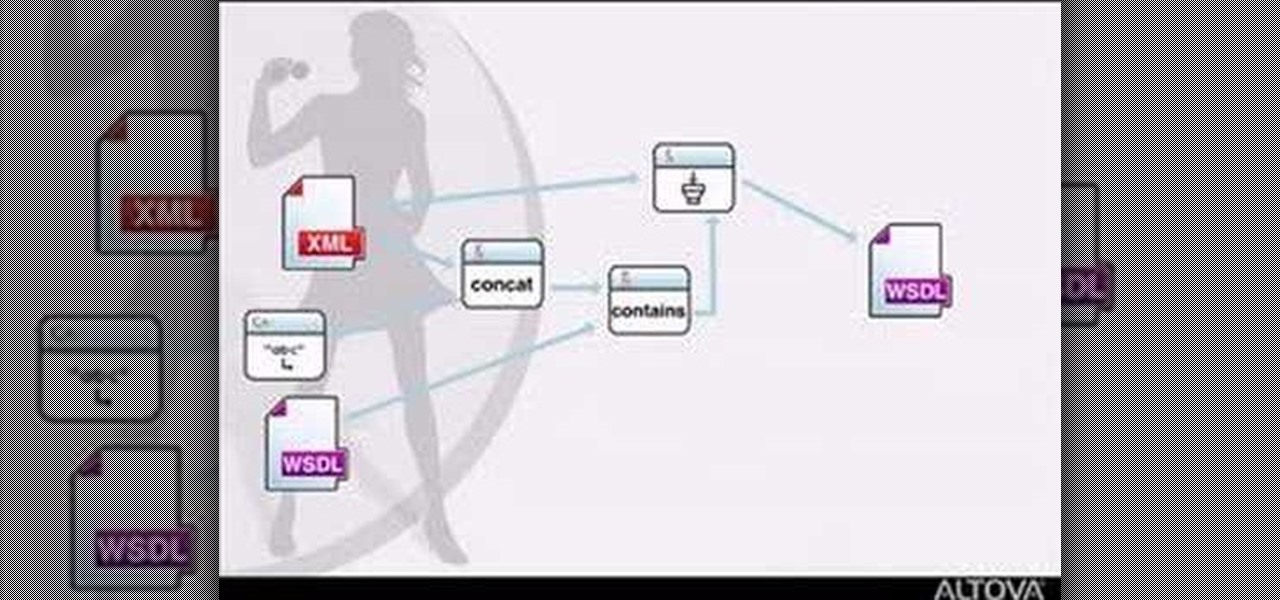
MapForce supports XML, databases, flat files, EDI and web services as the source and target of any mapping. In this tutorial, you'll take a look at how to use the different data sources available in MapForce.

Learn how to treat a fever, how to identify the symptoms, how to avoid getting a fever and how to deal with one comfortably with expert medical tips from a trained doctor in this free health care video series.

In skin care, chemical peels are useful for a variety of conditions. Learn about chemical peels in this free video on skin care treatments from a licensed medical aesthetician.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

We already know that Microsoft has something big planned for later this month, and now we have details on how to watch the company's big reveal.

By now, there's no way you haven't stumbled upon a TikTok video, whether it was on Facebook, Instagram, Twitter, or YouTube. Just watching these addictive short-form videos is enough to make you want to join up and make your own, and when you do, we've got some tips that will help get your TikTok account in order.

When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps on the Play Store and how to avoid them.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

Artificial intelligence and augmented reality go together like spaghetti and meatballs, and Lenovo has some ideas on how to spice up the recipe.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.