Thanks to Magisk, you don't have to lose root when updating to Android 11. The popular systemless rooting tool already achieved superuser access on Google's latest OS, even before the official release. It's currently in its experimental stages so the process is trickier than usual, but it does work.

The future of TikTok in the U.S. is all but certain. Microsoft, Walmart, or Oracle could save the day by buying the company, TikTok may win its lawsuit, or China's new restrictions could halt everything — but all could fail. Just like Vine before it, TikTok could be on its way out, only for opposite reasons. But will it matter if TikTok gets banned in the States? With the competition heating up, likely not.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.
Your iPhone and Mac can speak to each other in many ways, allowing you to start work on one device and seamlessly switch to the other, share clipboards between the two, and pick up phone calls and answer text messages on both. The compatibility is incredible, but there's even more you can do by incorporating third-party software into the mix.

If you're ever in a situation where you need to take a peek at the wireless spectrum, whether it's for Bluetooth or Wi-Fi devices, there's a fascinating Python 3-based tool called Sparrow-wifi you should check out. It's cross-platform, easy to use, and has an impressive GUI that shows you the signal strength of nearby devices.

Apple just released the fourth public beta for iOS 14 today, Thursday, Aug. 6. This update comes two days after the company released iOS 14 developer beta 4, 15 days after Apple seeded developers the third dev beta, and two weeks after the release of public beta 3.

Apple just released the fourth developer beta for iOS 14 today, Tuesday, Aug. 4. This update comes 13 days after Apple seeded developers the third dev beta, and 12 days after public testers got their hands on public beta 3.

Apple just released the third public beta for iOS 14 today, Thursday, July 23. This update comes one day after the company released iOS 14 developer beta 3, and two weeks after the release of iOS 14 public beta 2.

Apple just released iOS 14 developer beta 3 for iPhone today, Wednesday, July 22. The update comes 15 days after Apple released the second developer beta for iOS 14, and 13 days after the release of iOS 14 public beta 2.

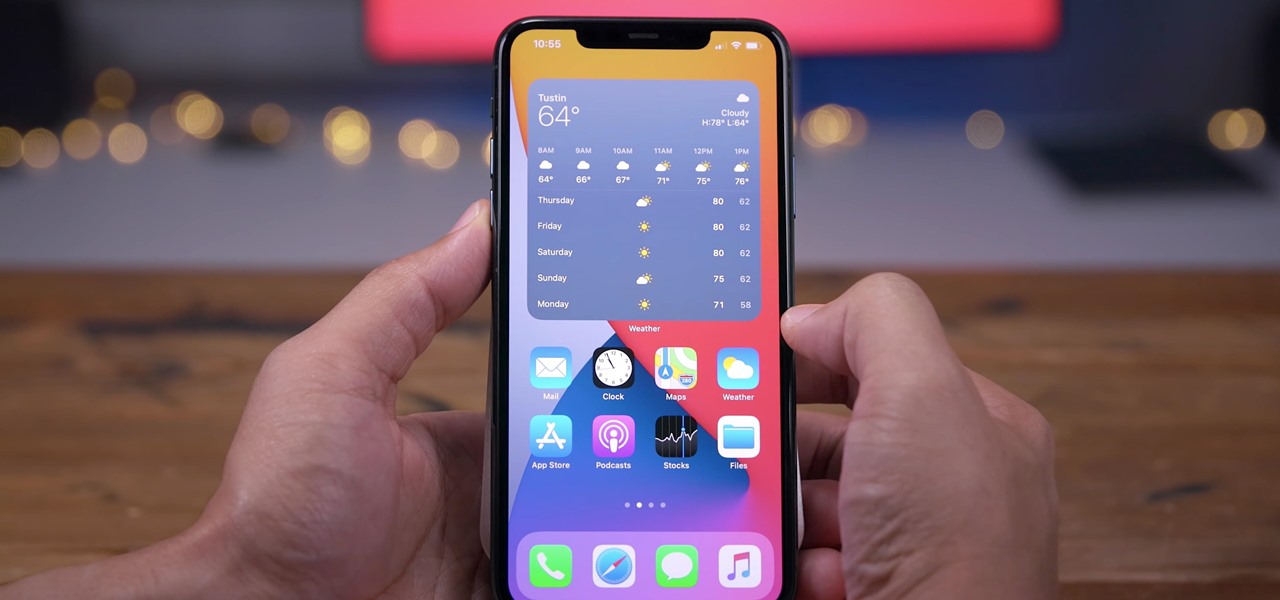
Apple just released public beta 2 for iOS 14 today, Thursday, July 9. The good news comes two days after Apple released the second iOS 14 developer beta, and 17 days after the release of the first developer beta. While this is the first public beta for iOS 14, it's called "public beta 2" to keep in line with developer beta numbering.

Apple just released the second developer beta for iOS 14 today, Tuesday, July 7. The update comes 15 days after Apple seeded developers the first iOS 14 beta, which introduced home screen widgets, picture-in-picture, and 4K YouTube support, among more than 200 other features.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

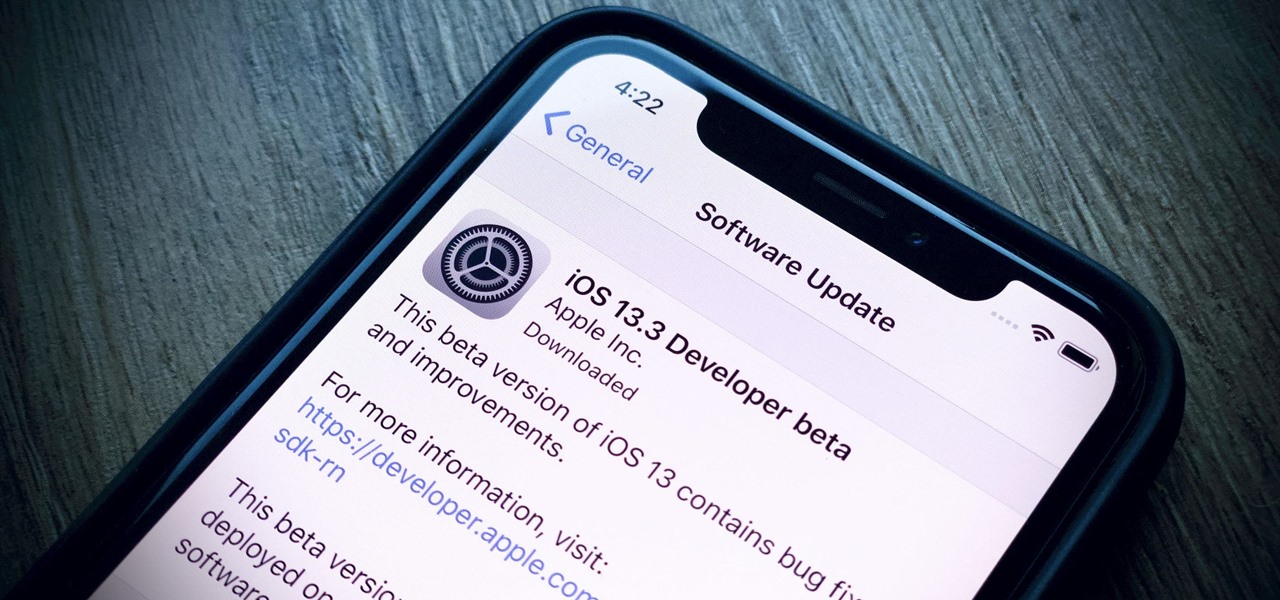
Apple's already gone through iOS 13.0, 13.1, 13.2, 13.3, 13.4, and 13.5 betas, and now it's time for iOS 13.6. If you want to try out new features on your iPhone before the masses, install either the developer or public beta.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

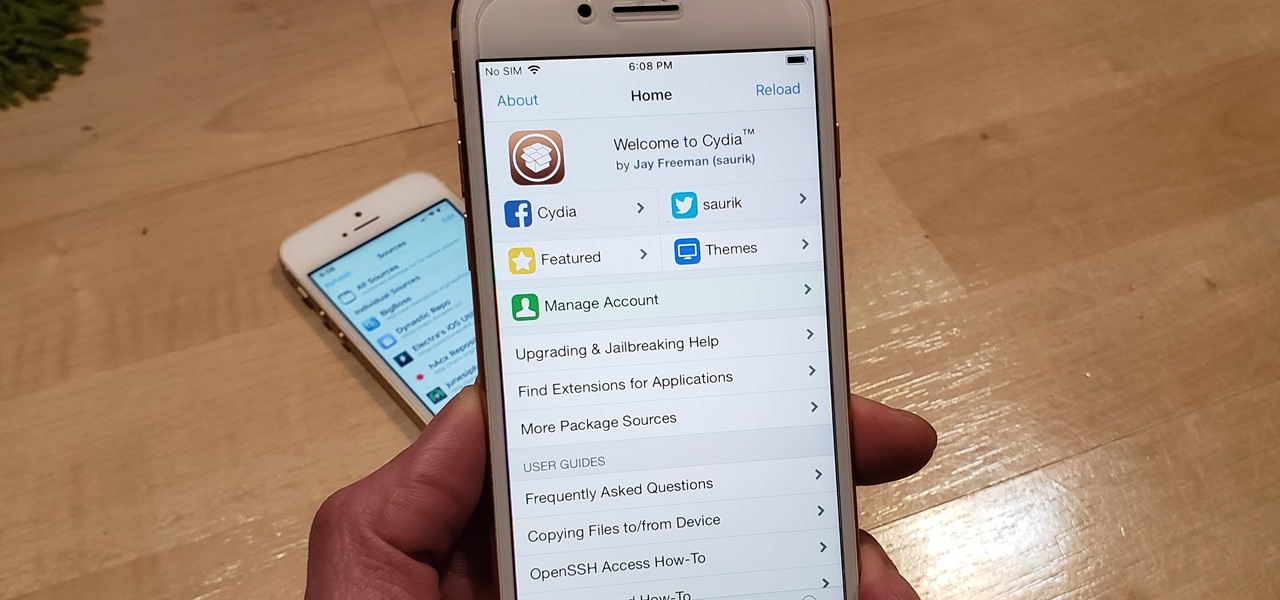
With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

There's never been a better time for streaming videos on your phone. With so many options available (including a potential mobile-only Netflix tier) and so many new smartphones having large screens, there's a good chance you know someone who mainly use their phone for videos. And if you looking for a gift for them, there are some great options.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveillance – Broadcast, or ADS-B for short.

UPDATE: Due to increased, uncontrollable spam, submitting anything other than comments on WonderHowTo and its affiliated network of sites is temporarily closed. Only current and past members who have previously submitted helpful news and guides may be able to submit forum posts.

Since its introduction on the iPhone 5S, Touch ID has made unlocking Home button iPhones quick and secure. The second-generation iPhone SE brought back the beloved feature in 2020 but didn't take any steps to improve on the technology. So if you're rocking Touch ID and having trouble getting it to read your fingerprints, there are some things you can do to fix it.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

The Mechanic character class is now live in Global MapleStory (GMS), the international version of Nexon's popular free massively multiplayer online role-playing game. Celebrate the release by building a super-powerful Mechanic to call your own! No idea how to invest your skill points? No problem! The build guide excerpted below eliminates the guesswork, permitting you to focus on what matters: playing the game.

http://www.amazon.com/What-Makes-Sammy-Budd-Schulberg/dp/0679734228

Watch this knot tying instructional video to learn how to tie the palomar fishing knot. The palomar knot is a popular and easy to tie knot for small terminal tackle connections. It is one of the few recommended fishing knots for use with braided lines. Hope this knot tying tutorial helps you master the palomar fishing knot. Tie the palomar knot for fishing.

Be confident your first aid skills are faultless in emergency. Our experts show the recommended way to bandage a hand safely and securely. Bandage a hand.

This Animal Welfare Foundation three-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a gerbil.

All you LARPers out there, watch and see how you can make a blue boffer sword for LARPing. This weapon passes all weapons specs as of Ragnarok XXI War Council for Eryndor.

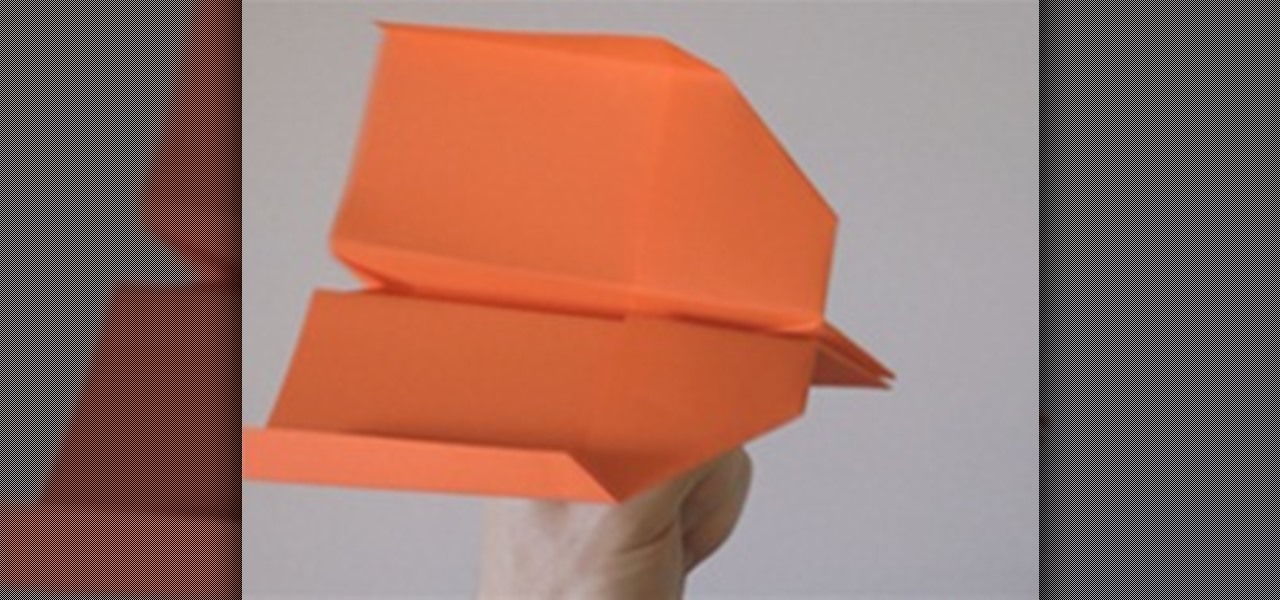
This swallow paper airplane uses some folding techniques from origami to make the head a little heavier then the rest of the plane, allowing it to make cool loops. As a kid, this was my favorite plane because it looks cool and is quite robust, so you don't need to fold a new plane after every crash.

Brake fluid is used in hydraulic brake systems to help apply immediate force to the brakes when you step on the pedal. It's essential for your road safety to use the correct type of brake fluid and keep it at the recommended level at all times. So fill your car's brake fluid with this video's advice. Fill your car's brake fluid.

The best way to store a bandsaw blade is to fold it. Here is a simple technique that gets the job done quickly and safely. Wearing gloves if the blade is wider than 1 in. is strongly recommended. Fold a bandsaw blade.

Chris Cooke explains three exercises you can do to exercise your triceps using weights. You can do triceps dips, lying triceps extension, and single overhead press. It is recommended that you do ten repetitions of each exercise. These exercises require two dumbells and a bench. Exercise your triceps using weights.

Chris Cooke demonstrates how you can exercise your calves with free weights. You can do the following: standing calf raise, single calf raise, and seated calf raise. It is recommended that you do 15 repetitions of each exercise. These exercises require dumbbells,

Middle-aged woman shows how to remove candle wax from a carpet. Knowing what kind of carpet you have is key into understanding if your carpet can be cleaned or not. Video recommends calling a professional if you are unsure. Different methods help to provide satisfying results. Remove candle wax from a carpet.

Learn how to help someone who is vomiting. From our favorite British imports at videojug, learn some helpful tips for those who are sick to the stomach. We don't recommend this to the queasy. Help someone who is vomiting.

Watch this knot tying instructional video and learn how to tie the improved clinch knot for fishing. The improved clinch knot has become one one of the most popular fishing knots for tying terminal tackle connections. It is quick and easy to tie and is strong and reliable. The improved clinch knot can be difficult to tie in lines in excess of 30 lb test. Five+ turns around the standing line is generally recommended, four can be used in heavy line. This fishing knot is not recommended with bra...
I recently found this video series that discusses (in a more round about way) the theories that make cryptography what it is today, which goes great with my most recent blog post. I haven't finished watching them all yet, but so far they have been fairly good and I would recommend watching one to see if you like it?!