If you're running iOS 10 or lower, there is no built-in way to make a screen recording on an iPad, iPhone, or iPod touch directly from the device, but that doesn't mean there isn't a way to record your screen at all.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Please read the following in Rod Serling's voice. Picture, if you will, a mother. She comes home after a long day at the office, relieved that she took some chicken breasts out to thaw and will be able to make a quick and easy dinner for her family. She opens her refrigerator to get the chicken, but to her horror she does not see it… she forgot to take the chicken out of the freezer after all. What will she make for dinner now? How will she feed her family? She has entered…the Panic Zone.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

As the days get shorter and the weather cools down, I prepare to "hibernate." I add piles of blankets to my bed, wrap myself in layers of flannel, and—most importantly—eat as if I'm storing energy for winter.

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

One of my favorite things about American Chinese food is how easy it is to eat: the pieces are bite-sized, the flavors are addictive, and the meat is always tender and easy to chew. But if you've ever tried to replicate any of your favorite takeout in the kitchen, you've likely noticed that the high heat required for most recipes thoroughly dries out the meat that you're trying to cook.

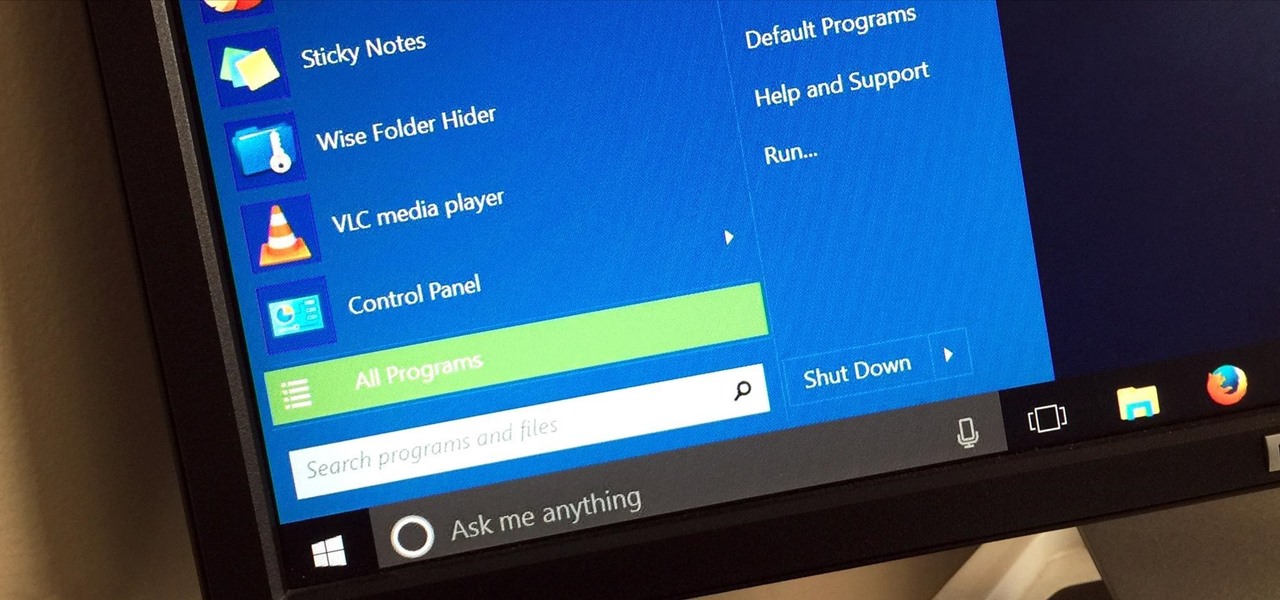
If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Preparing and serving seafood can be a daunting task. Fish is so delicate that one extra minute of heat can turn a juicy, flaky filet into a dried-out disaster. But that same fragility also allows us to use unconventional methods to chemically transform the fish into its cooked consistency.

The awesome thing about Android is that you rarely need to settle for what comes stock on your device. If your music app sucks, switch it. If you don't like your home launcher, swap it for a better one.

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.

There are many hacks for increasing productivity, but so many depend on tricking your own mind or behavior. When it comes to motivation in the workplace, though, sometimes the space within which you work dictates how you behave and the work you produce. So if you want to increase your ability to get more done in a single workday while doing a better job, consider changing your surroundings in the following ways.

Windows 95, which introduced the Start menu to the world, recently celebrated its 20th birthday! The feature was an instant hit, becoming a core component of Windows operating systems. Well, it was removed in the mistake that was Windows 8, but you should know by now that the Start menu has been reincarnated for Windows 10.

It goes without saying that a pizza stone is one of the keys to making a perfect pizza. The science behind pizza stones is relatively simple: the stone conducts and holds heat, which keeps the oven temperature steady even when a cold ingredient (such as an uncooked pizza) is introduced. This not only helps the pizza cook more evenly, but also allows the bottom to get crisp.

People like to cite the iPhone as the device that started the smartphone craze, but the truth is, smartphones had existed for years by the time Apple got into the game. The real groundbreaking feature that this device brought to the table was a multi-touch screen to go along with its "smart" functionality, and this is still the main method we use to interact with our devices today.

Your grater and microplane may look like single-purpose tools, but they're actually one of the most diverse appliances in your kitchen. Sure, everyone knows to use a grater on cheese and a microplane on citrus zest, but why stop there? Here are 10 things you may not have thought to grate:

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

While I frown upon any form of uneaten cookie, sometimes we overestimate our late-night cravings for baked goods leaving us with extra cookie dough at 4 a.m. If you're in the privileged dilemma of not having enough excess dough to make another batch of cookies but just enough left over that you can't justify tossing it, don't fret. Here are five effortless and unexpected ways to salvage it.

The 13-megapixel camera on the OnePlus One is capable of taking some pretty impressive shots, but the stock CameraNext app doesn't do the hardware justice. When compared to the camera app that ships on the ColorOS version of the One, you can immediately see an increase in clarity and low light performance.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Soup can be one of the most finicky dishes to make. While seemingly innocuous at first, the texture of this meal can change in an instant. For example, adding too many vegetables can result in soup that's too watery, such as tomatoes, which contain a lot of liquid.

Sitting in a cubicle and never seeing sunlight during the workday is unpleasant to even think about—and sitting in a flourescent-light cube can have terrible effects on both our work performance and overall attitude. Yet there are ways to counteract the effects of cubicle sitting, even if you can't sit in a sunny office or work from home.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

The new Nexus 6 and Nexus 9 models will be shipping with Android 5.0 Lollipop preinstalled, and the Nexus 4, 5, 7, and 10 will be getting the new OS update from Google very soon. But where does that leave the rest of us?

I became a big fan of polenta while studying Italian cooking. Previously, it never occurred to me that ground corn could create a dish that could rival the best pastas or potatoes. Those rich, golden bowls of cornmeal, cooked until tender and flavored with good olive oil, butter, sea salt, and fresh herbs soon became one of my favorite things to eat.

If you're using iOS 10 or lower, there is no built-in way to record an iPad, iPhone, or iPod touch screen, and Apple doesn't allow any third-party apps to screen record either. If malicious, an app could theoretically continue recording even after you think it's off, allowing it to capture account and password information that you enter on your device. This changes in iOS 11, which introduces native screen recording, but what do you do if you're still running iOS 10 or lower?

In the Apple's iOS beta 3, we were introduced to a new iCloud Drive feature, an option to disable QuickType, time indicators for Recently Deleted pics, and a way to keep "self-destructing" media.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

The Spanish and Portuguese introduced many things (some desirable, some not, depending on your POV) to Mexico in the sixteenth century: Christianity, language, and lots of flora and fauna.

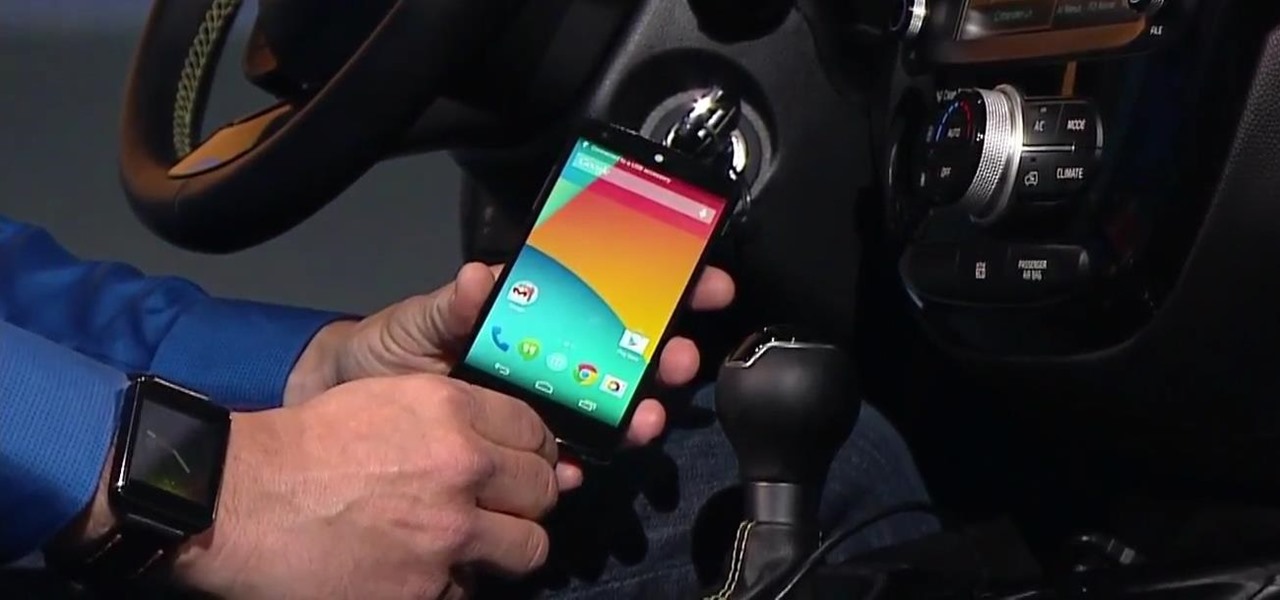
This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

The Moto X introduced tons of cool features that have slowly been ported over to other phones, like Peek notifications and always listening "OK, Google" detection. Another such feature allows you to twist your wrist to bring up the camera app from any screen—even with the display turned off.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

The Nexus 5 has a known issue with its display. Affecting all models from the first manufacturing run and most models thereafter, this display issue is easiest to notice on something with a white background. A yellowish tint, most noticeable when compared to other devices, seems to emanate from the Nexus 5's screen.

After years of making do with a cheap knife, I finally bought a really good 8" chef's knife—a Henckels, although I was also eyeing a Global santoku. It quietly but literally changed my life.