Everyone should be able to perform basic first aid, even those with hearing impairment. Deaf individuals are just as likely to save a life as anyone else, but they need to know how, just like everyone else. This video is signed to help those with hearing problems learn about strains and sprains treatments. Although strains and sprains are not a serious injury, they are still very painful for the sufferer, and the only way to make sure they heal properly is to make sure they get immediate atte...

With the current oil spill in the Gulf, the victims suffering the most are birds and fish. All of these gorgeous animals that have been living in this area forever are suddenly covered in BP oil and fighting for their lives.
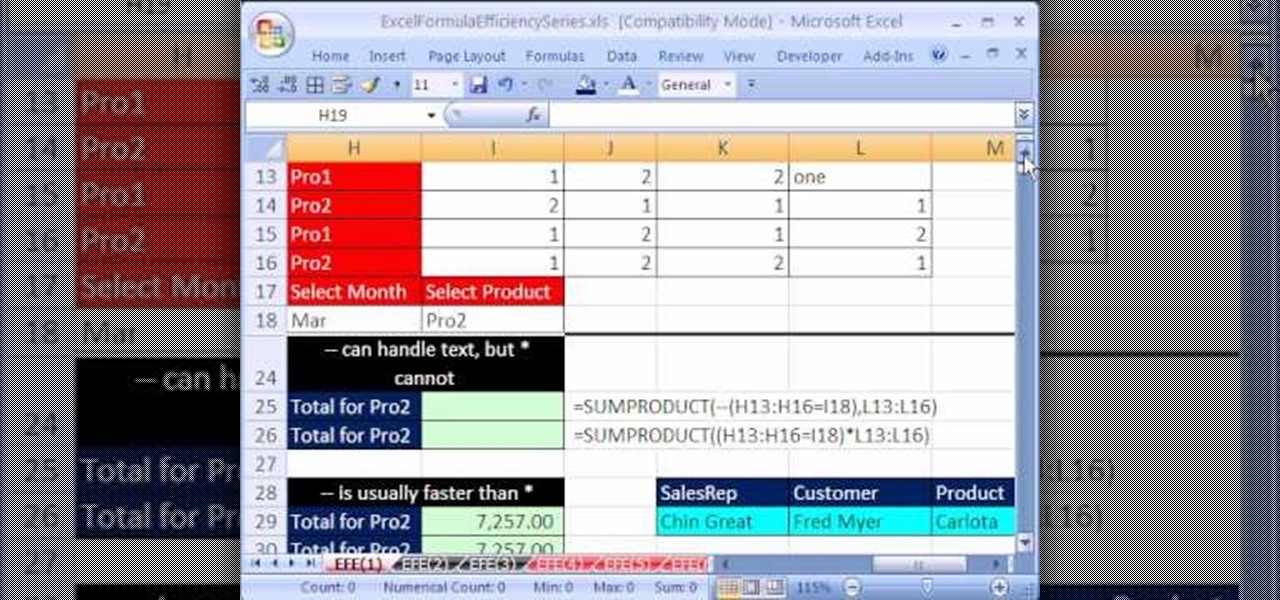
Are you looking for a way to make your Microsoft Excel formulas more efficient? If so, you're in the right place. With this free video lesson from everyone's favorite digital spreadsheet guru, YouTube's ExcelsFun, the very first installment in his "Excel Formula Efficiency" series, you'll learn about the basics of Excel's SUMPRODUCT function — why some people use double negative and why other use times one.

In this how to video, you will learn how to serve a tennis ball. Start off with an eastern forehand grip. You can pretend to shake hands with the racket to find this grip. The knuckle of the index finger should be on top of the handle. Make sure your stance is sideways to the net and the feet are shoulder width apart. Your foot should point at 1 o'clock. The back foot should be parallel to the base line. Your racket should start at pointed towards the net. The first step of the swing involves...
Want to vanquish even the toughest of foes with the greatest of ease? This hacker's how-to demonstrates a method for killing your Ninja Saga enemies with a single hit.
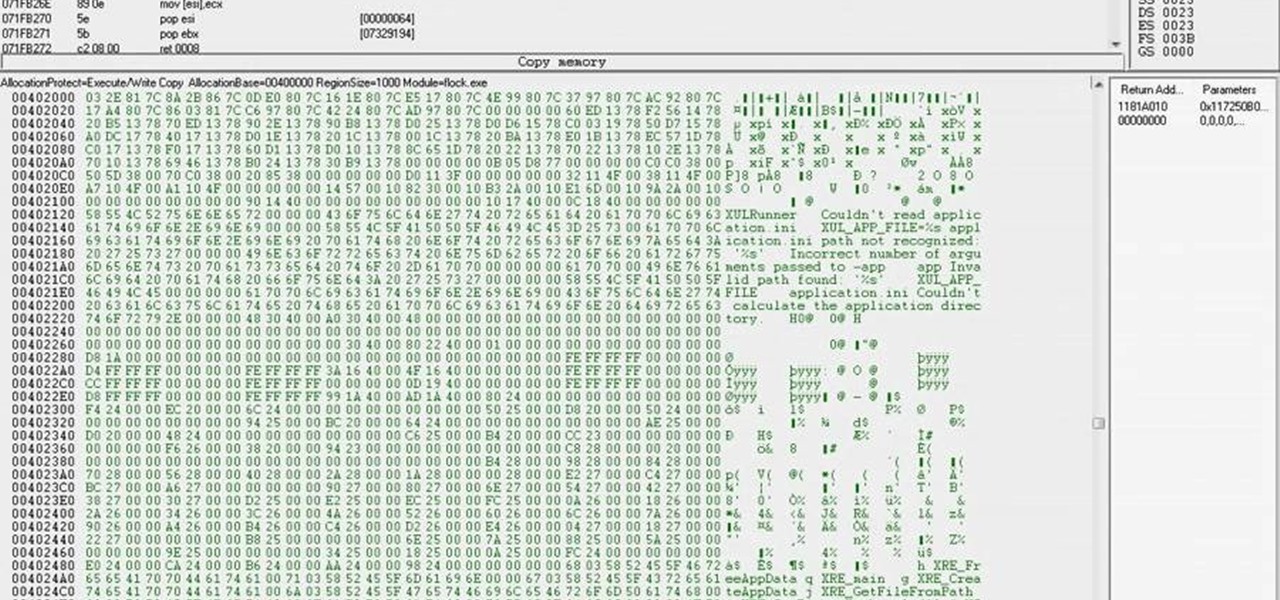
Dispatch your enemies with a single sword strike. This cheater's guide will show you how to smite even the toughest of opponents with a single hit (and a few keystrokes in Cheat Engine 5.5).

How to instantly bond with anyone and persuade them

John White of Southwest Yard and Garden along with Kitty Schafer teach you about bio-intensive gardening. Bio-intensive gardening is the combination of two techniques. Part of the technique involves composting top soil with other coarse organic material into a lasagna style mound. Add 2 inches of straw to the soil and spray with water. Add 2 inches of green material that you have collected from other area of your garden, such as bug eaten greens or specific greens for composting. Then add som...

Getting weird looks from the other dudes at the bar? Maybe because you're ordering a sex on the beach like the other women. Spit out that tropical drink or wine spritzer and throw away your stemware. It's time to put some hair on your chest, hoss.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to build a sign in Photoshop with 3D lightbulbs.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to retouch commercial products in Photoshop.

One of the coolest feature of the 3G iPhone is the high speed, always on, Internet connection. Having a constant connection to the Internet is pretty much a must have for any dot com mogul. The main problem with the iPhone is the screen is too small to do any serious Web surfing. Yes, it’s great for Twitter or checking up on emails but blogging from it is an exercise in frustration. Fortunately, there is a way to extend that 3G connection onto your laptop by turning your iPhone into a wireles...

This software tutorial shows you how you can blend three differently exposed images using Photomatix, and then demonstrate how to use some basic Photoshop techniques to touch-up the resulting image. [Note: the Flash overlay in this video doesn't sync completely with the audio; pausing for a second and then resuming it fixes the problem.]

Excerpts from a presentation by Dr. Simeon Hein at the International UFO Congress, 2005. Dr. Hein is the director of the Institute for Resonance in Boulder, Colorado. The Institute is devoted to the study of subtle-energy sciences including remote viewing, crop circles and related subjects. Dr. Hein has a Ph.D. in sociology and has previously taught research methodology and statistic courses. Dr. Hein first learned remote viewing in 1996 and subsequently became involved in crop circle researc...

Although strains and sprains are not a serious injury, they are still very painful for the sufferer, and the only way to make sure they heal properly is to make sure they get immediate attention.

Losing pictures is a uniquely frustrating experience. You take pictures to remember something, to capture a moment so you can look at it again later. So when you lose the thing that's supposed to be what's keeping your memories safe, it's unfortunate and infuriating. Photo Backup Stick® Universal will keep your pictures safe. Right now, you can get this awesome backup tool for $53.99.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

In late-2017, Instagram rolled out a feature that automatically saves your ephemeral Stories to a private archive. Before that, Stories disappeared into the ether after 24 hours, but not everyone was comfortable losing these precious photos and videos. If you post to Instagram Stories quite often, you can now easily access your history from your account — and you might not even know it.

While there aren't as many improvements compared to iOS 11's Photos additions, the tabs menu in Apple's updated Photos app for iOS 12 was revamped to include "Memories" inside a new "For You" tab that also houses featured photos and effects suggestions. This is also where you see sharing suggestions and all of the albums others have shared with you.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Snapchat offers a rich experience for anyone looking to communicate with pictures in addition to (or instead of) words. There are many ways to share your snaps, from Memories to My Story. You can even draw all over your snaps, creating a unique experience that hinges on your own illustrations. Sometimes, though, you want to customize your snaps in a different way. In a more collage-y sort of way.

Just when you thought Google Glass was dead, it turns out there may be a second life for the often ridiculed device that won't relegate it to the staid confines of factories and repair jobs.

The Guardians of the Galaxy have to be the most fun superhero team to have at a Halloween party. They dance, they break the rules, and they definitely have the grooviest music. So the Guardians are a great bunch to pick from for your Halloween costume — or even for a themed group costume. Just imagine the badass vibe when you all walk into a venue together with Star-Lord blasting "Cherry Bomb" from a portable speaker. Here's a roundup of some of the best Guardians of the Galaxy costume guides...

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

HIV infections persist despite treatment that successfully decreases viral blood levels to the point where doctors can't detect the virus. But that doesn't mean the person is cured. The virus hides in the body, not replicating, just waiting for a chance to jump out of the shadows and reemerge.

With summer just ahead, you, or your children, may be looking forward to some pool time or the water park. When planning water-based fun this year, keep a heads-up for microbes.

Could your fever, body aches, cough, and sore throat be the flu? Soon, finding out may not involve a trip to the doctor.

After California college student Luis Ortiz blacked out and was taken to the hospital in 2015, doctors were startled to discover the reason his brain was swelling—a one-centimeter long, wriggling tapeworm living within a ventricle in the middle of his brain.

Bacteria gets a bad rap. Most headlines focus on the danger and discomfort posed by pathogens like bacteria, but many of the bacteria that live on and in us are vital to our health. Many products out there, called probiotics, are sold with the implication that they're supporting these healthy bacteria that share our bodies — but do they actually work?

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

Remember that feeling when you first took your smartphone out of the box, powered it on, then proceeded to futz around with it for the rest of the day non-stop? If you've owned your device for more than a year, chances are, that scenario is a distant memory by this point.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...