Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stellar call quality.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

The latest iPhone update introduces big features like Live Activities and Clean Energy Charging, but those aren't the only things you'll notice different on iOS 16.1. If you build your own shortcuts in the Shortcuts app, there are a few things you'll definitely want to know about the new software. It's not a massive feature drop as with iOS 16.0, but they are important changes.

It can be very frustrating: You open your Messages app, send an iMessage, and then see that dreaded red exclamation point or horrible green SMS bubble. At this point, you may be curious whether it's just your iPhone or whether iMessage is broken for everyone, but how do you find out?

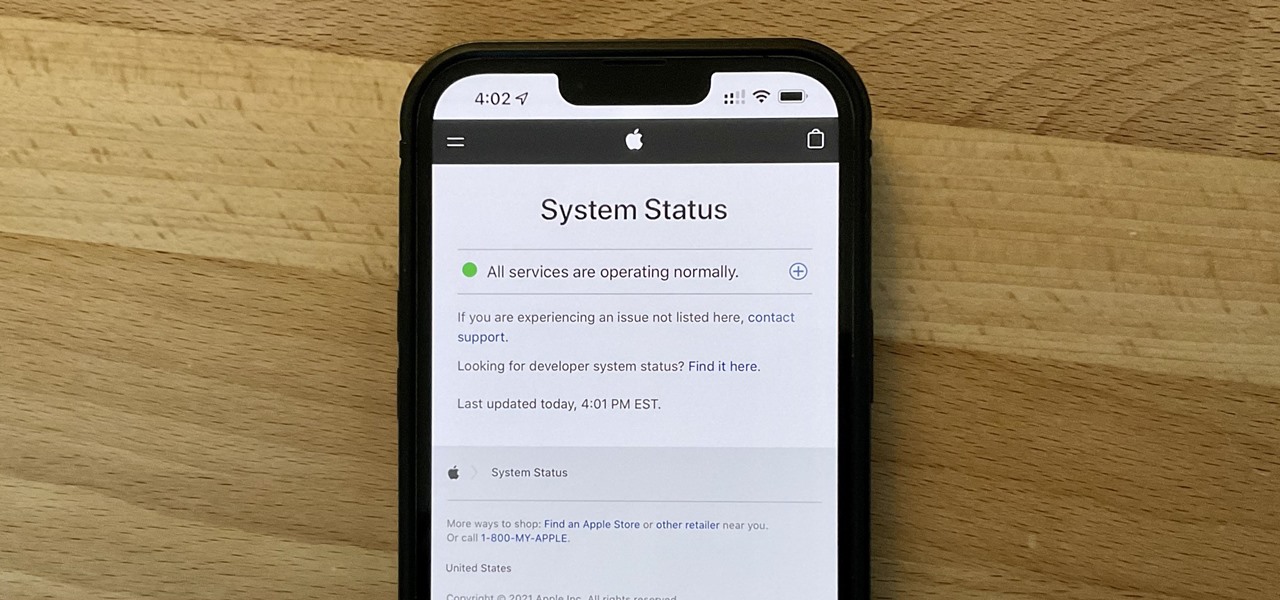
Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.

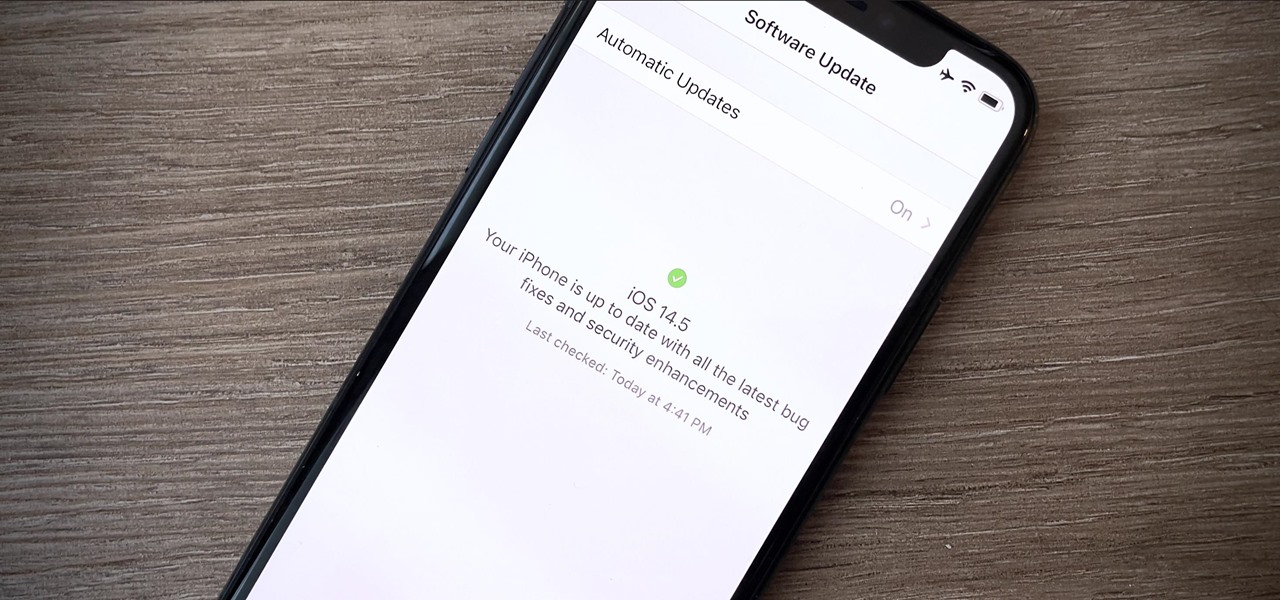
Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

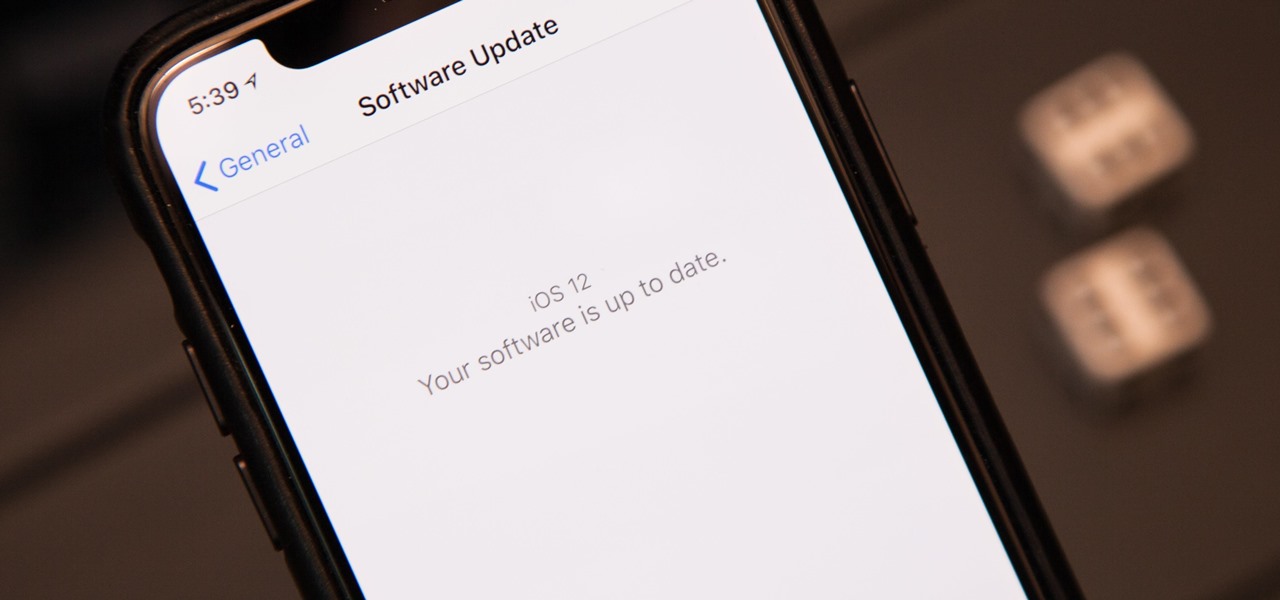
The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveillance – Broadcast, or ADS-B for short.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

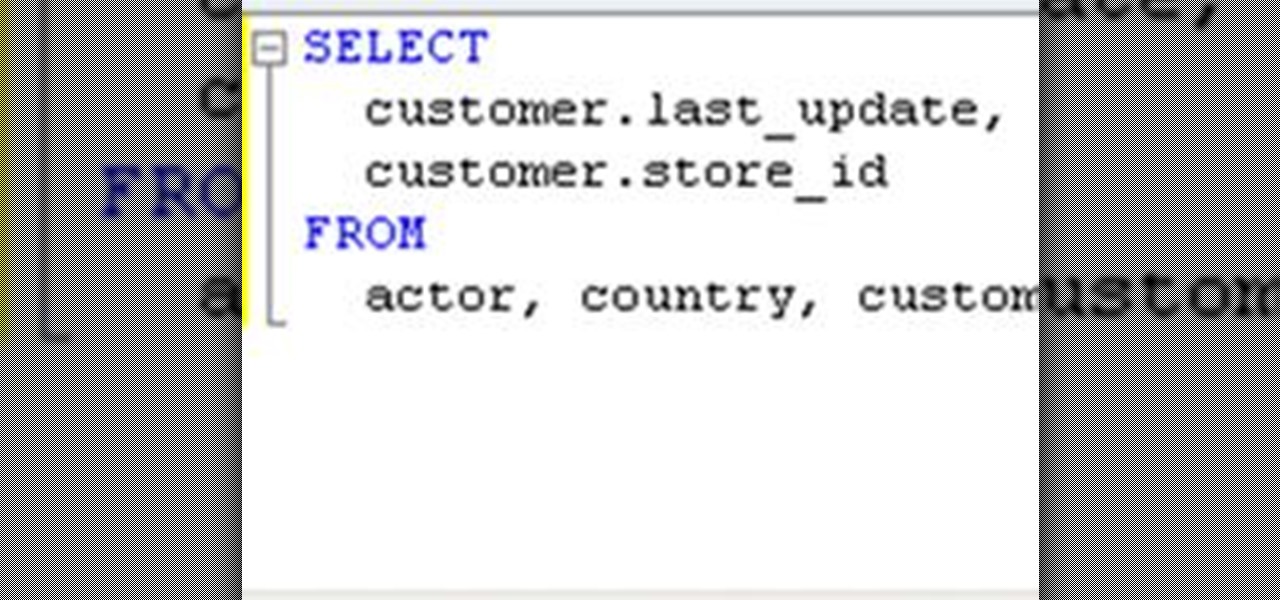
Full-Text search allows you to save large portions of text – even Microsoft Word documents, or other file formats – into your database and perform complex queries based on this textual data while expecting great performance. This lesson demonstrates how to set up Full-Text search paying particular attention to the nuances of setting it up within SQL Server Express. Enable full-text search in an SQL database.

Introduction In this post we will look at how to access a PosgreSQL database in your C/C++ application. It's not as hard as you might think, but you need to understand the procedure and the functions used.

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases.

Introduction PostgreSQL is a very popular Open-Source database management system. It competes heavily with many proprietary and commercial database management systems. More information on what it is and it's history can be found here and here.

In this clip, you'll learn how to use the Entity Framework and RIA Services to migrate data from an SQL database to a Silverlight DataGrid (data grid). Whether you're new to Microsoft's popular web application framework or a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free MS Silverlight programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look. Move data from an SQL da...

Interested in creating your own dynamic, web-based applications using Visual Basic 2005 Express? In this installment from the Absolute Beginner's Series of Visual Basic/ASP.NET video tutorials, how you can connect your applications to databases. You will learn how to enable your application to view and edit data stored. This will allow you to exercise the skills shown in the earlier videos. For more information, as well as tips for being a smarter user of Microsoft Visual Basic, take a look! ...

SQLyog is a Graphical User Interface (GUI) for the popular Relational Database Management System (RDBMS) MySQL. In this Dreamweaver 8 video tutorial you will learn how to create a database with SQLyog. It sounds complicated, but it really isn't. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Create a database with SQLyog and Dreamweaver 8.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.
Looks like someone created a remote exploit using javascript. Pretty scary stuff o.o. Intel Core2Duo cpu cache controller bug PoC | Inj3ct0r - exploit database : vulnerability : 0day : shellcode.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

Interested in creating your own dynamic, web-based applications using Microsoft Visual Web Developer? In this installment from the Absolute Beginner's Series of video SQL tutorials, SQL Server beginners will learn about tables and definitions of data types, properties, keys, etc. in this second video. Find out how table rows, columns, and fields interrelate and whether columns can be empty. For more information, as well as tips for being a more effective user of Microsoft Visual Web Developer...

If you need to build a SQL query, you can choose one of two alternatives. The first and a rather old way is using a console. But if you build your queries in MySQL console, you have to remember all the commands and keys. This is not a convenient way, because query execution is a time-consuming process. Another way is to use some graphical interfaces for MySQL. It can fulfill many developers' requirements, including query execution.

In this ASP.Net video lesson, you will learn about the GridView and FormView controls and how you can use some of the features of these controls to make editing and displaying of database content easier. Work with Gridview and FormView in ASP.Net.

Some cops already have the ability to extract data from your cell phone using handheld forensic devices, but soon police officers will have a new mobile data collection toy to play with—an Apple iPhone. Actually, it's an iPhone-based device that connects directly to the back of an iPhone, which is designed to give law enforcement an accurate and immediate identification of a suspect based on their facial features, fingerprints and even their eyes.
Unless you avoid the news entirely, you've almost certainly heard about the hacking sprees that have been taking place over the past several weeks. Tens of thousands of usernames, passwords and email addresses have been released online for anyone to download. Thankfully, it seems that one kind soul has put all that compromised info to good use.

100% functional LEGO ATM by Ronald McCrae. This bonafide brick bank performs the following functions:

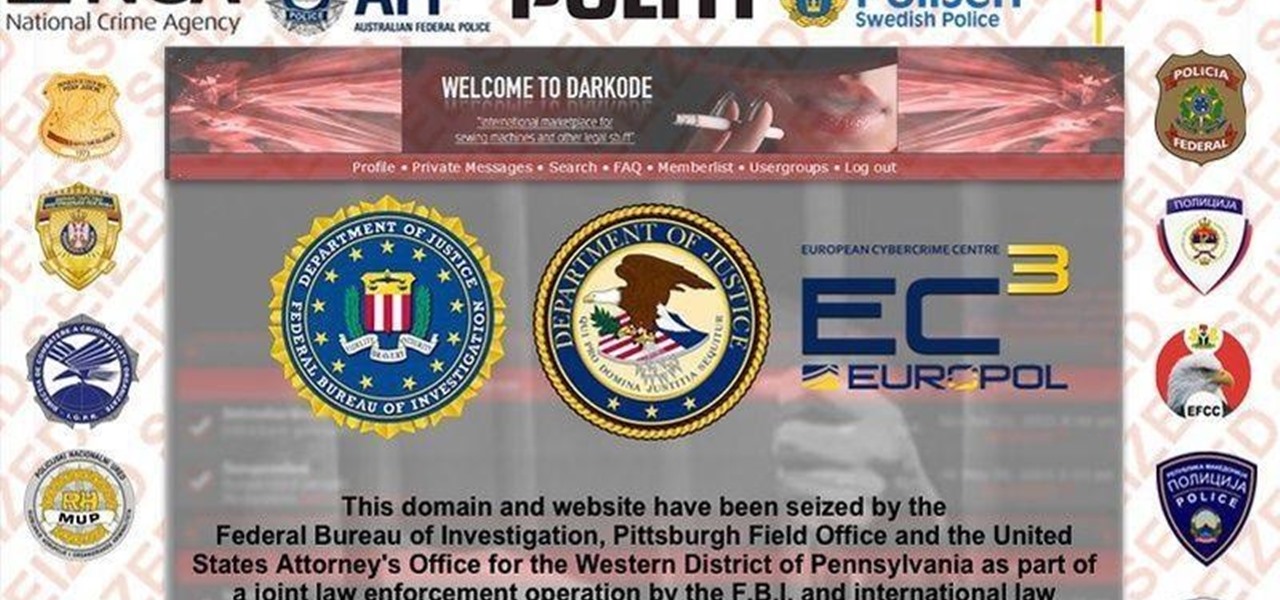
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...

There are two kinds of beer drinkers—those who just want to drink and those who want to enjoy it. The former usually sticks to the same kind of beer, drinking it habitually, while the latter is always on the lookout for new varieties. They like savoring the taste of a freshly poured dark lager and the roasted aroma of a hearty stout and are always looking for that "Holy Grail" of beer—the perfect combination of hops, malt and yeast. Thankfully, there's a mobile application that gets you once ...

Ever had your car broken into? Or worse, your apartment? Ever been pickpocketed? Handheld electronics—iPods, iPhones, iPads, GPS devices, digital cameras—are easy to snatch, light to carry, and useful to most. And when they're gone, they're gone.

The Environmental Working Group has put together a database of most sunscreens. Find a sunscreen that not only protects your skin, but also does not have chemicals that harm the rest of your body (you'd be surprised what some companies put in their sunscreen!). Check it out!

Check out this treasure trove for any sports enthusiast or casual gambler. Microsoft has a database of custom downloadable bracket templates in Microsoft Office (excel mostly) They have everything from soccer to NCAA basketball.

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."

SQL injection is a common web application attack that focuses on the database backend. WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. I plan to use WebGoat for a few future videos. This first WebGoat video will show the basics of installing WebGoat and doing two of its SQL injection lessons. Hack websites with SQL injection and WebGoat.

Wade Bourne of MyOutdoorTV.com shows you how important it is to use a hunting logbook year in and year out. The logbook acts as a database, where you can store information such as:

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.