In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.
Hello everyone! Hope everyone having good day!! I wanted to share an easy way to locate an appropriate exploit from the EDB, get it compiled, and run it all from inside the terminal.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

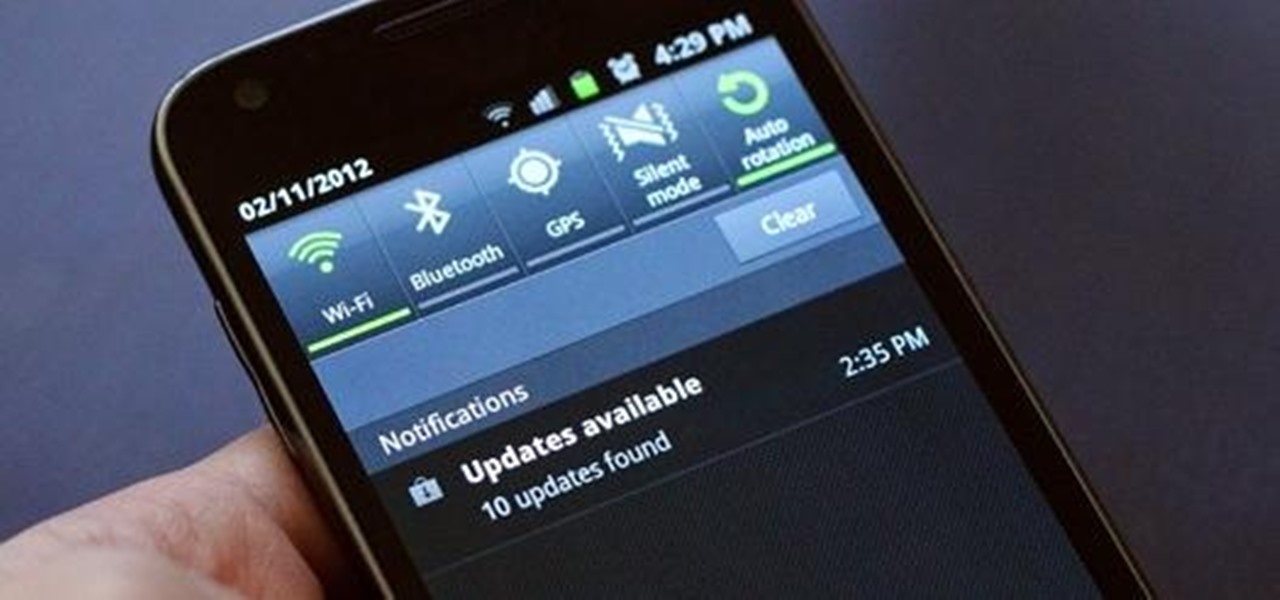
With the Google Play store on your Android device, it's a relatively easy process to check all of your application updates. All you have to do is launch the Market app, go to the My Apps section, and from there you'll be able to see all of the available updates for your applications, which should be positioned at the top of the list. The problem with this process is that many times, you'll go days or weeks and quite possibly even months without checking the Google Play application market, lea...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 20th installment in their joint series of digital spreadsheet magic tricks, you'll learn how to summarize survey data with a pivot table (grouping & report filter), COUNTIFS function (4 criteria), SUMPRODUCTS formula, SUMPRODUCTS & TEXT functions and DCOUNT database function.

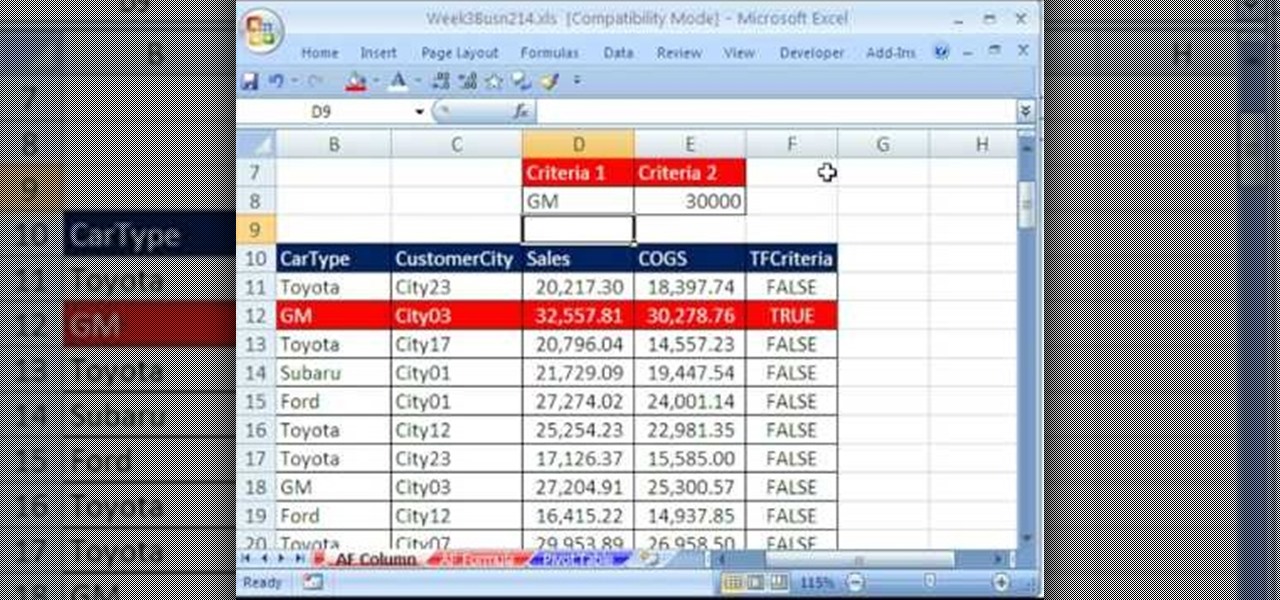
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 19th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about using Advanced Filter to extract data from an Excel List/Table/Database. See these 7 Advanced Filter examples:

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 244th installment in their series of digital spreadsheet magic tricks, you'll learn how to use advanced filtering to extract records from a database (table or list) based on 1 criterion (criteria) and place reesults on a new sheet worksheet.

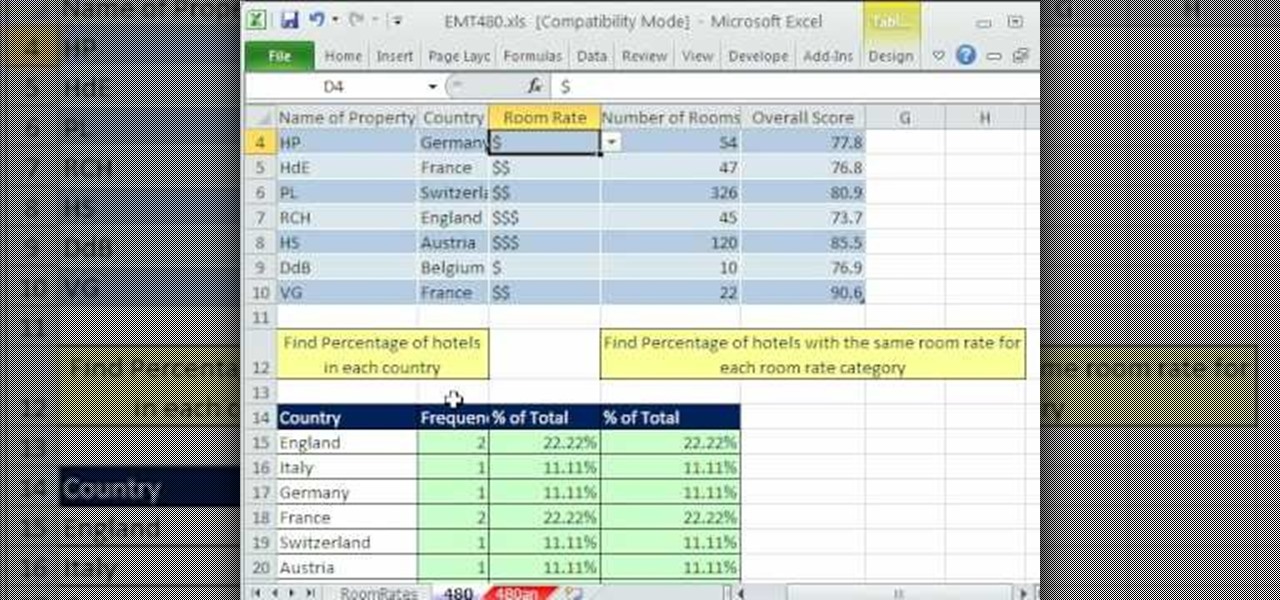
New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 480th installment in their series of digital spreadsheet magic tricks, you'll learn how to calculate a percentage of total from a database data set when the variable of interest is text (word). This is accomplished with recourse to the COUNTIF, SUM & COUNTA functions.

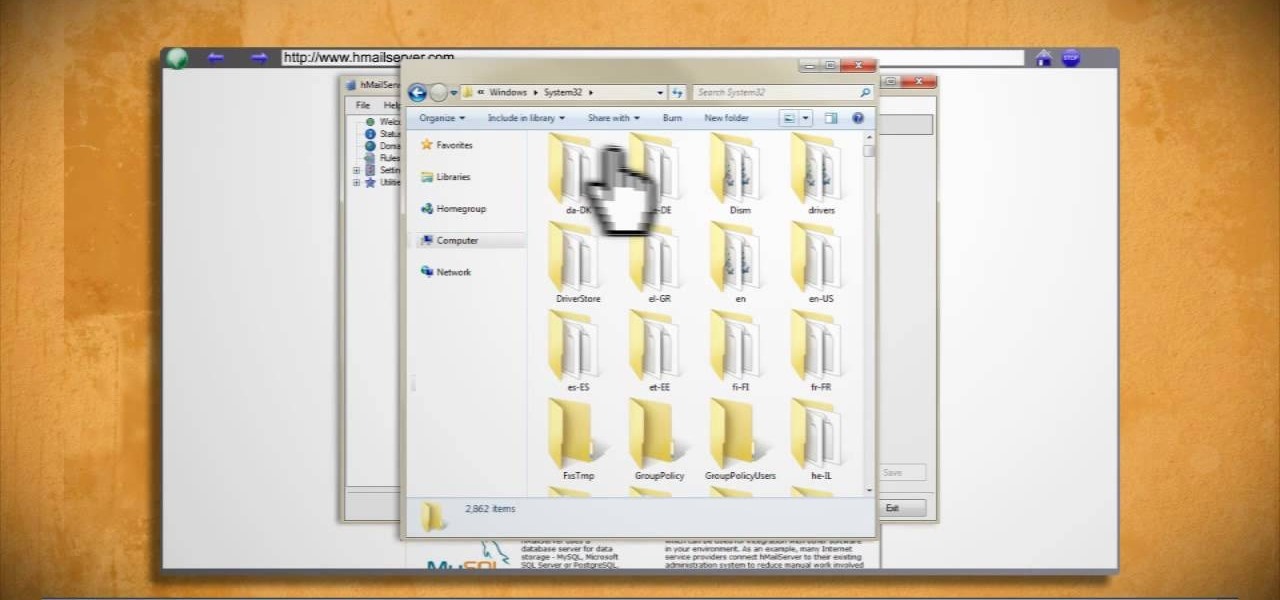
Learn how to make an e-mail server on your home computer to host your own web page and webmail service by following the steps outlined in this video tutorial. You will need a web server, an e-mail server, and a webmail interface. For the server, the most common program is WampServer, which you will need to download. Run through the installation process and grant the program access to your fire. Click on the new icon on your desktop and click Put Online and then Start All Services. This will g...

In this video tutorial, viewers learn how to cite reference books in MLA formats. Citation is a reference to a published or unpublished source. Viewers will learn how to cite an article in an online reference book and an article in a print reference book. The format for the online reference book is:

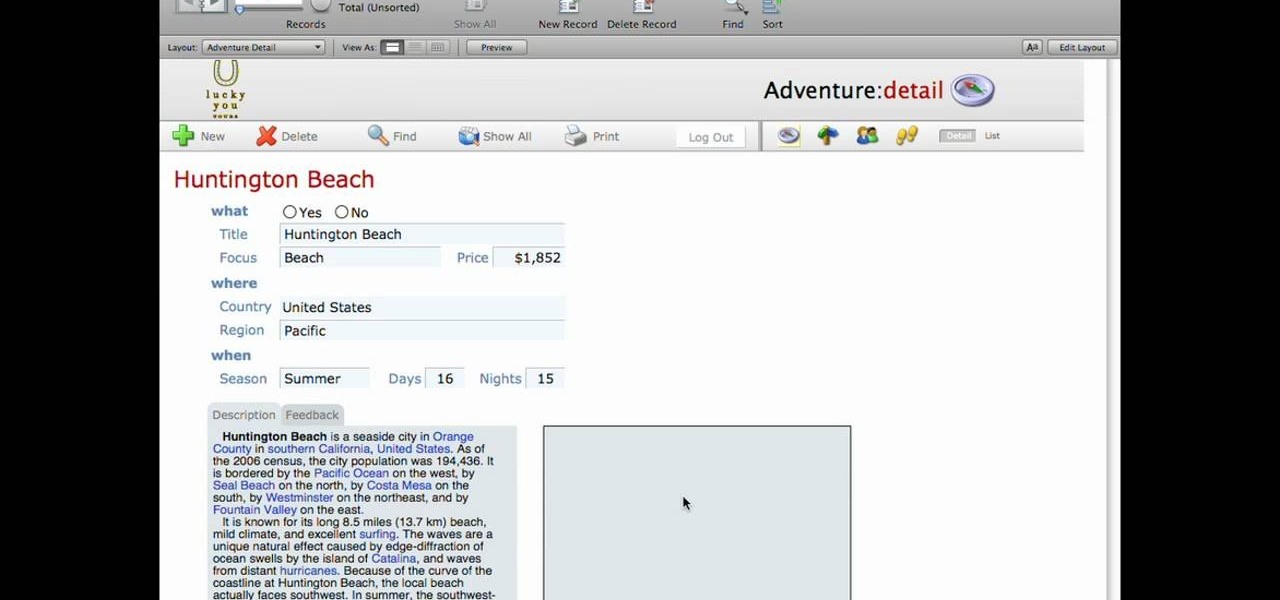
This lynda.com video tutorial shows how to use container fields with FileMaker Pro 10. When you want to create fields in FileMaker database you have the choice on what kind of fields you want to make. Many general fields are self explanatory like text, date etc., but there is a special kind of field called the container field. FileMaker Pro container field is a versatile data type in that it can store any kind of binary data. Container fields can be used to hold binary data in four broad clas...

In this four-part video, learn how to create a CMS with PHP and MYSQL. The basics of a simple CMS are split up in the following four parts:

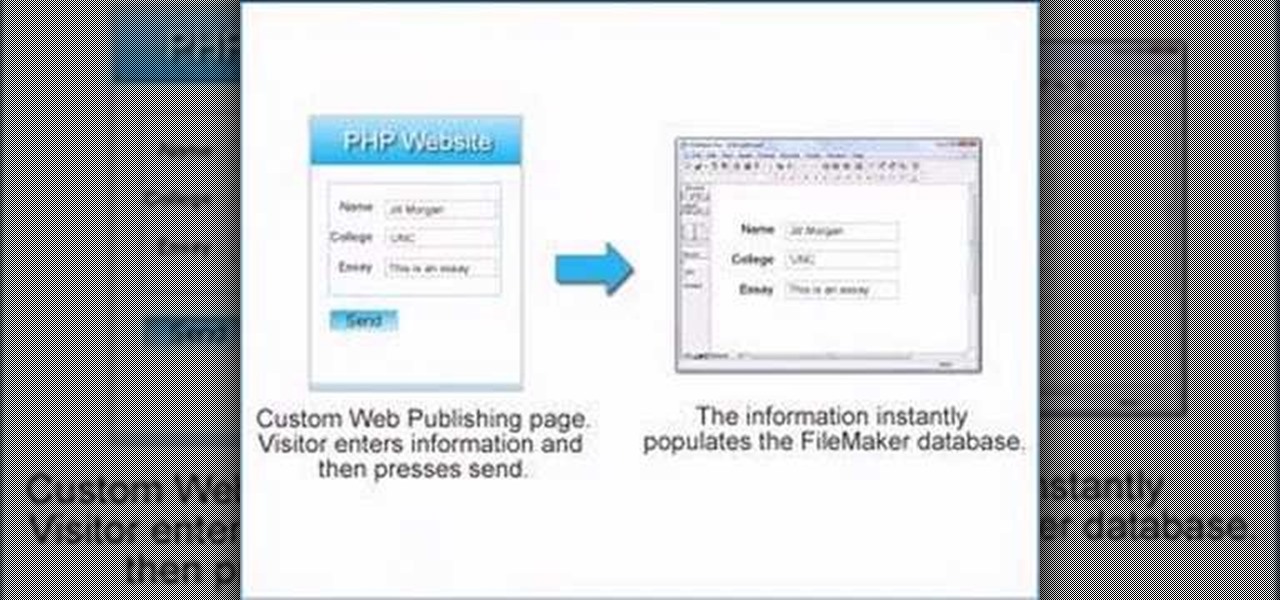
This tutorial demonstrates how to create what is called a complete client-server web application which consist of a Web Application, PHP, and MySQL. The tutorial shows how to automatically generate the PHP necessary to talk to a MySQL database using Adobe Flex Builder 3.

This tutorial on the companion Tech Ease for Mac site shows you how to use Inspiredata to collect, organize, and visualize data using several types of diagrams supported by the program. The movies were recorded on a Mac, but Inspiredata is a cross-platform program so the steps shown should work on the Windows version of the program as well. Inspiredata works like a database system that allows you to add notes and more.

If you're looking for an efficient way to communicate with your online customers or fan base, one way to accomplish this is by setting up a PHP database of people who have signed up with your site, so you can send them email blasts or news updates.

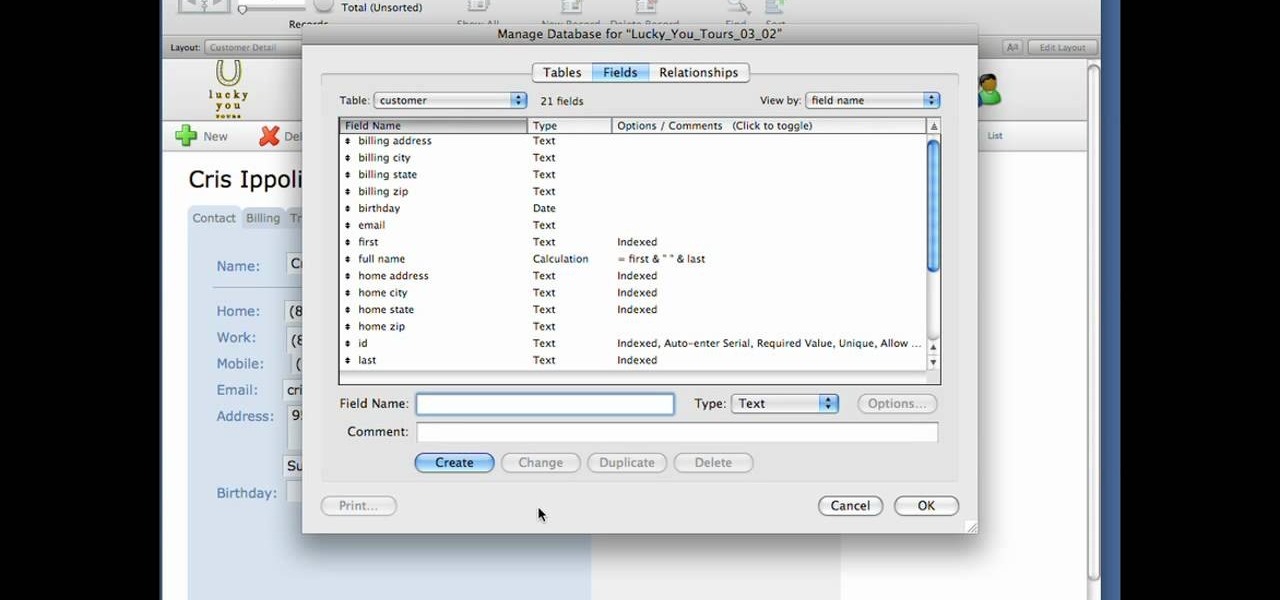
If your into data based business,then this one's for you. Text field's are very much important while making a data based solution in FileMaker Pro 10.You can go to file menu>manage>database and there is the field's tab. Text field is used for storing text and no other such use. Text field's can hold up to 2GB of information. It can help to store raw data and formatting information, i.e., color,point size as well as type face.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

FileMaker hosting and the top two reasons for hosting a FileMaker database are covered in this two part series. The second series is a complete step-by step tutorial for setting up your database for remote hosting.

With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

Welcome back my fellow army of hackers! Today we'll be hacking a website. Hacking is technically not the right word used here. It should be defacing! So we are going to deface a website...

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

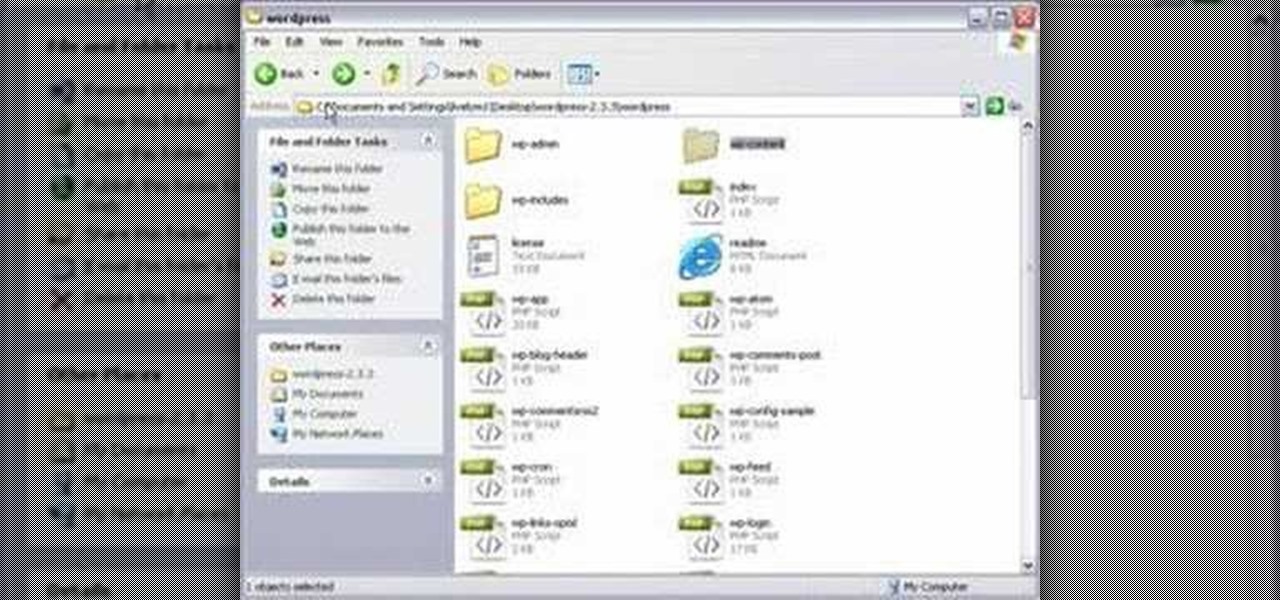
In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

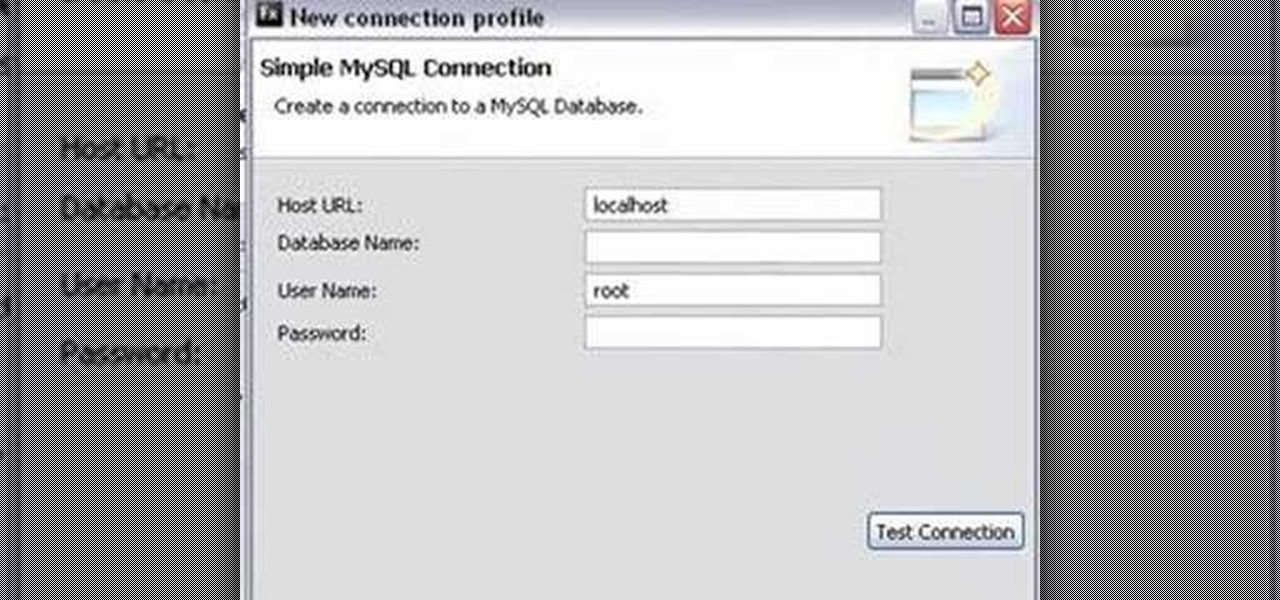
If you're new to DreamCoder for PostgreSQL, one of the first things you may want to know how to accomplish is to connect to a remote PostgreSQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a connection between a given PostgreSQL database and the DreamCoder for PostgreSQL, take a look!