Everyone shanks the ball sometimes in golf and most wonder why they do and how to prevent it. There are two reasons that you shank the ball. One reason people shank is because they are trying to keep the hands behind the ball and it creates such an angle that the only place you can hit the ball is in the shank of the club. Some people also flip the club over at the last second and that creates an angle that causes the shank to hit the ball too. What you want to do is tuck the left arm in and ...

The difference between a professional put and an amateur put is in the finish of the put. The professional moves his shoulders directly parallel to the target line while moving his eyes instead of his head to follow the ball. The amateur swivels their entire body to follow the ball which creates an inaccurate shot. This movement lifts the body which completely messes up a shot. For practice you can practice swinging your putter exactly the same path of a straight line. This will help create a...

In this video tutorial, viewers learn how to cure a push shot in golf with a proper ball position. If the ball is too far from your stance, you will not be able to make full contact. You will hit the ball to the right instead of hitting it straight ahead. Have the ball positioned so that as your body makes it's rotation, you'll catch the ball the moment the club goes down the target line. This video also provides a drill that will help viewers to properly position the ball. This video will be...
Ever wish you can have your own custom stickers? Well its not that hard and you can find everything you need at many major supplies stores. This video will show you exactly how to make professional vinyl stickers to stick anywhere!

In this video tutorial, viewers learn how to perform an outdoor strength training workout. This exercise routine will only require a chin up bar. For each workout, users can choose the amount of sets and reps to do. Users are encouraged not to rest too much in between the exercises. In this video, there are 4 exercises. These exercises are: chin ups, hanging knee lifts, navy seal chin up and a pull up and knee up combination. These exercises will target the biceps, back muscles and core muscl...
In this video tutorial, viewers learn how to do a body weight workout for beginners. Body weight workouts are recommended for those viewers who don't have access to a gym and would like to exercise. Body weight workouts require no equipment, only the mass of your body. Users work 30 seconds on each exercise. The body weight exercises are: wide squat, plank, split squat, side plank (both sides), hip raises and extending legs and push ups. This entire workout targets the glutes, abdominal muscl...

In this video tutorial, viewers will learn how perform the "Spiderman dumbbell curl". The name refers to the similar stance that Spiderman makes when she shoots webs. This exercise targets the bicep muscles. It will stimulate your body to gain muscle and lose fat. Start by sitting on an incline bench. Chest should be open, keep entire upper arm stationary, bring in palms, push elbows back a bit and palms should be facing towards shoulders. The exercise should be done slowly with 3 second posi...

In this video tutorial, viewers learn how to perform frontal splits in yoga. The frontal split is a stretch that targets the hamstring muscle. Begin by extending your right leg forward and flex the toes out in front of you on the mat. Very slowly and carefully, slide your right leg forward until you feel some resistance. Once you start to feel a stretch in your hamstring, you need to get your fingertips firmly planted into the floor or else on top of a block. This video will benefit those vie...

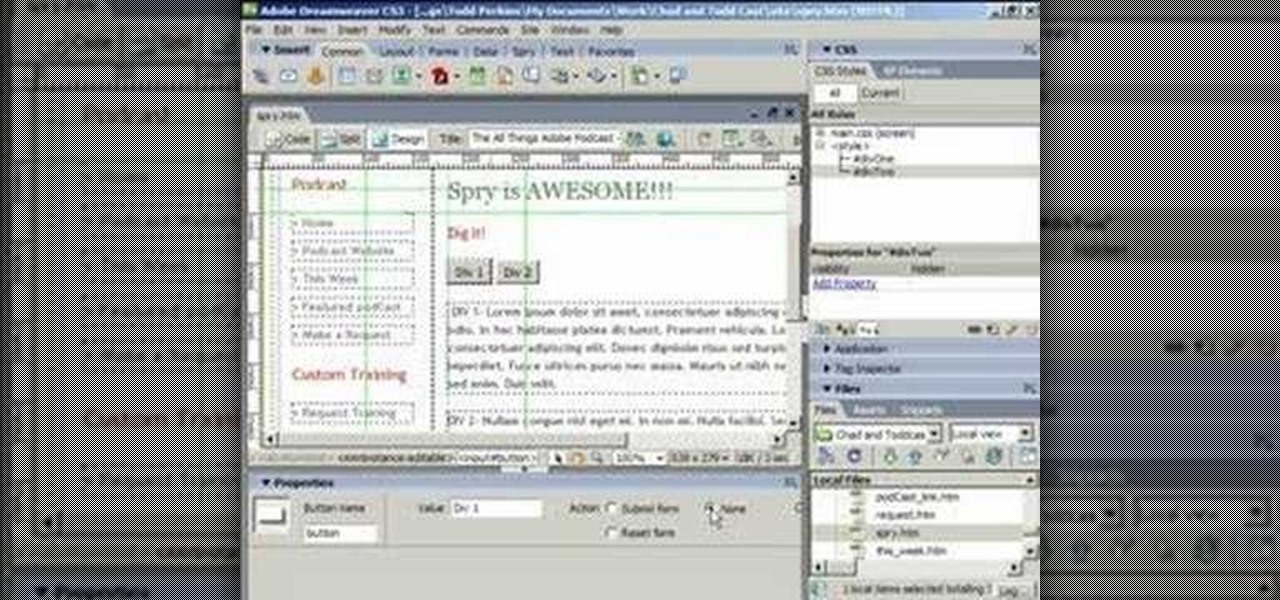
ChadandToddPodcast teaches you how to use the spry framework for AJAX in Dreamweaver CS3. This allows for effects on the page to happen, without the need for the browser to refresh. You start with a simple .html page. You have 2 buttons and 2 div tags with text in them. Div 1 and div 2 have the visibility property set to hidden. Click on the div 1 button, go to Tag inspector and click behavior with a plus. Click Effects and choose Appear/fade. The target element should be div 1. Fade from 0 t...

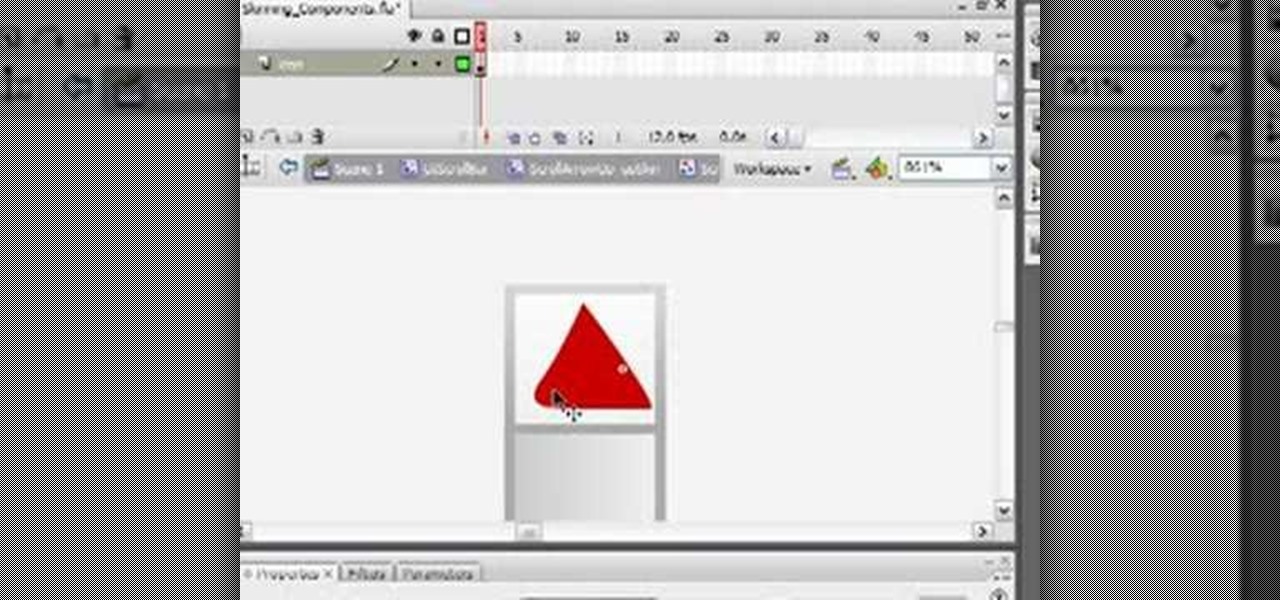
This video illustrates to create the skin components in Flash CS3. The procedure to create the skin components are, If you set an FLA to export for Action Script 1, or Action Script 2, the components panel will automatically refresh with the components that you are familiar with from Flash 8 Professional. If you change the file to export for ActionScript 3.0, you will see the new components. Flash will always show you all the components that you are able to use given your export target. In Fl...

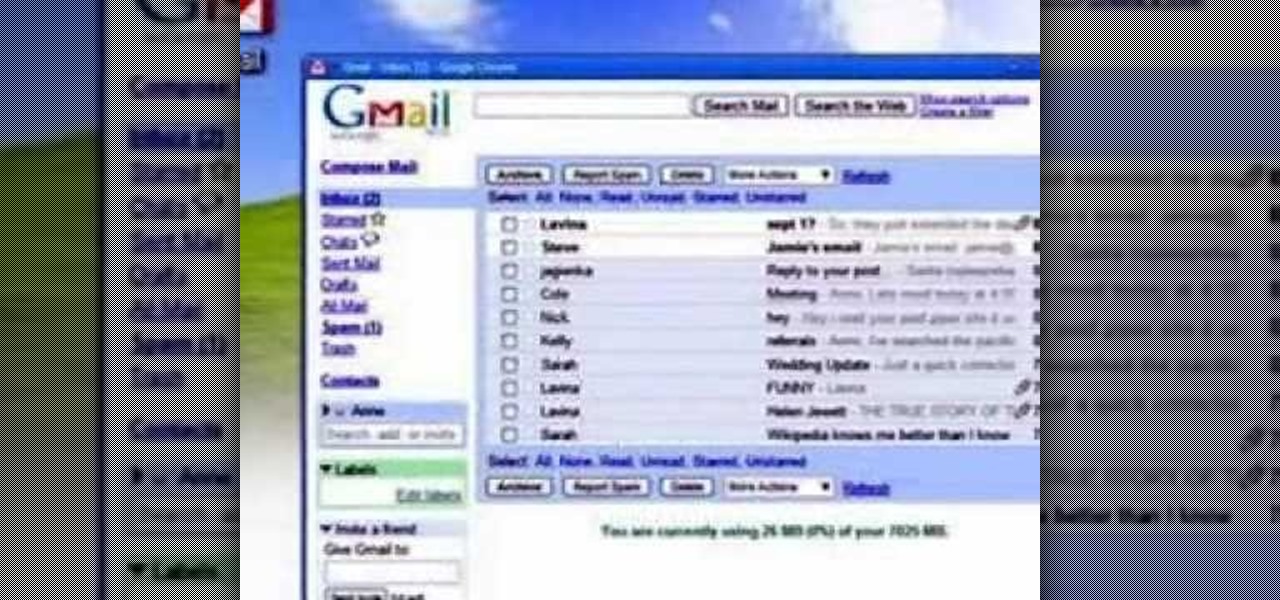
In this how-to video, you will learn how to access Gmail automatically every time you click a mail to link in Google Chrome. In order to do this, you must have a computer that has the Google Chrome browser, as well as a Gmail account. First, prepare Chrome to use extensions. Right click the shortcut and add the following command in the target path area. After this is done, add the new extension. A crx file from the blog must be downloaded. Install the extension and now you will be able to ope...

Paul Bolzoni is one of the best exterminators of New York City. Watch as he talks about some of his experiences as he goes around New York helping people with the bedbug epidemic.

Hacking into computer systems to steal passwords could be a bit complicated for the average everyday joe, but for all of your tech illiterate folks out there, there's any easy way to get that password, and all it takes is a camera.

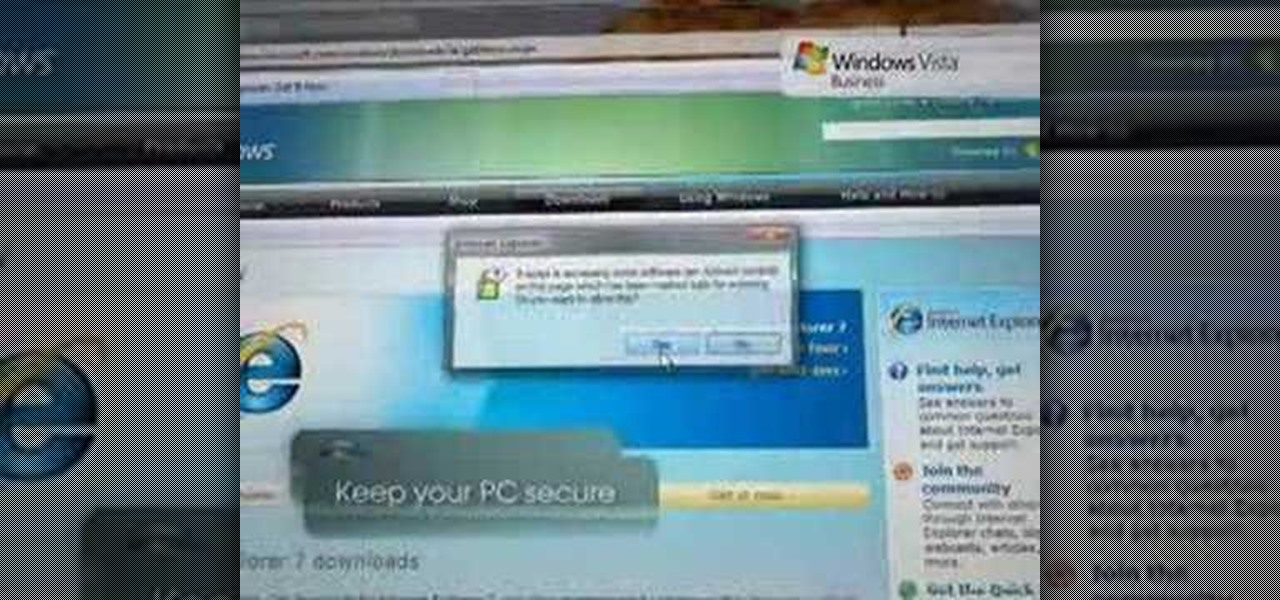
Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

In this video Chris Pels shows how to create an MSBuild project that orchestrates the execution of the aspnet_compiler and aspnet_merge utilities for an ASP.NET web site. First, learn the fundamentals of the compilation process for an ASP.NET web site and the role of the two command line utilities. Next, see how to create an MSBuild project file and the primary elements such as PropertyGroup and Target. Then learn the details of how to execute the aspnet_compiler and aspnet_merge utilities fr...

A hooking knee strike is legal in Thai boxing, not kickboxing. Learn the skills of Muay Thai in this tutorial on competitive kickboxing moves. When performing the

All day we use our calf muscles when we walk, run, and climb stairs. As a result calf muscles are popular massage targets. Learn the art of giving massage in this diet and health how-to video.

Pilates is great for strengthening and toning the body. This piltes how-to video illustrates the Single Leg Stretch exercise. It targets the transversus abdominus, rectus abdominus, obliques, scapular stabilizers and hip stabilizers.

This Pilates Side Bend exercise is used to enhance lateral mobility of the spine. It primarily targets the transversus abdominis, obliques and scapular stabilizers. Attention should be paid to the abdominal contraction to maintain rib connection and prevent the hips and shoulders from rotating. The cervical spine should stay aligned with the thoracic spine.

This pilates how-to video illustrates the Pilates Spine Twist exercise. This exercise is great for spinal rotation.

This pilates how-to video illustrates the Obliques exercise. This exercise is great for rotation, flexion and strengthening pelvic stability.

This pilates how-to video illustrates the Obliques Roll Back exercise. This is a challenging rotational pilates exercise for athletes and advanced clients.

Firebug is an essential Firefox extension for web designers and developers. You are able to quickly target any element on a page to see the markup, the CSS, the layout, and the DOM in an instant. Not only can you see all of this juicy information, you can edit and see the results directly in the browser window. This makes Firebug the go-to tool for debugging CSS trouble. Also indispensable for Javascript programmers. So all you Internet website designers out there, pay close attention to this...

training with a head target wall mirror. Learn how to use target mirrors to practice jabs and hooks in this free video for boxers.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.