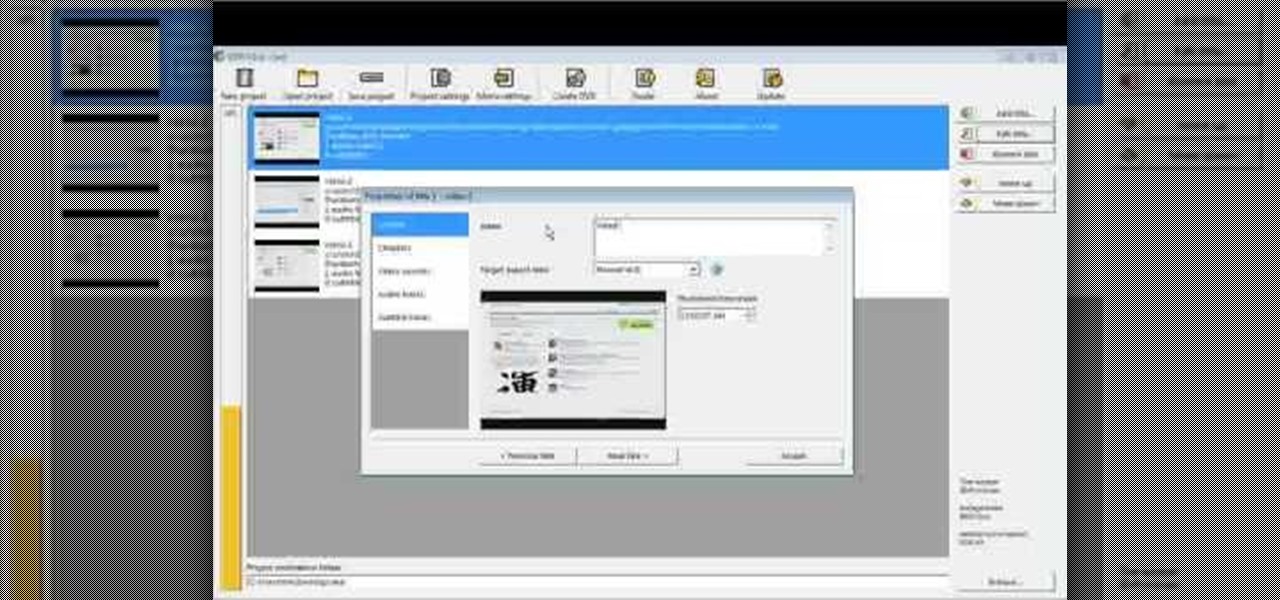
This video tutorial from Foreclosureresearch presents how to burn video files to a playable DVD using DVD Flick application.First you need to download and install free software called DVD Flick.You can find it at DVD Flick.Once it's installed, run the program. First thing to do is to set your Project Settings. Click Project Settings from top menu. From Project Settings window you can name the project, select Target size (size of your DVD), Encoder, Thread count, DVD format, bitrate, playback ...

Golf Link demonstrates how to identify whether your golf swing plane is correct. The swing plane is the path described by the golf head that controls the direction that the club head is traveling through when it impacts the ball. An on plane swing will have the club head directly traveling towards the target at the point of impact. That and a square face will make a straight shot. If the swing comes inside or below the plane, it will produce a hook shot or a push shot. A swing that comes outs...

You can manipulate the AF fine-tune on your Nikon DSLR in order to optimize the sharpness and resolution of your lenses. This is a great tool for achieving the highest picture quality possible.

You can organize your closet with simple drawers and shelves or racks that you purchase at a discount store such as Target. Outside of your closet you can have drawer space (use transparent drawers) by labeling your own drawers with large labels that you have written the contents of the drawer on and placed this at the front where it will be visible. The drawers can be divided into short sleeved sweater tops, long sleeved sweater tops, tanks, vests, short sleeved tees, long sleeved regular to...

This video shows you how to use an exercise band to do bicep curls, triceps extensions and shoulder raises along with some fun extensions of these basic exercises. When doing the bicep curl with the band it is very important to ensure that the band is firmly secured under your shoe, so that it does not slip forwards and snap. Once the band is secure you must curl the arms up towards the shoulders, keeping your elbows bent and close to your sides. The arms are still working in a negative resis...

This is a Computers & Programming video tutorial where you will learn how to take screenshots on Mac OS 10. 5. Andrew Grant says there are several ways of doing this. The easiest way is to hold down the Command and Shift key and press 3. You will get a screenshot of the entire desktop. To take a screenshot of a selected area, hold down the Command and Shift key and press 4. The cursor now changes into a target. The figures next to it are the values of the pixels from the left hand top corner....

In golf the grip is the key essential feature and this video shows you the most common mistakes. It is intended for a right handed golfer - left handed players should note that the opposite applies. Let your hands fall to your sides and let your fingers fall to the grip. The video shows a weak, neutral and strong grip. The strong grip shows a V shape formed by the left thumb and forefinger pointed to the right shoulder. The palm of the right hand should face the target. You should let the fin...

In this tutorial, Zain will explain how to download free mp3's from your PSP to your PSP. All you need is a wireless connection, and a PSP. First, go to your internet browser. You can enter on Kohit for downloading free music. There you have search box where you can write the title of the song you want. Type it there and then click 'go'. A song list will appear on the web page. Click on the song you want to download. Now click on 'Download now'. Go to options and click on 'Save Link Target'. ...

Do you win the prize for messiest room in America? That's a difficult contest, but how about messiest room in your house? It’s time to clean your room, so do a good job in the shortest amount of time and get your parents off your back.

Most use wireless computer mice these days for their computers, but there are still people stuck on wired optical mice, especially in an office environment. Those people are our targets. As pranking someone's computer may be frowned on, peripherals are fair game, and this prank from Kipkay takes their wired optical computer mouse and turns it into a foul-smelling smoke machine.

Fantasize about role playing? One of the most popular venues for role playing medieval fantasy is the board game, Dungeons and Dragons. Get a group of three or four together and have a blast!

Fishing is relaxing, but not if you hook yourself because you couldn’t cast a reel! You Will Need

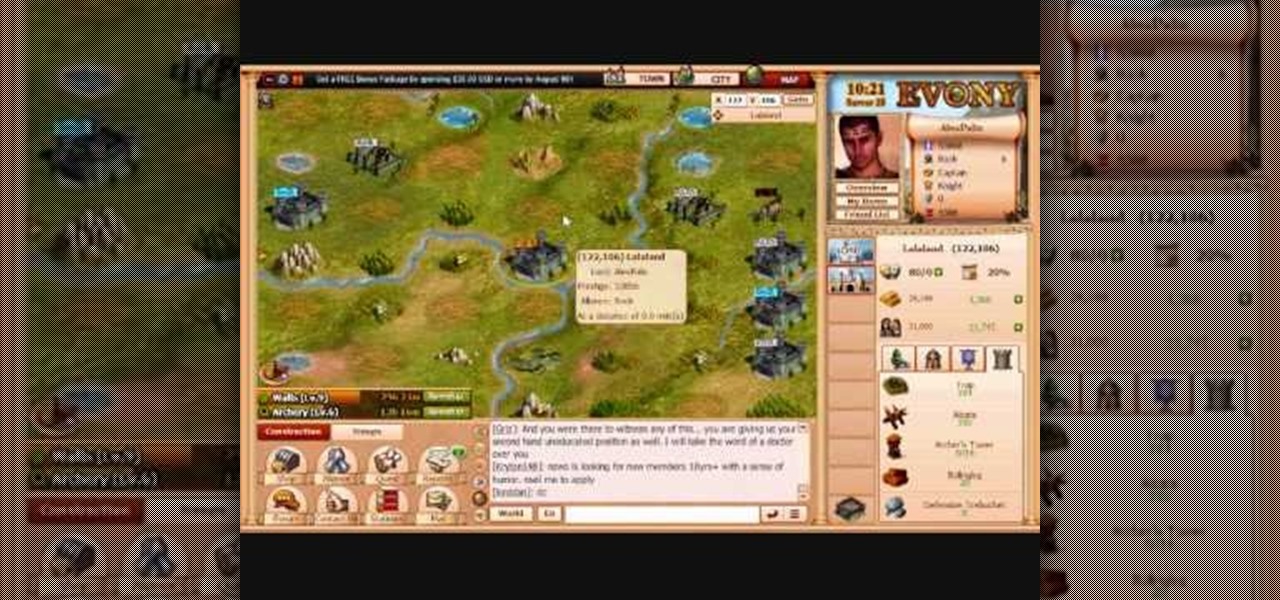
Learn everything you could possibly want to know about the internet, multiplayer game Evony with help from alexstewart2. Watch this video tutorial to learn how to farm rose, lion, cross, and nation medals in Evony.

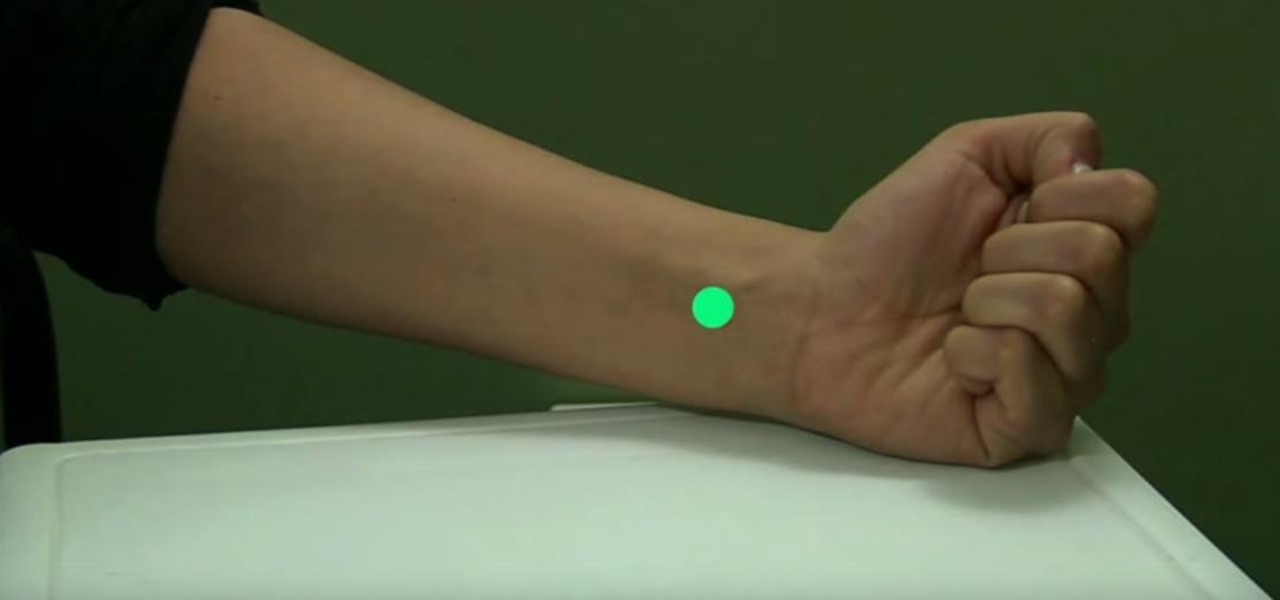
Stop that horrible sensation with a form of traditional Chinese medicine known as acupressure. Watch this video to learn how to relieve nausea with acupressure.

Have you ever had the urge to throw a ball at someone, but knew you could never do it? Regardless if for merely a gag or out of frustration, we all have that someone we would love to use as target practice, but know fully well we can't purposely try to hurt another person. Well, we have the solution here...

This pilates how-to video illustrates the Lateral Flexion exercise of the Side Leg Series. It is obviously a great exercise for lateral flexion and balance.

Learn how to do rope hammer curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do cable reverse raises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do medicine ball scoop tosses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do seated arnold presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do dumbbell lateral to front raises. Presented by Real Jock Gay Fitness Health & Life. Benefits

When Treasury Wine Estates released 19 Crimes Snoop Cali Red this summer, named for its new partner in wine, rapper Snoop Dogg, it already came with the brand's signature AR-enhanced label.

While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

Viewing and reading content on websites is inherently harder to do on an iPhone due to the relatively small display. Even if you have an iPhone XS Max or 11 Pro Max, you'll probably struggle sometimes to read through tiny text while browsing online. Thanks to a feature found within Safari's view menu in iOS 13, your eyes can rest a little easier.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

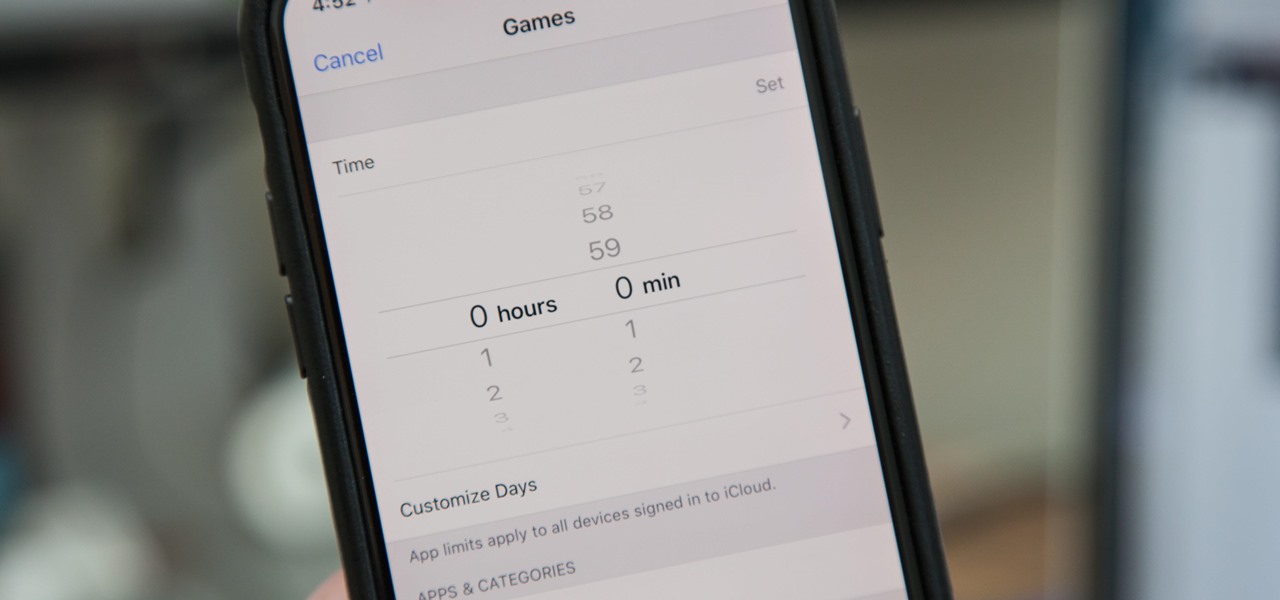
Most of us have, at one point or another, found ourselves glued to our smartphone in a trance-like state, totally unaware of what's around us. Well, Apple has a way to curb overuse with an awesome tool for iPhone starting in iOS 12. It can help nudge us away from our phones to spend more time attending to real-life matters.

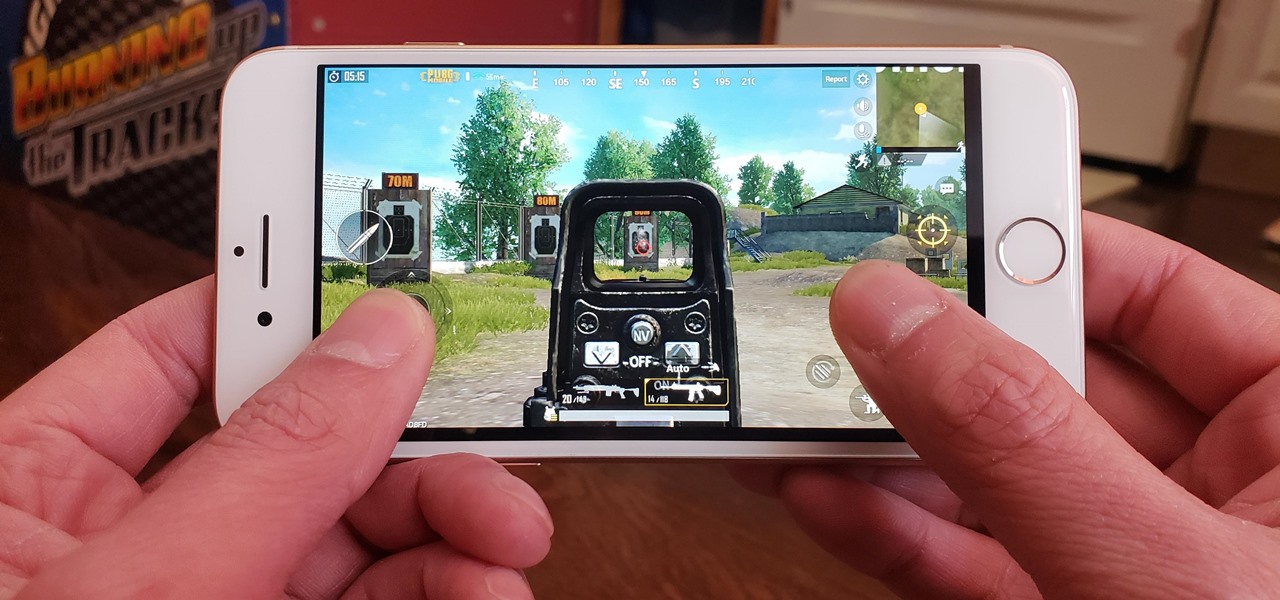
PUBG is continually getting better and more intuitive with each update, and version 0.4.0 is no exception. Besides a new training map to help you practice and a faster-paced arcade mode for on-the-go gaming, the newest version of PUBG now includes a feature that exclusively caters to iPhones from the 6S on up.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

With a new installment of the Saw horror series opening in theaters nationwide this weekend, Lionsgate is betting its ad dollars on immersive advertising to sell tickets.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

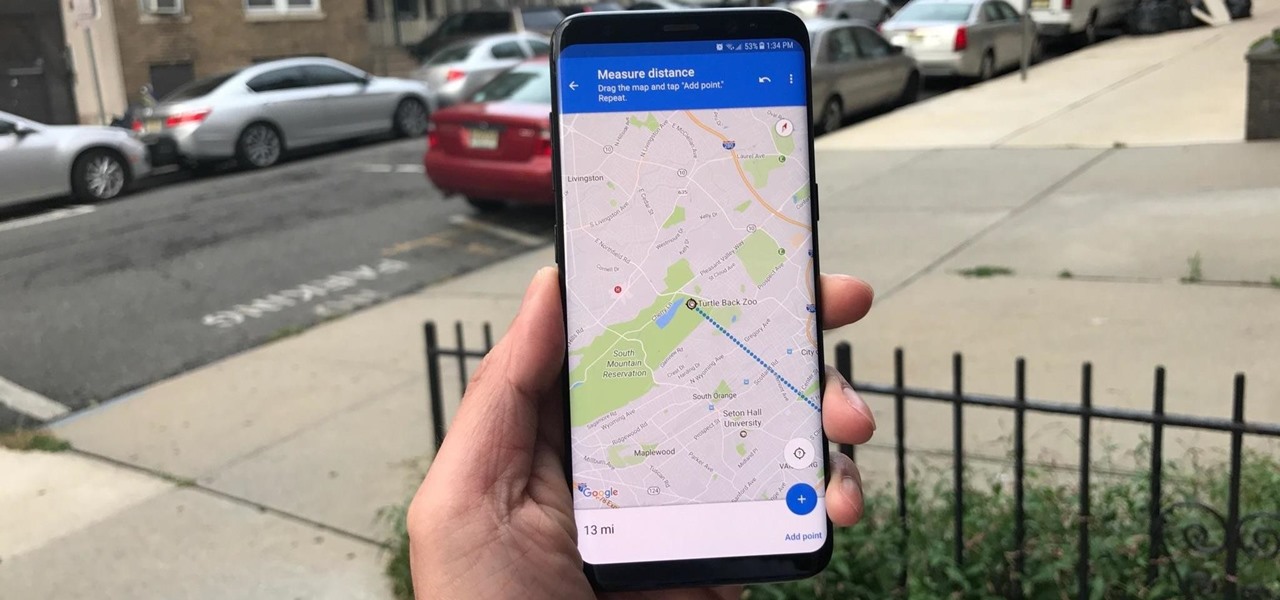
If you want to find out the linear distance between your hotel and a landmark or restaurant you want to visit, Google Maps has a great feature that lets you quickly measure the distance between two or more points. It's perfect for getting an idea of how far places are in relation to each other, which can help you plan trips more efficiently.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.