Minecraft is the most basic and barren open sandbox building game. There are a limited number of materials and recipes to craft. But with these few building blocks, people have been able to creatively build some amazing structures and cities. There is a physical limitation, but the beauty of the game is turning that limitation into a strength.

In case you've been living under a rock for the last couple of years let me begin by explaining who banksy is. Bansky, is the pseudonym of one of the most popular street artists in the world. banksy has put his work up in various major locations in the around the world. this Includes places like on the isreal/palestine wall, Goverment buildings, inside virgin records stores, and has even managed to slip his work into the lourve and many other major muesems (by gluing his paintings to the wall...

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

One of the most important marketing tools we should always be developing to help reinforce our brand is our references. Just like many companies use their client list and client references to build credibility and confidence for their products and services, we should also leverage our references to build credibility and confidence in our capabilities and brand. Sometimes reference checks are just a formality, but in most cases potential employers (i.e., potential clients) use reference checks...
Microsoft office 2010 is the successor version of office 2007 and is code named as office 14. It is the first 64 bit version of office which is only compatible with Microsoft service pack 3, Windows vista and windows 7. It was released on April 15, 2010. It is the first Microsoft application which offers free online version of word, excel, PowerPoint and one note. These can be easily used with all the popular browsing software. The various functionality which are added in office2010 are descr...

make a box to skate on and put 2 holes in the box and cover it with paper thats the same color as the would so its not noticable and under the box have fircracker or a flower bomb and as soon as whom ever lans on the box and gets halfway across set of the fircrackers

Check out this interactive video tutorial from Verizon Wireless on the Samsung i730 mobile phone. If you have just purchases this sleek cell phone, here's your chance to learn everything you can possibly know about it.

Snapshot: 12w08a brings us a few nice things a few things I'm not so sure about and a few things I just hope Mojang doesn't incorporate into the next official update.

Throughout this integral guide, I'm going to aid you along the path to bigger and better builds. Often times, people just jump in and build, but we mustn't hurry things if we want our builds to be all the more satisfying when they are finished. Building the actual builings should be the easy (and the most simple step in any great build), but we have to start with what's underneath your pixelated feet.

The latest in the Legend of Zelda series, Skyward Sword, released a few short weeks ago to very little fanfare. I have no idea why that is, because the game is absolutely gorgeous and pretty darn good. Maybe it was the fact that Nintendo forced motion controls in to this one, or maybe it was because everyone is busy playing Skyrim/Modern Warfare 3/Battlefield 3. Whatever the reason, if you even remotely like the Zelda series, give this one a whirl.

Aesthetic Houses: What are they? If you've played Minecraft for some time now, you most surely know how hard it is to build a great looking house to live in, that meets both your vision of your dream house and expectations for functionality. This brings us to the definition: in terms of Minecraft, its a structure that dosen't compromise beauty and appeal for functionality.

Speech recognition software made it easy to search Google on your smartphone, and Google Goggles made it easy to find answers from camera snapshots on your device. But now Google's bringing similar technology straight to your desktop, and with faster results—faster than Google Instant.

Video games consoles have long wanted to be more than just consoles. Nintendo Japan called the NES the Famicom because they wanted to make it the sole family computer. Obviously that didn't work out, and most efforts to make consoles into all-in-one entertainment systems have had similar fates. Sony has done the best job with the Playstation consoles, probably because they have experience with other types of electronics that most video game companies do not.
Fads, Fiascoes and Good Stuff in FrontierVille This Week The second in a series of weekly columns.

Chris Burden's latest piece is a portrait of L.A.'s hot mess of traffic, entitled Metropolis II. The artist has constructed a miniature highway system, complete with 1,200 custom-designed cars, 18 lanes, 13 toy trains and tracks, and a landscape of buildings made with wood block, tiles, Legos and Lincoln Logs. Burden tells the New York Times:

If you have any little ones in your life (or you're simply a grown-up kid yourself), Just Bento has has posted Maki's Top 10 Bento Rules for Back-to-School. Rules listed below, click through for full explanations.

You may notice the bonus bar in the upper righthand corner of your screen. This bonus is meant to give you coins on top of what you're already getting from the game. You DO NOT need to click on the stars and coins, etc that pop up unless you want to get this extra bonus. They will be added to your loot automatically once they fade.

A tutorial showing how to send messages in a Windows-based network without any programs. Send messages on a Windows network with the cmd prompt.

Learn to make your own custom message box in Visual Basic. Program a message box in Visual Basic.

A rollover status message can be quite helpful to the user. In this Dreamweaver 8 video tutorial you will learn how to create one. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Create a rollover status bar message in Dreamweaver 8.

This has been something a few people have been messaging me about on my Youtube account so this tutorial shows you how to download Flash games. It is really easy and requires no coding. Just follow the steps and you will be on your way.

This tutorial is for Ubuntu 10.04 users who want to tether their iPhone 4 (software version 4.2.1). No jailbreak needed! You have two options - you can tether through USB, or tether through Bluetooth.

Graffiti is a great way of getting your message out to the masses. The earliest known graffiti dates back to 30,000 years ago and used the traditional apply-paint-to-wall technique. Though our paint now comes in cans and not from scavenged berries, the actual graffiti process hasn't really evolved from those first cave paintings.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Taking great photos doesn’t mean you have to invest in an expensive camera. By learning a little bit about photography and the camera you have, you can use a simple point-and-shoot to capture amazing pictures. Try out these tips to begin!

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Last week, I started a weekly feature on Scrabble World called Scrabble Challenge, where you can solve a few (hopefully) challenging word puzzles. Normally, these will be on Fridays, but today I have a potentially unsolvable puzzle for you to try and solve, in addition to the upcoming one...

Making your way into an online community can be really exciting. Some life-long friendships and lasting romances begin in humble chat rooms and message boards. But for the novice internet user, one of the biggest hurdles can be trying to figure out just what people are saying to one another.

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?

In this Motivation & Self Help video tutorial you will learn how to organize & manage your work emails better. For many people, sorting through and managing emails is a real challenge. You will learn what to watch out for when you write an email. The nature of the emails you receive partly depends on the emails you send out. If you write vague or incomplete emails, you will not receive a reply or get the reaction you expected. You must follow these rules while writing emails. In the 'To' fiel...

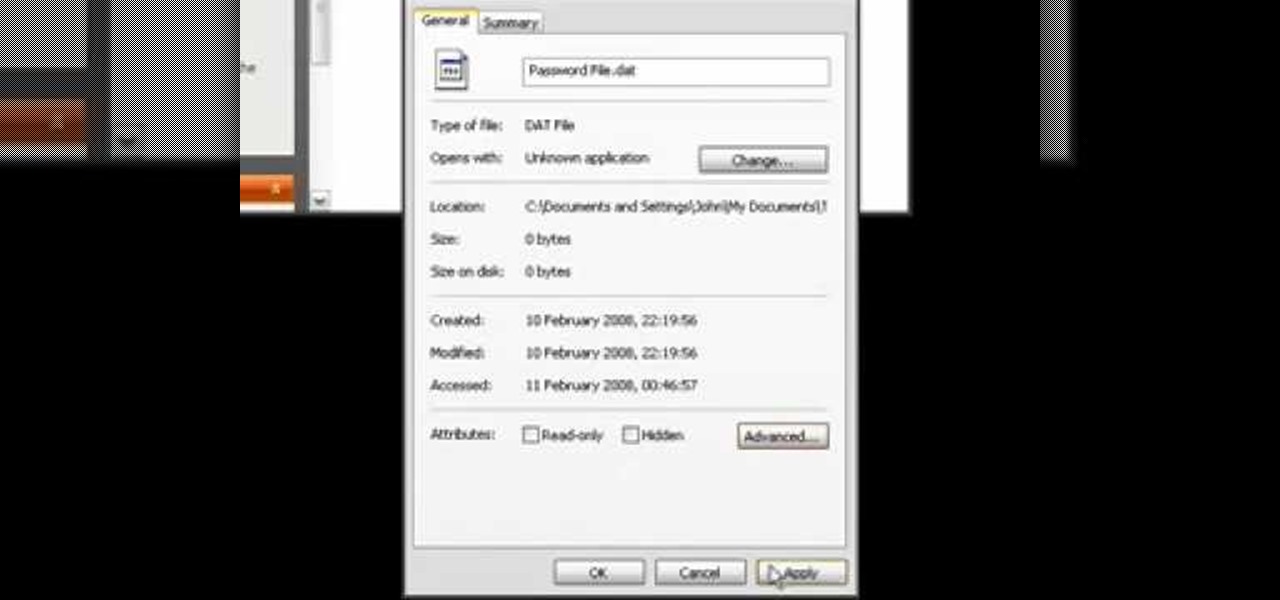
If you have files on your PC that you don't want other window's accounts to be able to access, you can encrypt them. Right click the file that you want to encrypt and select properties from the drop down menu. Once the properties page comes up, choose advanced. Now choose Encrypt contents to secure data and click ok. Now you click on apply. Select encrypt the file only and click ok. Hackers and administrators will not get an access denied message when they try to open the file. To make things...

There are so many fun and exciting goals in FrontierVille. They just keep on coming and getting more complex!

Want to stick it to your mobile carrier by porting your cell number to Google Voice? Now you can! On Wednesday, January 19th, Google Voice began allowing select users to transfer their personal numbers to Google Voice for a one-time fee of $20. Though the feature is still in limited release, Google has stated that they intend to make the feature available to all Google Voice users "in the near future." Terrific, right? Not entirely!
Moscow, May 21 — Some Western countries are still considering a military operation against Iran as an option over its nuclear programme, a Russian minister said Sunday.

There's no denying the coolness of an iPhone. But what if you pulled a homemade wooden cell phone out of your pocket instead? You'd probably be the talk of the town. If you like that idea, then make it a reality by building your own cell phone!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.