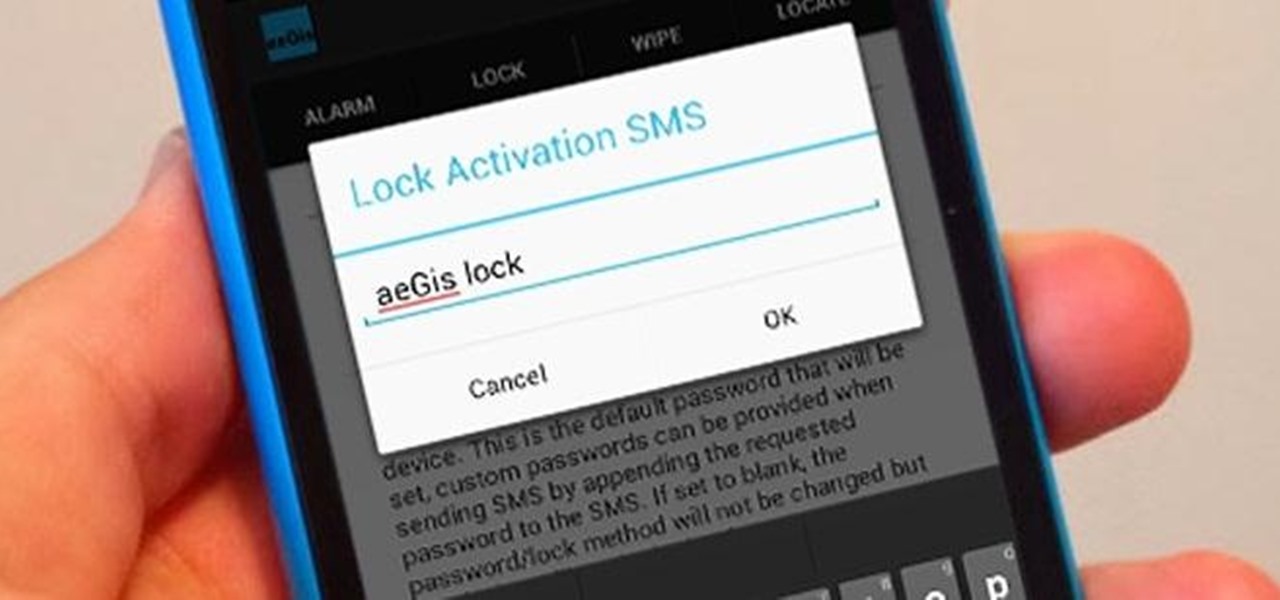
The great thing about security apps (other than the obvious) is that there is an abundance of them littered throughout the Google Play store. Cerberus, Got Ya!, Avast! Mobile Security, Norton Security & Antivirus, and Android Lost Free are just a few of the gems you can find in the plentiful sea of security apps for Android. Once in awhile, though, a new security application comes along that stands out from the rest, like AeGis.

The time is near—Messenger will finally kick the bucket come March 15th. So, if you're still using Windows Live Messenger for all of your IMing needs, it's time to finally make the move over to Skype, which Microsoft bought back in 2011 for a cool $8.5 billion. If you've been using Messenger, you probably already received the mass email that Microsoft sent out warning of the end date. Microsoft is looking to make the transition as smooth as possible. All you have to do is download the latest ...
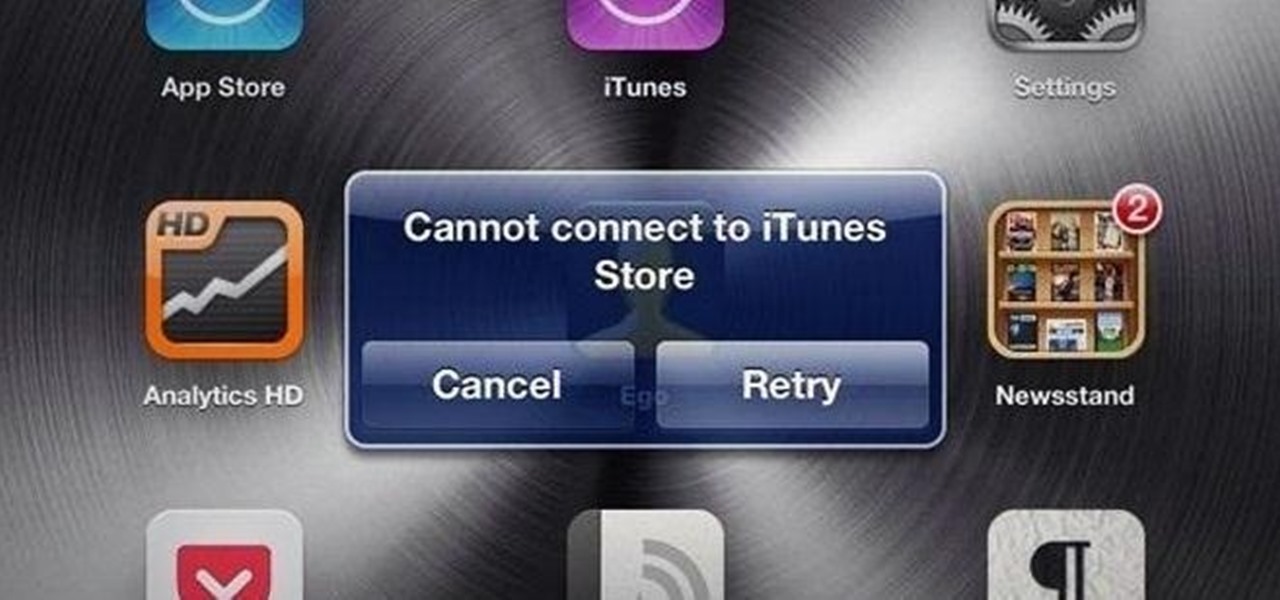
Since iOS 6 was officially released yesterday, several bugs have been reported, including issues with Wi-Fi, Passbook, and battery life (although Apple has apparently fixed the Wi-Fi bug). Some users are also having problems connecting to the iTunes Store, which is probably insanely frustrating because the first thing you want to do with a new OS is try out new apps. Luckily, there's a way to fix this by tweaking the date and time settings. Open Settings, then go to General >> Date and Time. ...
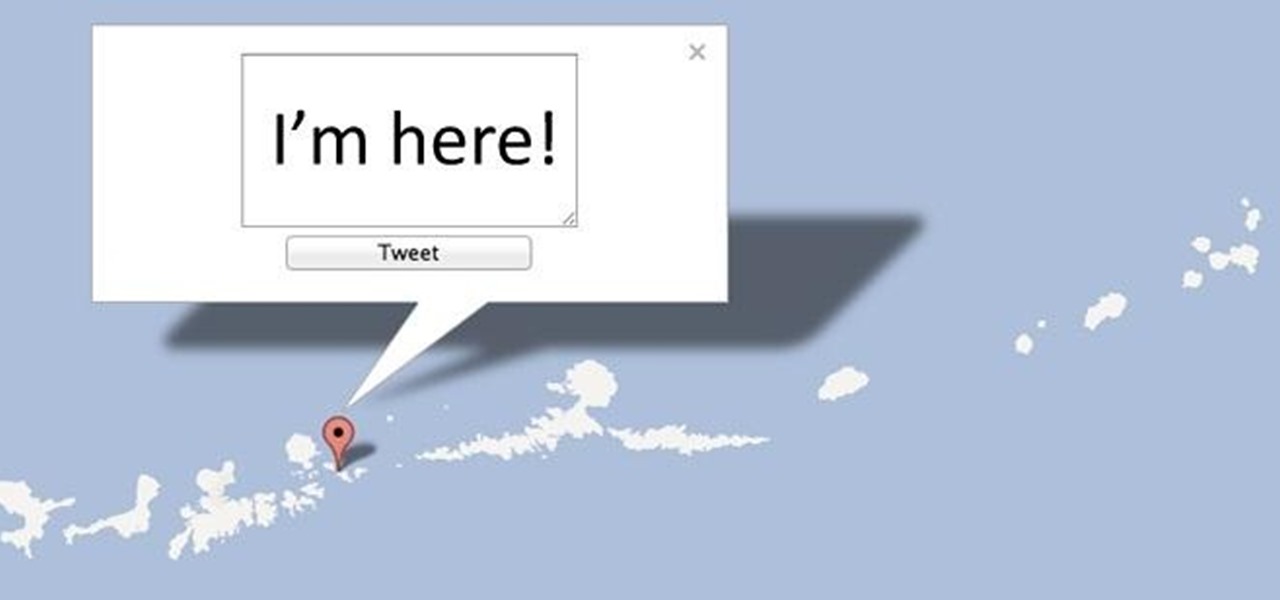
There are plenty of reasons not to use location information when you tweet, whether you're trying to stay safe or just don't want your crazy ex showing up while you're in line at the grocery store. But a new website called 'Please Don't Stalk Me' could actually make broadcasting your location work to your advantage—it lets you tag your tweets with any location you choose, anywhere in the world. Playing hooky? Send a tweet from 'home' to take care of any suspicion from your boss and coworkers....

The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...

Finally, what appears to be a fair and worthy competitor to the iPhone: Google's Nexus One. Unfortunately, not much competition concerning the price- runs exactly the same amount as the iPhone.

Austrian composer Peter Ablinger has created a "speaking" piano. Ablinger digitized a child's voice reciting the Proclamation of the European Environmental Criminal Court to "play" on the piano via MIDI sequencer. Apparently, the computer is connected to the piano, which analyzes the human speech, and then converts it to key-tapping.

Swedish advertising company, Rolighetsteorin, recently created musical stairs reminiscent of Tom Hanks and Robert Loggia's beloved FAO Schwartz piano scene in Big. The campaign is for Volkswagen, though I'm fuzzy on the connection between the two.

Cobalt blue, permanent red, and lemon yellow tube paint is useful for painting roses with watercolors. Find out what supplies you need to paint roses and other flowers with watercolors in this free watercolor video lesson. Paint a rose with watercolors - Part 1 of 10.

Make your own personalized coasters using Scrabble tiles! You design them, so they can say anything you want them to! Pick a theme and make a set or make each coaster completely different from the rest.

In this article I am going to show you how to quickly and easily make a professional looking trailer.

Christmas is just a few days away, which means everyone is out shopping for last minute gifts. But wait— you still need some Christmas cards! The stores are going to be packed and Hallmark's going to have huge lines— so now what?

When your business is in constant communication with different companies using letter paper, one of the more essential things that you need is your own stationery set. This is made up of business cards, envelopes and letterheads which you need when you do corporate mailing.

You've probably heard about Rep. Greg Walden (R-WA) tweeting in Morse code back in December. .-- .. .-.. .-.. / -.-. .... .- .. .-. / -.-. --- -- -- / .- -. -.. / - . -.-. .... / ... ..- -... / --... ...-- ... / .-- --... . --.- ..

We haven't seen an emoji update for iPhone since iOS 15.4, which gave us 112 new emoji characters, but that's finally changed with the release of iOS 16.4. Here are all the new emoji you get after installing the latest software update.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

When I was unemployed I looked for different ways to make money. Most of that work was connected with online stuff; I’ve tried writing content, refreshed my old Photoshop skills and even created postcards, but then I realized that my passion to music can bring me more money than all of the other work. I was an active member of a few musical forums and started to add affiliate links to my posts instead of simple ones, so they can be profitable.

The widely used expression "free as a bird" intimates an enviable existence: delicate, yet mighty wings transporting to destinations no human could so breezily venture. But despite their fanciful, superhero ability, in truth, the avian race leads one of the most difficult existences in the animal kingdom. Yes, birds have existed for eons—they likely evolved from small dinosaurs of the Jurassic period—but for these creatures, life can be ruthless.

Not long ago in Rome during a Master’s Tennis Tournament something remarkable happened. In a tightly contested game, American Andy Roddick challenged a linesman’s call on a ball hit by his opponent. The remarkable thing about this incident was that Roddick argued against his own interest. He insisted that the opponent’s ball had landed inside the line and that he, Roddick, should NOT be awarded the point. Spectators applauded as if they’d witnessed a miracle. Imagine! Sportsmanship in a profe...

Wedding themes are no rarity, but a SCRABBLE wedding? I never would have guessed, until I came across "10 Ways to Incorporate Scrabble Into Your Wedding" at CasaSugar. Now, I'm one of the biggest SCRABBLE nerds out there, but I could never see myself getting hitched amongst SCRABBLE tiles and SCRABBLE cakes and SCRABBLE cuff links. I'd also be afraid that none of my guests would actually come if they knew SCRABBLE was the theme. Hell, it's hard enough to get any of my friends to play a simple...

I have always wanted to mess with people's heads, at those self-service registers.

The trend of online video sharing came to the mainstream with popularization of YouTube, which let users view, submit and share video clips. YouTube started off in the year 2005, and quickly became one of the most visited websites on the internet. Sensing the emerging trend, large companies like Google joined the trail and launched their own video sharing sites (Google later bought YouTube).

This is a very simple, but very funny prank to play on your friends using Windows. Creating the file

Smartphones are crazy awesome. You can do your banking, track your children, find directions, and even pretend to have a mustache. The only thing that these personal supercomputers are missing is physical interaction with the environment.

As some of you Mad Science readers will remember, we recently covered the separation of water into hydrogen and oxygen using electrolysis. Passing a current through water can rend it apart, but we can also recombine that oxygen and hydrogen to make electricity! This is the principle behind those vehicles run by hydrogen fuel cell engines.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Oh Data, You so Awesome! We are going to use Node.JS to gather us some data. Given nodes plethora of well abstracted network abilities and it's deep evened nature, it will make quick work of plugging into various data sources and gathering / making good use of said data.

Earlier in the week, Obama’s attorney general stated something that is quite alarming. “In this hour of danger, we simply cannot afford to wait until deadly plans are carried out, and we will not,” Eric Holder said during a speech at Northwestern University’s law school in Chicago. It's a very ambiguous statement. Why do people talk like this? Why can't they just talk straight to the point? Well, most of the time it's to hide something. Take a look at this video: What do you think of that! Th...

In this article, I'll be showing you how to make a simple yet effective static electricity generator. Basically, this device allows you to carry a constant static charge on your body and discharge it on anything grounded or of opposite polarity. The electricity generated is around 8-10 kV, at a very low current. The shock is enough to startle your friends, just like a static shock from a trampoline or carpeted room. You'll need a little experience in soldering and circuit design to build the ...

Insight Description: In our government class, each student was required to participate in any branch of government from local such as working with your community representatives; state; working with your senator or an organization and federal; which you can entreat in a presidential campaign. The total number of students who participated was Twenty-one and each individual needed to complete at least Ten hours or more.

Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group website.

Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.

In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorithm), then the text to be encrypted. The program takes the key and text and inputs it into the "cryptograph" or code-based algorithm from PyCrypto. PyCrypto can use 16, 24, or 36 character encryption keys, but for the sak...

It's once again Monday, which means it's time to highlight some of the most recent community submissions posted to the Math Craft corkboard. Since two of these posts were on polyhedral versions of M.C. Escher's tessellations, I thought we'd take a look at building a simple tessellated cube based off of imitations of his imagery.

By now, most of you have updated to the new Xbox look. Just as expected, it's got some great new features. The dashboard looks great and Bing integration is awesome, but I'm very unhappy about the new Netflix interface. It's awkward, slow, and half of the items don't even load correctly. I can't even play some movies. And the instant play feature is kind of annoying. When I first chose a video, I was hoping when it instantly started playing that it was a trailer, à la Zune. Alas, no.

Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do not show up on time, we have to go backwards and catch everybody up. This wastes time and will also make other users' experience less enjoyable when they have to watch and listen to the same thing 100 times. Punctuality as...

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

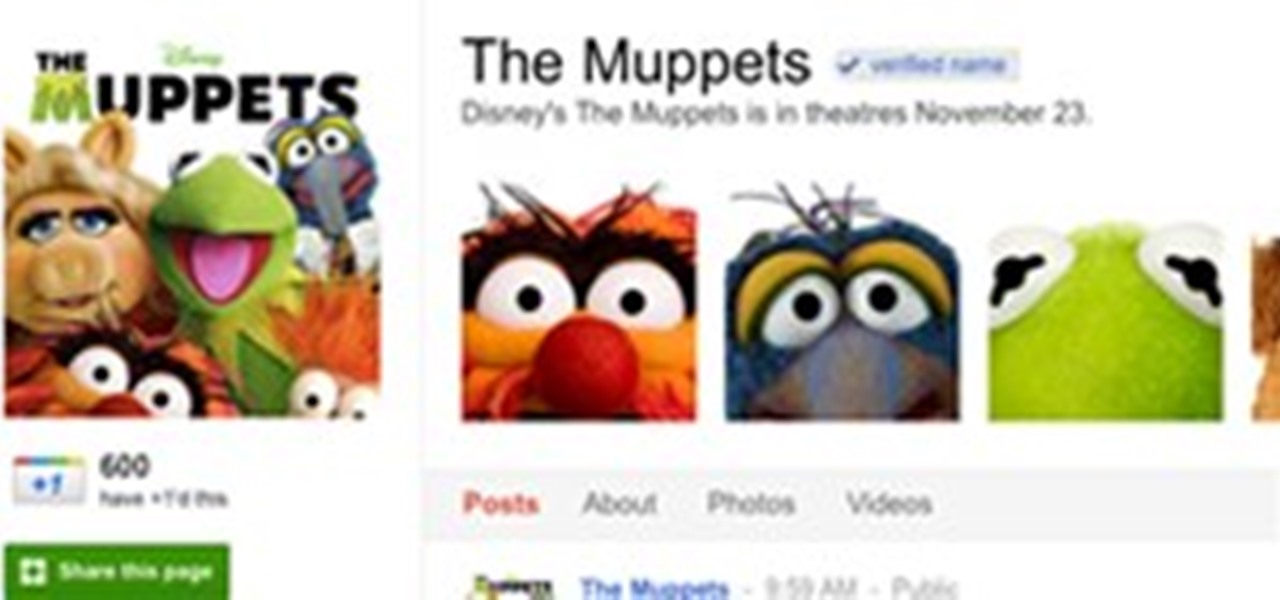
Many companies were disappointed when Google+ rolled out and banned the creation of accounts specifically for businesses and brands. Fortunately, today, Google began rolling out Google+ pages, for them to start connecting with customers and followers. For an example of what a Google+ Page looks like, check out the one for the +The Muppets:

Our first Community Byte went well! We had around 8 people in the room coding collaboratively and watching to learn. LukeStav did the kind task of hosting it on Gobby for all of us, so big thanks to him!

Beginning this week, Null Byte will be hosting a new feature called Community Byte, a weekly coding and hacking session held in the Null Byte IRC. This is a chance for our community to do something fun, and make something awesome together!