As of this week, Gmail is going to start letting Google+ users email each other using a new option called "Email via Google+." There's nothing wrong with making it easier to get in touch with people you want to hear from, but the default setting allows anyone with a Google+ account to send a message to your Gmail inbox. After the feature is in use, Gmail will start to suggest Google+ connections along with your other contacts as recipients. Email addresses will not be displayed for Google+ co...

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can control practically everything on your Xbox One—if it can understand you.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

Why can't I see who is stalking my Facebook profile?

If you've tried watching a video that requires Adobe Flash Player installed on your Samsung Galaxy Note 2, then you're probably well acquainted with the "Flash Player is not installed" message. If you try tapping the deceiving Install Flash Player button it takes you directly to the Adobe website, where you're greeted with a message saying:

It only takes a minute for something well intentioned to turn into something sinister. Facebook created 'memorial pages' as way for friends and family to share their thoughts and feelings for those that are no longer with us.

If you have a lot of friends on Facebook, chances are that every day is at least one of their birthdays. If you took the time to individually post a message every time, you'd spend ALL of your time on Facebook, but you don't want to be a bad friend either. Let's face it, some people take this stuff personally.

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

It's been almost a year since all major banks blockaded WikiLeaks from recieving funds. It's their only source of actual revenue, so help out if you can.

We've all seen this warning message at one time or another while playing around on the internet in the Mozilla Firefox web browser:

Unlock and jailbreak your iPhone! You can either reinstall the entire operating system, wiping all the data from your phone, or you can wait for Black Snow to come out. In the method shown in the video, you can unlock right away. To restore, hold option (on a Mac) or shift (on a PC) and click restore. After it is done restoring, you should be getting an error message that the phone isn't registered and to insert a SIM card. Insert the SIM card you want to use. Close iTunes and open up www.bla...

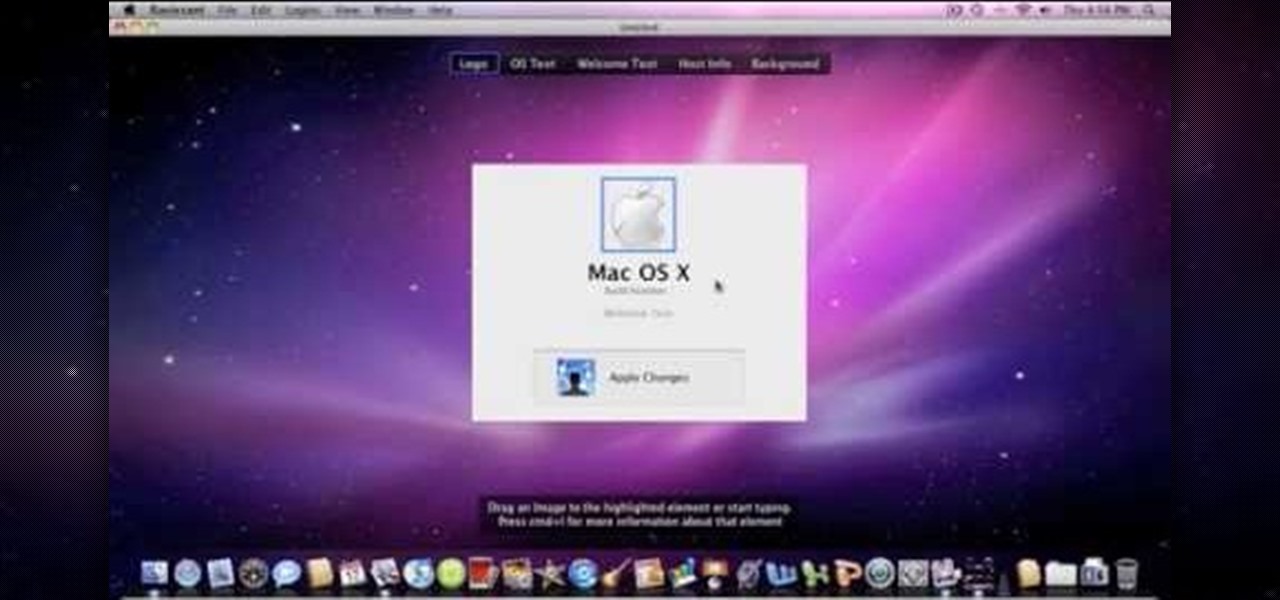
Change the Snow Leopard login screen with this video tutorial. Download and install the application Ravissant, an app that lets you customize the login screen in every aspect. Have a background image ready and an Apple logo image, if you want. Modified Apple logos can be found here , created by Evil-Slayer]. Open Ravissant, and you should see your login screen, but don't try to log-in! IMPORTANT! If you want to keep your original login screen, go to the top...

With the right app and software, a wireless printer will allow you to print directly from your Apple iPhone or Apple iPod Touch. Print & Share is an iPhone and iTouch app that enables you to print files, emails, webpages, contacts, images from your iPhone photo album, and camera photos that you can take and print right away. But, to print off your device, you need to first install the right app and software. It works with both Windows and Mac operating systems, and is primarily for printing d...

Show someone you care about them by spending a little extra time on their Christmas card... and in the process, save some money. In this tutorial, learn how to make a pop-up three-dimensional Christmas card for your loved one.

Researching genealogy takes a little enterprise and the skills of a master sleuth.. Watch this video to learn how to research your genealogy and family tree.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

Google recently started testing a new SafetyNet check that might spell trouble for rooted Android devices. It cross-checks your SafetyNet status with Google remote servers, making it impossible to fool by normal means. If Magisk shows you pass SafetyNet and you're still having issues, you might be affected by this change.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quirky commands and funny responses.

The international, Exynos-powered Galaxy S7 and S7 edge have had a working root method ever since a few days after release. But the North American variants—those using Qualcomm's Snapdragon 820 processor—have locked bootloaders, and have proven to be almost unrootable up until now.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Video: . Recycle your hard drive into a hidden flash memory device that only you know how to turn on and use in secret. This DIY hack project allows you to recycle your broken hard drives back to life and turn them into something useful.

mIQ? What is it exactly? It's a handy web service that helps you manage your mobile life, with free and easy online access to all of the content and information stored on your mobile device. How does it work? Best Buy has answers. The Best Buy Mobile team explains how simple it is to use mIQ to backup all the data on your cell phone, including messages, photos and contacts.

No need to make a bad situation worse when running into an ex boyfriend or girlfriend. There is no need to be petty or spiteful when keeping to a nice yet vague conversation will ultimately leave you looking like a real class act.

Don't make people around you wish that cell phones had never been invented. Mind your manners by following a few simple rules.

While new features in Safari, Camera, Photos, Notes, Weather, Messages, and other Apple apps may steal the show on iOS 17, there are some impressive new features you need to know about when it comes to FaceTime audio and video calls.

While the iPhone came before the first Android smartphone, every new iOS version seems to include a wealth of features already existing on Android, and iOS 17 is no exception.

For the average consumer, augmented reality is a fun way of dressing up photos and videos for social media. However, AR is also gaining momentum as a medium for storytelling, particularly in sharing powerful messages.

Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.