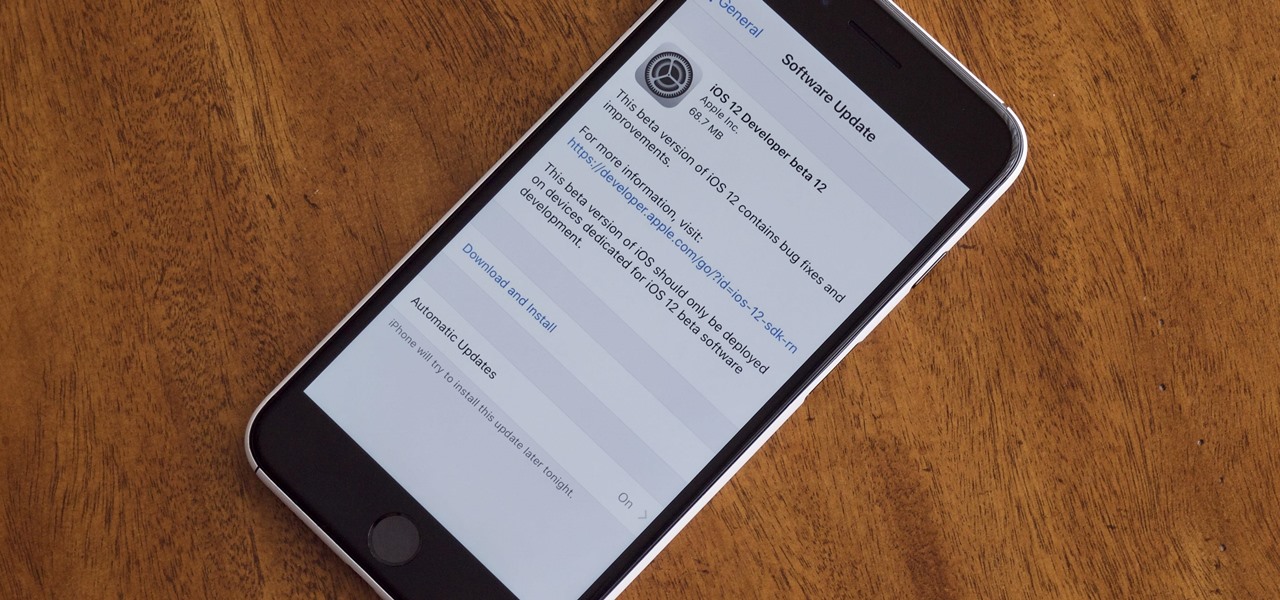
Right before the Labor Day weekend, Apple issued iOS 12 developer beta 12, which comes four days after dev beta 11 and public beta 9, and just one day after announcing the Sept. 12 event. This update primarily fixes a bug where you would be continuously prompted to install a new iOS update even when none existed.
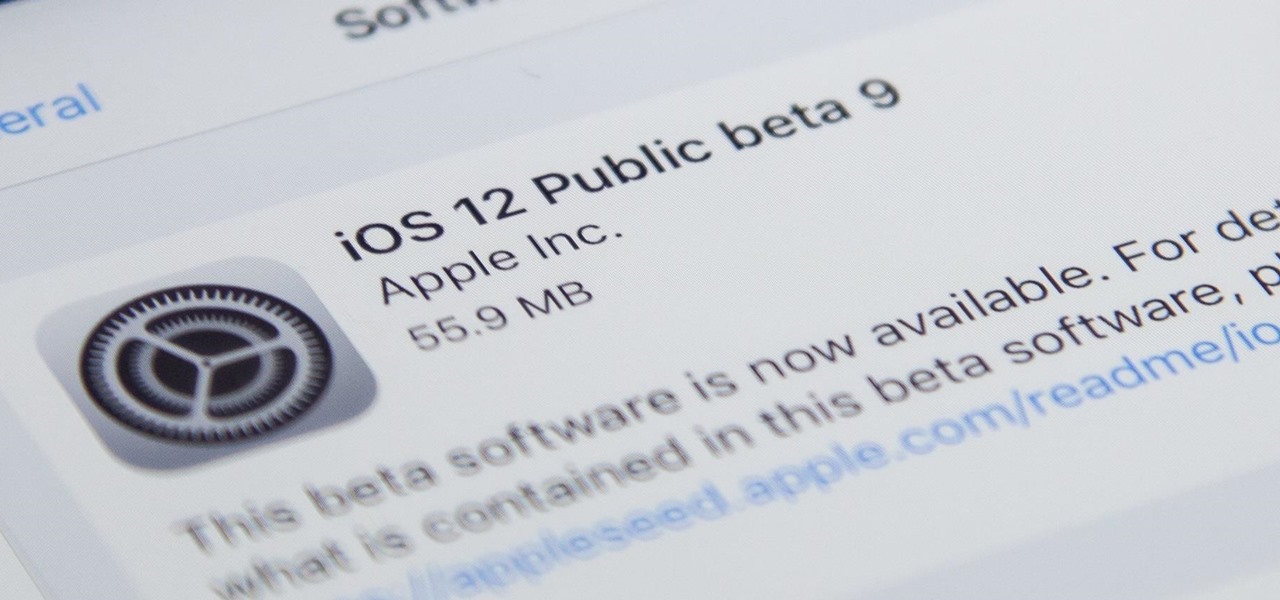
Apple released iOS 12 beta 9 to public beta testers on Monday, Aug. 27. The update comes at the same time as the release of dev beta 11. This is surprising, as Apple typically releases developer betas at least a few hours before the public version. Then again, everything Apple is doing with its iOS 12 beta as of late is surprising.
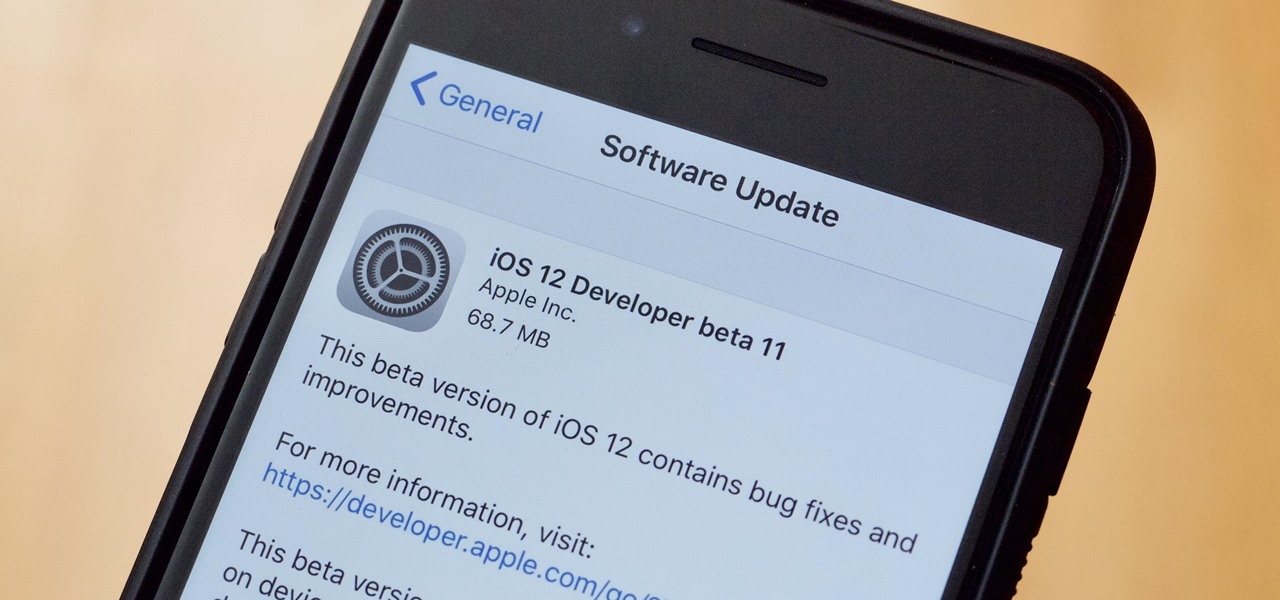
Apple released the eleventh developer beta for iOS 12 to registered software testers on Monday, Aug. 27, only four days after the company unexpectedly released both dev beta 10 and public beta 8. Apple has ramped up its beta release schedule as of late, offering minor updates twice a week in the lead-up to iOS 12's official debut in a few weeks.

Apple released the tenth iOS 12 developer beta unexpectedly Thursday afternoon, Aug. 23. The update comes only three days after the release of iOS 12 developer beta 9, a surprising move for Apple, even with the irregular releases the company has made in recent weeks.

Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.
Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.

Apple developers, check your iPhones — Apple released the eighth developer beta for iOS 12 on Wednesday, August 15. This update arrives just two days after the release of dev beta 7, which Apple quickly pulled after complaints of unusual performance and stability issues.

Extra hardware buttons have become a trend with smartphones lately. Often, these are unmodifiable buttons designed to launch a voice assistant. That isn't the case with the BlackBerry KEY2. Making a return from the KEYone is the Convenience Key, which also received an upgrade.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Instagram has long-resisted easily resharing content. While it's been testing a "regram" feature for a long time, it still lags behind apps such as Twitter and Facebook when it comes to resharing content. But while Instagram is a bastion of original material, there is a feature in place for you to reshare stories from those you follow. Your friends can reshare your stories too.

There are a lot of things that make iOS great, but lock screen widgets are not among them. If you want more information on your lock screen other than the date, time, and notifications without having to swipe to a sidebar of widgets, you'd normally look toward Android. However, iOS 12 aims to shake that up a bit with a secret Weather widget for the lock screen — not for the Today view.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices access to their visual voicemail apps. For that, there's Google Voice.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

Technology ages rapidly. We're conditioned to refresh our iPhones every one or two years, and why wouldn't we? New iPhones are fast, and our old ones inevitably slow down, sometimes to an unusable degree. However, it turns out, there's something we can do about that, and it doesn't involve buying a new iPhone at all.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

There are a few different ways to install Magisk. If you're already rooted and you just want access to Magisk modules, you can use Magisk Manager to install the Magisk framework. Or, if you want to pass SafetyNet on a rooted device, you can switch from SuperSU to Magisk SU. But the best way to do it is to start fresh by installing Magisk on a non-rooted phone using TWRP.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

With the release of Apple's ARKit comes endless possibilities for education and learning. One of those possibilities is an AR rotating model of our solar system in your room, another is using AR to instantly know the nutritional value of food items.

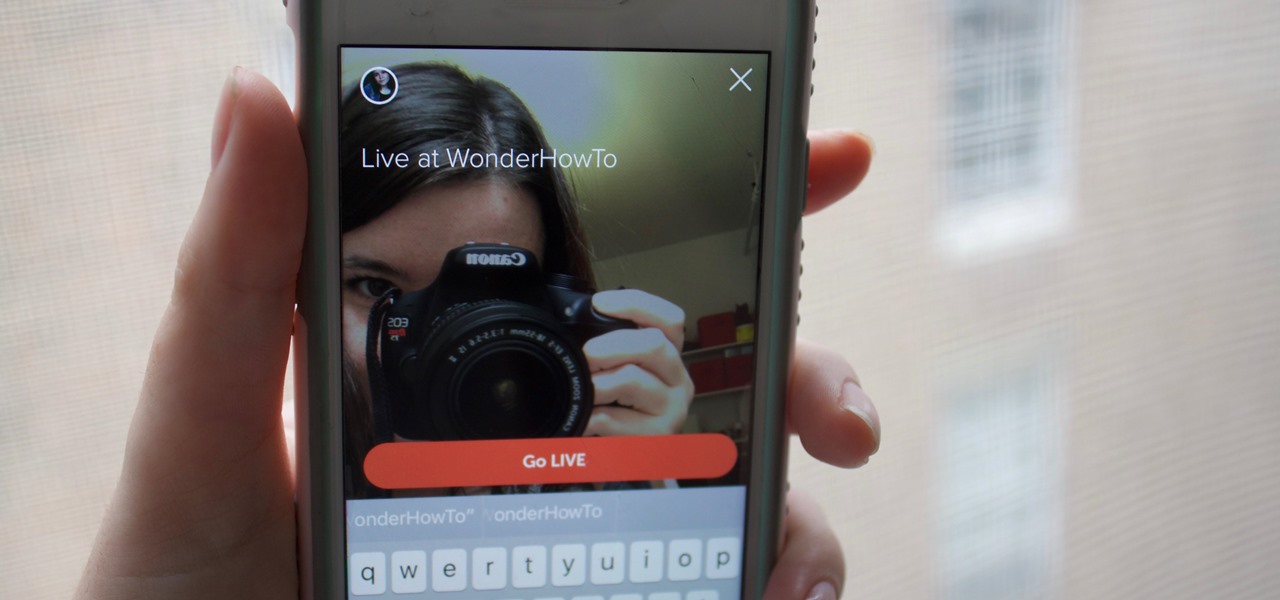
It seems that every major social media platform is adding a "Go live" feature to their apps lately. Twitter, in particular, has been at the forefront of the live broadcasting craze for quite some time now.

There's nothing more fun than unlocking a hidden Snapchat filter or lens and beating everyone to that perfect first selfie. So when a new filter or lens comes out, like the current Uganda Knuckles one, it's always interesting to see how things will turn out.

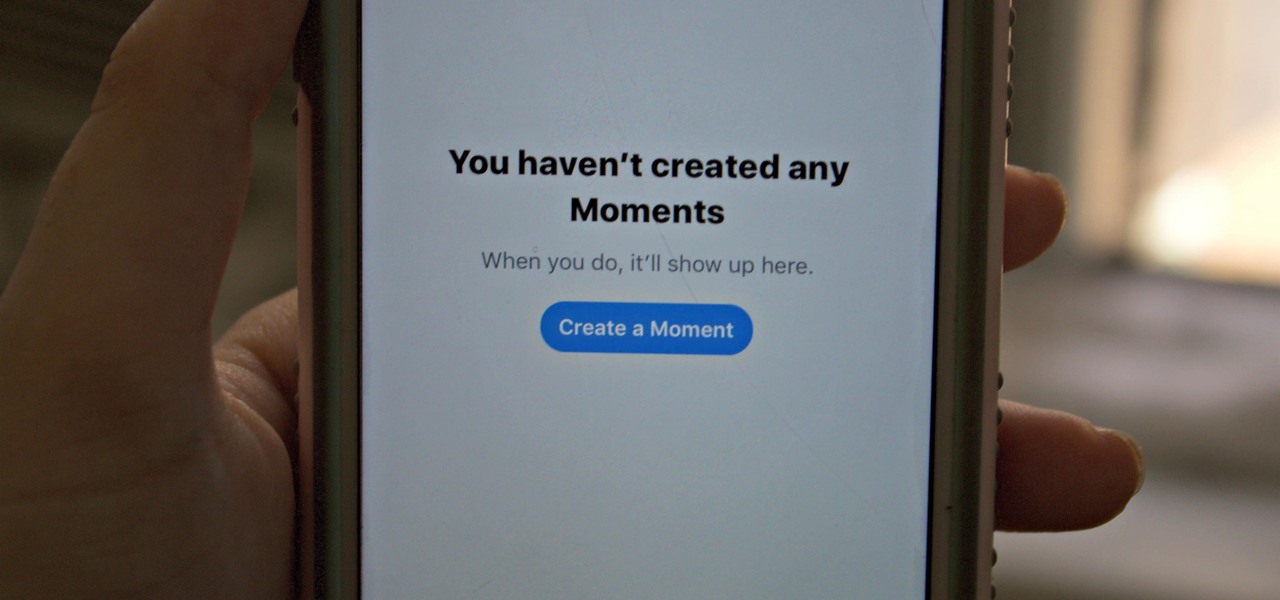
Twitter's Moments feature stitches together multiple tweets into a slideshow-esque story. This is particularly cool for you to keep up with major things that are happening in the world without having to follow and search for a ton of people to figure out the scoop.

YouTube is nothing without its creators — the people who make the content worth visiting the site again and again. Many of us have favorite channels and creators we return to, but it can be difficult to keep track of all the new videos they make, as the alternative is to be plagued by unwanted notifications.

The stock home screen app that comes with your phone is nothing compared to Nova Launcher. Not only is Nova faster, but it's got tons of customization tweaks like gestures, adjustable grid sizes, and icon packs, just to name a few.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

When Google issues an Android update, the changes are usually all over the place—fixing issues, adding functionality, playing catch-up with the latest thing Apple added to iOS. It's how the smartphone wars have evolved, where the two competing operating systems continually match and one-up each other.

Microsoft's HoloLens comes with helpful features for capturing video and photos, but sharing whatever you record isn't as straightforward as you might expect. So here are the many ways to get your media off the device to share with the world.

The Oculus Rift is finally shipping to customers in more than 20 countries, and we're getting a good idea of how the device holds up from the initial reviews. You'll see some common threads throughout: along with an impressive virtual reality experience, the device is very comfortable with a solid design.

Samsung's 2016 flagship devices are some of the most beautiful, powerful smartphones ever made. And amazingly enough, thanks to legendary root developer Chainfire, the Samsung Galaxy S7 and Galaxy S7 edge are about to get even more powerful.

This tutorial shows you how to create an intruder alarm that sends you text message alerts when motion is detected. This may sound complicated but I am pretty confident any beginner with electronics should be able to do this just fine. The range sensor senses motion and tells your Arduino board to send the text (SMS). So you can leave the intruder detector at home, connected to your network, and still receive the SMS alerts, no matter where you are, as long as you have cell phone service.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Learn how to remove blackheads from nose and face, naturally at home! Video: .

Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the development of RRO as a way for manufacturers to implement themes in their skinned versions of Android.

As Android's de facto virtual assistant, Google Now lets us speak directly to our phones in plain English to answer our questions and perform many basic tasks. With the app open, just say "Okay Google," then wait for the beep, and ask almost any question.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

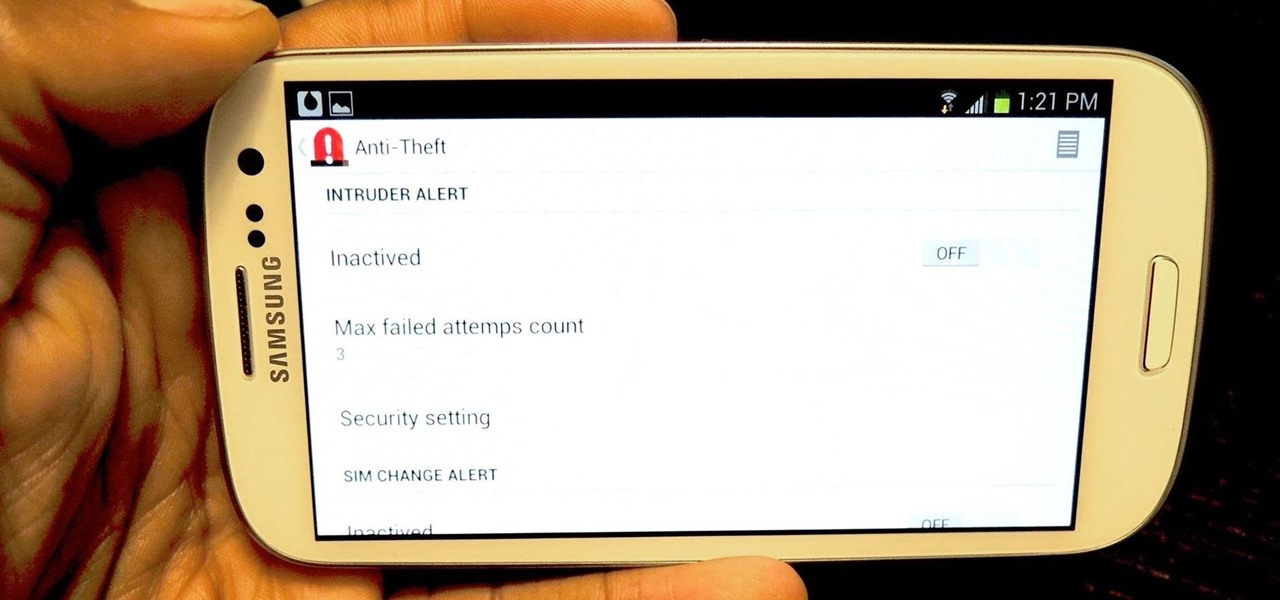
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.