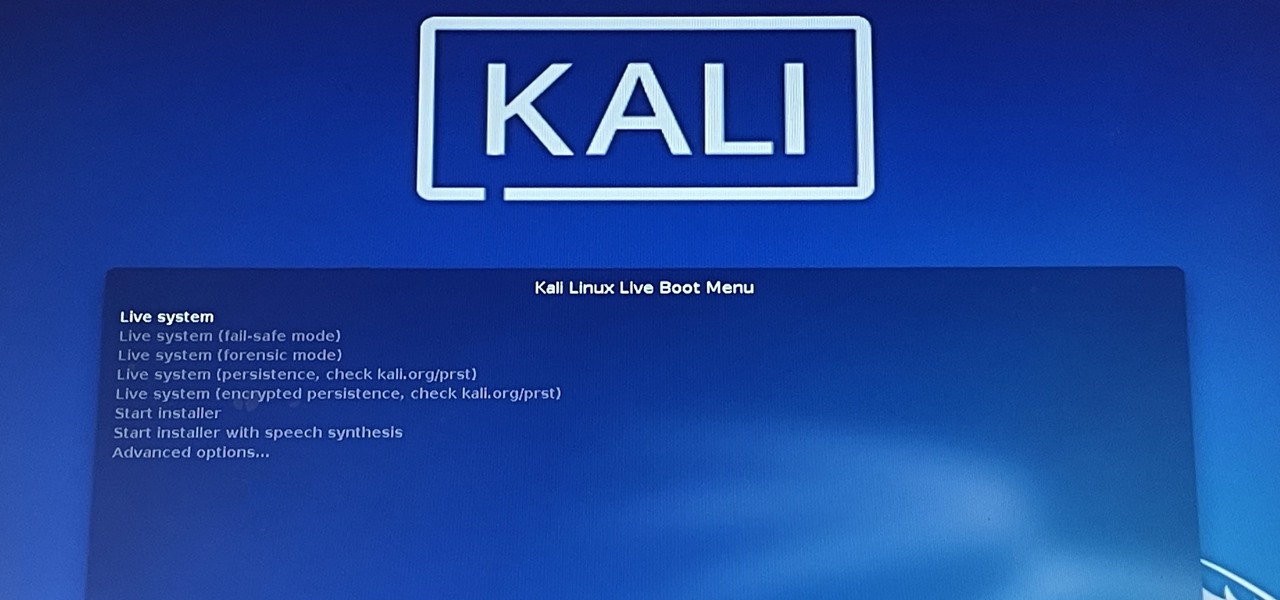
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB drive.

Streaming media companies like Netflix and Hulu make deals with Roku to have their apps featured on Roku's remote controls, but there's an inherent flaw with this model: the buttons become useless if the app no longer exists. So, is there anything you can do to change those defunct buttons on your Roke remote?

Apple's stock keyboard for iPhone has gone through many changes over the years. Some have been significant, and others more subtle. Overall, most of these updates have been fairly obvious, so you're probably already using them — but there are more than a few interesting features that were slipped in under the radar that you may not know about.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.
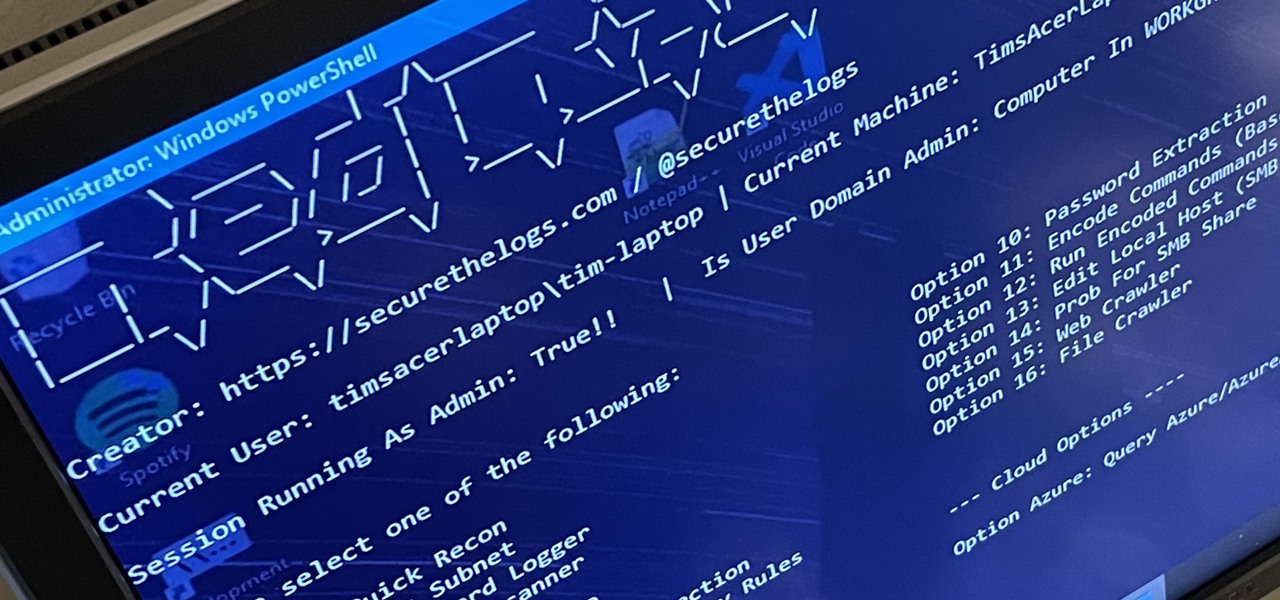
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."
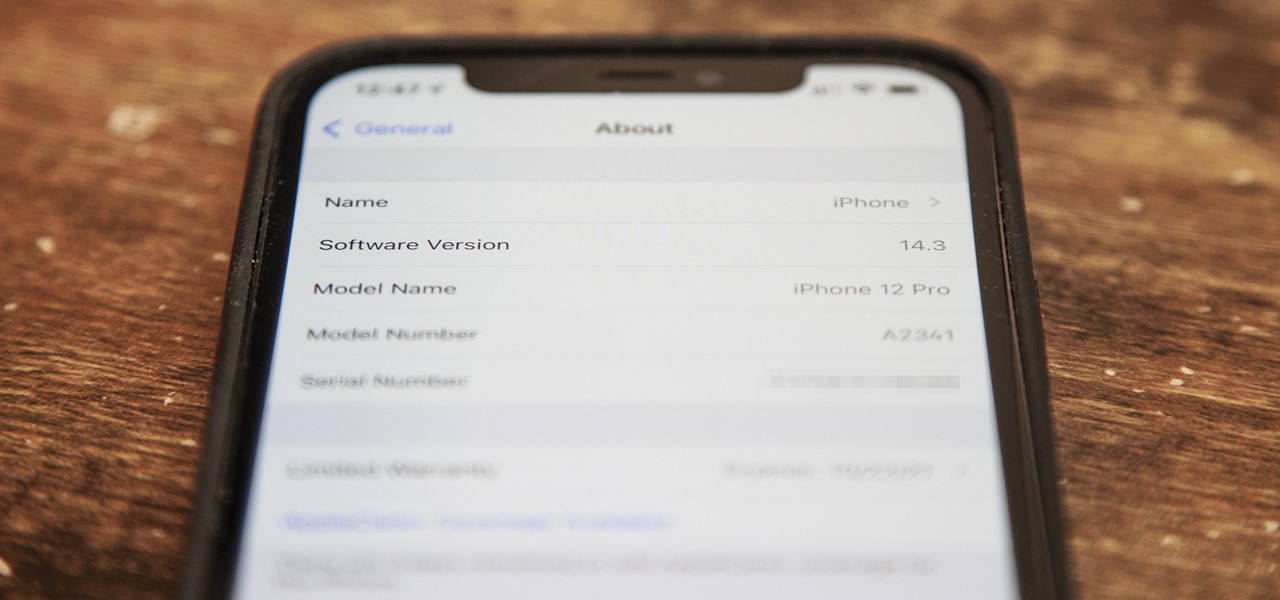
Just as expected, Apple pushed out iOS 14.3 to the masses on Monday, Dec. 14, which coincided with the pumped-up release of Fitness+, Apple's subscription workout service for Apple Watch users. It also came one day before the new AirPods Max hit buyers, and the iPhone needs iOS 14.3 to use all of its features.

Apple's first release candidate for the iOS 14.3 beta came out on Dec. 8, but there must have been a serious bug in the system because iOS 14.3 RC 2 followed it just two days later on Dec. 10. These builds highlight everything that you should expect to see on the stable version very soon.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

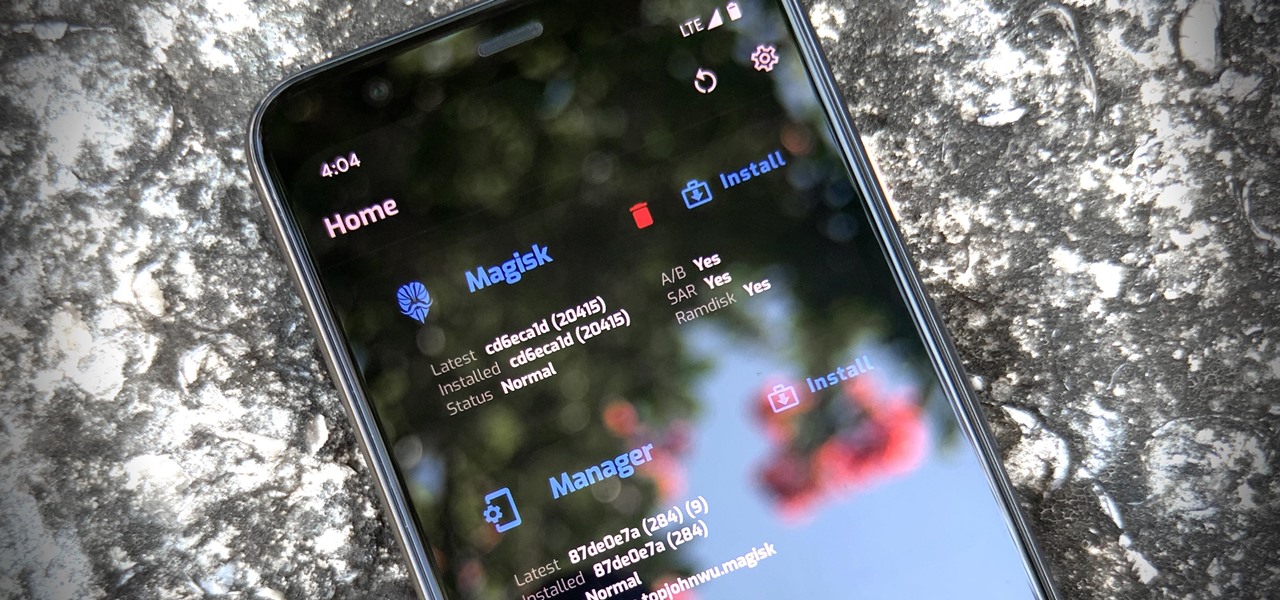
The Pixel 5 is a great value proposition in this era of $1,500 phones. With its reasonable price tag, fully open-sourced software, and unlockable bootloader, it's also an ideal phone for rooting.

Thanks to Magisk, you don't have to lose root when updating to Android 11. The popular systemless rooting tool already achieved superuser access on Google's latest OS, even before the official release. It's currently in its experimental stages so the process is trickier than usual, but it does work.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

Apple's Shortcuts app lets you make and use custom icons for any app on your iPhone, but it won't actually replace any icons. If your goal is to change the official icon for the app itself without any redirects, there's a growing list of third-party apps that'll let you do just that.

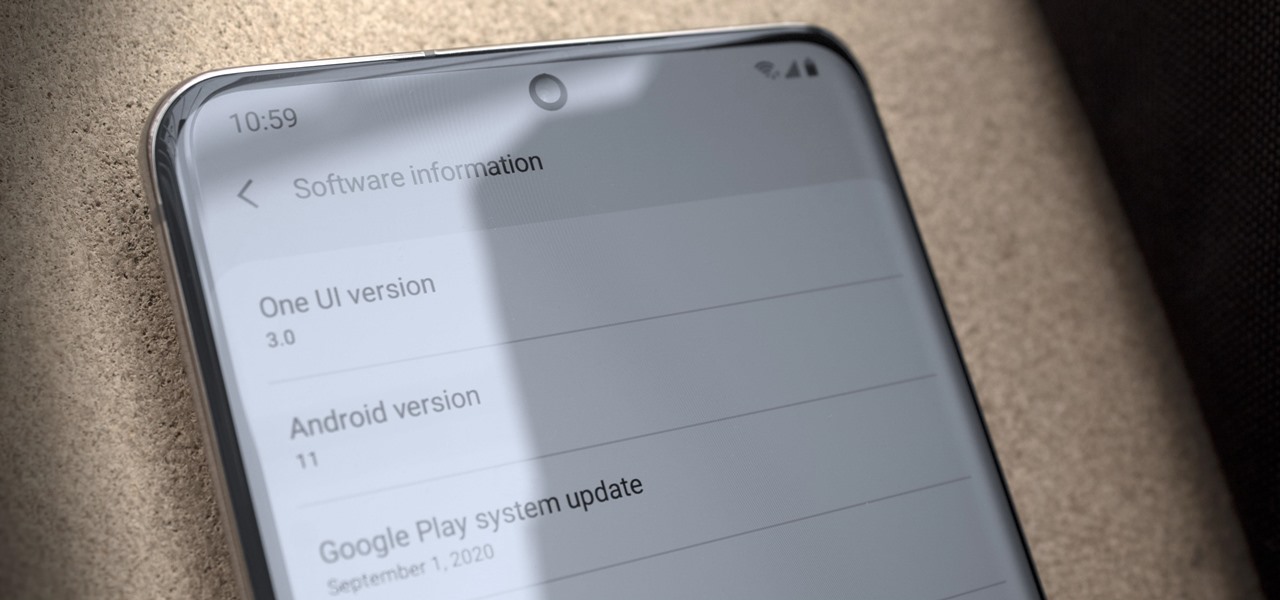
Just days after Google released the official Android 11 update, Samsung already had a pre-beta build of One UI 3.0 available for developers to test their apps on. So this year's main OS upgrade is likely hitting Galaxy phones even earlier than we thought.

Apple just released public beta 2 for iOS 14 today, Thursday, July 9. The good news comes two days after Apple released the second iOS 14 developer beta, and 17 days after the release of the first developer beta. While this is the first public beta for iOS 14, it's called "public beta 2" to keep in line with developer beta numbering.

Apple just released the second developer beta for iOS 14 today, Tuesday, July 7. The update comes 15 days after Apple seeded developers the first iOS 14 beta, which introduced home screen widgets, picture-in-picture, and 4K YouTube support, among more than 200 other features.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

Apple's new iOS 16 software update is finally here, and there are over 350 new features and changes for you to enjoy on your iPhone. There are major lock screen and home screen improvements, a pleasant surprise for the Contacts app, and tons of new upgrades to Safari, Mail, Messages, and more.

Apple just released the fourth public beta for iOS 14 today, Thursday, Aug. 6. This update comes two days after the company released iOS 14 developer beta 4, 15 days after Apple seeded developers the third dev beta, and two weeks after the release of public beta 3.

Apple just released the fourth developer beta for iOS 14 today, Tuesday, Aug. 4. This update comes 13 days after Apple seeded developers the third dev beta, and 12 days after public testers got their hands on public beta 3.

Apple just released the third public beta for iOS 14 today, Thursday, July 23. This update comes one day after the company released iOS 14 developer beta 3, and two weeks after the release of iOS 14 public beta 2.

Apple just released iOS 14 developer beta 3 for iPhone today, Wednesday, July 22. The update comes 15 days after Apple released the second developer beta for iOS 14, and 13 days after the release of iOS 14 public beta 2.

If you've ever gotten a call from a private caller on your Grand Central number and you want to call them back, now you can. This does not work with Google Voice. Log on to Grand Central and find a message you've received from a private caller. If you know the name of the caller, input it. This will help a lot. Mark the message as new. Now call your number and access the voicemail. Press 2 to return the call. It will return the call, but won't reveal the number. Now you can leave a message of...

In this tutorial, we learn how to bypass Captcha codes on Facebook. First, go to Facebook and log into your account. Next, go into your settings, then your accounts settings. In this section, click where it says "mobile". Next, it will take you to a section where you can activate a phone. You can use your cell phone for this, because Facebook is going to send you a verification text message next. So, enter your cell phone number and when you get the text message click "activate". Now, Faceboo...

If you're trying to use Cheat Engine to cheat for more money on Ninja Saga and keep getting an error message, this tutorial shows you a remedy. Make sure that you're playing Ninja Saga in either Firefox or Internet Explorer.

In this tutorial, we learn how to use Quick Connect Wireless with Epson Projectors. First, make sure you have one cable connected to the projector and one cable connected to the computer with a USB streamline. This makes it much easier and more efficient to plug in your projector. As soon as you plug this in, you will see a message appear on your notebook, then the screen will star to appear on the projector as it does on the notebook. It will take a few seconds, depending on the monitor and ...

In this how-to video, you will learn how to send a fax for free with your computer. First, go to the website MyFax. You will see a screen with forms to fill. Fill out the appropriate information, such as your name and who you are sending it to. You can also enter an external message with the fax. You can then upload the file you want to fax onto the form. Once this is done, enter the email addresses of the people whom you will be sending the fax to. Once this is all filled out, click on the b...

In this video from whenwillapple we learn how to copy and paste video files on your iPhone. First go into your camera roll. Click on the thumbnail of the video file you would like to open. Once opened, tap and hold your finger on the screen until copy pops up on the screen. Tap the word copy. Now go to the home screen. Go into your mail and create a message. Tap and hold the blank area in the message until the paste options come up. Tap on the word paste and your file will paste into the emai...

YouTube user diabeticHOWIE instructs you on how to enable MMS (Multimedia Messaging) for your iPhone 3G or 3GS. He claims that this may not work for the first generation iPhone. Using his step-by-step tutorial, you will be able to send multimedia messages to your friends and family.

This is an educational tutorial on the basics of taxi operations in Flight Simulator (FSX). Watch and learn ground operations and taxiing a few different planes like the DC-3 and the cub in this aviation tutorial.