You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down the Internet? Could they even do it?

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned how stalkers work.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Bash (Shell) Scripting for Beginners Intro

Problem: You're a PC gamer who absolutely loves The Elder Scrolls series and were eagerly anticipating the release of the newest game, Skyrim. But as much as you'd like to pick up the new game, money is tight. What do you do?

Now that it's been a week since Google+ rolled out pages, we've gotten over our euphoria at finally getting the feature after a long wait, and reality is starting to sink it. It's not as flexible as a Facebook page, it seems to be time consuming, and you can't even get a unique URL. On the other hand, your Google+ page will show up in Google searches, and help bump you up a bit. Here's how the search stacks up when I search for "WonderHowTo" in Yahoo! vs. Google (Note: I've turned on private ...

There are many impressive accomplishments in Minecraft, too many to name in fact. Sprawling builds, complex machines, and massive servers are the hallmark of Minecraft and things keep getting bigger and better. No one doubts the epic scale Minecraft has reached, but every once in a while something grand comes along that sets a new benchmark in awesomeness. By far the most recent step in this long line of big ideas was an innovation pushed forward by YouTube user Kimundi2. The premise of this ...

It's been a long journey for Netflix users. At first, it was a rough ride as Netflix struggled to find its place in the homes and hearts of movie watchers everywhere. Once monthly subscriptions bumped off the pay-per-rental charges, Netflix soared to great heights, known for their flat-fee unlimited rentals without due dates, late fees, or shipping and handling fees. And it was smooth sailing when streaming services were incorporated into monthly plans, with customers being able to rent DVDs ...

I don't know what I'd do without my computer. I can't do my job without the internet. I communicate with employers, friends, and family through emails, video chat and Twitter. I schedule meetings and plan deadlines. I bank. I shop. I read the news. I play games. I watch my favorite shows. Yes, I'd be rather lost without this little plastic box of circuits.

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.

I have an absolutely wonderful time making projects and writing articles for all of you mad scientists! Today, I will bring you behind the scenes for a look at the workbench, tools, and software that make the Mad Science World possible.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

For as long as I've loved SCRABBLE, I can't believe I've never come across this before. "CRAZIEST" - A short story by Liz Dubelman about words

There are plenty of apps that can translate text on websites and even in the real world. But when you need to write a message in a language you don't speak, it's your keyboard that will come in handy the most.

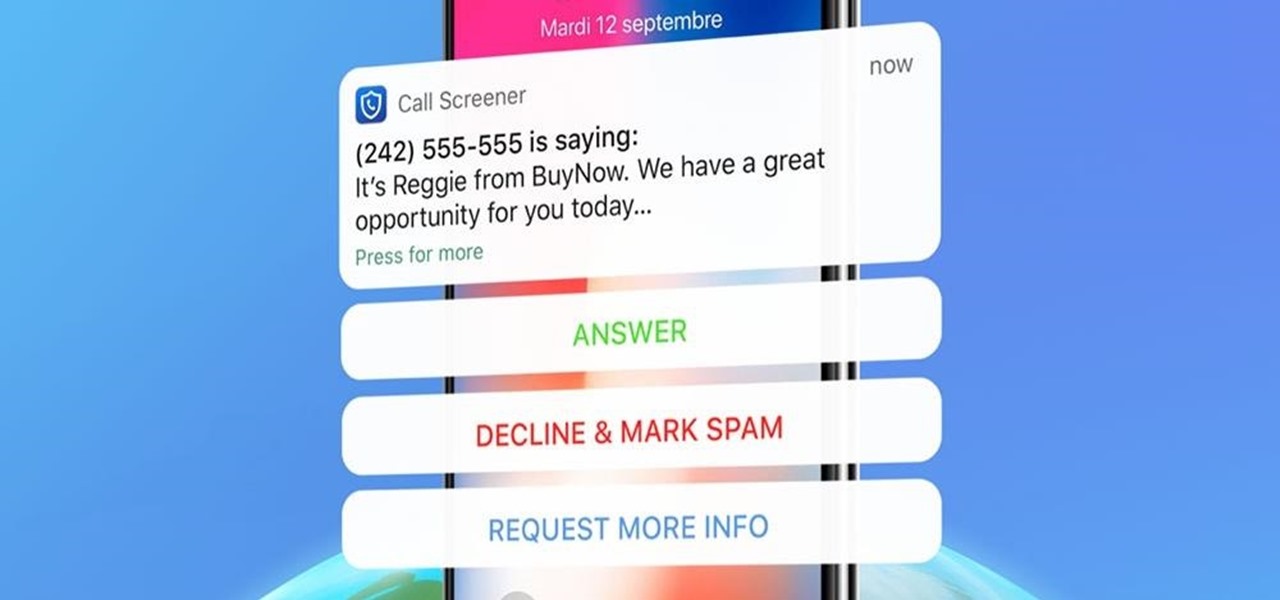
We all know the stress that a ringing phone causes these days. Should you pick up that unrecognizable number? More often than not, it's a bad decision. You hear the automated message and hang up. Or worse, a real human asks you about your day before trying to sell you something.

Most people are aware that you can reply to messages within notifications. The "Reply" button has been a feature in Android since 7.0 Nougat, saving precious seconds needed to open the app and respond there. But did you know the convenience doesn't stop there?

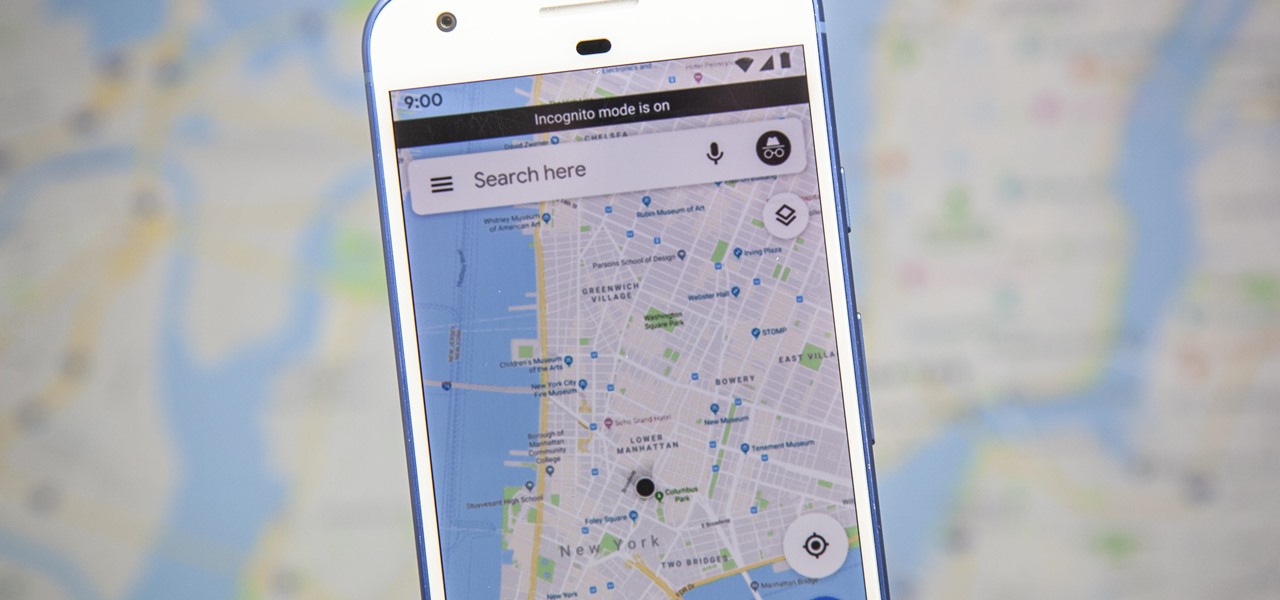
Google just recently added an incognito mode feature to Google Maps for iPhone and Android. With that, you can now use Maps in private at any time, which means you can browse and search with peace of mind.

When your bootloader is unlocked, your phone shows a screen that tells you the bootloader is indeed unlocked and how software integrity can't be verified. But if you're the one who unlocked the bootloader in the first place, all this message does is slow down the bootup process dramatically.

One of the Pixel 4's coolest features is a new voice recording app that instantly transcribes speech into text so you can easily search for it later. This is currently a Pixel exclusive, but we're here to present it to you on a silver platter.

If you want to root, it's step one. If you're a tinkerer, it's vital. It's Android's hidden "Developer options" menu, and it's definitely worth taking 30 seconds to unlock.

Swiping between pages on your iPhone's home screen feels very natural, but surprisingly, Apple has another way to switch between screens, and it's been staring us in the face this whole time.

You open the App Store to see a huge red number hovering over your profile icon. There's a ton of updates to install, so you tap "Update All." But wait! You needed to check Instagram or send a reply to a timely WhatsApp message, but those apps are now stuck waiting for others to update first. Luckily, you don't need to stick to your iPhone's update queue — you can choose which apps to update first.

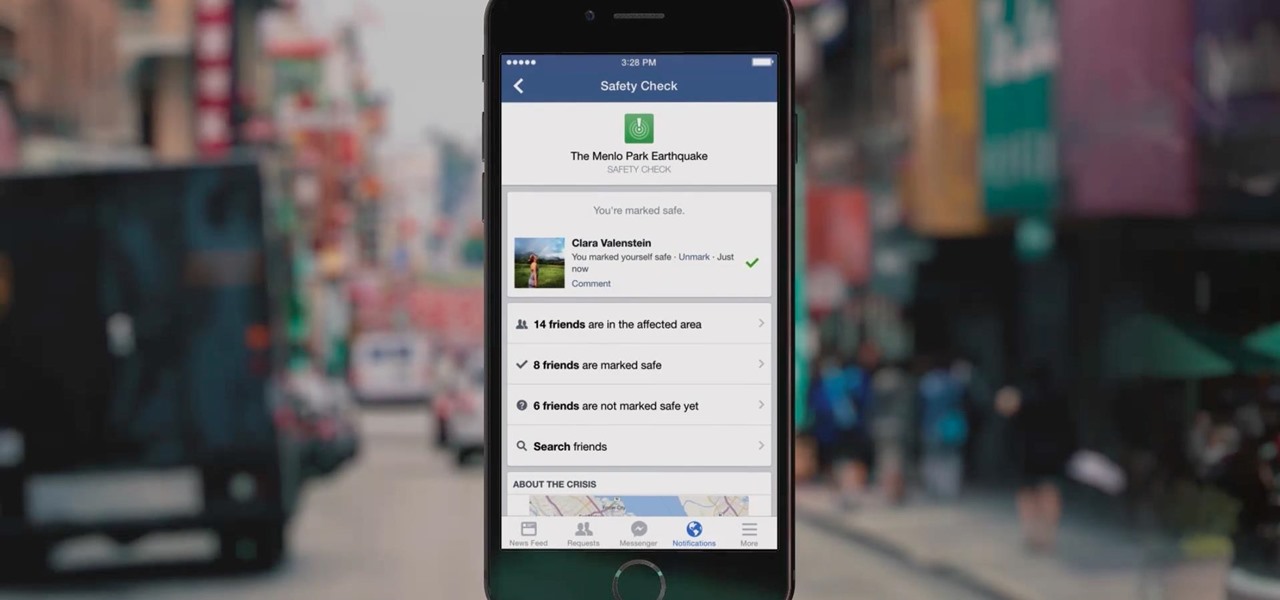
Facebook's 'Safety Check' is a useful social media function — it provides users a comfort that in the event of an emergency, they can let friends and family know they are safe. While certainly not perfect, the service is now essential during disasters and tragedies. That service is finally getting some improvements, as Facebook rolls out new features and updates.

Apple's 9.3.2 update for iOS has been completely destroying some users' iPad Pros, and there's only one way to fix it.

Encryption is on everyone's mind these days, from the FBI's battles in court with Apple to WhatsApp's recent announcement of end-to-end encryption for their one billion users. Now you can add Signal, whistleblower Edward Snowden's favorite messaging app, back to that whirlwind discussion. Created by Open Whisper Systems, Signal is an encrypted messenger app that allows you to send text, images, video, and audio messages without the fear of prying eyes. They already have an Android and iOS app...

If you want your Kindle to connect to the internet, you have to install the latest update for Kindle devices (not the Kindle Fire) by today. Amazon released a statement urging Kindle users to install a "critical software update" by March 22nd to maintain the Kindle's internet capability, which includes accessing and downloading Kindle books from the online store or any other internet-required service.