In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

We all have one of these: clairvoyance, clairaudience, claircognizance and clairsentience. With this video, you will learn how each clair delivers spirit messages to you on a daily basis. How To Recognize And Develop Your Intuitive Gift | Masters Channel.
Moscow, May 21 — Some Western countries are still considering a military operation against Iran as an option over its nuclear programme, a Russian minister said Sunday.
Sunday, April 29, 2012 2:00pm until 6:00pm

Have an HTC smartphone? Chances are that some of your stored personal data has been hijacked by malicious apps on your device. Android apps that have permission to access the Internet, which is pretty much every ad-supported app out there, can snag valuable information such as email addresses, location history, phone logs, text messages, and more.
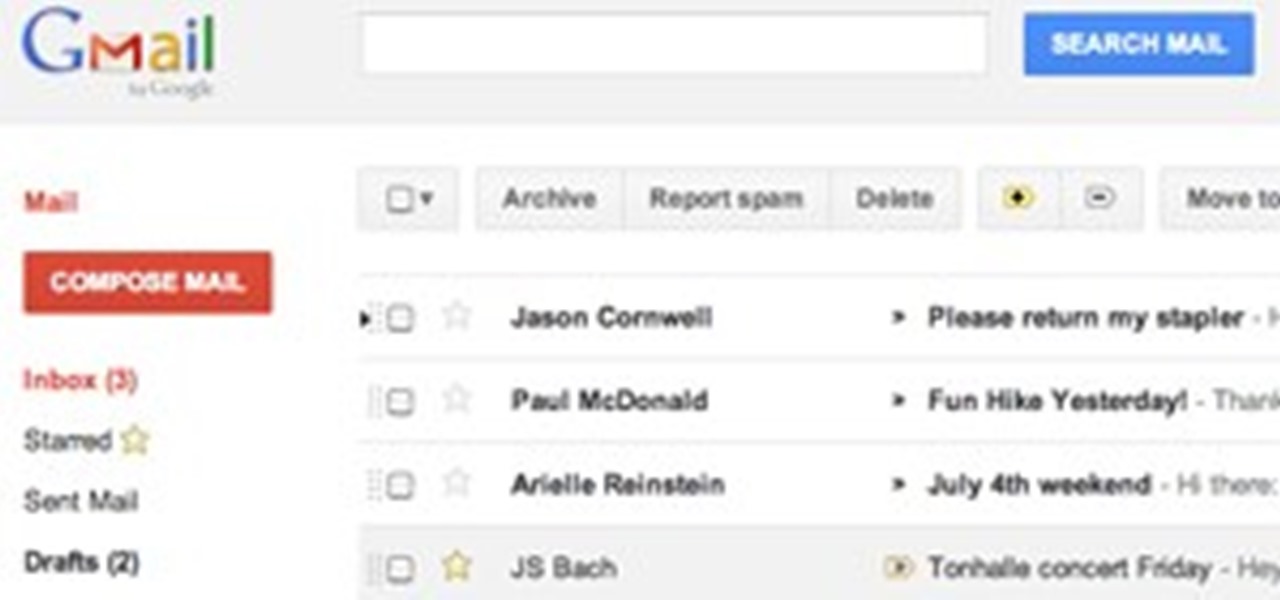
Google's hard at work beefing up their new Google+ social network, and while they continue to improve new features like Circles and Hangouts, they haven't lost track of their other online features already widely in use. If you're already a part of the Google+ project (currently closed to invites right now), you've probably noticed the changes in Picasa Web, but Gmail has been getting some great updates as well—and you don't have to be in the Google+ network to use them.

Time to confess a personal bias: I love Gmail. I think it's the best thing since sliced bread. I try to be impartial when I write about software and online services, but seriously -- of all the free email services out there, why would you use anything else?

Inspired by the beauty of traditional signage printed on doors and buildings, Rero is a French graffiti artist who makes a simple, yet heavy mark. Using the universally common Verdena typeface, Rero brands abandoned public spaces in extreme disarray with his own codified messages based on theories of public use of imagery and private property.

It's happened to the best of us—a drunk dial or text; a humiliating Tweet or incriminating photo uploaded to Facebook. Spirits are high, gestures are fearless… If only we could take it all back once the cold, sober morning light creeps through the blinds.

Okay, look behind your shoulder. Now check behind the other. Anybody looking? No? Then read on... Here's the scenario: You're single. You're an avid Facebooker. You're tired of your sans hottie reputation, and you're yearning for some much needed street cred. Well, Facebook street cred.

Eric Abrahamson, a professor at Columbia University, writes in to Forbes on how to be the Michelangelo of work shirking. The article is intended to help managers better understand their team's lack of productivity, but it also provides 10 simple tactics for all the lazy asses out there. Introducing exhibit A, June, a total lazy ass who lasted almost a decade in her job before being laid off:

Microsoft has finally released Windows Live Essentials 2011, their suite of consumer applications designed to compliment Windows and compete against Apple's iLife software. Windows Live Essentials 2011 is only available for Windows Vista and Windows 7 and can be downloaded from the Windows Live website.

These are great times. It is about time advertisers invaded our video games in the same way they do our driving (billboards), walking (fliyers, posters), and our private home (emails, bulk mail, text messages).

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

Google is great. They provide us with tons of free services and open source APIs that we can code fun tools for, one of which I don't think gets enough credit: Google Voice.

In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorithm), then the text to be encrypted. The program takes the key and text and inputs it into the "cryptograph" or code-based algorithm from PyCrypto. PyCrypto can use 16, 24, or 36 character encryption keys, but for the sak...

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Our first Community Byte went well! We had around 8 people in the room coding collaboratively and watching to learn. LukeStav did the kind task of hosting it on Gobby for all of us, so big thanks to him!

Welcome to part two in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.

Google started culling Google+ accounts. There are two main targets: businesses and those who are using pseudonyms. For businesses, Google is promising to provide their own version of Facebook Pages, which will be released later this year. For those who use pseudonyms, they aren't so lucky. According to Google+'s community standards, users must "use the name your friends, family, or co-workers usually call you". The purpose of this rule is ostensibly to discourage spammers and people from set...

By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe".

Life has always been complex and challenging. The challenges today are just different than what they were in the past. Nowadays instead of hunting and scavaging for food and living in the elements we’re bombarded with suggestions and demands from our highly sophisticated societies. How is it possible to find harmony amidst what are often contradictory messages?!
Microsoft office 2010 is the successor version of office 2007 and is code named as office 14. It is the first 64 bit version of office which is only compatible with Microsoft service pack 3, Windows vista and windows 7. It was released on April 15, 2010. It is the first Microsoft application which offers free online version of word, excel, PowerPoint and one note. These can be easily used with all the popular browsing software. The various functionality which are added in office2010 are descr...

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).

In each day of our life, we see inflammation. We see it during sore throats and abscess formations in our bodies, and even slight tooth pain is a form of inflammation. Sometimes it's good when it fights to protect us from invading organisms, but sometimes it becomes bad when it occurs in inappropriate ways, like acne.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Welcome to part three in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.

Just installed the new iOS 5 on your iPad, iPhone or iPod touch? There's a lot of great features to check out and play around with. After messing around with it on my iPhone 4 for a few minutes, these seven additions caught my attention. Check them out below—and tell us what your favorite new features are in the comments below.

We've covered Chrome browser extensions that make your Google+ experience richer and more useful, but there are still many users who prefer to use Firefox. To that end, I've gathered 13 Firefox add-ons to aid in the enhancement of your Google+ experience.

A few weeks ago I wrote about Atomic Web as the best web browser for iOS devices, and while I believe it is a superior option, Atomic Web is not the only alternative web browser you can use on your iOS device. There are three more—Dual Browser, iCabMobile, and iSwifter—that are all great options because of their unique features. Let’s check them out.

Always falling asleep behind the wheel? The National Highway Traffic Safety Administration (NHTSA) estimates that there are over 56,000 sleep-related accidents each year, resulting in 40,000 injuries and 1,550 deaths annually in the United States. Don't want to be a statistic? Then you may want to try out ASP Technology's mobile application which aims to keep you awake when you're fatigued on the road.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.
ATTENTION COLLISION REPAIR INDUSTRYHave you ever put your stud in your stud gun to repair a dent and the stud falls out before it reaches the panel? Sure it has, it has happened to all of us. However, the new Magna-Spot eliminates this problem with their exclusive (MPS), which secures the pins in the electrode. You can read the press release below to learn more of the benefits.ENTER AND WIN THE NEW MAGNA-SPOT STUD GUNDetails to this contest are going to be revealed in layers as follows:

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

Sure, you go online to email and shop and do research. But have you ever been curious about how the internet actually works? Don't worry, you don't need a degree in computer science to get a handle on how your info gets from point A to point B. Learning the basics of the internet will give you a whole new appreciation for all those emails and chat messages that seem to magically appear. Get ready, because we're about to enter the wonderful world of digital data!

INTRODUCTION In this Digital world now almost every one knows the a, b , c of computer. From a child of 5th grade to an old man, everyone knows how to operate computer and do simple work on it. Thats why you need to have something which makes you different from others.

L4D2: Chapter two - The Underground "Ok explain something to me, how is an under-the-river tour scenic?" - Nick

When you pick up your iPhone, the display turns on. Often, that's convenient since you want to use your iPhone anyway. But think about those times you're simply picking it up to take it with you somewhere. The display turns on anyway, and now you're accidentally responding to messages, turning on your flashlight, opening your camera — you get the gist.