Watch this first 'tutorial'.FauxTo! Hoax! Con! May 28, 2008, this video was uploaded to YouTube illustrating the popcorn popping power of a circle of ringing mobile phones. Radiation. Amazing. Viral. Millions viewed.

What is Indirect Care? Does it affect the CNA's exam result? Indirect Care entails your behavior in terms of how you communicate with the resident, valuing residents' rights and residents' safety and security. Indirect Care is absolutely important because: (1) it is a graded performance, (2) it has separate score ratings, and (3 )it greatly affects the testees' overall performance during the clinical skills exam.

In this video you will see how to heel toe shift and double clutch shift while auto racing with Gary Sheehan. Both methods are used in racing but can be applied to regular street driving as well. There is no verbal instruction, but you can get the idea just from watching Gary's feet. More experienced drivers will pick up how to heel toe and double clutch from this video better than beginners. Heel toe and double clutch with Gary Sheehan.
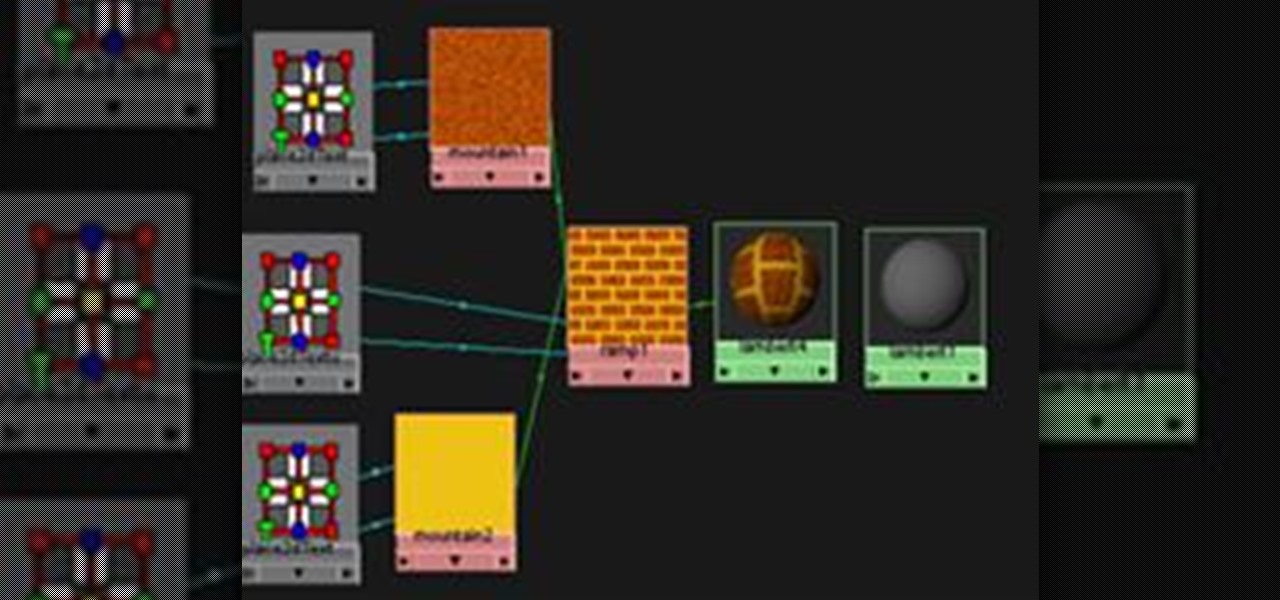
This is a guide to making a very simple procedural texture for Maya. As with all procedural textures, the basic texture can be refined and added to.

Polymer clay is an exciting arts & crafts medium. Actually, "clay" is a misnomer; it contains no true clay, but rather consists of tiny particles of polyvinyl chloride (PVC) combined with plasticizer, which is what makes it malleable like clay.

In this math made simple series of tutorials the author shows how to find a percent of a number. He shows that to compute x percentage of something we need to movie decimal point in the percentage number two places to the left. There fore to compute the percentage of a number we multiply it with the modified percentage number which has its decimal moved two places to the left. He goes and demonstrates this method by solving many sample problems. If you are looking to find out the percentage o...

Addison's disease is an endocrine disorder where your body is unable to produce adequate amounts of steroid hormones. As such, patients with Addison's disease require hormone replacement therapy.

An insertion pin allows you to stretch the size of your piercing one size at a time. The tapered shape allow you to increase the size of your piercing in a gentler manner. This how to video teaches the method on inserting the pin easily and comfortably. Watch this tutorial and you will be able to stretch your piercing in no time. Use an insertion pin to stretch your piercing.

The Replace Color tool lets you select one color and paint over it with a different color. To use the Replace Color tool, choose whether you want to select replacement colors from the swatches or from the image itself using the From drop-down. This is not always the best method to do this, but it's one of the fastest and worth knowing. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Repl...

If you have a Samsung device, you probably know the hassle of dealing with both the Galaxy Store and the Google Play Store at the same time for apps. Samsung's offering is forced onto you whether you like it or not; however, it's the only way to officially receive essential updates for your Samsung apps. The good news? You can keep on top of these updates with a super simple trick.

On the Android version of the Telegram app, the attachment icon disappears when you input your first letter or emoji. This "feature" forces you to either delete what you wrote to attach a picture first, or just send the file afterward. Since both of those options suck, we were happy to find a hidden third way.

The Customizable timer Ever wanted to make a simple timer that ranged from 5 minues to whatever you wanted? It's actually fairly simple! In this tutorial I walk you through every step of the way and have a video to show you it in more detail.

When I was attending college, my friends had a phantom thief in their dormitory. Almost every night, a different item of food would go missing, never to be seen again. There was constant speculation as to whom the thief was and how to catch them. Security cameras were deemed too invasive, but none could think of another method of surveillance... until today.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

How to play Spy, my personal favorite class What do Spies do?

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

Today's guide is on creating a password protected folder on Windows 7 without any additional software. Yes, you heard that right. No extra software at all! This guide is intended for beginners. But please note, this method should not be used to store financial or otherwise highly confidential material. It might be a good place to hide a planning document for a family member's birthday party or similar occasion where you need to keep something secret temporarily.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

Snapshot: 12w08a brings us a few nice things a few things I'm not so sure about and a few things I just hope Mojang doesn't incorporate into the next official update.

Accounting and Finance Degree

Here is my investigation on Teen Stress Base on FTA. QR/ER on Stress

Lock picking is defined by locksmiths as "the art of opening a lock without the key". There's many ways to accomplish this, but I'm specifically interested in using a lock pick set. Since locks vary in shapes and size, it's better to stick with just one kind of lock at first. Most locks are based on fairly similar concepts, so sharing methods across locks is possible.

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

Having bills to pay is one of the worst parts of life, especially around the holidays. And if you're extremely unlucky, you might also have to pay some hefty medical bills. This can put a heavy damper on plans, wants and needs. What's worse? The people that you owe money to are pushy and always bother you to pay in a more timely fashion, or worse, pay bigger premiums.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. A redstone sorting machine can not only cure a cluttered unmanageable Minecraft home, but make for an integral part of an efficient work space. With the redstone sorting machine, your items can arrive at the mere press of a button.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Welcome back to Minecraft World's Ultimate Survival guide! A few days ago, we reviewed a good way to start off right when you spawn, plus a small rundown of the mobs. Now we will continue on to combat strategies. Note that these are strategies, not specific How-To's, so the best way to get better at it is to do it yourself!

Now, I know what you're thinking... "I need an extra sexy coffee table that is like no other."

These boxes are inspired by a comment from Imaatfal Avidya on a corkboard post on Platonic polyhedra from sonobe units. Imaatfal was commenting about how the cube and octahedron are related to each other.

Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things.

When it comes to social engineering, Null Byte is here to show you how it's done. Social engineering is the key fundamental to unlocking tons of possibilities and opportunities in your everyday life. So, what is social engineering? Social engineering can be called many things. It's taking nothing and turning it into something. It's taking the bad and making it good. Above everything else, it's the art of manipulating the world and people around you—coercing that salesman into giving you a low...

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?

When you first become interested in learning how to program, it can be difficult to find a place to start. A lot of questions come up, especially if you're new to the idea of programming entirely. After you pick which language you want to learn, you have to worry about how you're going to write the language.

Here is the final part in Null Byte's series on mastering the skills in The Elder Scrolls V: Skyrim. We have already covered the slick and brutal methods to raise our Spellcasting and Combative skills. Skyrim's intelligent new leveling system has trumped the former methods of spamming repeated moves to raise levels quickly. Rather than casting a spell, or jumping up and down constantly, the new system requires that we use our skills in practice to get experience for them. This causes leveling...

Skyrim is an enormous RPG recently released by Bethesda. After many long years of waiting (I had 1000's of hours clocked into its predecessor, Oblivion, way back in 8th grade) the game is finally out and it surpasses everyone's expectations—save for removing custom spell crafting... Why, Bethesda?

The Elder Scrolls V: Skyrim set off a bang in the video game world this month. It will likely be video game of the year a few times over. Skyrim is another part to a series set in the fantasy world of Tamriel, a world filled with mystical creatures, folklore, and even its own history. It's quite the beatuiful and immersive experience. If you have not picked up the game yet, please do (my fiancée even plays!). Also, make sure to buy it new, so the hard working coders at Bethesda get the money ...

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.

WENDIGO n pl. -GOS windigo 62 points (12 points without the bingo)

Welcome to part three in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.