In a previous tutorial, we were able to place the Mona Lisa on vertical surfaces such as walls, books, and monitors using ARKit 1.5. By combining the power of Scene Kit and Sprite Kit (Apple's 2D graphics engine), we can play a video on a flat surface in ARKit.

In a previous tutorial, we were able to measure vertical surfaces such as walls, books, and monitors using ARKit 1.5. With the advent of vertical plane anchors, we can now also attach objects onto these vertical walls.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Jailbreaking gives you root access to the iOS file system, allowing you to install third-party apps and tweaks on your iPhone that aren't available in the App Store. It opens up a whole new realm for what your device can do, but it can also cause instability across the system and can dissuade you from getting future updates from Apple that have important features, bug fixes, and security enhancements.

April Fool's Day, aka National Screw with Your Friends Day, is finally here. You can always pull a conventional prank, like strategically placing a whoopee cushion on your mom's chair, but that joke has been exhausted generations before smartphones were around. We live in a day and age where smack cam is the new level of pranking, so it's time to step your game up, novices.

In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

With each update, Chromebooks are slowly becoming the Android tablet we always wanted. They already run your favorite Android apps and recently added a multitasking feature introduced to Android smartphones a few years ago: picture-in-picture mode.

It wasn't too long ago that the power menu for stock Android didn't offer much beyond turning the device off, but Google has steadily added more functions, like capturing screenshots and provisioning access to emergency information.

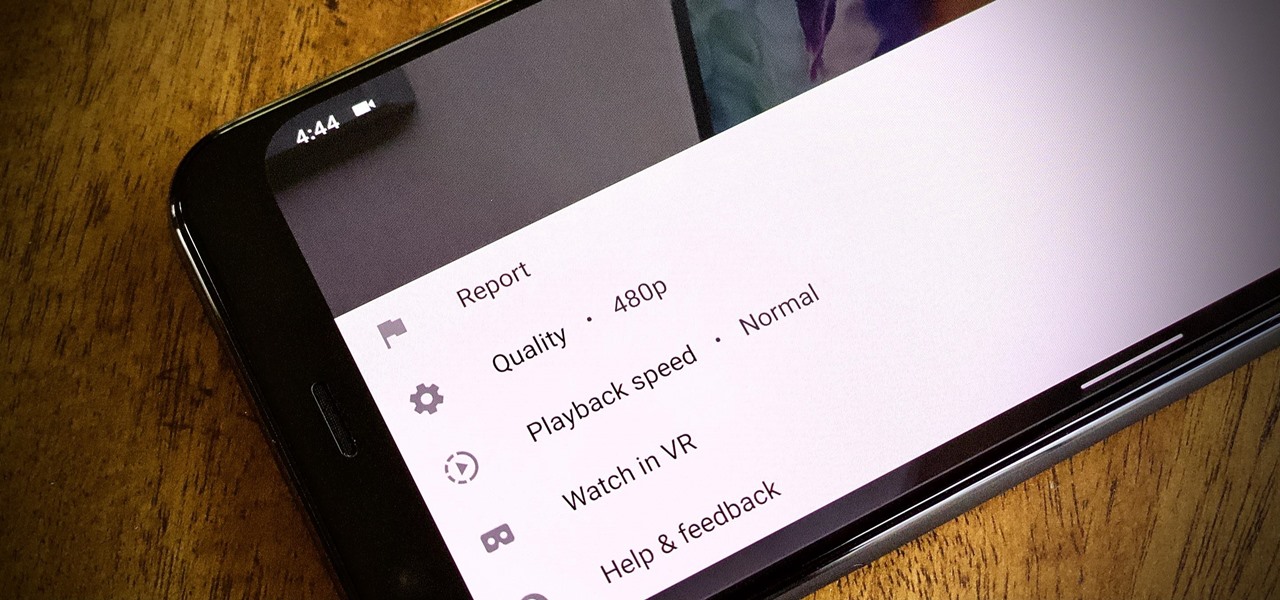
To reduce stress on internet bandwidth during the COVID-19 pandemic that the novel coronavirus is causing, Google decided to set YouTube's default video quality to 480p. That said, even when you could stream at HD quality without adjusting anything, you still couldn't switch the default to whatever you liked. We have a few methods on hand to help you change that.

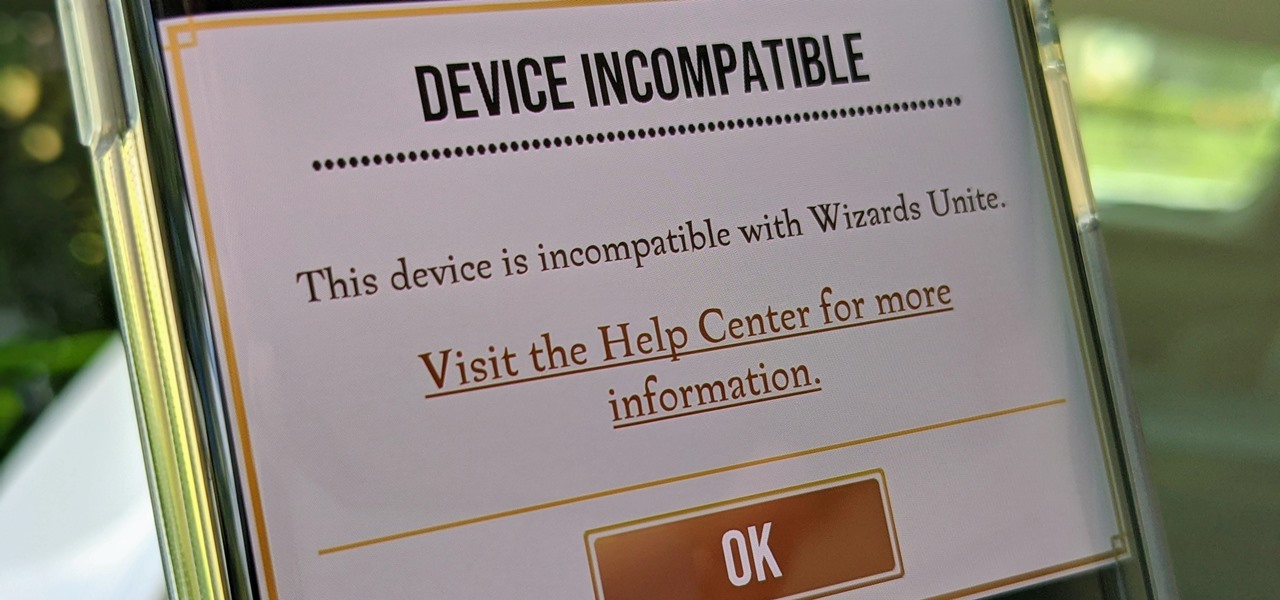
Harry Potter: Wizards Unite has gained quite the fan base since its launch, but not without a few bumps along the way. Niantic, the game's developer, has a long-running history with trying to block all root users on Android. The methods will vary for each game, but this time around with Wizards Unite, they appear to have a new detection feature at play from the recent 2.9.0 update. Let's find out what's going on.

With the rise of OLED displays, Android users have been begging Google for a true system-wide dark mode for years. While a system-wide solution is still somewhat unlikely, Google has given in by providing a dark mode for certain apps, including Contacts.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

Christmas came early for Apple, as the company was awarded more than 40 patents by the US Patent and Trademark Office on Tuesday, including one covering a system for compositing an augmented reality construct based on image recognition.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

What would it be like to have clothing that killed microbes? Or paper that repelled pathogens? A research team from Rutgers University has developed a prototype out of metalized paper to zap the bad guys without being super expensive. Sound good? Read on.

If you're an Android fan, you're probably familiar with Qualcomm's Quick Charge technology or, at the very least, what it can do. Quick Charge 3.0, the third generation of Qualcomm's fast-charging technology, is built into most Snapdragon SoCs and it's what lets you charge your phone's battery up to 70% power in just 30 minutes. What's not to like?

During the summer, fresh strawberries are everywhere: at your neighborhood farmers market and in many desserts like strawberry shortcake and strawberry rhubarb pie, to name just a couple. Bringing home a few baskets of the ruby red fruit always seems like a good idea... until they begin to turn to mush or grow mold only a few days later.

Virtual, mixed, and augmented reality all provide different but compellingly immersive experiences that draw us in through sight and sound. But what about our other senses? A few strange inventions are already exploring the possibilities.

Vacuum sealers keep food fresher longer by first removing the air from plastic food preservation bags and heat sealing the bag to keep air out. They have rapidly become a popular way to keep your frozen food fresh.

Unless you're in law enforcement, you won't usually have a flashlight on hand for those rare moments when you need to sift through the dark. However, it is very likely that you will have your phone on you, so you'll have fast access to a bright light with just a few easy taps.

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

Salad spinners are one of the more divisive kitchen tools out there. On one hand, they're incredibly easy, efficient, and useful. On the other hand, they're a single-use tool that takes up a lot of space.

Apple just sent out a new update to their iPhones, and while that normally wouldn't have any impact on Android users, the fact that they included 184 new emojis means that the text messages you receive from friends and family members with iOS devices might come across with blank or missing characters.

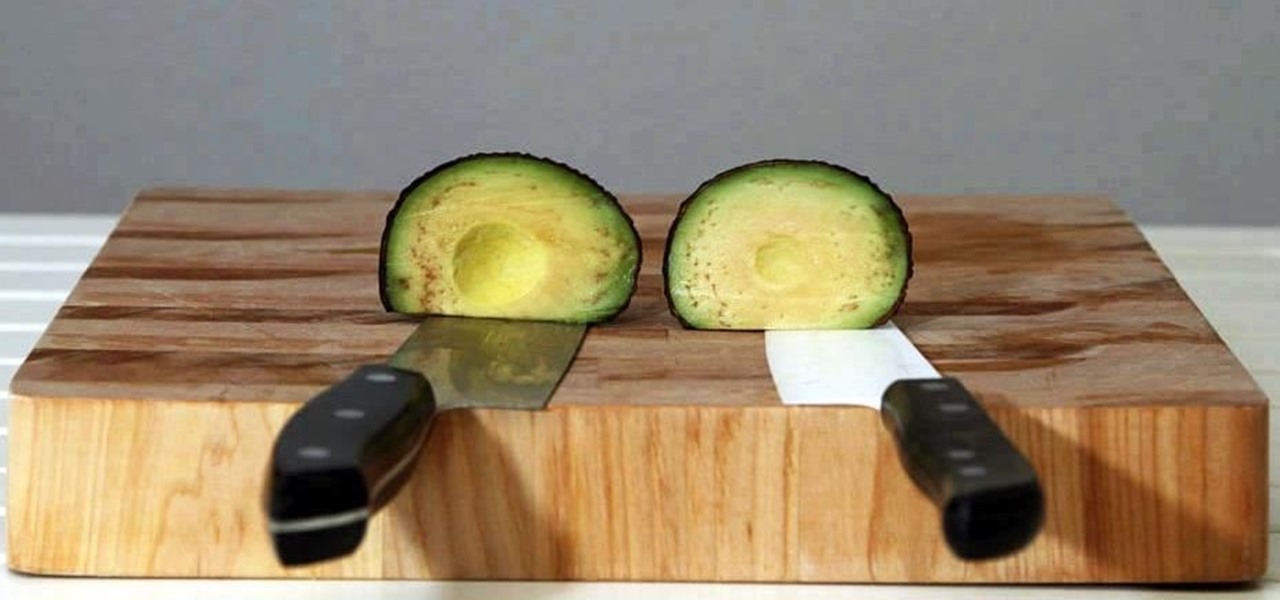
Keeping apples or avocados from browning after being cut is impossible; within minutes of being exposed to air, these fruits (yes, avocado is a fruit) begin to brown. No matter what you try—adding lemon juice, keeping the pits in place, immediately sealing the produce in an airtight bag—brown discoloration always occurs. However, air is not the only reason that foods like apples, avocados, and lettuce brown: it's also due to the knife you're using.

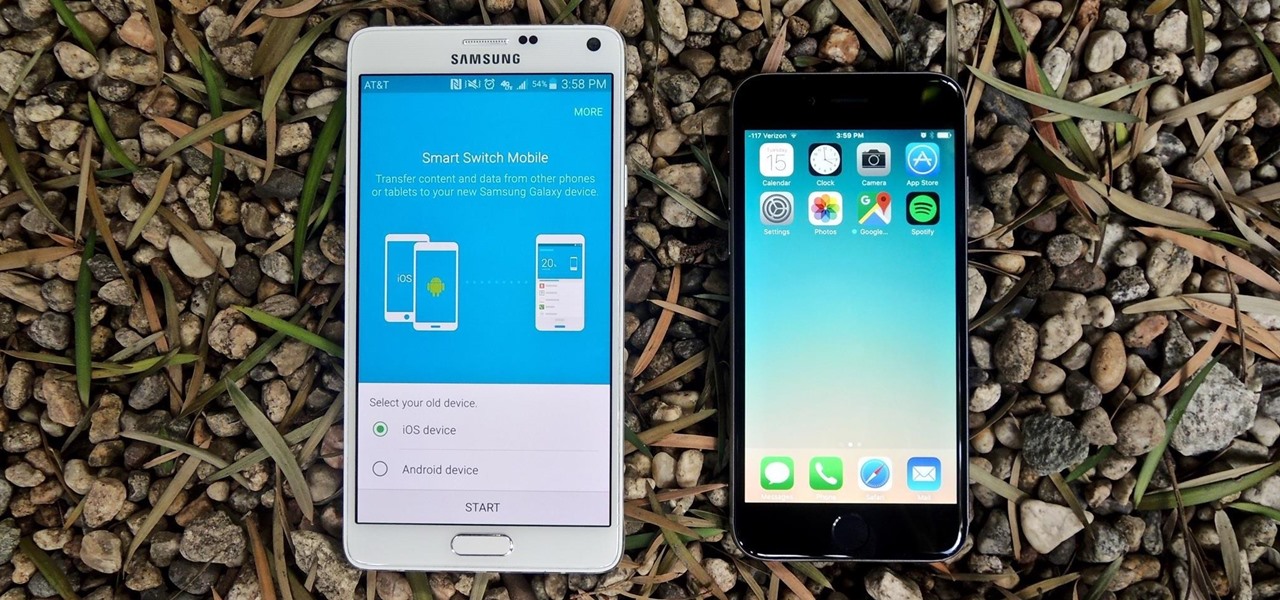
Thanks to Smart Switch, it's easier than ever now to ditch your iPhone for a brand new Samsung device, like the Galaxy S6 Edge+ or Galaxy Note 5.

Given how much use it gets on a daily basis, the power button is always one of the first hardware features to call it quits on an Android phone or tablet. So if your power button is acting up, or you don't want it to, you can extend its lifetime by simply finding ways to use it less.

Cast-iron cookware breeds a strange kind of obsession. When I got my first pan, I spent untold hours seasoning, cooking, researching the best non-soap methods to use for cleaning, and re-seasoning that thing. Finally, I became exhausted by the whole process and realized that you can skip seasoning a cast-iron pan as long as you use it regularly and clean and oil it properly in-between uses.

Screen mirroring was a long-awaited feature for the Chromecast, now available for select devices (and even more with root). While great news for those who couldn't wait to play games, watch movies, and browse pictures on a big screen, it did mean that you had to keep your device's screen on the entire time it was being mirrored.

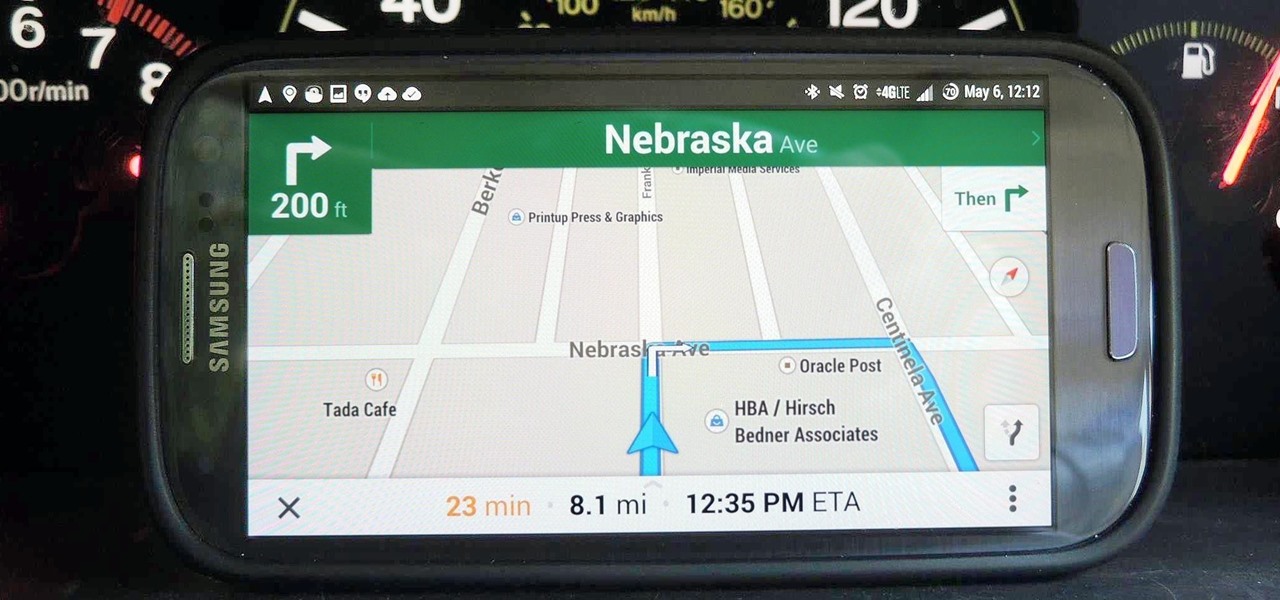
This week, Google sidestepped their usual "Update Wednesday" strategy by dropping a huge update to their Maps app for both Android and iOS. We're accustomed to seeing new features and bug fixes to their stable of apps on Wednesdays, but today's Maps update was presumably big enough to get its own release day (it's Tuesday, folks).

My kitchen isn't nearly as well-stocked as I'd prefer, and I often come across recipes that call for odd tools and appliances I don't have. Let's just say I've resorted to some unconventional methods to get the job done without them.

A flat soda tastes awful. It's almost as bad as drinking a room temperature milkshake. Of course, you can always opt to buy single-serving cans or 20 ounce bottles, but that's always going to be more expensive than 2-liters.

The advantages of rooting have been covered before, and with rooting comes flashing ROMs and mods to your device. The easiest method for flashing anything is to do it through recovery.

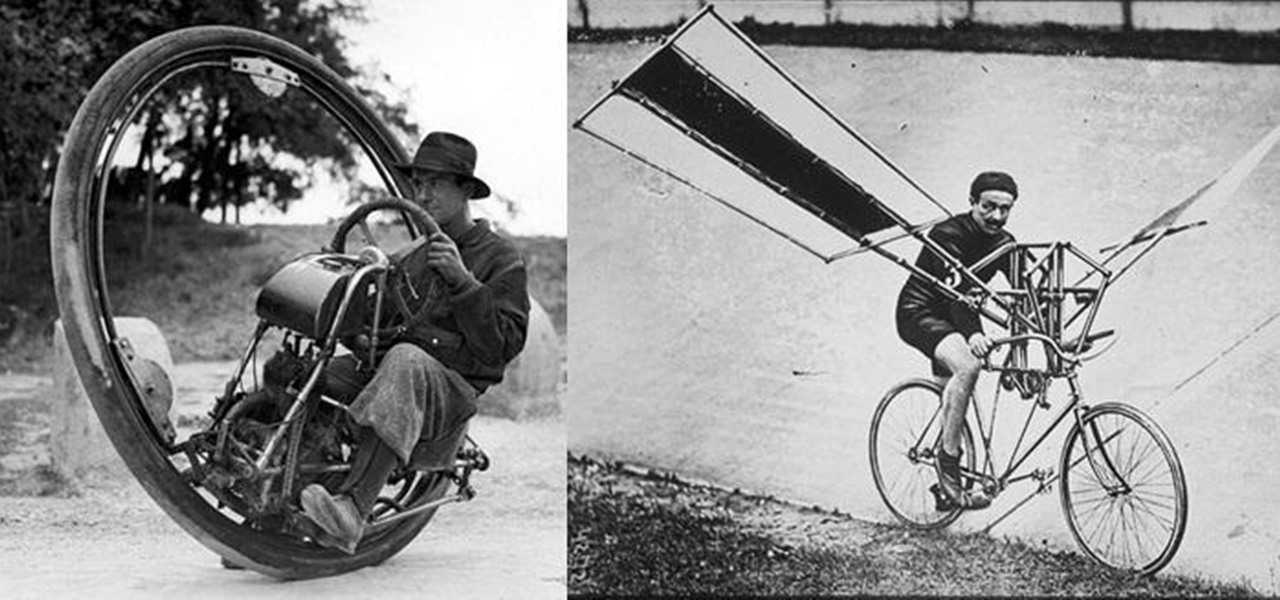
We don't spend much time thinking about bicycles today, do we? Sure, they're a "green" alternative to driving everywhere in cars, but the vast majority of America has dismissed them as simply being too much work, or more importantly—too slow. That wasn't always the case, though, I assure you!

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.