Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a participating website or put yourself out there and sell the iPhone on your own. It's all about what's best for you.

Navigating and editing text is an essential part of any operating system, and with iOS 13, Apple has made some significant changes. Some things remain the same when working with text, but there are many updates to moving the cursor, scrolling, and selecting, cutting, copying, pasting, undoing, and redoing text.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

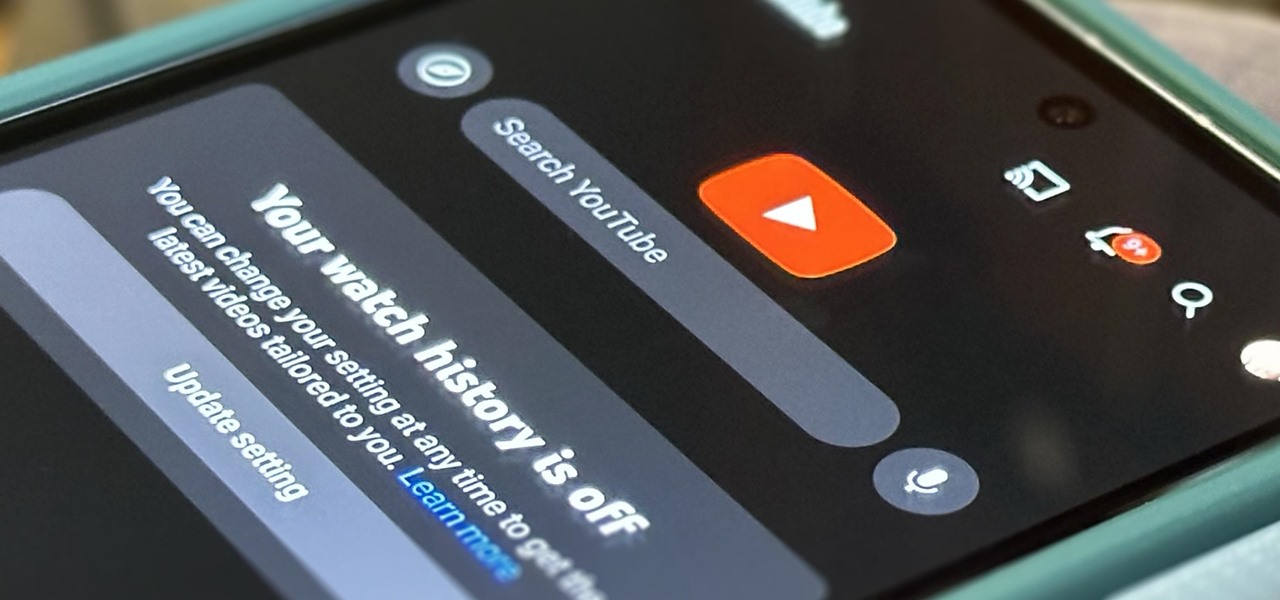
If you're an avid YouTube viewer, you may find yourself overwhelmed on the home page by recommendations from your past viewing habits. But now, you can have a clean slate on your YouTube home screen, free of recommendations.

For the avid multitasker, listening to audiobooks and podcasts is the ultimate way to passively absorb knowledge while performing other activities — but there are other options. You can turn any written text on your Android phone into speech that's read aloud to you, so there's virtually no limit on what you can soak up audibly from your headphones or speaker.

It's easy to copy text from webpages, messages, documents, and other views on your Android device — except when it isn't. Many apps block or prohibit text selection, forcing you to take screenshots or write out the whole excerpt manually. But you don't have to resort to those methods since there's a simple workaround to selecting and copying text from uncooperative apps.

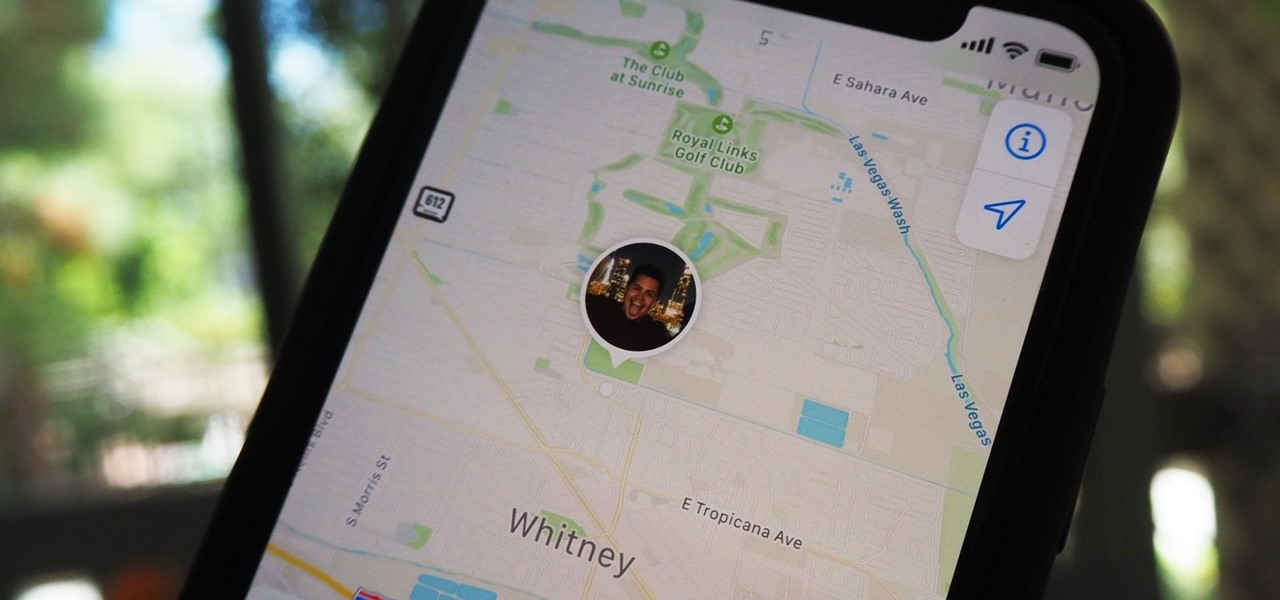
Sharing your iPhone's real-time location can be very useful when you want family and friends to know where you're at or your estimated time of arrival. By doing so, they can track you when you can't or don't want to update them manually. Depending on how you shared your location, however, they might still be able to track your exact coordinates after the initial share.

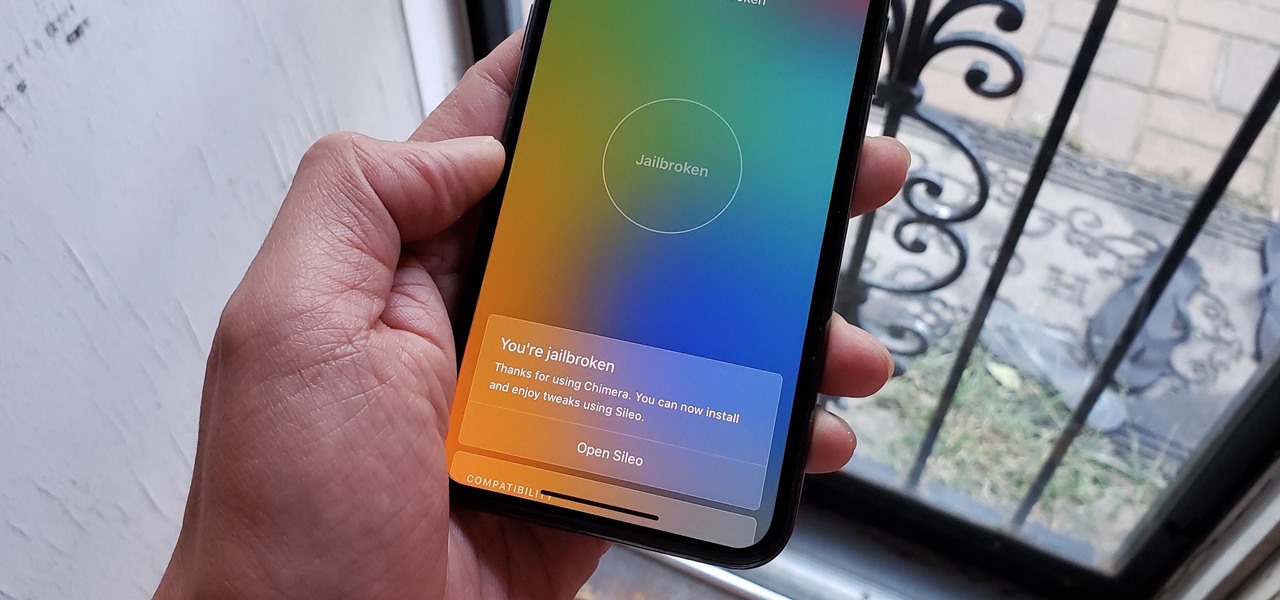
Compared to fully untethered jailbreaks, semi-untethered methods like Chimera for iOS 12 have one major handicap: you need to re-enable the jailbreak every time your iPhone turns off or restarts. As intimidating as it seems, however, kickstarting the mod and restoring your tweaks is still pretty easy.

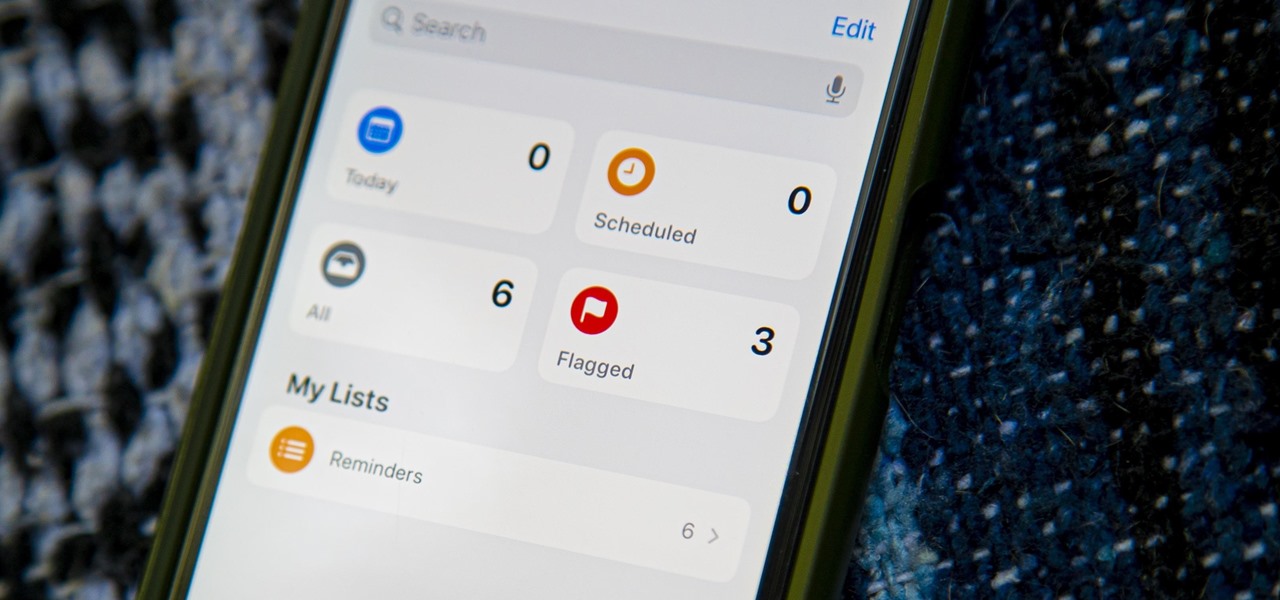
Reminders may have received the biggest update out of all the native Apple apps on iOS 13. Among other things, the new Reminders app now comes packed with smart lists to make it easier find things, and a flagging feature to help you better manage your most important reminders.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Dark mode helps battery life and low-light viewing, and it also just looks better. That's why apps like Facebook Messenger, Twitter, and Chrome have adopted dark themes, and it's why both iOS and Android have added a system-wide dark mode. But what about WhatsApp?

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Samsung's popular Good Lock app has been updated to work on One UI and now lets you take full advantage of its awesome add-ons to customize your S10 in a few simple taps. One add-on in particular lets you get rid of mostly redundant indicators like the NFC "N" for a cleaner status bar.

To build hype for the HoloLens 2 among developers, Microsoft is borrowing a page out of Magic Leap's playbook.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Many apps, including Facebook, Twitter, and Facebook, do not let you download videos, even if they are living on your own account. Saving these videos usually requires a third-party app or screen recorder, which is inconvenient and can result in loss of quality. However, TikTok, the newish popular short-form video platform, makes it easy to download videos — even if they're not yours.

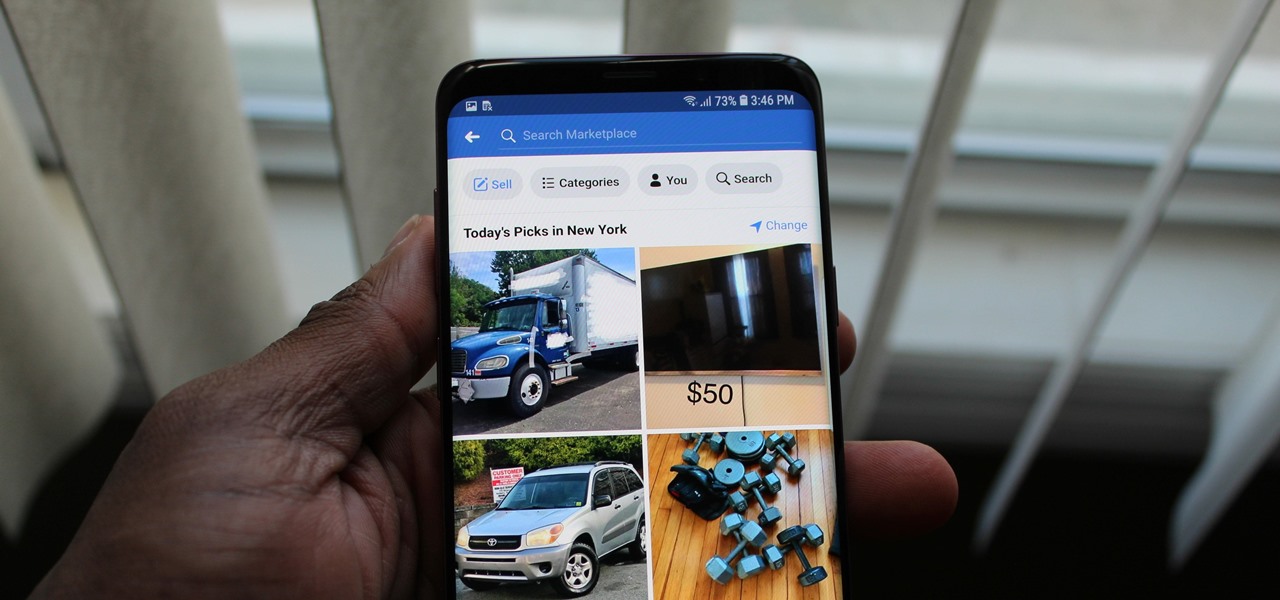
While many of Facebook's tools are well received as they enhance the experience, one which is often complained about is the Marketplace. The Craigslist-like feature which offers a way to facilitate transactions between users can be a little overbearing with its alerts. However, you can change that.

New documents reveal that electric car company Tesla has filed a surprising new patent that has nothing to do with batteries or autonomous driving and everything to do with augmented reality.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

On Thursday, at the Augmented World Expo, Stockholm, Sweden-based eye tracking company Tobii announced that the augmented reality display company Lumus will integrate its eye tracking technology into the Lumus DK50 AR development kit.

A newly-filed patent application from Disney Enterprises, Inc. teases more augmented reality lightsaber duels, either for at-home gaming or for the media behemoth's forthcoming Star Wars theme park.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

The most significant customization aspect of the iPhone is most definitely the home screen. Before iOS 14, Apple only threw in a feature here and there to appease those who like a more personal touch on the most visible part of the operating system. Now, there are great customizability options to give you a real personalized touch, and that includes app icons.

Apple's latest iPhone operating system is notorious for its frequent bugs and glitches. The latest iteration, iOS 11.3, is no exception, as users are experiencing not only 3D Touch issues but missing screenshot previews as well.

Taking photos that are actually printed and hung on a real wall, versus being shot and shared via a social wall, is a seemingly lost art, but PhotoBloom AR wants to change that with augmented reality.

Just weeks after officially launching its mobile augmented reality toolkit, Google can now claim one of its first Android and ARCore app exclusives with the Curate app from Sotheby's International Realty.

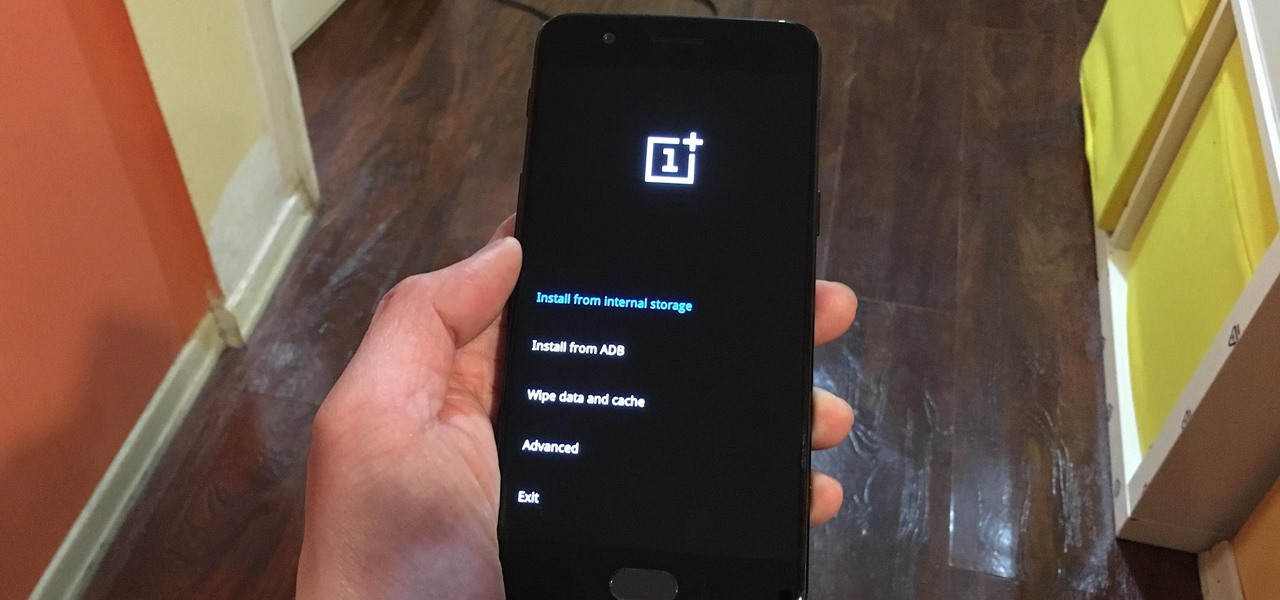
Both the OnePlus 5 and 5T have two pre-boot menus that every owner should know about: Recovery mode and bootloader mode. The recovery screen lets you wipe cache, perform a factory reset, or install firmware, which can help save the phone from a soft-brick. Bootloader mode, on the other hand, lets you send Fastboot commands via PC or Mac to lock or unlock your bootloader or flash images.

With the raw, visceral feeling of zooming around on the open road, it's easy to get carried away when you're out for a ride on your chopper, super bike, or scooter. This increases your chances of getting lost, plus routes can differ slightly for motorcyclists and cagers, unbeknownst to most drivers. Luckily, Waze has rolled out a feature that caters specifically to bikers.

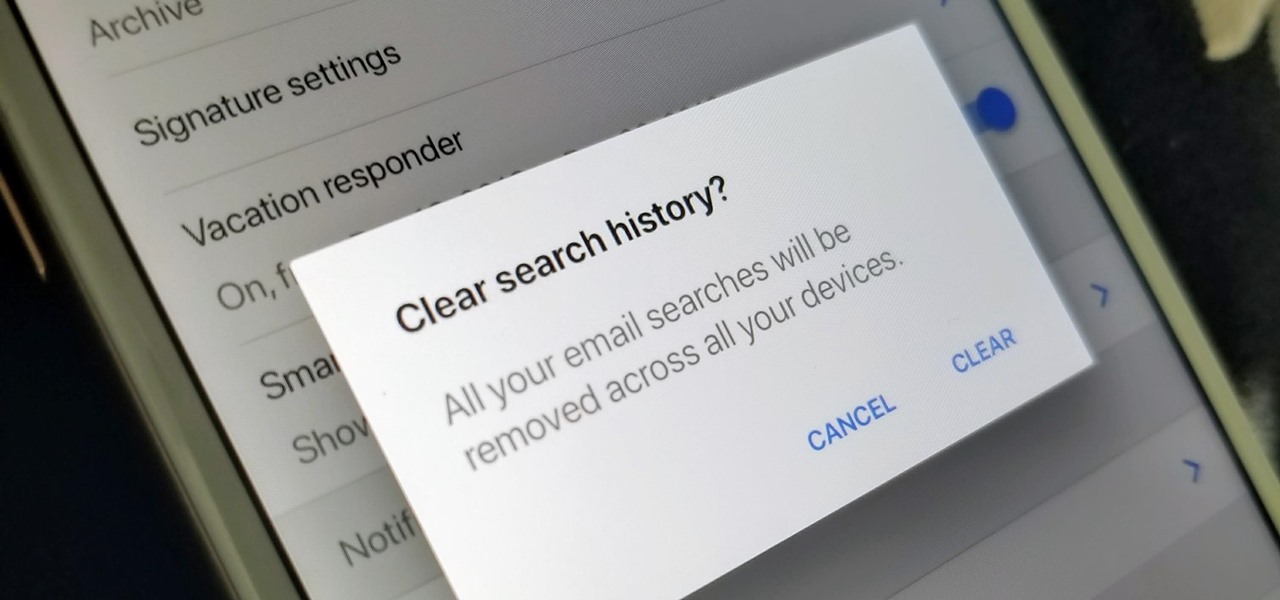
The Gmail app on both Android and iOS has a powerful search engine that helps you find any email with a few keywords. Even more impressive is Gmail's ability to remember previous search queries for future reference. However, this list of past searches can become extensively long and needs to be reset from time to time.

Based on newly surfaced information, transparent smartphones like those teased in Iron Man 2 and those hand-tracking monitors made famous in Minority Report may eventually end up being "designed by Apple in California."

The first big update to iOS 11 since its release in mid-September just came out, so check your iPhone for a software update to iOS 11.1, because there are a few things you'll want from it. While there's no sight of Apple Pay Cash or Messages in iCloud, there are some significant improvements you'll need to know about.

As with any new releases, full updates that completely revamp the look and feel of your iPhone's operating system will have teething problems that eventually get ironed out with incremental updates. iOS 11, with its issue of not being able to connect to the App Store on some iPhones and iPads, is no exception.