Microsoft and Unity have been working closely to make sure that HoloLens and Windows Holographic are supported closely with the popular game engine. Unity released a special HoloLens Technical Preview version earlier this year based off of Unity 5.4, but the update today of the main Unity app, version 5.5, has all those Holographic enhancements built right in.
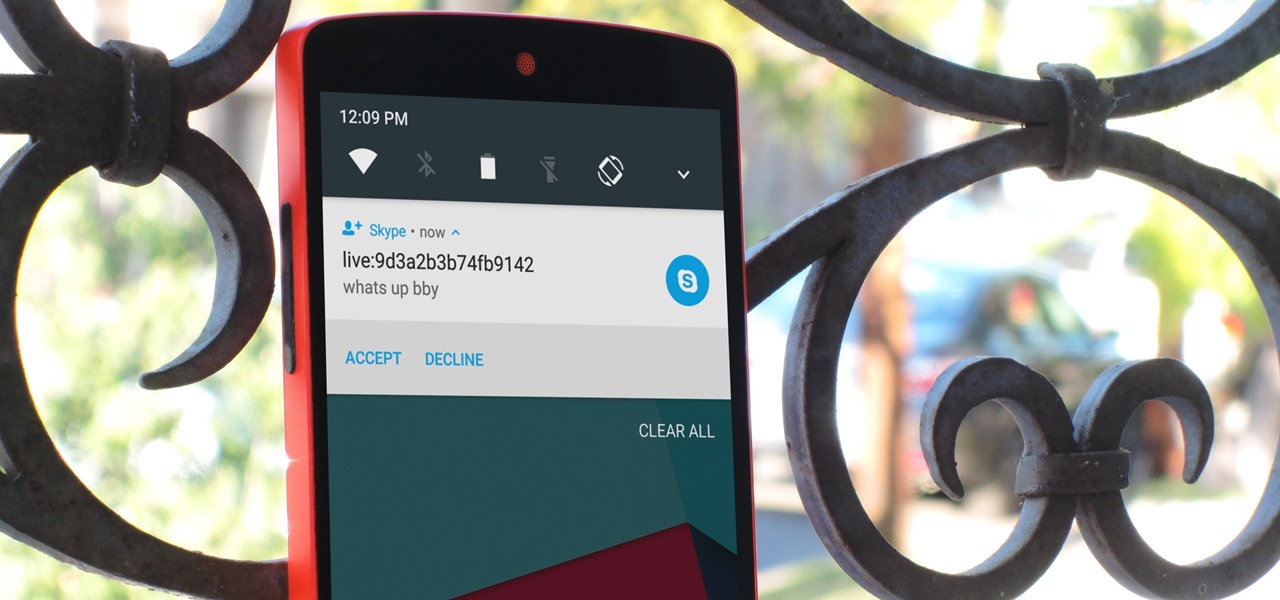
Skype is one of the most popular messaging and video chat services for a good reason—it's packed to the brim with tons of cool features. But one bit of functionality that Microsoft left out is the ability to block friend requests from people that aren't in your contacts, which can lead to a lot of unwanted notifications from spammers and bots.

Dutch police are using a system very similar to Pokémon GO on smartphones, but they aren't walking around trying to catch little pocket monsters. The purpose of this system is to give augmented reality help to first responders who may be less qualified to work a fresh crime scene. If successful, the idea of a contaminated crime scene could be a thing of the past.

In recent weeks, Unity has made a few great leaps forward for HoloLens development. These new features will increase iteration speed inside Unity and quickly increase the output of applications in the mixed reality space. Of these new features, let's take some time to talk about Holographic Emulation and why this will do so much for the development community.

While Leap Motion and Microsoft are looking to capture natural human motion with cameras, Enflux figured out how to do it with a shirt and pants that feel completely natural.

Microsoft has the HoloLens and Google has their money on Magic Leap (as well as their own Tango and Cardboard, among others), but we've heard next to nothing about how Apple plans to enter the virtual/augmented/mixed reality space. A new patent offers some clues.

Since its purchase by Microsoft in 2014, Minecraft has regularly been pushed to new platforms such as Windows 10, Wii U, and Fire TV. In that spirit, Microsoft-owned Mojang has been developing virtual- and augmented-reality versions of the blocky sandbox game.

Gesture Input works hand-in-hand with Gaze Input. If you think of Gaze Input like a mouse cursor, Gesture Input is how you "click" in HoloLens—which Microsoft calls "tapping." It's kind of like a touchpad, only in 3D.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

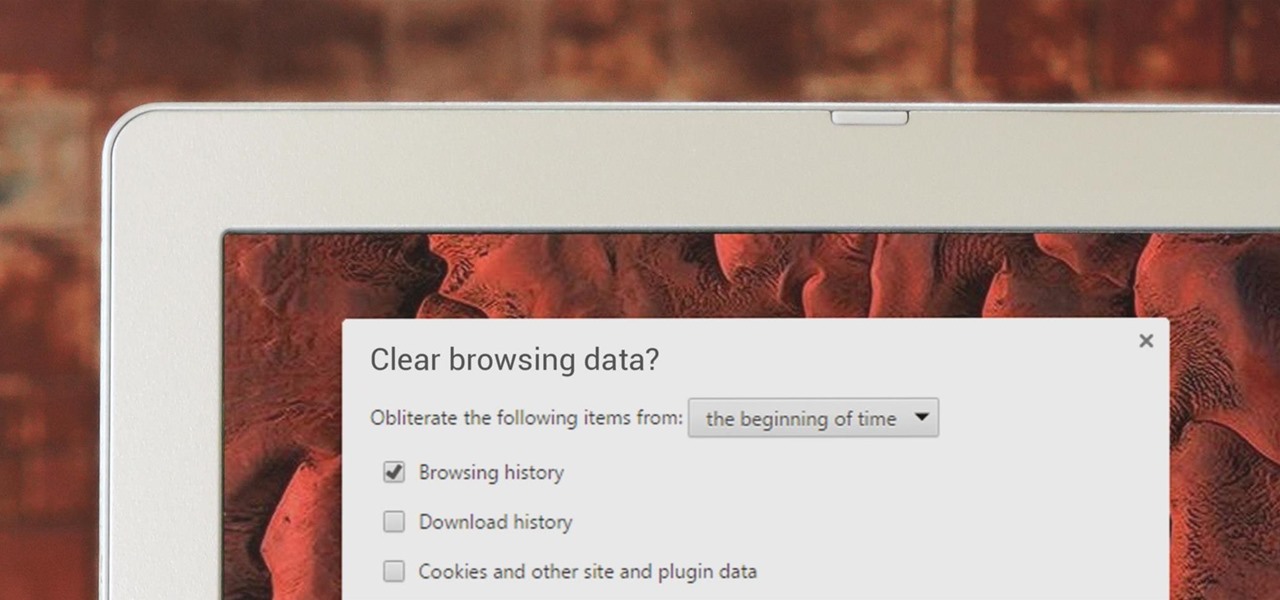
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.

Scanners are much too cumbersome to fit in a pocket, but with the use of just one application, you can replace all that bulky hardware with your Android smartphone and take it with you wherever you go. All you need to do is find the scanning app that fulfills your needs. Here are our five favorites that are good for business pros and average joes alike.

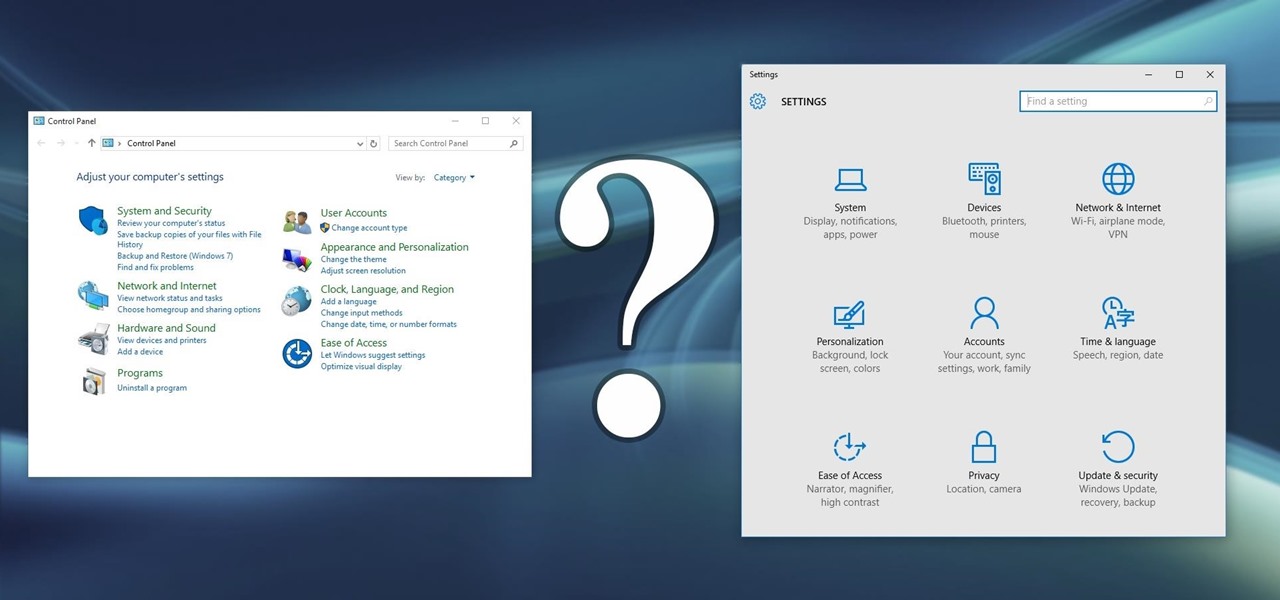
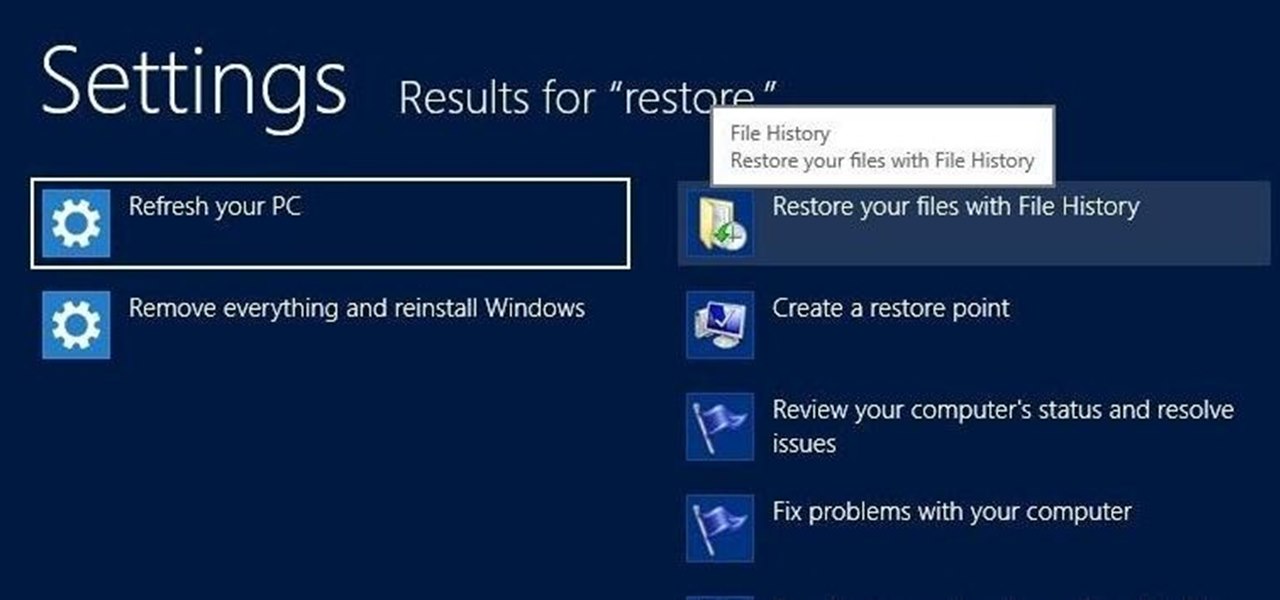
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

Cortana, Microsoft's personal assistant for its Windows Phones and Windows 10, will soon be released for Android. That is, officially released. It's hard to keep a good thing locked away, and to that end, Cortana for Android has been leaked, thanks to APK Mirror.

Surely you're aware of the Sony hacking scandal by now (here's a quick primer if you're not), as well as the multi-billion dollar company initially bowing to threats by canceling the Christmas release of the The Interview, the film at the center of the whole debacle.

Metro apps are pretty nice, but they absolutely suck on a Windows desktop with a mouse and keyboard. That's to be expected though, since Metro (also known as Modern UI or Microsoft design language) was created mainly with touch input in mind for Surface Pros and Windows Phones.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

This web design Tutorial will walk you through process of linking to files on your computer. You can link file types including but not limited to Microsoft Word, PowerPoint, PDF, Videos and so on for download on your website.

There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Windows 7 has a new feature called Device Stage. It's a powerful and handy hub for all of your electronic gadgets that connect to your PC. It's device management for the power user! Microsoft shows you the layout real quick, so watch and learn.

Libraries is a cool new feature in Windows 7 that helps you find and manage all of your documents, music, pictures and videos in one location, no matter what location there in. This video from Microsoft outlines the usage of this new feature.

Is your Outlook inbox starting to seem overwhelming? No problem! In just a few minutes you can corral that growing pile of e-mail by using the 'archive' feature. Have a look at this video and learn how to use this handy option and clean up the mess in your inbox.

The future is now, which means you can do crazy things like connect to the world wide web through your Xbox 360 and PS3. Cool, right? Definitely. But before you start surfing the Internet you'll need to adjust the settings on both your computer and gaming console. This instructional video tutorial demonstrates the process and offers helpful user tips in setting up an Internet connection on your video game system using Microsoft Windows XP.

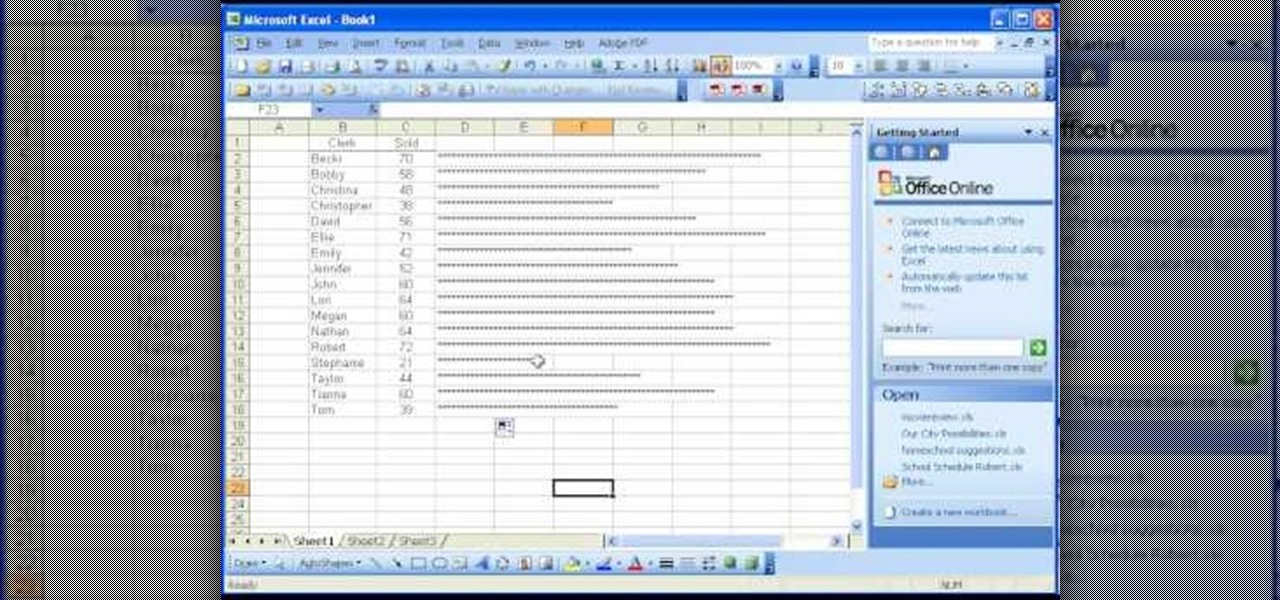
There are many functions in Microsoft Excel. One function that people rarely use is the Repeat function or REPT. In this video, an example used is a chart of people and their sales of a certain item. Just looking at the numbers, it is hard to compare the different sales easily, but a more visual approach may work better. Next to one of the cells, type in "=REPT(" which is the repeat function. A popup should say "=REPT(text, numbertimes)". For "text", type in *** or anything, really. For "numb...

Want to learn a cool glitch for the LEGO video game? Check out this video on how to create headless characters in LEGO Indiana Jones for Nintendo Wii. This is just for the Wii and may not work on other gaming consoles.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

The worlds of augmented reality and virtual reality are closely linked in many ways. That means it's smart for AR insiders to keep a close on new developments in VR. If you have been paying attention, you know that Oculus CTO John Carmack is one one of the most important thinkers in the VR space.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.