
How To: Make a ring toss game
A ring toss game can provide a fun activity that can be enjoyed indoors or out. Learn how to make a ring toss game in this free crafts video series.


A ring toss game can provide a fun activity that can be enjoyed indoors or out. Learn how to make a ring toss game in this free crafts video series.

The Tesla CD Turbine is a little homemade turbine made from CD's, CD spindle, supermagnets, and glue. It runs on faucet water pressure.
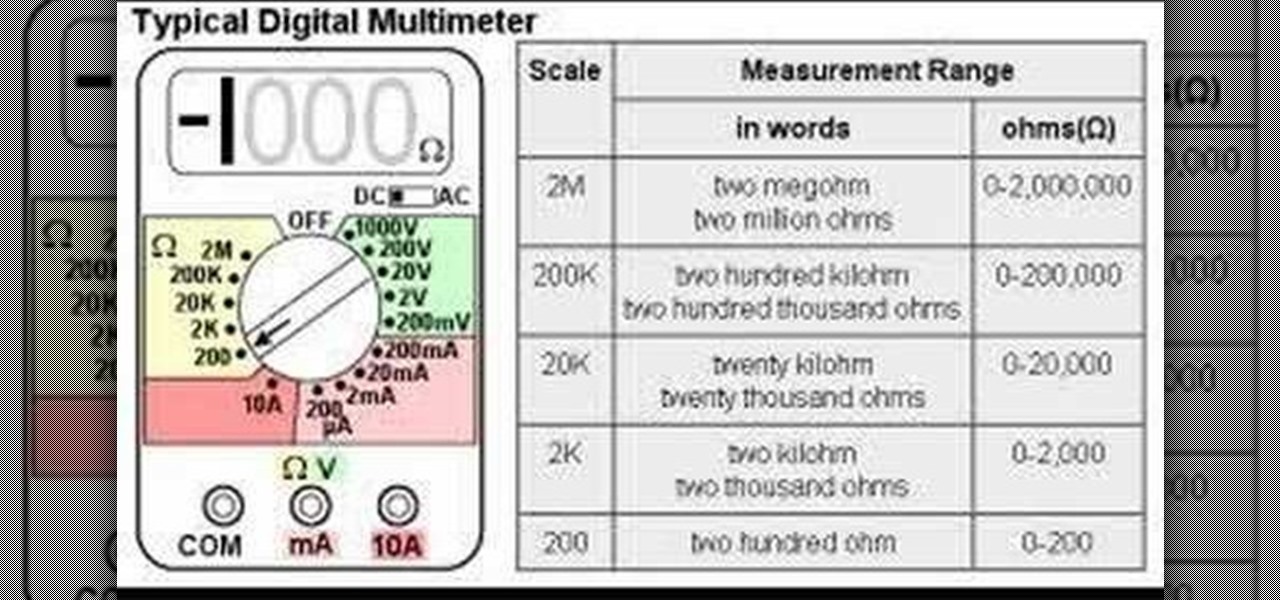
This is a guided hands-on laboratory activity to help a student understand the proper and safe use of a multimeter to measure electrical resistance. These two video guides the student through the proper techniques for measuring resistance with a multimeter, but you'll need some assorted resistors, a rectifying diode, a photo cell, an electronic labs kit, and some other stuff.

Do you love a good mystery? Were you a huge fan of "The X Files" or any other freaky movie or TV show? If you are daring and not afraid of the unexplained, Paranormal Investigator may be the job for you. Check out this video to see if you qualify and exactly how you can get into this spooky field.

Hacking seems like the only solution to today's flash-based games, like Club Penguin. If you can't do it yourself, let a cheating program do it for you. That's the new fad. Cheat Engine. That's all you need to hack online games.

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to talk about group competition games. These make the party worth while. For example; if you have let's say about 14 party guest, you can divide them up into groups of 2, put 7 in one group and 7 in the other and have a different activity for each group competition. Let me show you an example. I purchased this bag of straws, M...

Being stuck inside for the near future is less than ideal, but at least you have the world of eLearning to sharpen your skills while you kick back on your couch. Case in point, The 2020 Premium Learn To Code Certification Bundle has all the training you need to start coding like a pro right at home, and it'll only cost you $39 today.

You're halfway through reading an article on your iPhone, when the display just turns off. Frustrated, you open the article again, only for the display to go black again. You shouldn't have to keeping touching the screen to keep your iPhone from going to sleep. Luckily, you can delay or even stop your iPhone from doing so with just a few taps.
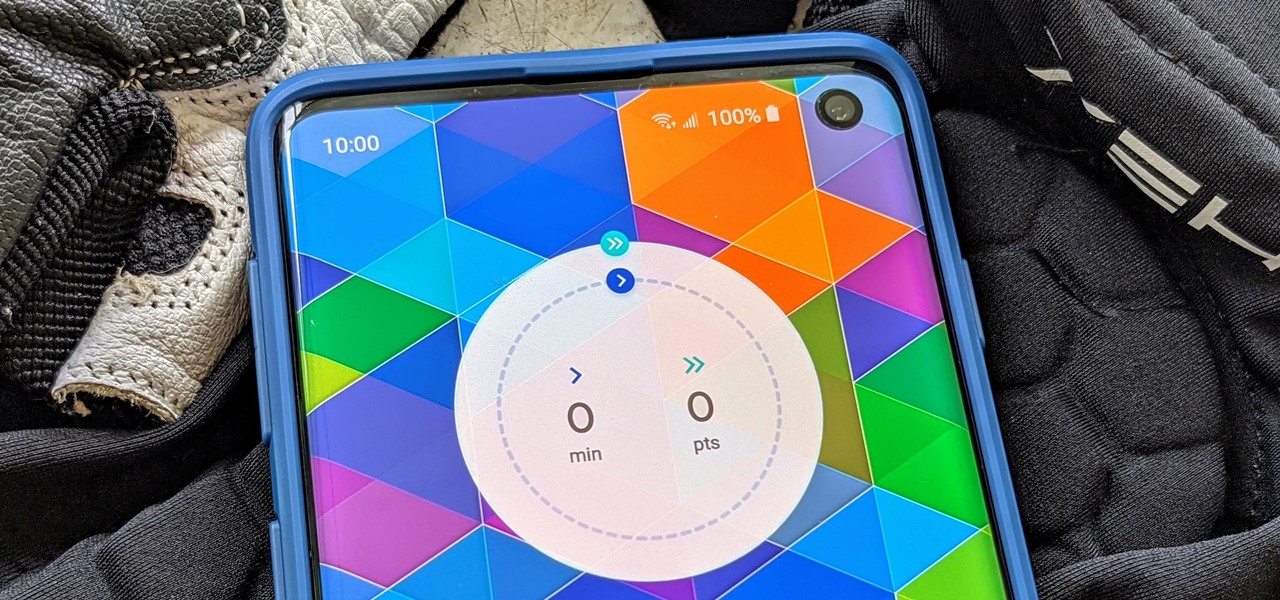
One of the great things about Google Fit is how it gives you a central hub for all the fitness-related data in both your personal life and workouts. You can track the steps you take, log your heart rate measurements, or even record your sleeping habits. The easier it is to access this data, the more useful Google Fit becomes.
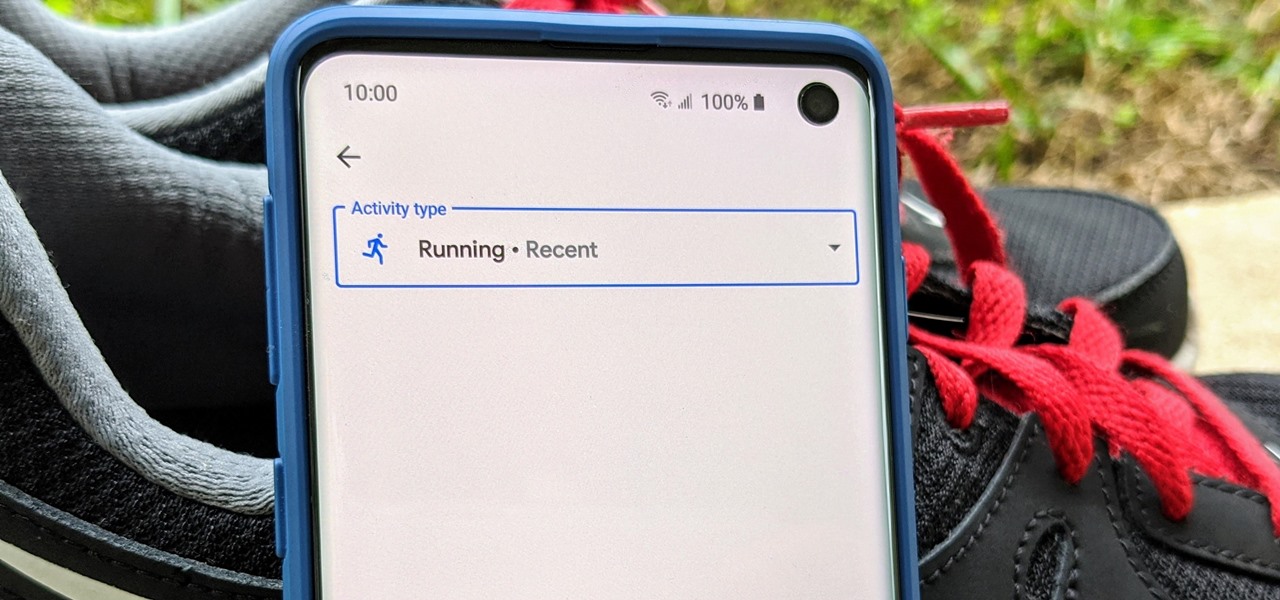
Google Fit houses all of your essential fitness-related information in the cloud for safekeeping at all times. You can easily let your device detect your workout sessions for you automatically based on a variety of sensors. At the same time, the Fit app makes it easy to manually start a workout as well.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Every year, fans of Irish culture, as well as those looking to celebrate their own culture, come together on St. Patrick's Day, March 17.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.
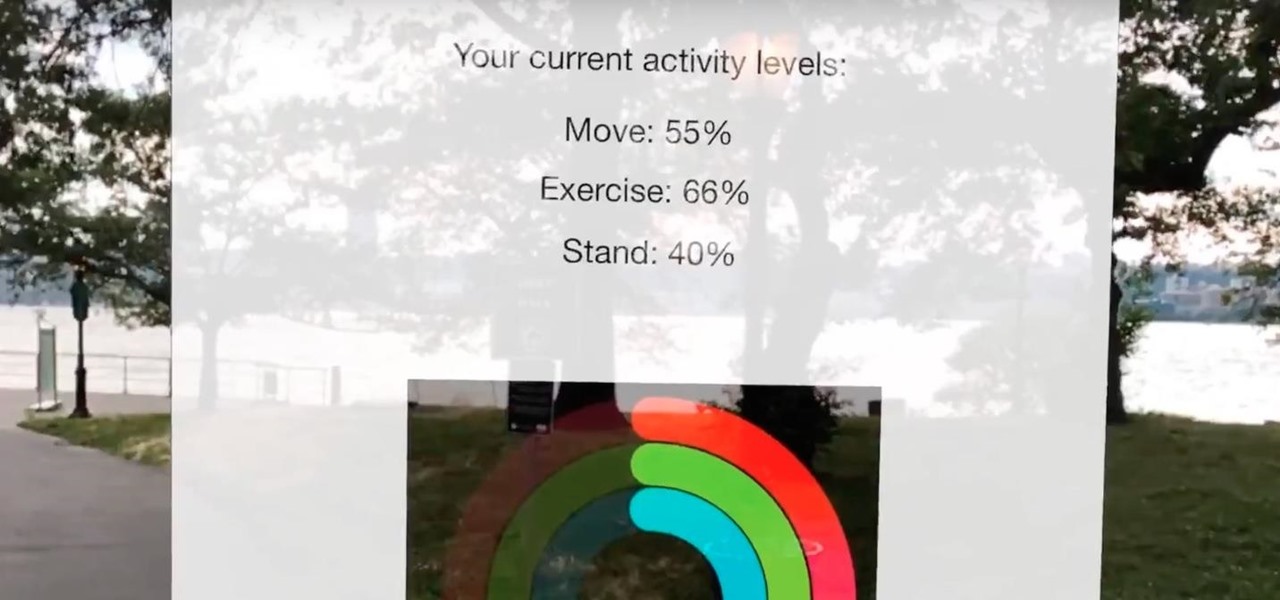
When people work out, they want to get the absolute most out of their routine. Going on a run is great exercise, but finding an optimal route that works best for you can be difficult. Luckily, Apple's ARKit has the capability to make it much easier to get the most out of your workout.

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

It's no secret that Google stores your search history in order to provide you with targeted ads when surfing the web. What's even more interesting (or freaky) is that your Google Now voice searches are also being stored, and you can actually listen to them right now.
Animal lovers, especially dog owners, know that pets are a part of the family, but it's often incredibly frustrating to know if and when something just isn't right with our furry companions. If you're out and about most of the day, your dog will be so happy to see you when you come home that you may have no idea they were tired and listless all day long, which can be a sign of health problems for your pup. This is where FitBark comes in.
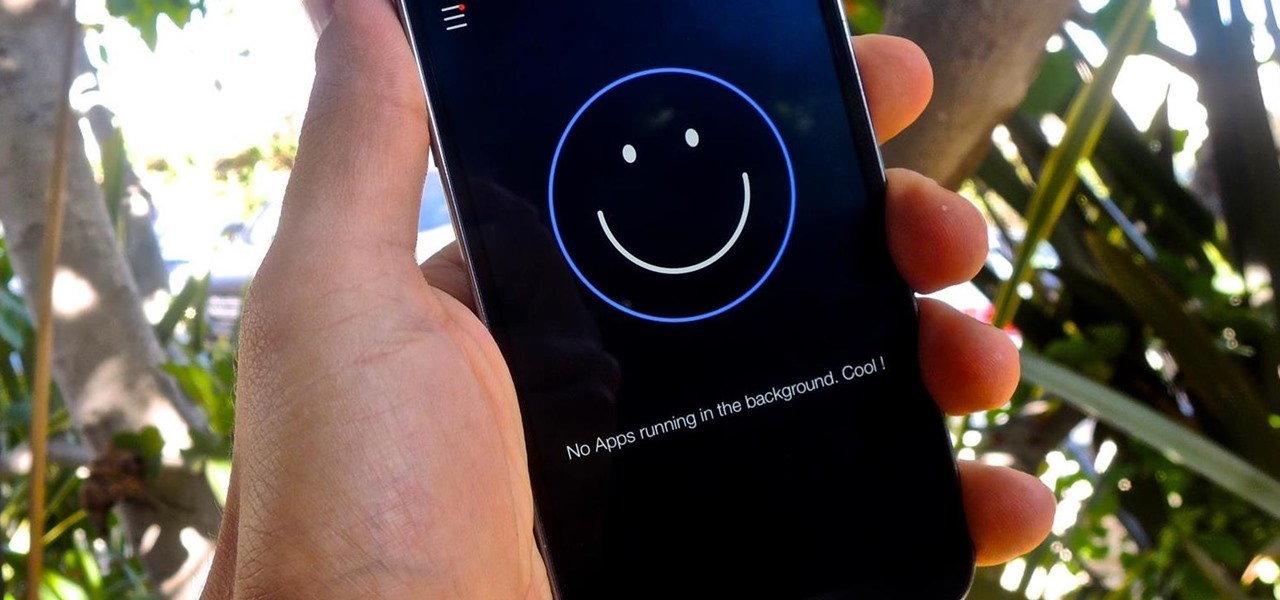
Contrary to what you may think, clearing or swiping away apps in the Recent Apps view on your Android device does not necessarily stop app activity or running tasks—and these running processes can actually be eating away at your battery life. Depending on the app or process, it may only be a small percentage, but every little bit helps these days.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

When iOS 17 first came out, the iPhone's Clock app received a giant new feature, one that lets you set multiple timers and keep track of them on the Lock Screen, Notification Center, and Dynamic Island. Now, the iOS 18 software update gives us something just as exciting for the stopwatch.
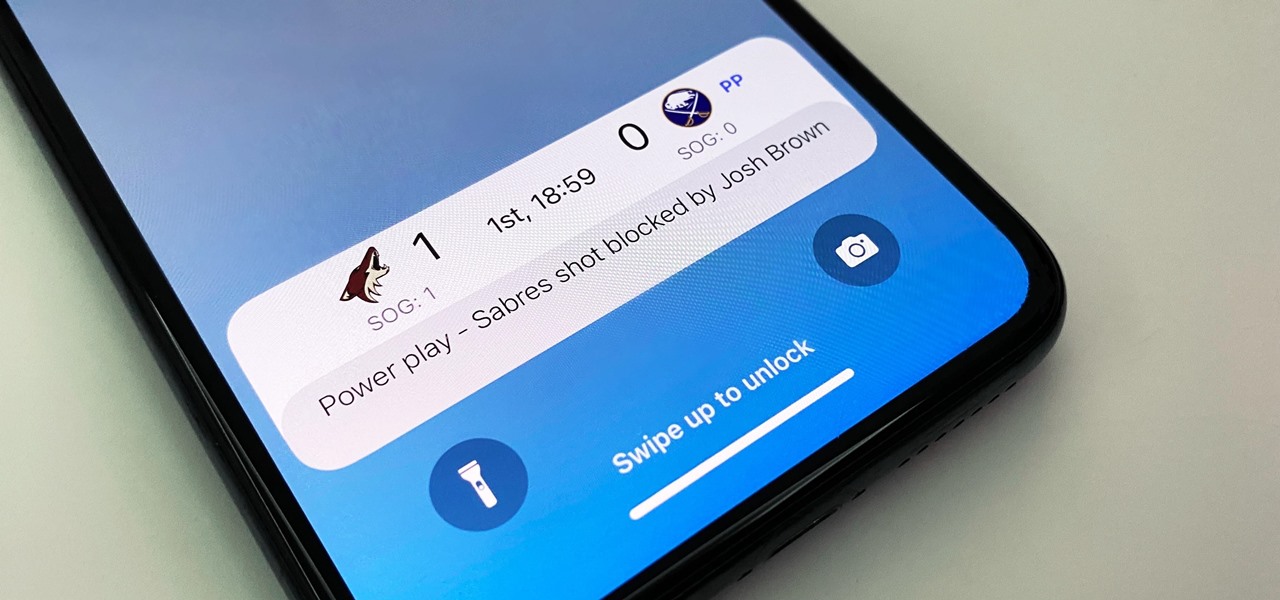
Live Activities is Apple's hottest new feature for iPhone, but it's not always straightforward. Sometimes you'll trigger one without realizing it, but it may seem frustratingly impossible to start one when you really want it.

Alternate US history is the go-to move for hot new cable and streaming shows, from HBO's Watchmen to Hulu's The Handmaid's Tale, reimagining how things might have turned out is an endless well of narrative inspiration.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.

In their first head-to-head major contract clash, Microsoft has emerged victorious over Magic Leap, as the US Army has awarded a $480 million contract to the HoloLens maker.

I've had a thing against bananas ever since Mario Kart; not only do I believe it's the worst weapon in the game, but it's also a very funny-looking food. Nevertheless, bananas are a great source of potassium, and I can't overlook that.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

If you prefer glow sticks over candles during a power outage, then this how-to is for you! Although glow sticks are used as temporary light sources, there are other applications for them. Divers use them for night diving, fisherman use them to catch swordfish, and the military uses them for light markers, along with infrared versions used in conjunction with night vision devices. But with all these handy uses for glow sticks, the most popular is — recreational use, like dancing at raves, some...

Not every nurse can get an IV every time, that's why it's important to stay in practice for the proper technique used for inserting a peripheral IV. This is a common medical procedure that all fields related to medicine should know. Even the soldiers in the military are taught how to insert an IV — every soldiers, not just the medics.

Do you have what it takes to join the elite and become a sniper? Maybe not in real life, but in a video game, you surely have the guts to become a military sniper. In Sniper: Ghost Warrior, you control a highly trained sniper, amongst a team of US Special Forces, as you try to control a military coup d'état (or just "coup") in the island of Isla Truena, which is a small fictional Latin Amercian country. Can you and your sniper team save the country from ruin?

In this tutorial, we learn how to find your recovery heart rate. First, get your heart rate up by doing some sort of activity that you enjoy doing. After you have your heart rate up, figure out how many beats you have in fifteen seconds. After you have counted this, multiply it by four. Now, sit back and relax for two minutes exactly. Next, time another fifteen seconds with your stop watch and count how many beats your heart has. Multiply this number by four, then subtract the two numbers. Af...
If you're sick and tired of you laptop dying all the time, then the answer may be right in front of you— power management. In Windows 7, it's easy to control your power settings to help you laptop's battery last longer. Watch and learn from none other than Microsoft.

Keith Ferrazzi teaches you how to be outgoing. Although it is difficult to talk to people you don`t know, you might miss out on opportunities if you don`t. Only by reaching out to people, you will meet them and they may get to know you enough to perhaps be of help to you in your carreer. You have to learn how to speak up. One way is to pick a role model in your social circle who is outgoing and watch how they behave and listen to what they say. Joining a Toastmasters group is also recommended...
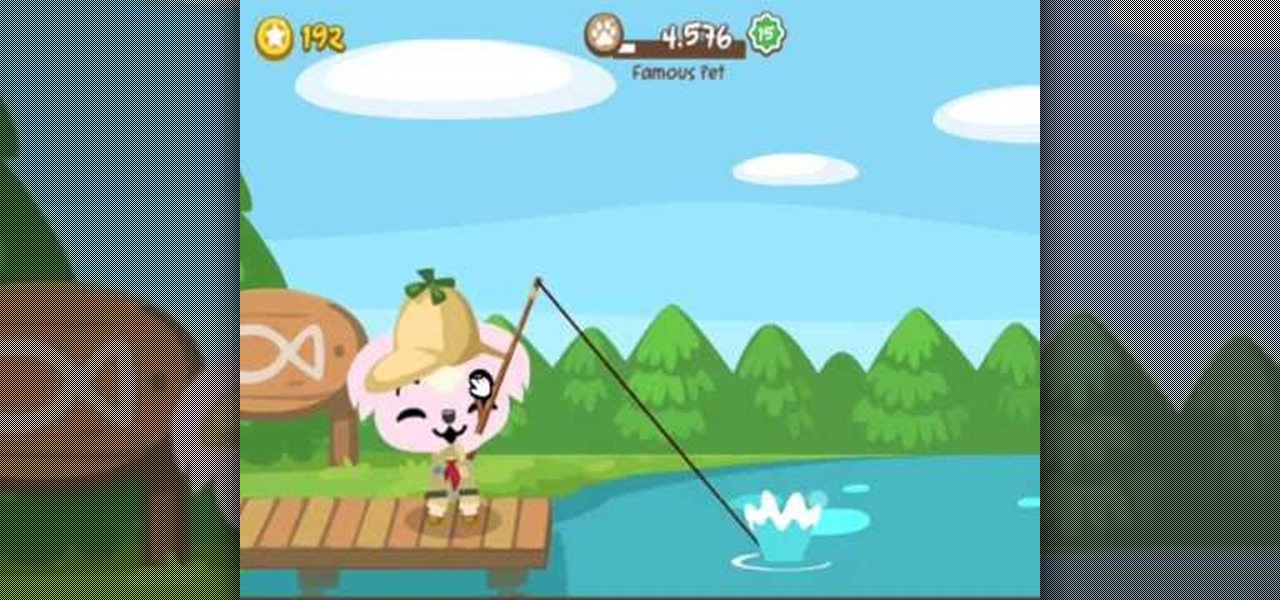
See how to hack Pet Society from Playfish! Pet Society is the popular online game where you can design and take care of virtual pets. Check out this video tutorial to learn how to fish in Pet Society (11/15/09).

d-CON is here to help identify and remedy rodent problems in your dining room. Watch this video tutorial on how to use d-CON Quick Kill Glue Traps to kill mice in the dining room. Signs of a mouse in the dining room include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your bedroom. Watch this video tutorial on how to use d-CON Ultra Set Traps to kill mice in the bedroom. Signs of a mouse in the bedroom include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your home. Watch this video tutorial on how to use d-CON Ready Mixed Baitbits to kill mice in the home. Signs of a mouse in the home include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your bathroom. Watch this video tutorial on how to use d-CON Bait Wedges to kill mice in the bathroom. Signs of a mouse in the bathroom include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.