How To: Build Your Own Kinect-Like 3D Tracking Interface with Cardboard, Foil, and Arduino
Back in 2008, media artist Kyle McDonald created a 3D interface that could track movement, which he turned into a virtual Tic-tac-toe game.

Back in 2008, media artist Kyle McDonald created a 3D interface that could track movement, which he turned into a virtual Tic-tac-toe game.

Yep Kitty Litter, but DON'T FREAK OUT! Read or watch the video before you make any assumptions. This mask is perfect for oily, dirty, large pores skin! If you need to detoxify your skin, this is the best mask to use, and you can make it right at home! Use this once every 2 weeks. You should deep cleanse your face once every 2 weeks to remove impurities. Unscented Kitty Litter is made out of Clay, Bentonite clay to be excat. Bentonite is clay that is is rich in minerals and it comes from volca...

Kongregate is a site that allows users to upload games. Users must go to the site to download the hack. On the site, select Kongregate. Then select the first topic and click on KBH 2.0.14. Once downloaded, you can extract the files onto your desktop. Open up the file and follow the video on how to use it. It also comes with the auto rater. This video will benefit those viewers who play games on the Kongrgate website and would like to earn badges.

This video tutorial shows you how to use a free program to customize the HTC Home plug-in for Windows Mobile touchscreen devices. You can use any Windows Mobile cell phone or other device for this hack. YOu can run applications like Streaming Media on your HTC Home site from your smartphone. Just watch and learn.

See the low cost fluorescent lights Bill Myers uses when shooting video, and how to quickly set your camcorder to get perfect color under these lights.

Join parallel sticks with shear lashing. Potentially--if you did this to enough sticks--you could build a house this way. It might take one hundred years but, let's face it, you probably have time if you are on this site.

Got some home-recorded video on DVD you want to put on your Web site? Tom Merritt from CNET shows you how.

This tutorial shows you how to use iPhoto '08 to create a book (or photo album) of your photos. The cool part is when you're done making it, you can upload it to the Apple site to buy your book and have it printed and shipped to your door.

Born in New York, raised in Los Angeles, Ric O'Kane started competing as a martial artist at 18. He has trained at the World Famous Jet Center in Van Nuys, California where he fought with Benny “The Jet” Uriquidez in the early ‘80’s to mid ‘90’s. Ric holds four titles. Muay Thai, otherwise known as Thai Boxing is a hard martial art practiced mainly in Thailand. Named as the national sport, a modified version of Muay Thai is practiced by the military in self defense.

How far would you go to save your life? For James Franco, who plays real-life hiker Aron Ralston in Danny Boyle's "127 Hours", staying alive means cutting off your own arm with a dull pocketknife. If you've seen the movie (or even heard about all the people who fainted and threw up after watching it), you know that it presents one of the most grueling self-amputation and bone breaking scenes in movie history.

These videos will take you through the fifth episode in Alan Wake on the Xbox 360. You're almost to the point of discovering where Alan's missing wife is. Is she in Bright Falls or is she dead? Before you can find out, you have to defeat Episode 5 - The Clicker. Watch the gameplay on Nightmare Difficulty.
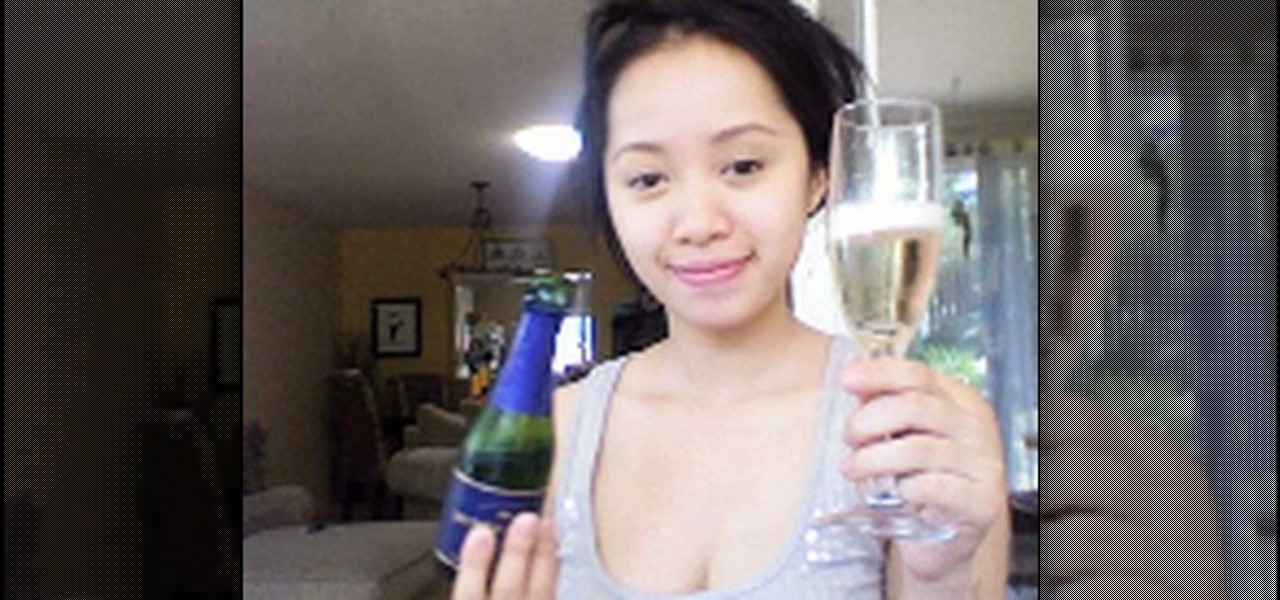
Michelle Phan presents this tutorial video on caring for your skin with champagne. You can use less than a sip of your champagne as a detoxifying cleanser/ toner.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to fix, enhance, and retouch photos in Photoshop.

Imagine a game almost anyone can play that combines the best of skee-ball, bowling, and shuffleboard. Welcome to the ancient sport of bocce.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.
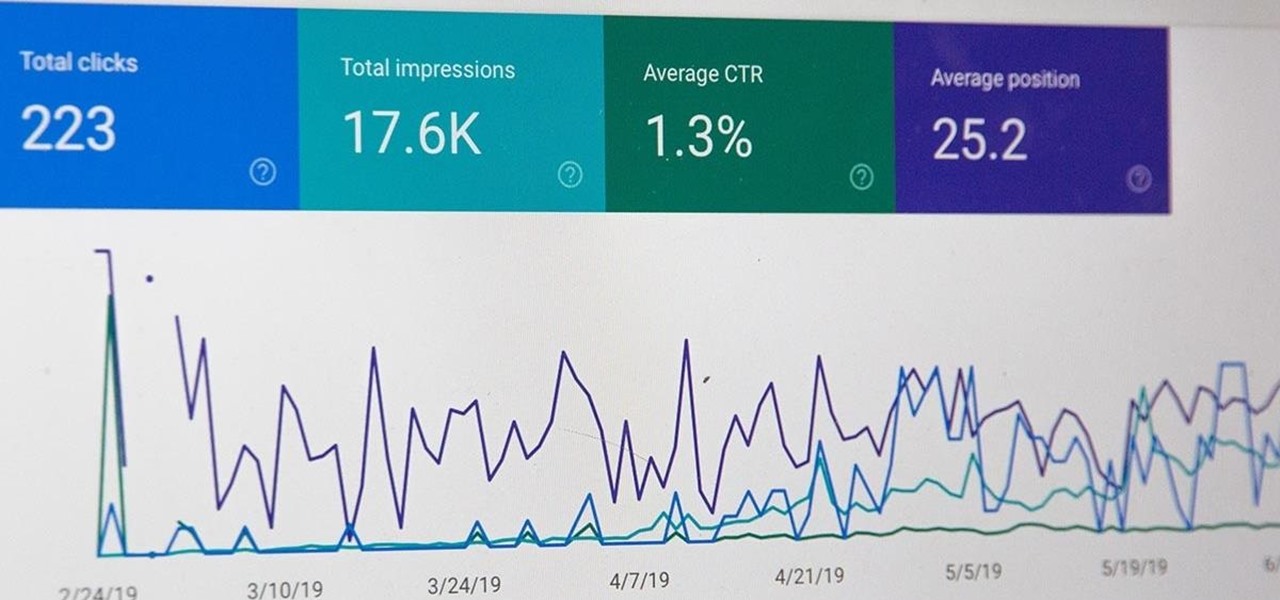
You know just how great your products and services are. Now it's time to let the rest of the world know. Of course, that's easier said than done. You're probably competing with bigger, more established brands that can afford to spend their way to the top. You can make it a fair fight with a little SEO optimization.

The web development landscape has changed dramatically over the past ten years. Both aspiring and seasoned developers now need to know a wide range of programming languages and platforms to create truly pro-level sites from scratch, and continuing education is vital if you want to stay ahead of the curve and be competitive in this increasingly popular and lucrative field.

For a decade, Microsoft Azure has been transforming businesses across the globe. The cloud-computing service is leading the way in software as a service (SaaS), platform as a service (Paas), and infrastructure as a service (IaaS) protocols.

With over two billion websites floating around cyberspace — only 400 million are estimated to be active — you need every tool you can get to stand out. Great design, fonts that capture attention, and SEO placement are all necessary ingredients to success.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.
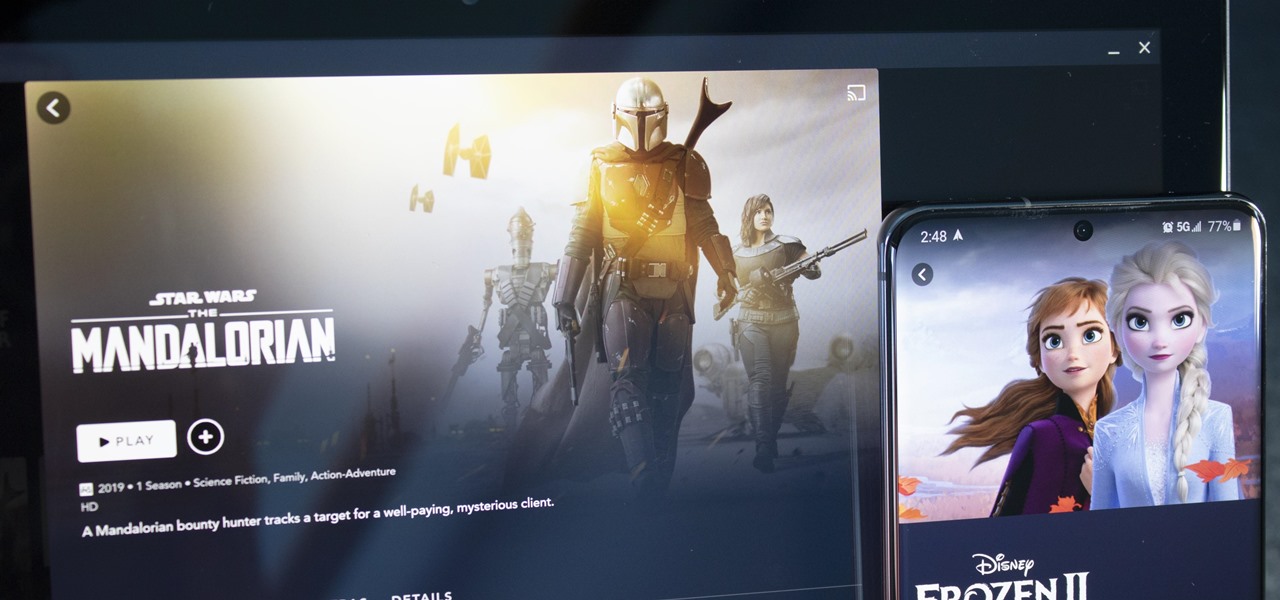
With shows like "The Mandalorian" and movies like "Frozen 2," Disney+ has quickly become a must-have streaming service. However, with Netflix, Amazon Prime Video, and Hulu, adding another subscription-based service can become expensive — but there are ways to trim down the cost.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.
A universal dark theme has long been one of the most sought-after features we've been urging Apple to introduce for iOS. While this wish went unfulfilled with iOS 12, there's renewed hope that it'll finally touch down with iOS 13's arrival. The jailbreak community, however, has had this functionality available for quite some time, and you can too if you're running the right iOS version.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.
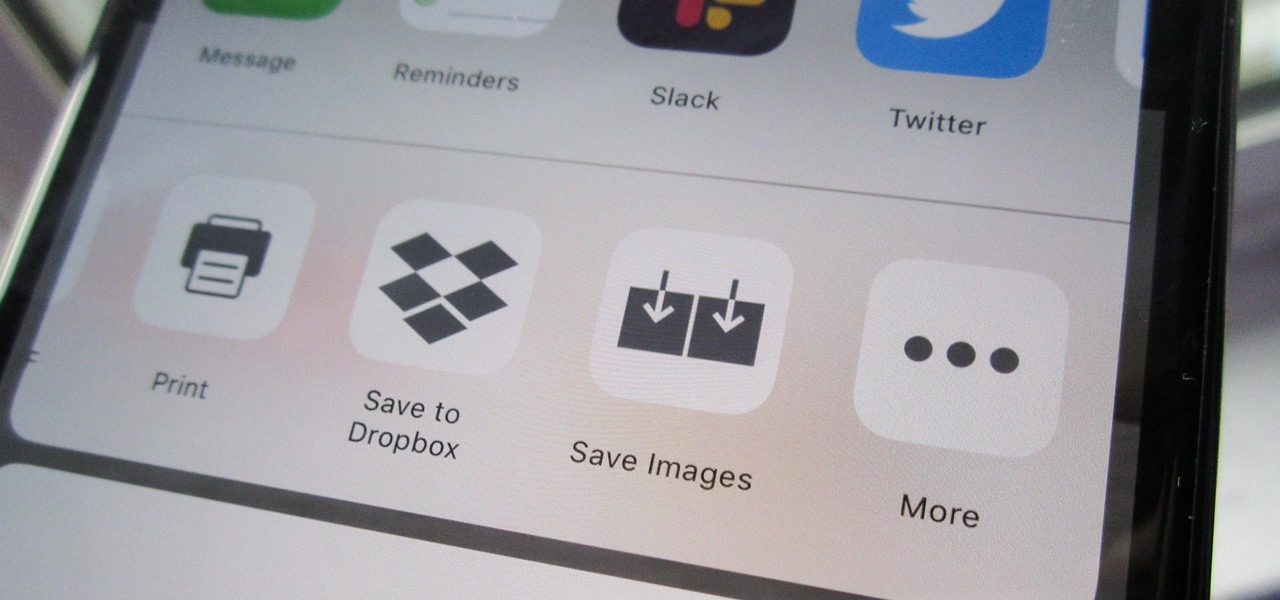
Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Sony Pictures has tapped the powers of augmented reality as provided by startup 8th Wall & the Amazon Sumerian development platform to help it promote the latest motion picture manifestation of Spider-Man.

Now that the Magic Leap One is out in the real world, the mystery behind the company lies not in whether it will actually ship a product, but when it will ship a consumer product. Or, does CEO Rony Abovitz steer the company in a different direction first?

Let's face it, iPhones are expensive. With the latest iPhone XS Max reaching as high as $1,449, our wallets could all use a little support. That's where Black Friday comes in, supplying us with deals and discounts on iPhones of all kinds. If you're looking for a new iPhone this holiday season without having to break the bank, you've come to the right place.
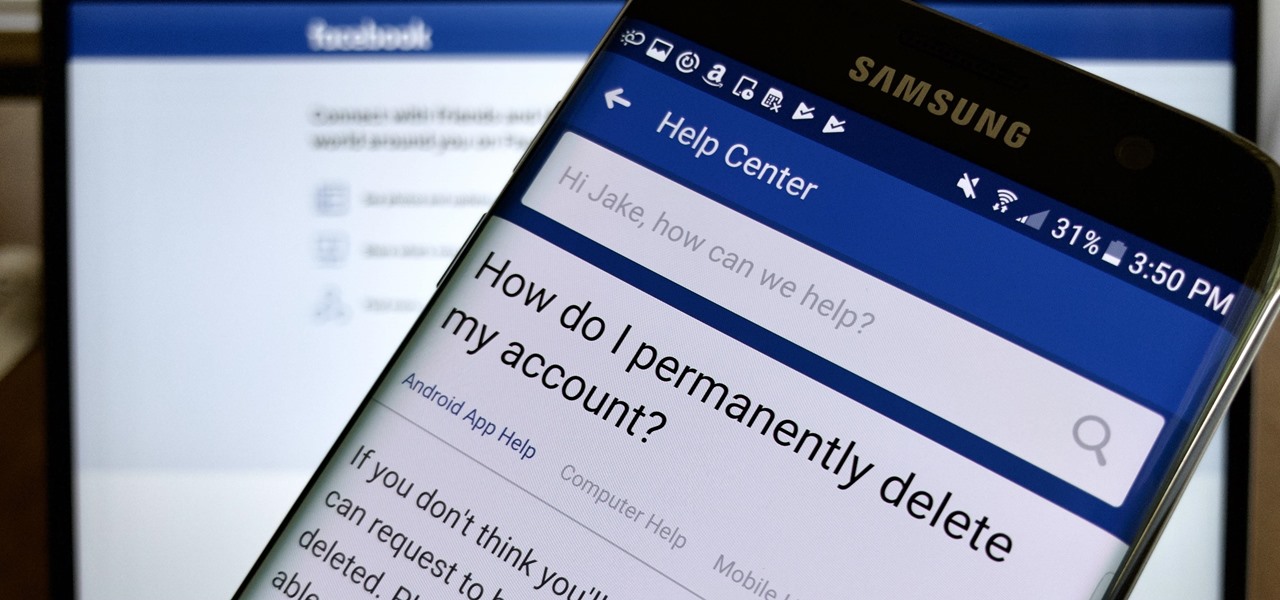
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account is actually a quick affair. You just need to know where to look.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

Last year, OnePlus released not one but two excellent flagship devices with the OnePlus 5 and 5T. While the 5T released sooner than expected, it brought some worthwhile upgrades, such as a near bezel-less display and a much-needed camera enhancement. Now, that the OnePlus 6 has arrived, it's time to see what OnePlus has in store for 2018.

With Mobile World Congress fast approaching, all eyes in the industry are set on Samsung's Galaxy S9 announcement on February 25. While leaks and rumors about the S9 and S9+ have been flooding in for quite some time, we're getting a much clearer picture of these handsets as the announcement draws near.
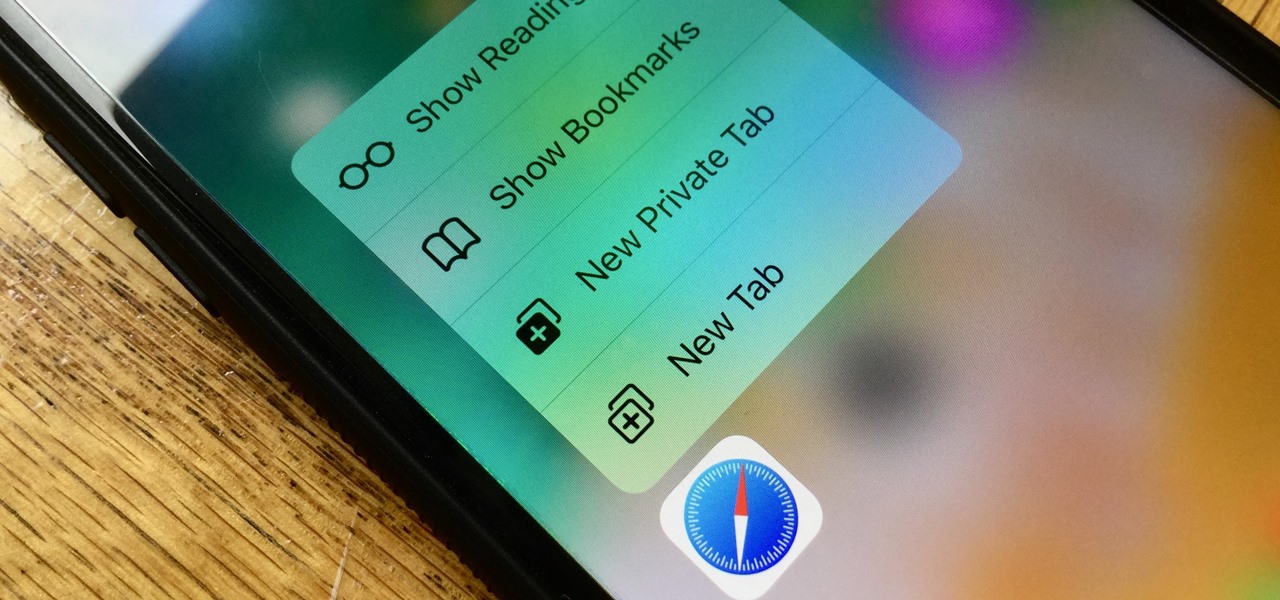
Introduced on the iPhone 6s, 3D Touch is just about the closest thing to a "right-click" that we have on iOS. Apple and app developers utilize this feature to give us helpful options that might otherwise clutter the overall app experience, as well as opportunities to "peek" into an action without committing to it. Safari on iPhone is no exception.