Synchronize and backup your Microsoft Office Documents using Google Docs and Docsyncer. This is a great tutorial from Tinkernut on how to backup your files and Word docs using the free Google software.
Want music now? Not keen on downloading software or suspicious files to get it? This is a handy media trick from Tinkernut on how to torrent audio files without downloads. Stream music torrents without having to download any torrent software using Bitlet.org .

This video illustrates tapping on the '3' or the upbeat (halfway through the beat). Count '1-2-3-4' for each beat. ('1' being the downbeat, '3' being the upbeat or exact middle, and '2' and '4' being the places inbetween or the quarter beats). It is not a synchopated embellishment, as it happens on an even division of the beat.

Have you become a Jedi in your Star Wars delusional mind? If so, break out of the the asylum with a Jedi lightsaber. Oh, but you don't have a lightsaber yet, okay. Well, this video tutorial will show you how to make a very inexpensive LED light saber with the most basic parts you could find. Novastar will shares his Jedi wisdom on LED light sabers, so pay attention, or you could never get out of that loony bin.
Learn the important steps necessary for the best printing experience when printing to the HP Photosmart Pro 9180. Keep in mind that many of the steps that are detailed in this tutorial can apply to many of the other fine HP printers. Here is a detailed explanation of the changes that were made to the 10.0.1 update to Adobe Photoshop CS3. Remember, having all the current versions of Adobe Photoshop, and the Epson drivers is critical to success when printing.

You may have lost your files but you needn't loose hope, too. In this episode of Lab Rats TV, Andy and Sean show you how to recover your deleted data (and your marriage!) using oranges. For detailed instructions on recovering your own lost data, take a look at this tech how-to.

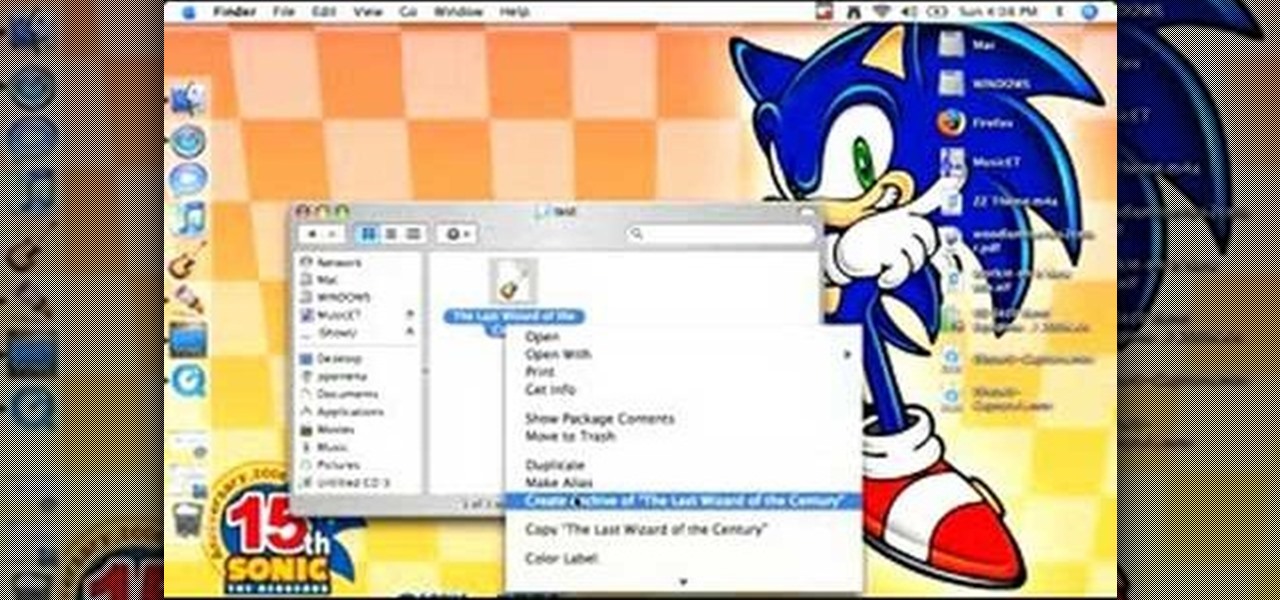
This software tutorial will show you how to email GarageBand files. Learn how to zip the GarageBand file and create an archive so you can email your GarageBand music files.

Here is a very in-depth description on how to make a silencer, but really a sound suppressor for your paintball gun. If you want to try to make a suppressor for a real firearm, the principles are basically the same. So, for ninja-like paintball action, watch this video tutorial to see how to make a silencer for a paintball gun, or sound suppressor, whichever you would like to call it.

This tutorial video will show you how to make an adorable greeting card that has a hole in the middle for storing files. this greeting card it great for any occasion and means so much more because it's hand made.

Learn how to record audio from video files (even Flash .flv files or Youtube videos) using the Windows sound recorder. All of the software used in this tutorial comes bundled with Windows.

Now that summer is swiftly approaching, it's time to start wrapping your mind around that most enjoyable of summertime treats: Ice cream. While you can certainly go to the store and purchase bulk packages of rocky road, store-bought ice cream is full of gnarly-sounding ingredients that sound more like a chemical found in a mad scientist's lab than actual food (xanthan gum, anyone?).

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

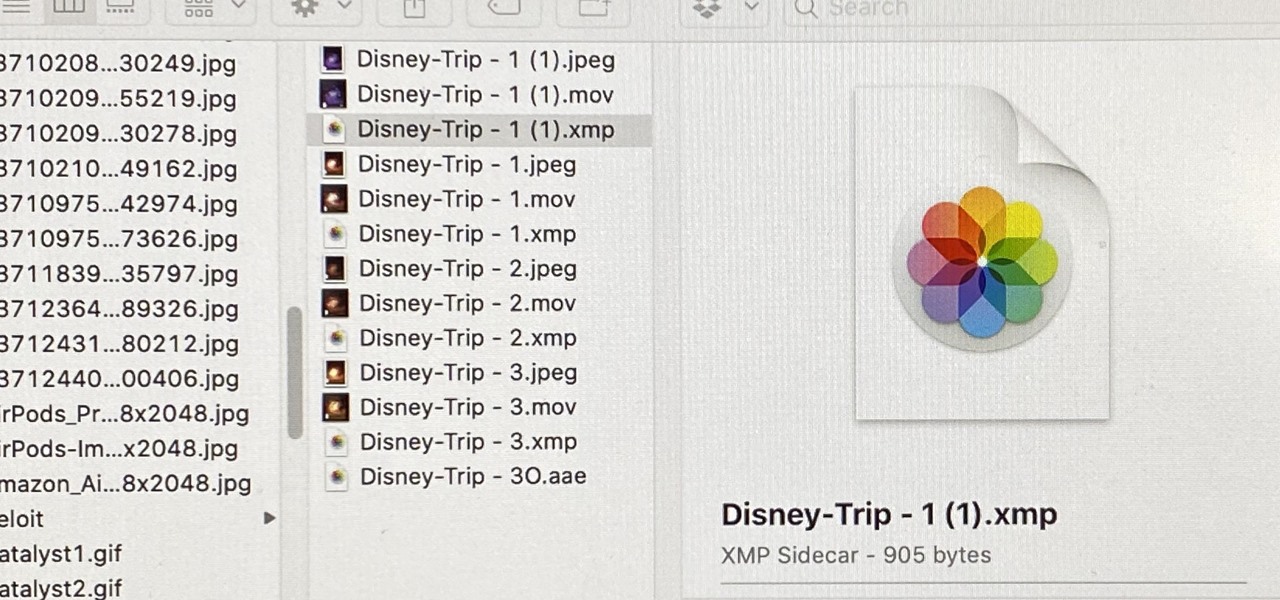
When you export an image from the Photos app in macOS, you may not be getting the whole deal. In the export menu, you need to select either JPEG, TIFF, or PNG, and if you don't make any adjustments to the quality settings, it'll likely be compressed. If you need the original full-resolution file or want to get the video that's attached to a Live Photo, there's a simple way to do it.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

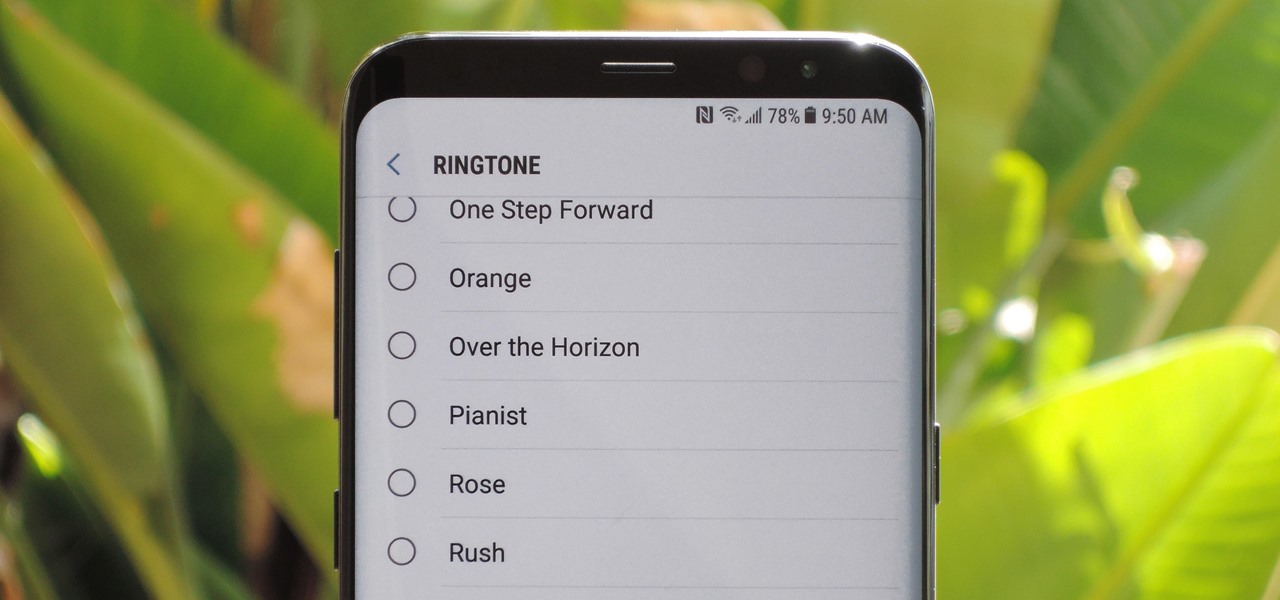
The Galaxy S9 was announced February 25, and it's jam-packed with features like AR Emojis and and a Dual Aperture camera. You really love the cut of its jib, but maybe you don't have the means to get your hands on one. Well now, you can get the Galaxy S9's notification sounds and ringtones, to help you feel like you own one.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Apple's codec for photos and videos in iOS 11, HEVC (High-Efficiency Video Coding), as well as the container, HEIF (High-Efficiency Image File Format), result in a reduction in size for pictures and movies without sacrificing quality. Seems like a win-win situation, but Windows-users can't open the .heic extension that these files use. In order to open HEIC files on a Microsoft Windows PC, you'll have to turn to third-party apps and tools. One of these tools, CopyTrans HEIC for Windows, essen...

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

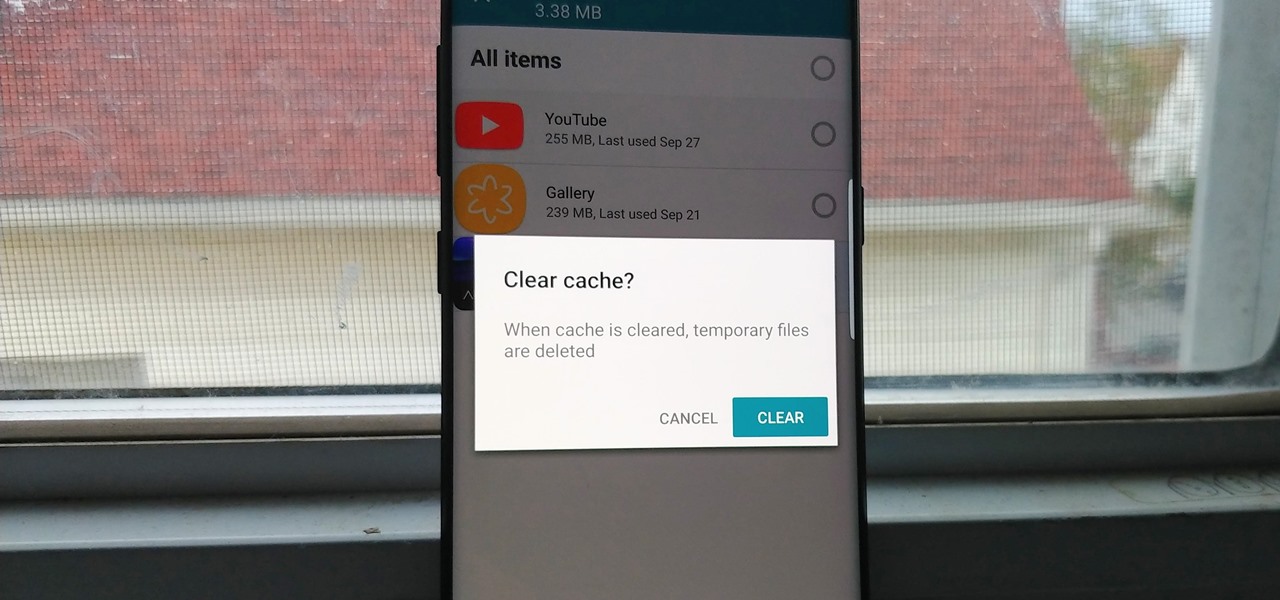
Since the release of the T-Mobile G1, the Play Store has been flooded with apps that claim to improve performance by clearing cache and storage. These apps are typically useless, rarely providing more than a temporary fix which Android undoes immediately. As Android has continued to improve cache and storage management, such apps have become more trivial. However, there are few decent ones out there.

A fairly hidden feature in iOS 10 let you turn websites and documents into PDFs, but thanks to the new Markup function in iOS 11, this process has become a lot more streamlined.

Even though the Galaxy S8 and S8+ are only just now being released to the public, the software leaks have been rolling in for a while. Everyone seems to have gone crazy for the new look Samsung is pushing out with Samsung Experience, the successor to TouchWiz. As a result, there have been quite a few applications ported over from the Galaxy S8 to older Samsung phones.

The LG V20 was released in the fourth quarter of 2016 as a flagship phone with audio capabilities far superior to that of anything else on the market—but only if you have your headphones connected. The single bottom-firing speaker, on the other hand, is just unpleasant to listen to. At first, it was believed there was a software issue with the speaker. However, it turned out to be an issue with the speaker grille impeding sound.

As the first phones to be made by Google, the new Pixel and Pixel XL have several slick customizations that you won't find on any other Android device. There's tons of functional stuff like the new Google Assistant and a much-improved camera app, but also a few aesthetic tweaks to help class up the joint.

A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

Android Nougat came with a lot of new features, including a futuristic and sleek circle animation. When this article was originally published, it was rumored that the circular design would be used as the new boot animation in Android 7.0—but as it turns out, you'll only see this screen while you're installing a firmware upgrade or working with ADB.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

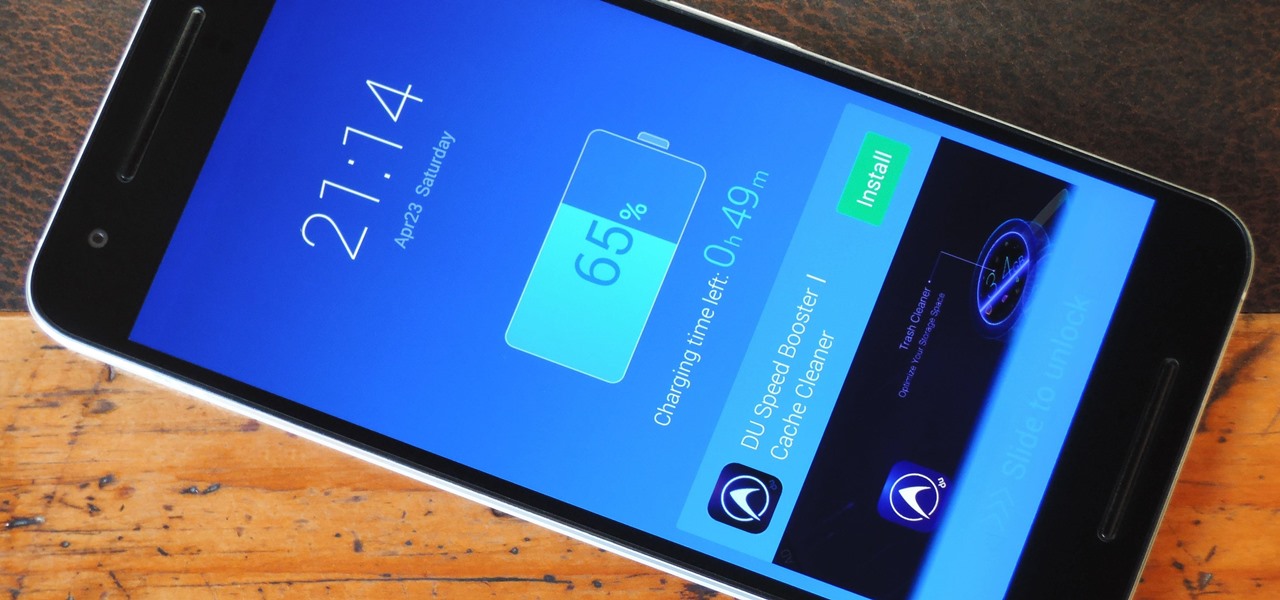
There was a somewhat recent outbreak of malware on Android, and it came from an unlikely source—the Google Play Store. Several established apps have received updates a few months ago that contained an unwanted add-on called either DU Quick Charge, DU Battery Boost, DU Boost Charge, DU Speed Charge, DU Speed Booster, or another name starting with DU.