MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.
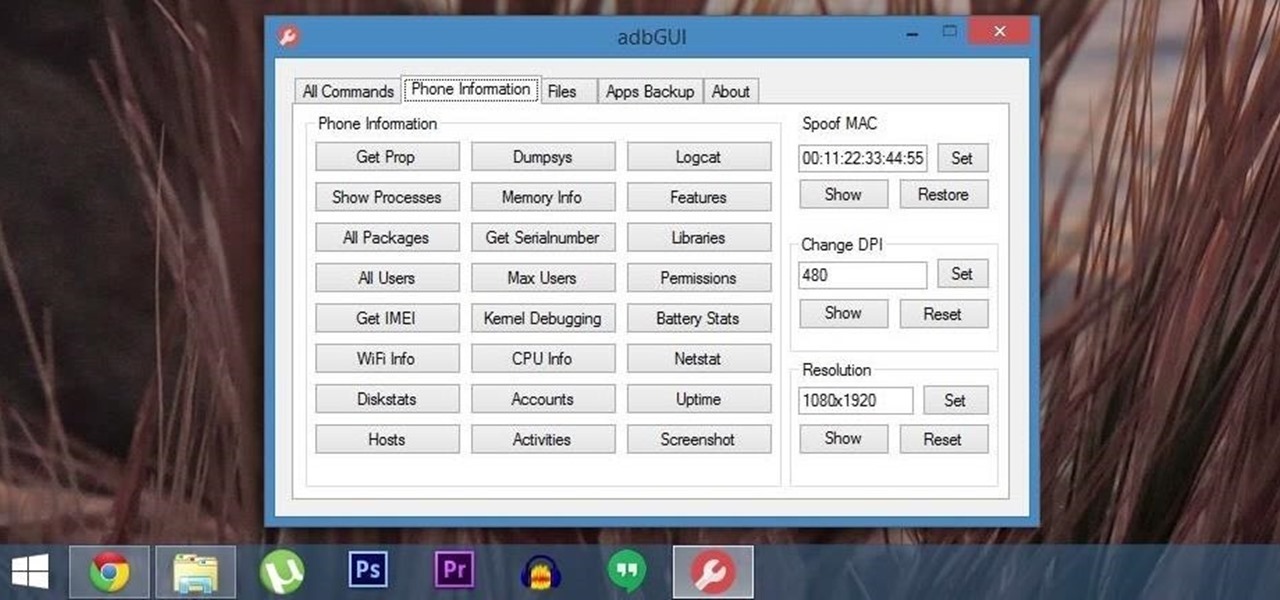
Android Debug Bridge (or ADB for short) serves as a remote terminal interface for executing shell commands on any Android device. Put simply, ADB lets you send commands from your computer to your phone or tablet, some of which would require root access if they were performed on the Android side of the connection.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.
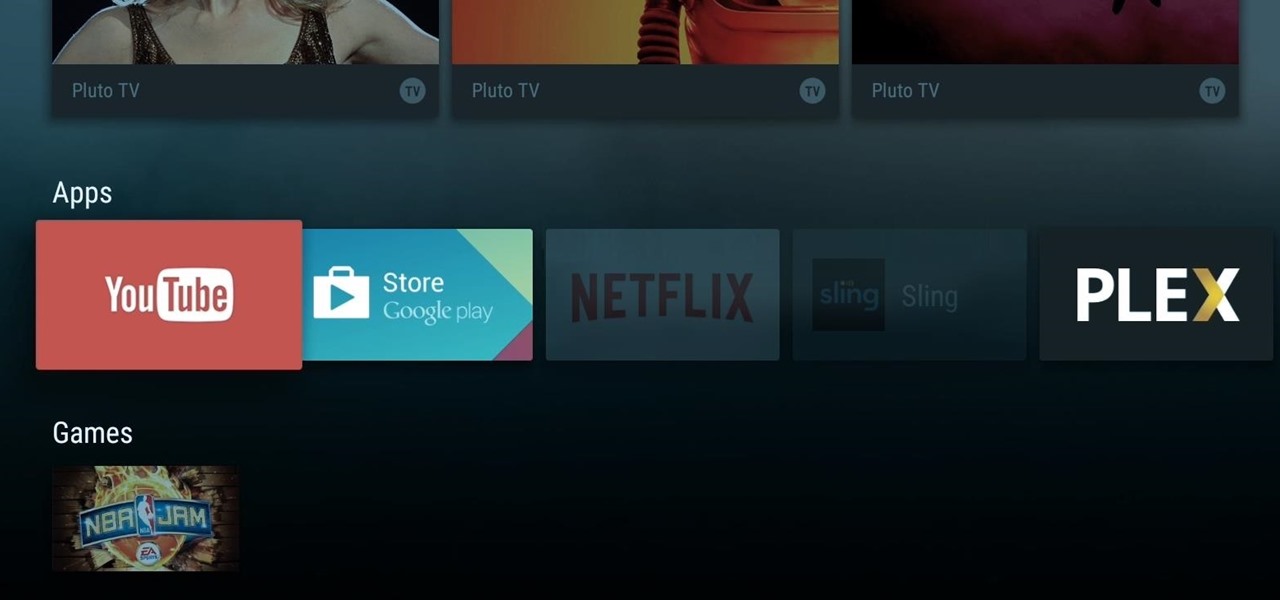
When Google announced its new Android TV platform, one of the features they advertised was a home screen that automatically reorganized your apps based on how frequently you used them. Unfortunately, this feature either didn't make the cut, or is still under development, since the home screen on the Nexus Player always remains static.

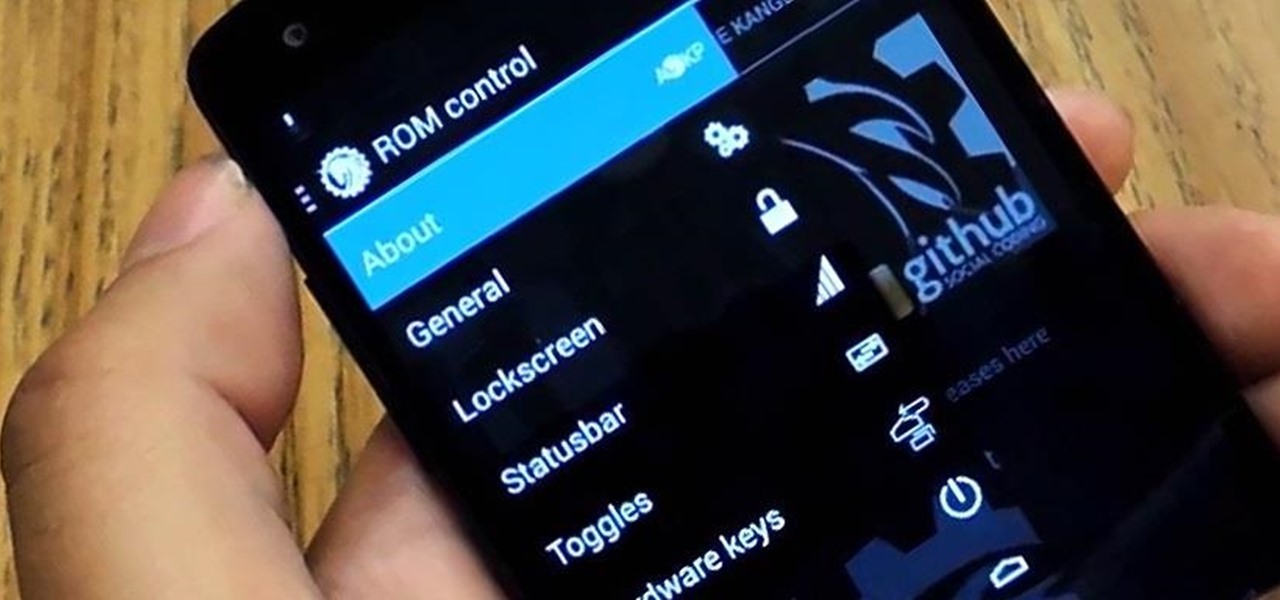
Most custom ROMs are built from the freely-available source code of AOSP, so they share a lot of common ground with stock Android. The difference, though, is the fact that Google adds many minor tweaks and finishing touches to AOSP while creating the version of Android that ultimately comes pre-installed on Nexus devices.

The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

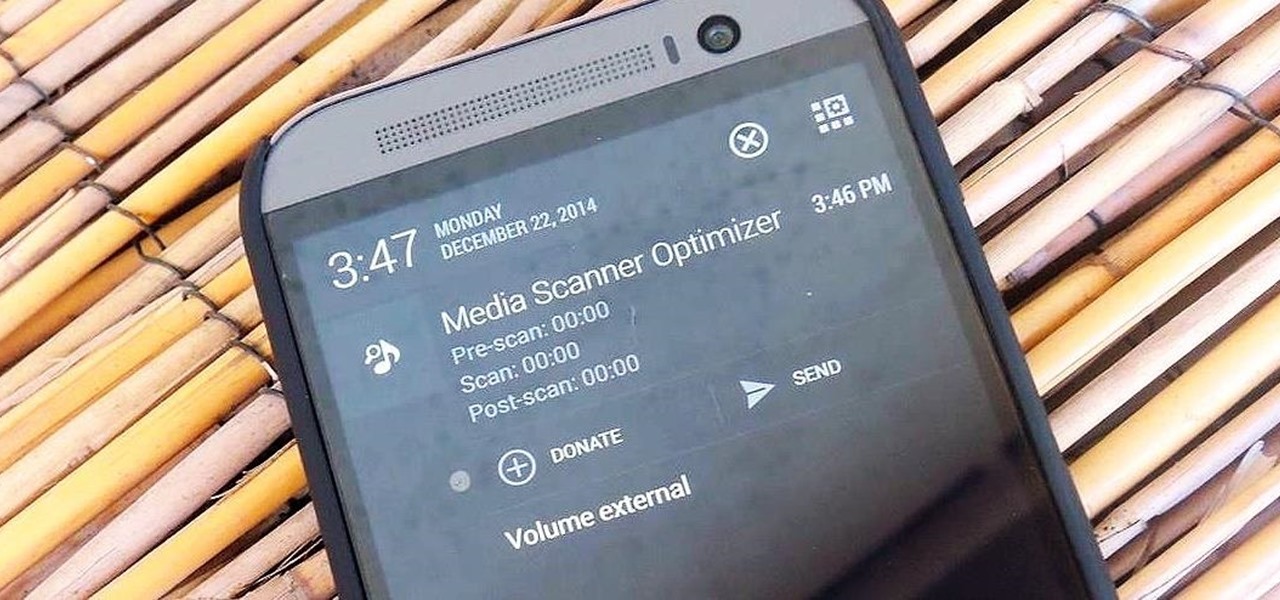
Battery life is extremely unpredictable on an Android. Finding the right ROM and kernel combo can make or break having the kind of battery that will last you all day long. Even if you do find the perfect pair, you then have to worry about apps, widgets, and other processes constantly waking your phone and draining your juice. While your media scanner isn't the biggest battery hog out there, it can definitely take a chunk out of it.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Back in March, Samsung partnered with Slacker Radio to create a streaming service called Milk Music. For those of us who don't own a Galaxy device, this news was a non-starter, as it was exclusive to Samsung's flagship line of phones and tablets.

While LG G3 users have been patiently waiting, developer the cubed and his Codefire team have been diligently working on a successful unlock method for the heavily locked-down bootloader. Now it's finally here, and the unlocking method is extremely easy to do—and it works for all G3 variants.

If you've ever noticed that the stock launcher on an Android device seems to just feel faster than any third-party home screen replacement app, this is not a placebo effect. Most manufacturers, Samsung included, force their stock launchers to reside permanently in your phone's memory, thus reducing the risk of redraws.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

With the release of the ARChon Runtime, many Android apps can now be run within the Chrome web browser. Minor changes must be made to existing Android APK files before they can be installed on Chrome, so the process isn't exactly as easy as pasting an Android app into a folder on your computer.

With recent security breaches in the news, there is no better time than the present to make sure you know exactly what's happening on your device.

Though they share the same name, the HTC One and OnePlus One have completely different sound quality. HTC had put a lot of time and effort into fine-tuning their BoomSound technology, while OnePlus is still fairly new to the game, with brand recognition being a much greater objective than awesome speakers.

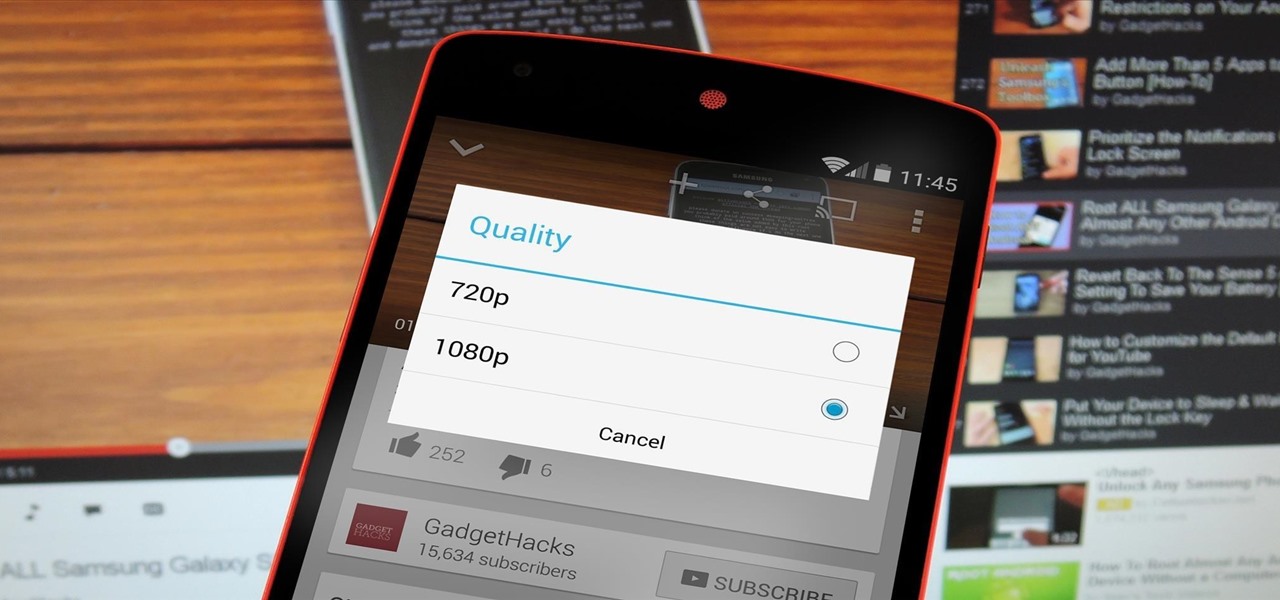
The Nexus 5 and Nexus 7 (2013 edition) boast beautiful 1080p screens that are capable of displaying images and videos in ultra-sharp high definition. But for some strange reason, the YouTube app only allows for streaming of 720p content on these devices. It's not a limitation of YouTube for Android, since other devices support 1080p playback out of the box, and some, like the LG G3, even support higher resolutions.

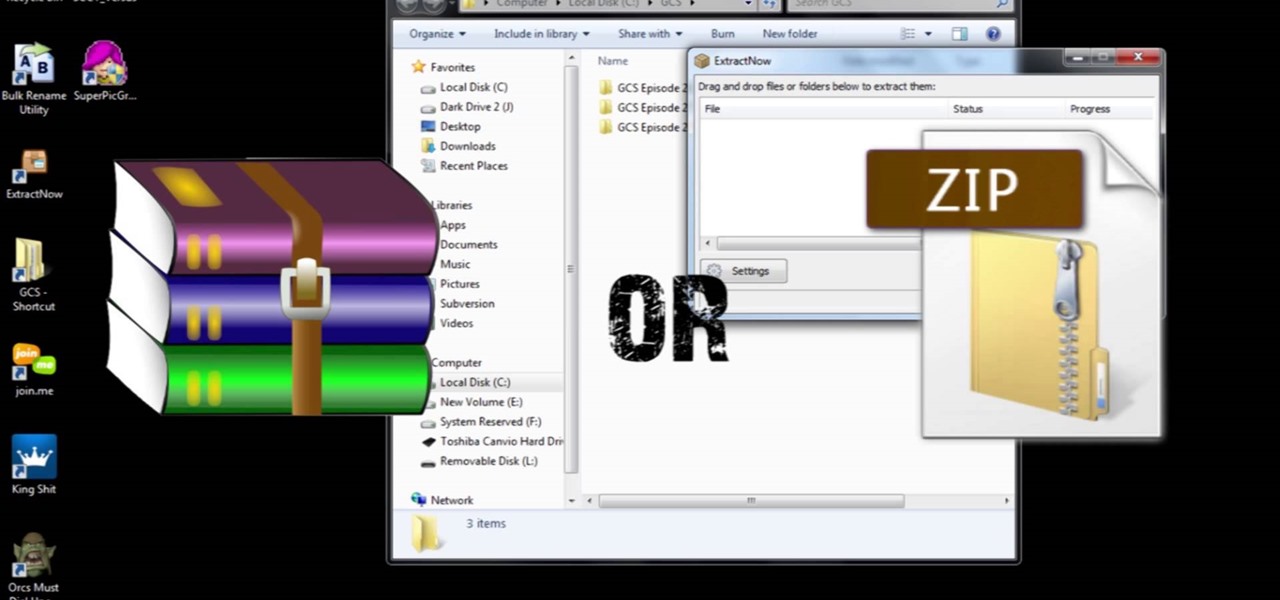
This is a video that I created for teaching you(the viewer) how to batch unrar, unzip, or extract a lot of files at a time but I do it in rap form. I know it sounds weird but I still hope you like it.

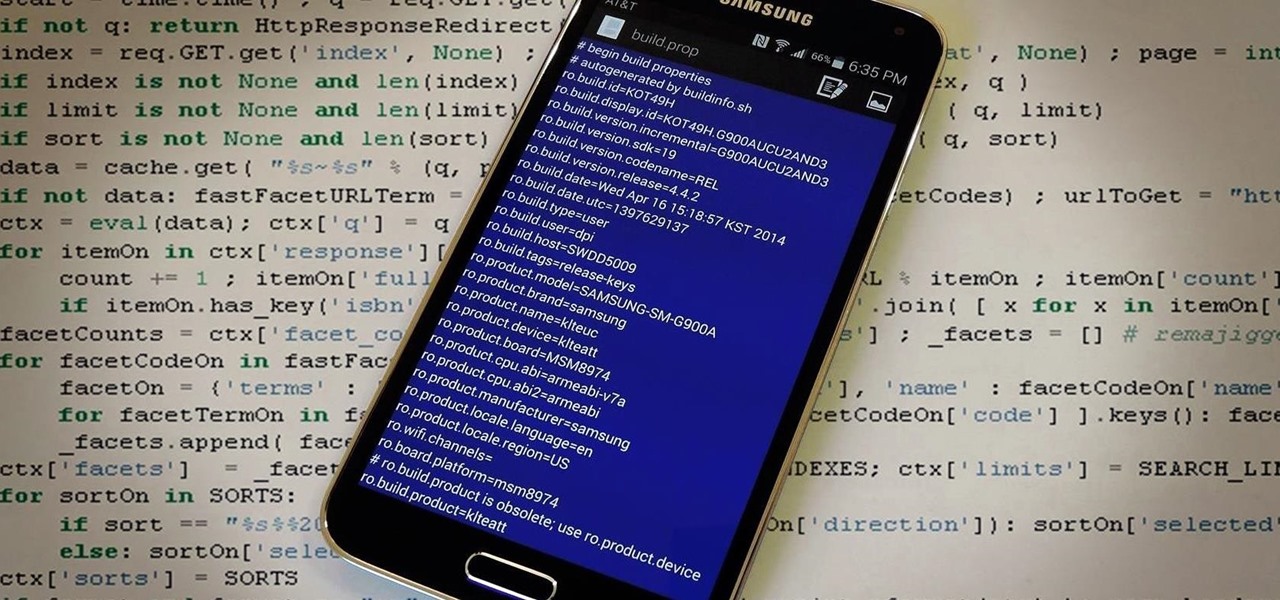
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

With so many keyboard options available for Android, there's no reason to limit ourselves to the default one, or to just the ones available in the Amazon Appstore. While the Appstore does provide alternatives, such as SwiftKey, it doesn't come close to the selection available in the Google Play Store.

Amazon released the Kindle Fire HDX back in late-2013, and if you picked one up or received one as a gift, you've probably had a good amount of time to get to know your tablet.

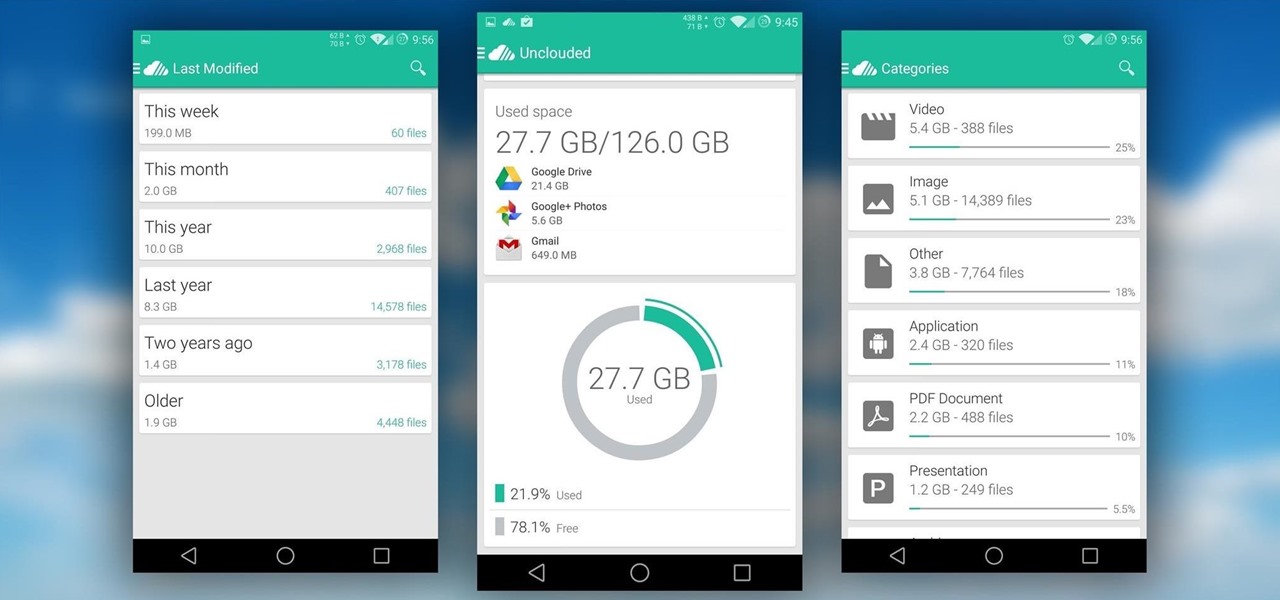
It seems like every cloud service out there is offering tons of upgrade options and free promotions to give people as much space as they need to store their files online. I personally have over 100GB of Google Drive space which is shared between multiple computers, phones, and tablets, so keeping track of everything can be a huge pain in the ass.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

Sense 6 came with a ton of new features for the HTC One, but for some reason, HTC decided to keep one of them hidden to all non-Harman Kardon editions.

Thanks to a recent back-end update to Google's Search app, every KitKat-running device can use "Okay, Google" from within any app—even the lock screen. However, the default settings for the OnePlus One's mic leave it unable to detect your voice unless you have it right up to your face. That isn't a good look for anyone, but thankfully there is an easy fix to get this working correctly.

BlackBerry was one of the first companies to put anything that resembles a modern-day smartphone on the market, but now, seeing one out in the wild is like stumbling upon a fossil. Now that they've announced the BlackBerry Passport, it seems as if this is their last-ditch effort at remaining relevant.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

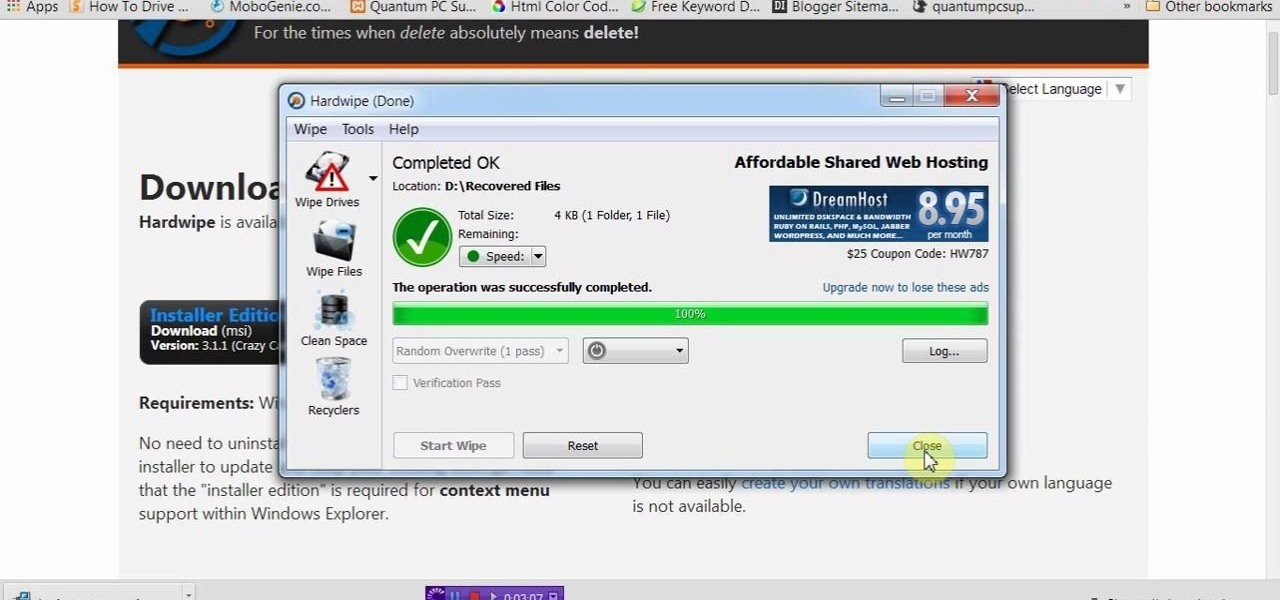
If you delete data by using Hardwipe tool, then it can't be regained by any means. The file or data will be deleted permanently. Watch the video and follow all the steps carefully. Employ the technique in your own PC.

If you're like me, you are a non-stop, sweating, never-give-up workout fiend. Okay, not really, but like a significant amount of people, I would love to live a healthier lifestyle. The Misfit Shine makes fitness a lot easier.

With apps and games getting bigger and more memory-hungry every year, storage space is at a premium. High-definition videos and photos of innumerable pixels certainly don't help the matter, either.

In this tutorial, I will show you how to make an origami backpack! Origami: (Back to School) Backpack!

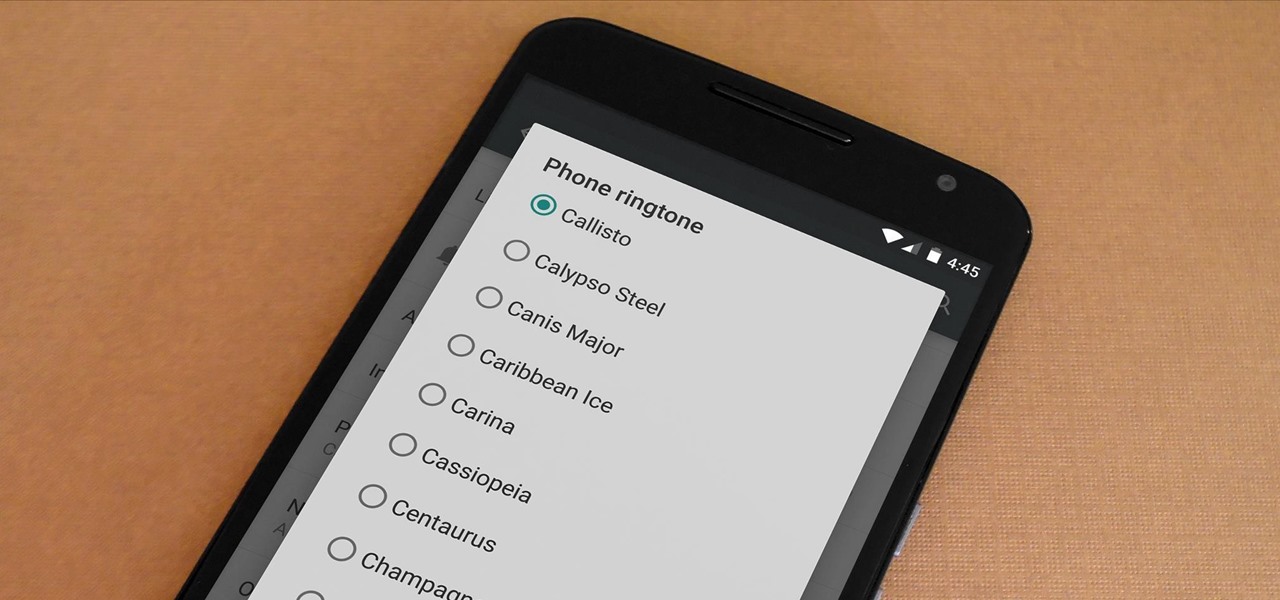
Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.

In this tutorial, I will show you how to make a beautiful origami rose. Take care of your folds at the beginning, and the rest should be fairly easy if you follow the tutorial exactly. Making careful folds, and making sure everything is properly aligned will allow you to get best results for the final product. This rule is something that should probably be kept in mind when making any origami model. Other than that, have fun!

The flexibility within Android is pretty amazing. Unlike iOS, you can make a lot of modifications with nothing more than a download from Google Play, but to really step up your softModder game, you'll need to go a little further.

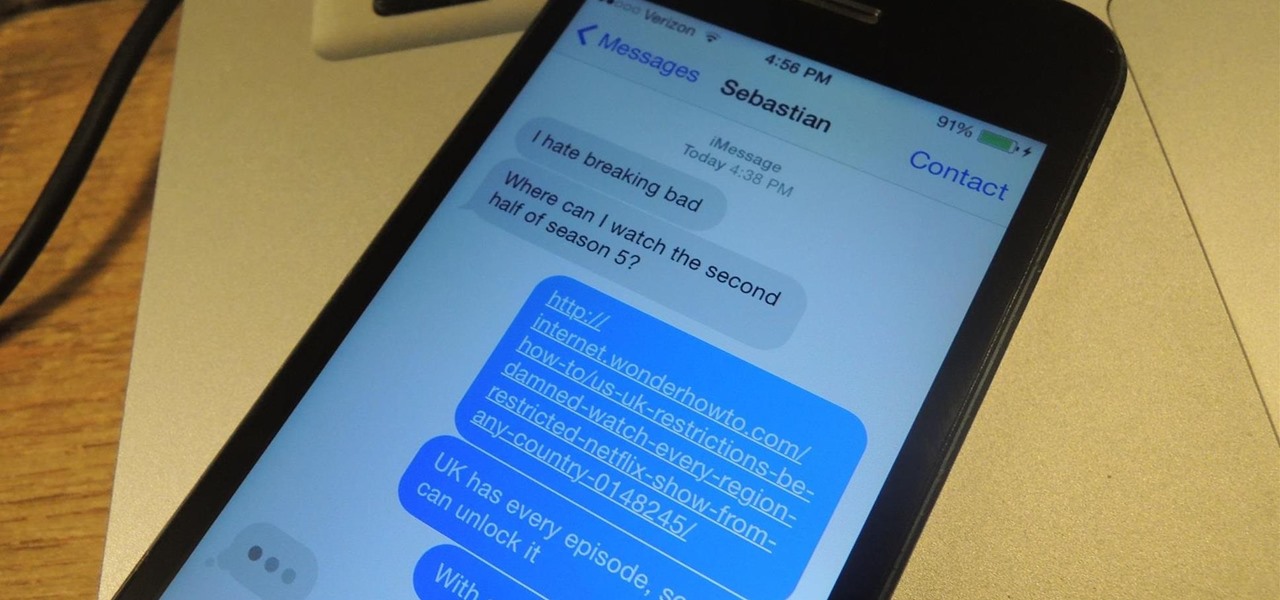
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

Just because you wanted a stable, stock Android version on your HTC One doesn't mean you have to miss out on Sense because you bought or softModded to a Google Play Edition. As long as you have the Android SDK tools and you've unlocked your bootloader, you can turn your HTC One into the Developer Edition, a Sense version free of carrier bloat.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!