Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Spotify launched an experimental feature in early-2018 called Spotify Voice, a voice assistant that lives right in the app. It lets you speak to quickly find and play your favorite songs, albums, artists, videos, and podcasts on the music streaming service. Although the feature was initially only available on iOS, it's been ported over to Android so that anyone can take advantage of it.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.
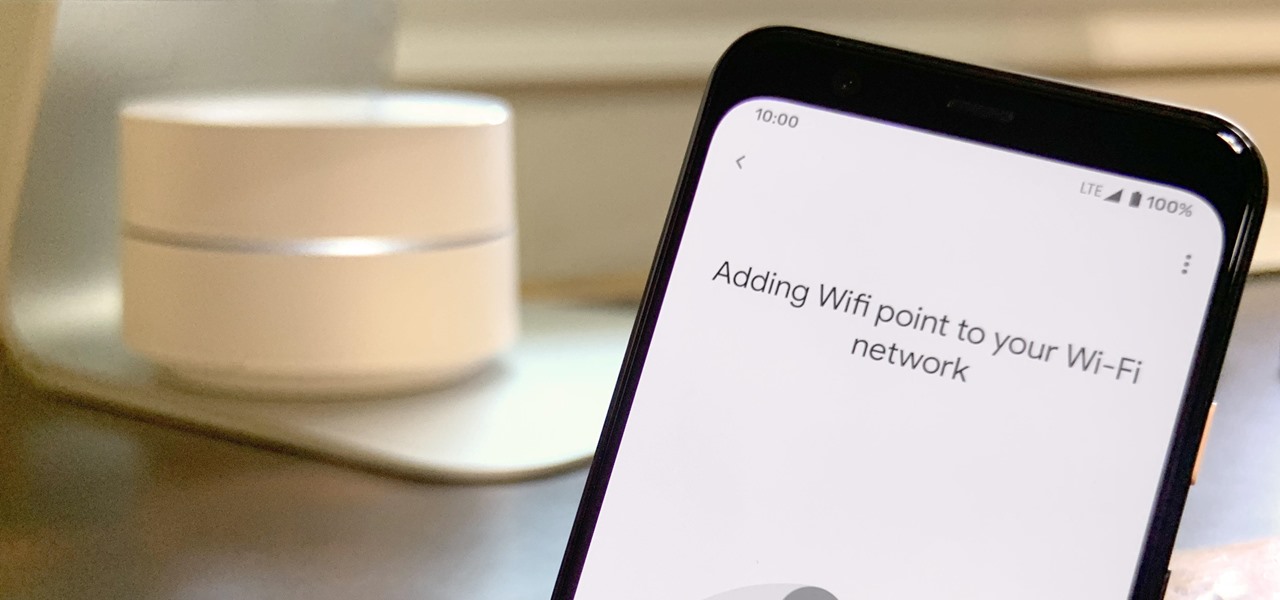
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

The biggest new feature in Android 10 is the system-wide dark mode. Both Samsung and Google phones have it, so third-party support is everywhere. The only problem is OnePlus forgot to include a way to quickly toggle dark mode on and off.

We might never truly know all of the colors behind old and classic black-and-white photos, but thanks to technology, we can get a pretty accurate colorization. Although Photoshop is a popular way to colorize these images, you can now use your iPhone, along with a nifty shortcut, to transform and give new life to vintage photos.

Whether you love Motion Sense or think it's a gimmick, one thing we can agree on is that its functionality is limited. It's currently limited to switching tracks on a playlist, snoozing alarms, silencing calls, lowering the volume of alerts, and checking notifications. But a new mod will help you do so much more with it.

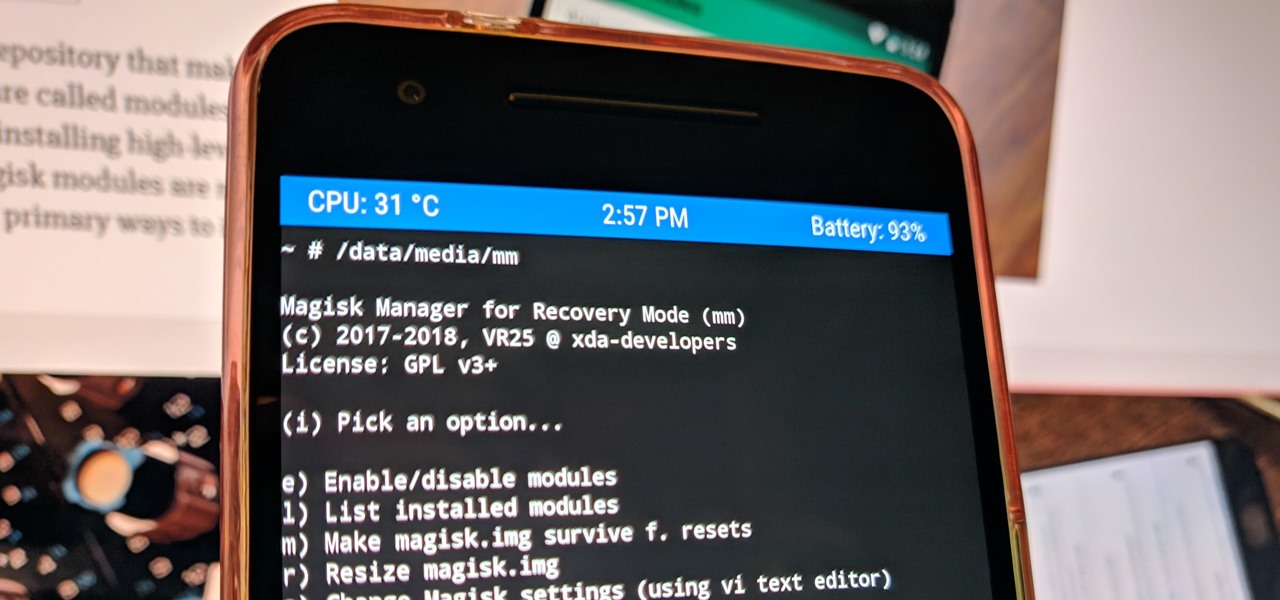
The Pixel 4 is one of the most talked-about phones of 2019, so you know there will be lots of third-party developer support. Mods are already popping up, so you'll want to get Magisk installed as soon as possible to get root access. The current method used to gain root is the quickest way yet, thanks to the recent TWRP custom recovery support for the Pixel 4.

The Pixel 4 is one of the most talked-about phones of 2019, and it has many things going for it, especially in the world of rooting and modding. Just as with previous Pixel generations, unlocking the bootloader is the gateway to realizing your device's true potential. It can make way for such things as TWRP, Magisk, custom ROMs, and many other device-specific mods just the same.

Your iPhone has seen a lot of new features in a very short amount of time. For starters, iOS 13 introduced over 200 of them, including, among many others, system-wide Dark Mode. Before you even had a chance to breathe, however, iOS 13.1 came along and dumped an additional 22 features in your lap. For us beta testers, now its time to explore new features all over again with the first public beta for iOS 13.2.

Beta testing Apple's mobile OS has never been more interesting. After eight seeds of iOS 13.0, Apple unexpectedly released the first beta for iOS 13.1, a whopping 23 days before iOS 13.0 made its public debut. Since 13.1, however, we haven't had any betas to sink our teeth into. That is, until now, as Apple just released the first developer beta for iOS 13.2 today, Wednesday, Oct. 2.

Every year, Apple releases a new version of iOS. Each iteration promises new features to make using your iPhone that much better. This year, iOS 13 introduces over 200 new features and changes, including system-wide Dark Mode for the first time on iPhone. That said, you might want to pump the brakes before dashing to download and install the new update right away.

Apple Maps has had a rocky history since its introduction, which included limited features and questionable data, earning it a reputation as a lesser alternative to Google Maps. Since then, Apple has worked to close the gap, and in iOS 13, they're introducing Collections, which allow you to create groups of locations on your iPhone that you can then quickly access and share with others.

Apple's Reminders app has never been particularly sexy or appealing, but that changes in iOS 13. Although the productivity tool has always been useful for quick to-dos, it now has an overhauled user interface with several new features, including grouping lists together for improved organization.

Apart from the flashlight, camera, and apps you access via notifications, widgets, location-based alerts, and the Control Center, there's no way to open other apps straight from the lock screen that you use frequently. If you have a jailbroken device, however, you can remedy this and add the home screen's Dock to the lock screen to get into your go-to apps even quicker.

In this era of smartphones, we all know very well how easily we can get addicted to our devices. Spending hours each day doing the endless scroll through Facebook and other social media sites just because we feel like we'll miss something if we don't. Both Google and Apple are aware of this and are trying to help control smartphone addition in their own way for Android and iOS.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

Apple has several ways for you to communicate in the Messages app aside from texting — and that includes audio messages. You can send a voice recording via iMessage by long-pressing the microphone icon just right of the input field and speaking. However, by default, these audio messages self-destruct after two minutes, which isn't good if you want them archived.

Samsung has stepped up its camera game with the Galaxy S10's dual- and triple-lens systems. But as impressive as the hardware is, the native Samsung Camera app still isn't as good with image processing and video stabilization as the Google Camera app for Pixel phones. Thankfully, you can get the best of both worlds.

When it comes to customizing Android, there's nothing quite like Magisk. You can potentially combine dozens of modules to create a one of a kind user experience tailored to you, but not all modules will work well together. You might run into a bootloop by accident once in a while, which could cause some issues on its own.

When someone sends you a funny video, image, tweet, what have you, often the first thing you want to do is share it with someone else. Instead of copying the link and jumping over to another chat to do so, WhatsApp makes it easy to share content right from the thread you received it in, via the forward feature.

For some reason, the Slack app on Android and iOS is a little less customizable than Slack on other platforms, so you can't adjust the sidebar theme to different colors directly inside the app. But that doesn't mean you can't customize the look of your mobile app at all. It's just a little less convenient.

While Apple has moved on from Touch ID to Face ID in newer iPhone models, there are still plenty of iPhones with fingerprint sensors — in fact, Apple's second-generation iPhone SE is the first new Touch ID iPhone in three years. With Touch ID, you can register up to five fingerprints, but it doesn't stop there. Using a little-known trick, you can sneak another five fingerprints in there for a total of ten.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Each year, Apple seems to design its devices to be more difficult for owners to repair themselves. So when an iPhone breaks, a trip to the Genius Bar or an Apple Authorized Service Provider is most likely necessary. But if you have an iPhone X that needs a new battery, a leaked video just spilled the beans on how to replace the battery precisely as Apple would.

Extra hardware buttons have become a trend with smartphones lately. Often, these are unmodifiable buttons designed to launch a voice assistant. That isn't the case with the BlackBerry KEY2. Making a return from the KEYone is the Convenience Key, which also received an upgrade.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

One of the latest trends in Instgram is breaking up larger videos into more digestible clips to use in stories. Stories max out at 15 seconds, making it a pain to show anything meaningful in that short time frame. Fortunately, you can virtually extend the duration of your Stories on both your iPhone and Android phone.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

If you're anything like me, when you first find a good song, album, or playlist on Spotify, your initial reaction may be to share it with your family and friends. While there are the usual share methods available in Spotify that are available in other streaming music services such as Apple Music and Google Play Music, Spotify goes one step further with QR-like codes users can easily scan.

Bookmarks and favorites are handy options for saving interesting websites you come across while surfing the web on Android but are far from ideal when it comes to instant access. Thankfully, Google Chrome gives you the added ability to save webpages and progressive web apps directly to your home screen for added convenience.

The "Up Next" feature in Apple Music helps you control which songs you want to listen in the order that you want. However, this list can become messy fast, quickly becoming a collection of songs you never wanted to listen to in the first place. Luckily, Apple has built a way for you to clear Up Next, it's just not very obvious.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

One of the biggest improvements with the Galaxy S9 and S9+ is the redesigned camera, with the latter scoring an impressive 99 overall on DxOMark. But with an abundance of features and enhancements, tweaking the camera's settings for optimal performance can be a little confusing.

Over the past week, we've had a number of important launches take place in the Android community. Samsung is in the middle of their rollout of the Galaxy S9, with preorders in the US shipping this week. Google also rolled out the first Android P developer preview last week. While these may seem unrelated, there are actually a number of Android P features inspired by Samsung software.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

IFTTT is the king of simple automation apps. With minimal setup, you can easily add applets that companies and users create. You can also create your own applets to suit your needs. Sometimes, though, you need to trigger an action on your own. For times like these, adding a widget to your home screen is exactly what you need.

Google's launchers are some of the most polished home screen apps out there, but they lack the ability to customize. With the old Google Now Launcher, we had Xposed GEL Settings to add options for tweaking the layout, but that project was abandoned when the Pixel Launcher came out. Now, a new root mod will give us some key customization settings for Google's latest launcher.