Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

We regret to inform you the former king of third-party keyboards, Swype, has officially retired on both Android and iOS. A few weeks ago, we noticed Swype's mysterious disappearance from the iOS App Store but had hoped it was just pulled temporarily, not gone forever. Unfortunately, Swype is no more, but there's something that's ready to take its place for you on your phone.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.

Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to.

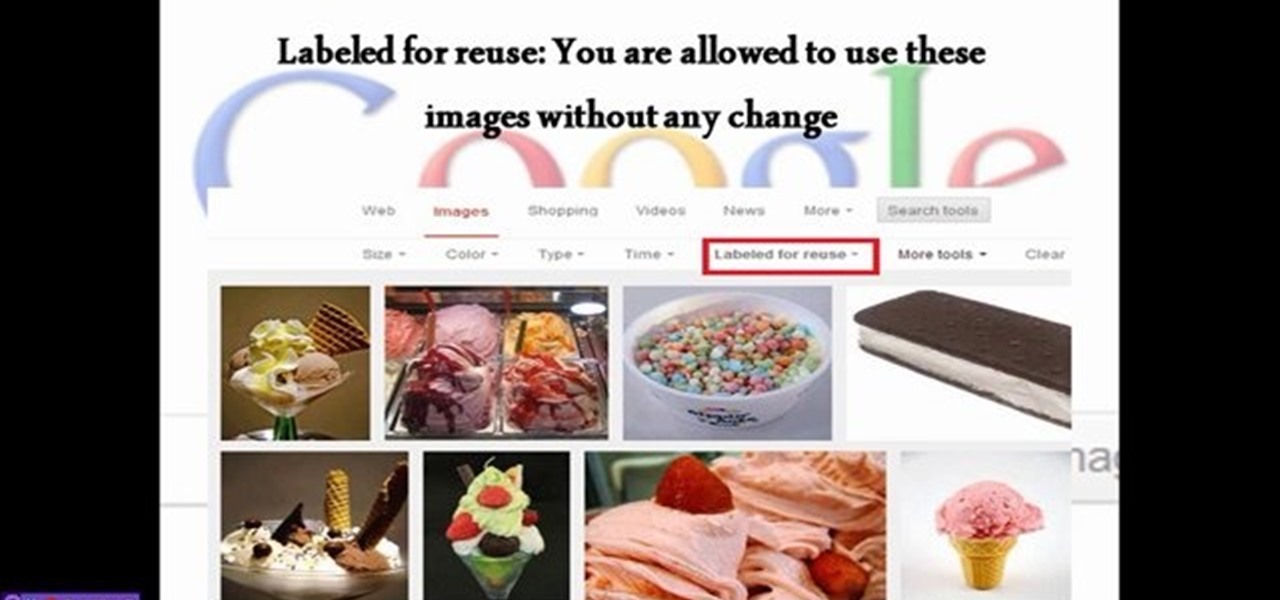
This video will show you how to isolate or distinguish images in Google according to their usage right. Google also provides you information about the commercial or noncommercial usage permission. Watch the tutorial video and select your image for reuse.

Apple's new iOS 8 has a ton of new features, and so does their revamped Safari app, only some of the features aren't quite as obvious as others. In this guide, I'll show you my 5 favorite Safari secrets in iOS 8 for your iPad, iPhone, or iPod touch.

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

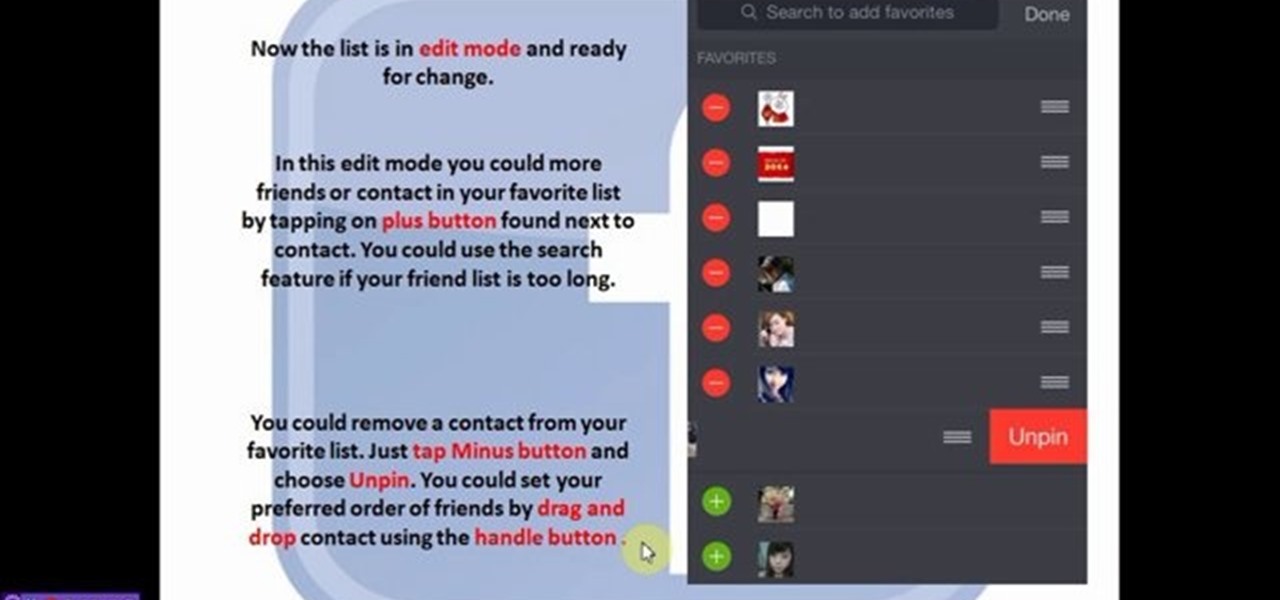
You could pin your favorite friends on top of chat list. This will save your time of searching to chat with your favorite friends. This feature is available for IOS and Android phone only. Follow the video and do it yourself.

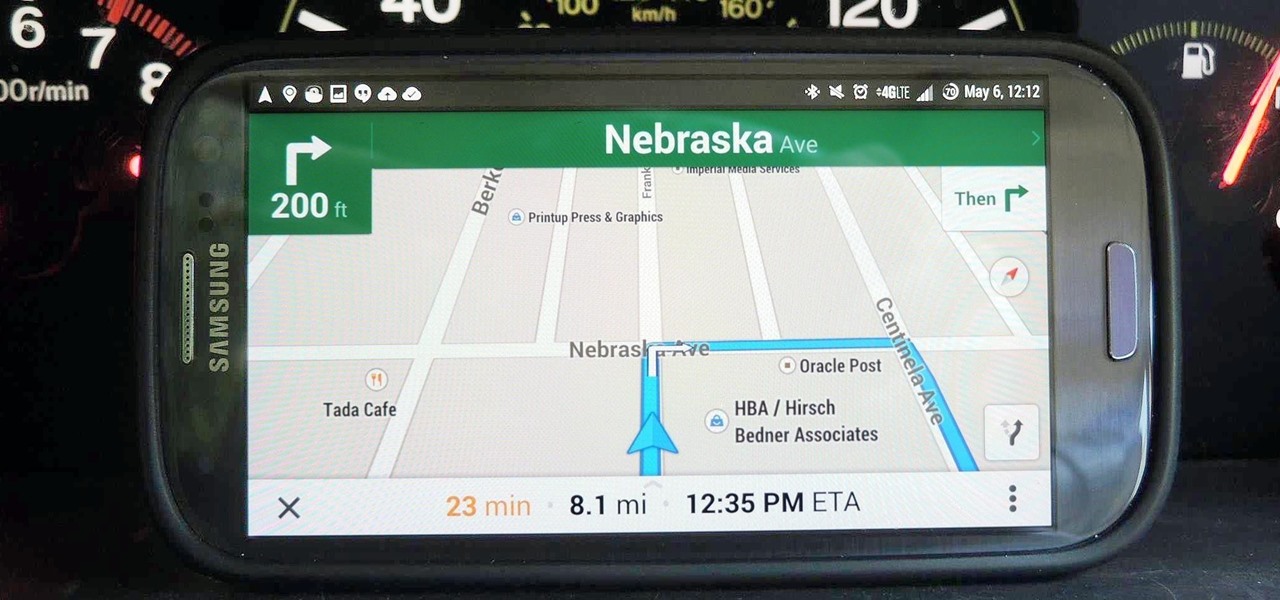
This week, Google sidestepped their usual "Update Wednesday" strategy by dropping a huge update to their Maps app for both Android and iOS. We're accustomed to seeing new features and bug fixes to their stable of apps on Wednesdays, but today's Maps update was presumably big enough to get its own release day (it's Tuesday, folks).

The new Google Now Launcher has hotword detection and one-swipe access to Google Now, but personally, it's not enough to convert me away from other launchers like Apex or Nova. Just because it's Google's official launcher for stock Android doesn't make it better than all the rest.

Here's a quick tutorial how I make some of stackable bracelets. These bracelets are super easy to make, and always in style (: Make your own stackable beaded bracelet and wear with fun your new “Arm Candy” bracelet.

Simple and colorful pattern sample. You can use this sample to make a handbag or something else that you like.

The newest Android operating system, Android 4.4 KitKat, has been unleashed with the arrival of the Nexus 5, and soon to be rolled out to other Nexus devices and Google Play Edition smartphones any day now. Only problem is, the Samsung Galaxy S3 isn't getting 4.4 for a very long time. It doesn't even have 4.3 Jelly Bean yet.

Like the buttons on your computer's mouse and keyboard, the Home key on your Samsung Galaxy S4 serves a vital function in navigating through your device. It can get pressed dozens of times a day, going through hours of use and abuse.

There's no shortage of cool customizations for my Samsung Galaxy S3, except when it comes to the launcher. Sure, there a ton of Android launchers out there, like Nova Launcher or Apex Launcher, that allow you to customize app placement, app grouping, infinite scrolling, etc. There's even Facebook Home for those who are Facebook addicts.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

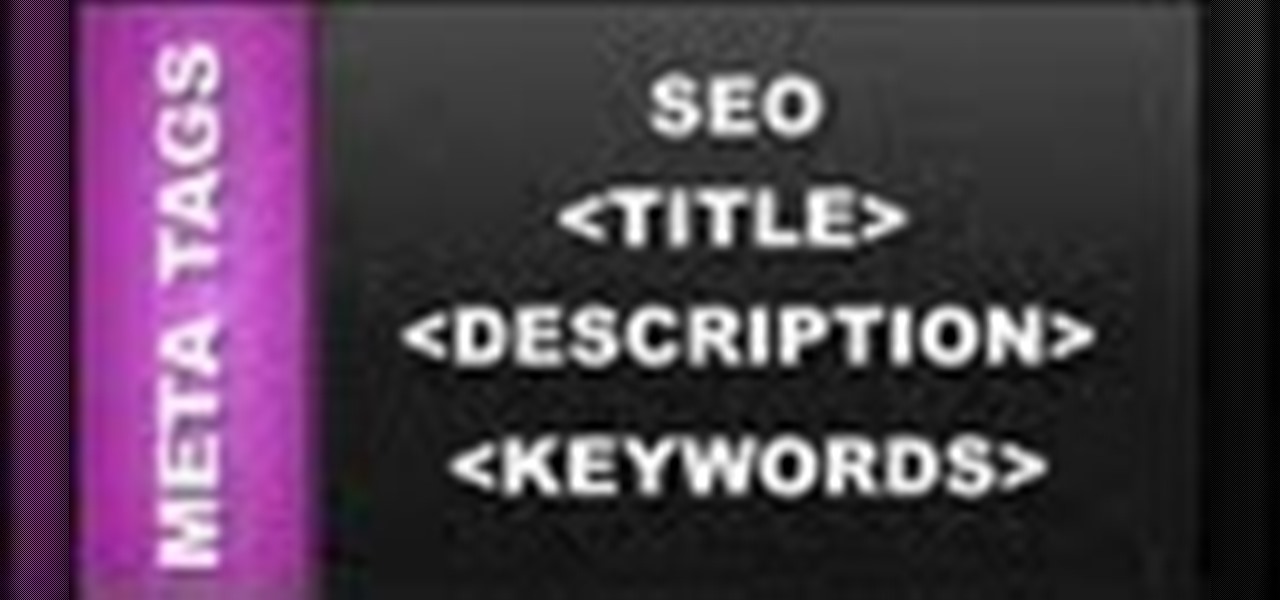
This web design tutorial will teach you how to add titles and descriptions that are relevant to your web page. Also you will learn how to add keywords for your website by using the website properties panel to add relevant keywords and phrases to your document in Xara Web Designer. The concepts taught for this web design tutorial are also referred to as Search Engine Optimization (SEO) meta tags.

First of all you have to go to Photobucket. In the search option you have to type in '3d gif''. Now click 'search'. You shall get a number of photos and you can select the image that has red color moving screen. It is better to get image this way without a virus. Now you have to right click on the image and save as '3d image animation wallpaper' and click save and then save it on your desktop. Now right click on your desktop and click on the properties. Now go to the desktop and then select ‘...

For inserting a picture, from the INSERT Tab click picture. Then the insert dialog box gets opened. From there you can locate the desired picture. Locate the picture to be inserted and double click it. We can also replace the picture selected. For replacing any one of the following can be done: Under PICTURE tools, on the FORMAT tab, in the ADJUST group, click Change picture OR right click the picture to be replaced and click CHANGE PICTURE. Locate a new picture, and double click it.

Learn how to record calls by using Skype in this video tutorial. 1. Open Skype and go to Tools.

Syncing your bluetooth earpiece to your BlackBerry device can be tricky. But pairing your bluetooth enables BlackBerry with your earpiece is actually quite easy. Best Buy has answers. The Best Buy Mobile team explains how to connect a Bluetooth earpiece to your mobile device. See how to access connections set-up on your Blackberry and also see how to wear a Bluetooth headset.

Grab your PSP and get ready to ROCK Metal Gear Solid: Peace Walker! This video walkthrough guide will take you through every mission, from the main ones to the secondary ones. Follow along and learn the tips and tricks to the gameplay so you can beat the game yourself! Peace Walker is the fifth installment in the Metal Gear series.

In this video, we learn how to use uTorrent to download files. First, go onto the uTorrent website and search for what you want to download and in what category you want. After you hit the search button, you will be presented with different things you can download. Click on one of them, then download and save it. Next, you will go to uTorrent software on your computer, and it will download what you just clicked on. When it's finished, you will be able to open your file right away. If you don'...

Use installous properly on your iPhone

At Daily Mugshots, you will be able to save your own mug shot. The first thing that you will have to do is sign up for an account. You will need a Flash Player in order to use this site. After you have your account set up, you can take a picture from your computer. You can also upload pictures that you have taken elsewhere. When you save your picture, you will have to wait until it is finished processing. When the blue bar is filled, then it will be stored in your mug show.

You don't have to browse your entire contacts to find the one you're looking for anymore. There's a shorter way to find the contact of your choice on the iPhone. It's a nice little shortcut you can use when you know exactly who you're calling. So how? With the Search function. Best Buy has answers. The Best Buy Mobile team explains how simple it is to find contacts via a shortcut on your Apple iPhone.

Shallisubscribe teaches viewers how to change the slide to unlock words on the iphone! First, you need to jailbreak your iPhone or iPod Touch! Next, open up Cydia and search for 'iFile'. Next, after downloading this open up Cydia and search for 'Slide to Unlock Killer'. You will also want to download this. Next, open up iFile and at the top left corner press that button 'var'. Scroll down until you find the folder that reads 'stash'! Next, find the 'theme' folder and click on the 'Entriegel K...

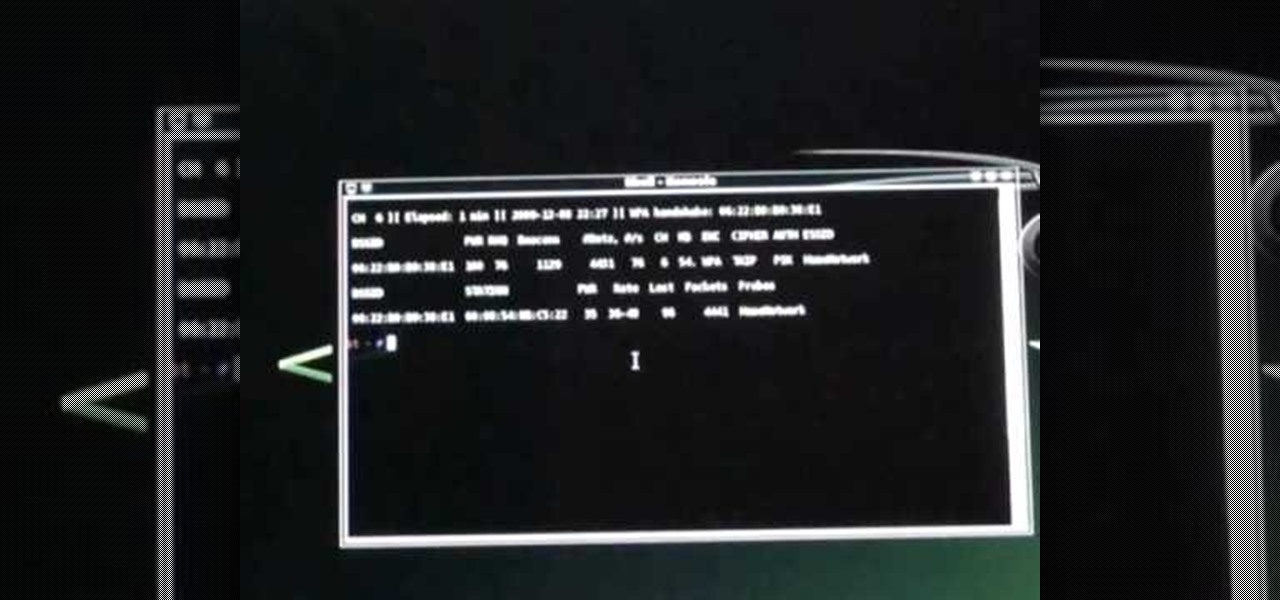
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

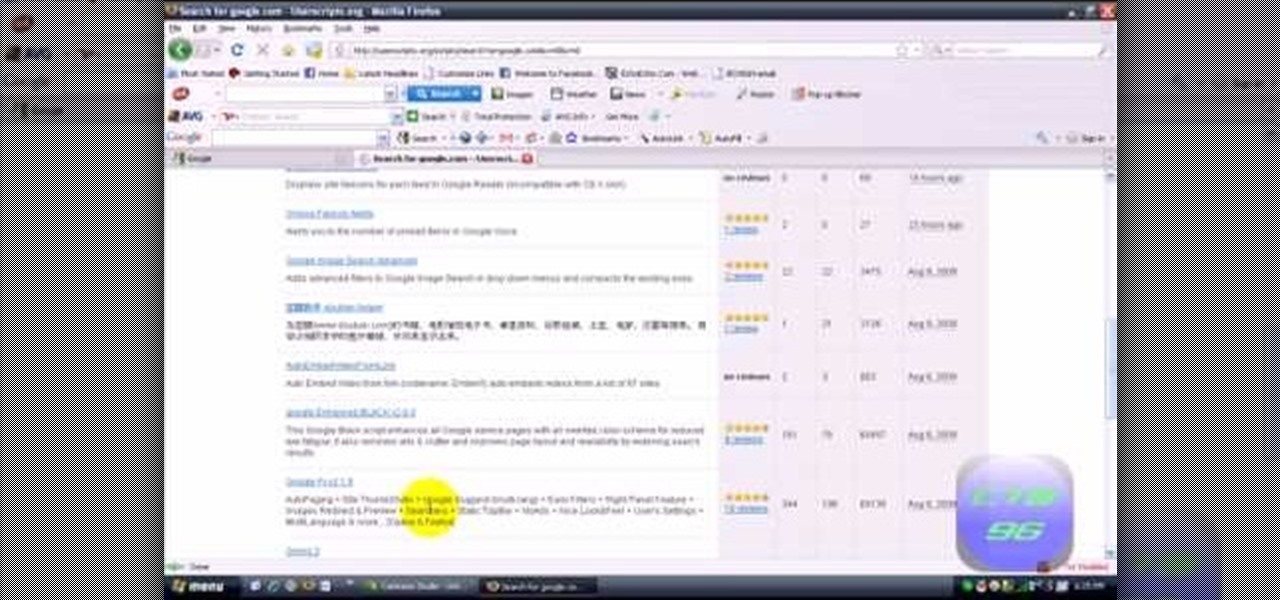
Greasemonkey is a Firefox add-on which works as a script manager for the collection of scripts available on the userscripts.org website. It can be used to manipulate the view and functionality of websites which has a user script. Greasemonkey only works in Firefox and not on any other web browser.

The video tutorial is about creating an 8 or 16 bit Nintendo Character necklace. The first step is to select or search an 8 or 16 bit game character, the person in this video tutorial recommends choosing a sprite (which is a 2D character. Doing online search will help a lot in finding a Sprite character. The second step is to gather the supplies such as Perler Beads and Peg Boards. The peg board will be used in assembling the Nintendo Character necklace. Other supplies includes ring, chain an...