
How To: Create a Basic Client-Server Connection in C Part-3
Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.


Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

We've all been there before. Preheated the oven, popped in the cake, and then became distracted by this, that, or the other... until we either smelled burning or had the smoke detector pierce our eardrums.

I was bored when I found this piece of literature: ==Phrack Inc.==
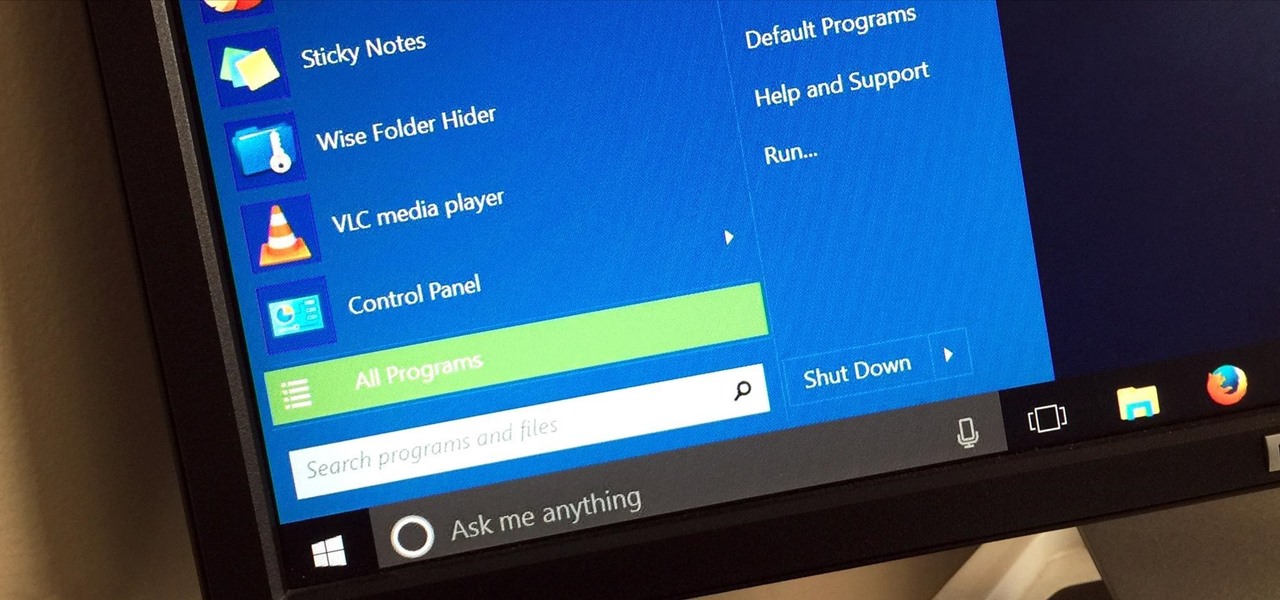
Windows 95, which introduced the Start menu to the world, recently celebrated its 20th birthday! The feature was an instant hit, becoming a core component of Windows operating systems. Well, it was removed in the mistake that was Windows 8, but you should know by now that the Start menu has been reincarnated for Windows 10.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Sriracha has quickly become one of the country's most universally loved condiments. The addictive and affordable chili sauce seemingly goes on anything, and with anything, and never seems to get old. To wit: when I studied abroad, all of our food was boring, pre-packaged Sysco shipments; for three months, I smothered every breakfast, lunch, and dinner with Sriracha. And after all of that, I still eat it almost religiously.

One of the great joys of cooking is taking the most basic of foods and preparing them in new and exciting ways. About two years ago, my wife opened my eyes to a delicious staple of Indian and Moroccan cuisine that is made in a very elementary way, the preserved lemon.

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

"Does bottled barbecue sauce even taste that bad?" a friend of mine asked. Well, truthfully, no. But it also doesn't taste that good, especially if you've had truly great barbecue or even your crazy uncle's homemade sauce at a holiday cookout.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by the week.

A very large aspect of minecraft is redstone. Infact, redstone is probably what keeps me playing minecraft today. Ever since the piston update of beta 1.7, redstone has taken minecraft to a whole new level, with the ability to manipulate the entire world around you with the flick of a switch. In this guide I'm going to quickly cover a few great redstone tips you probably did not know!

Video: . Step 1: Today We Are Going to Draw an Airplane. Let's Start with a Rectangle in Two Point Perspective. Before We Begin We Need to Figure Out Where Our Horizon Line and Vanishing Points Will Be. Sit Back and Think What Kind of Look You Are Going for.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

If you have an iPhone, iPad, iPod touch, Mac, or Apple TV, then you already have a quick way to subscribe to Apple TV+, Apple's entry into the streaming wars. Some of you might even have a free year of the service. But if you don't have any of those products or you're just looking for a smart TV or streaming device that supports Apple TV+ natively, check out these Black Friday deals.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.
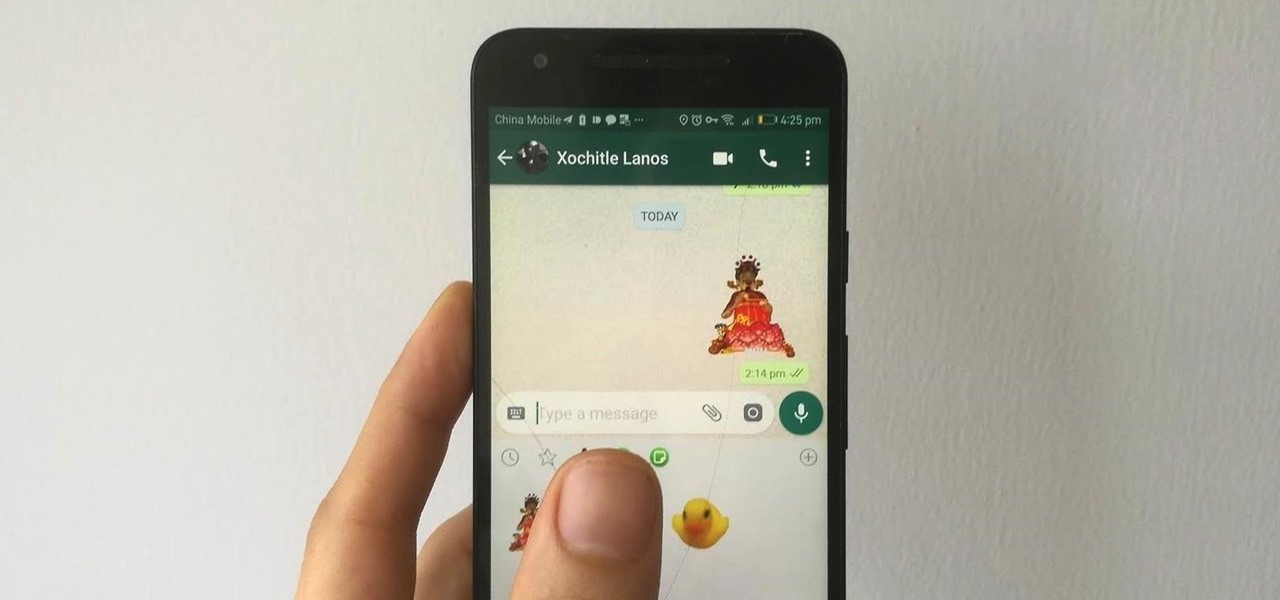
WhatsApp stickers can make your chat more fun. The stickers that come with WhatsApp are fine, but they're standard and accessible to everyone. What if you wanted to show off unique stickers that your friends haven't seen? To take things to the next level, you can create your own WhatsApp Stickers.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

In July 2017, LG announced a new smartphone lineup, the Q series. These devices focus on providing some flagship features at a more affordable cost — features such as an 18:9 1080p display. LG's goal here seems to be adding value for the more budget-conscious users, and in 2018, they've continued the series with the Q7.
Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.

Nintendo's Super NES Classic system, a pint-sized version of the iconic Super NES from the '90s, is highly anticipated in the gaming world. The retro system has already met its fair share of controversies and it's been a long journey to preorder. Finally, the Super NES Classic is officially available for preorder, but it's selling out fast.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

Are you looking for a little microbe magic? Think composting. Composting is a great way to reuse food and plant waste that you would otherwise throw into the trash, which would just end up in a landfill somewhere. During the composting cycle, microbes reduce this organic waste until it can be fed back into the soil as rich, crumbly compost. When returned to the soil, compost feeds plants and improves the nature of life underground. Sound like a great idea? It is — and it's easy.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

In the past, creative chefs and bakers have been rewarded for their daring in the kitchen with viral attention from the internet—like the rainbow bagel or cronut. These sensations weren't crafted for the sake of going viral, but ended up generating an insane amount of buzz anyway.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

With the weather warming up and the days getting longer, fruit salads are starting to appear at backyard BBQs, beach picnics, and pretty much everywhere else. Often these sweet side dishes are unremarkable, with each colorful bowl blending into the next. Luckily, there are easy ways to spice up your fruit salads so that everyone will still be talking about them next summer.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Gravy is a relatively simple dish, yet it's remarkably easy to mess up. We've all experienced the disappointment of excitedly pouring gravy onto our mashed potatoes, only to realize it's too runny, too lumpy, or too bland. And because gravy is so simple, even if you don't mess it up, it's still challenging to make it memorable and delicious.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

My daughter moved into her first apartment last year, a huge rite of passage in any young person's life. With a mother and two grandmothers who are good cooks (to say the least, in the case of the latter), it's not surprising that she turned to us for some advice about how to improve her own skills in the kitchen. Without question, the single best piece of advice we have given her is to employ mise en place each and every time she prepares a meal.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Greetings My Fellow Aspiring Hackers,