Apple pushed out iOS 12.1.3 developer beta 2 to all developers on Wednesday, Dec. 19. It's an interesting and mysterious update, as it follows the sudden release of iOS 12.1.2. That software only had one beta version before its stable release, which would explain why the iOS 12.1.3 dev beta skipped version 1 and went straight to version 2 since it's basically a continuation of the first iOS 12.1.2 beta.

Although Niantic is already an augmented reality startup unicorn thanks to the success of Pokémon GO, the company has reportedly captured yet another round of funding.

Apple just released the first version of the iOS 12.1.2 beta to developers on Monday, Dec. 10. The update arrives mere days after the Cupertino-based company seeded the official version of iOS 12.1.1 to the public, itself of which had been in beta development since Halloween.

French cosmetics giant L'Oréal isn't wasting any time putting its new subsidiary, ModiFace, to work. On Thursday, the company launched a new tool that enables a photo-realistic augmented reality simulation of nail polish shades and textures to be accurately displayed on a user's fingers in real time.

Magic Leap One owners, start your virtual engines, as automotive virtual reality developer RelayCars has published an app to Magic Leap World that lets users customize and test drive a 2019 Kia Stinger.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

Election Day is like the Super Bowl for network and cable TV news, so ABC News is breaking out the big guns with a new augmented reality experience to win over eyeballs of viewers.

In the waning days of October, at the Innovation Tokyo 2018 conference, attendees got their hands on some of the new augmented reality experiences that Niantic is working on through its Real World Platform.

Our national month-long celebration of all things creepy and crawly comes to a climax on Wednesday with Halloween and will end with Día de Muertos on Friday, so now is the ideal time for the The New York Times to publish a mildly chilling augmented reality story for children.

While these days it is better known for the cross-platform gaming sensation Fortnite, Epic Games also makes Unreal Engine, one of the top development environments for 3D content and, in turn, augmented reality and virtual reality experiences.

On Tuesday, Blue Vision Labs, one of three Google-backed companies working on AR Cloud platforms, announced its acquisition by ride-sharing company Lyft.

On Thursday, yet another piece of the Magic Leap puzzle fell into place at Twilio's Signal developer and customer conference in San Francisco.

Electronic Arts is inviting players of The Sims Freeplay and their friends to visit the homes of their Sims in augmented reality with a new AR mode that supports multiplayer and persistent content using ARKit 2.0.

Adding another arrow to its quiver of augmented reality acquisitions, Apple has reportedly acquired Spektral, a computer vision company with technology for real-time compositing (otherwise know as the "green screen" technique in broadcast TV and film).

Leading augmented reality headset makers Microsoft and Magic Leap are among the companies now vying for a military contract for battlefield heads-up displays.

The first mobile augmented reality app out of the gate with support for Magic Leap One Creator Edition is Thyng, who is planning to release the headset version of the app later this year.

We often take for granted how reliable our iPhones are — so much so that many of us get panic-stricken at the very rare event where our device freezes up as a result of a buggy app or an update gone awry. Because of this, knowing the basics of troubleshooting is a handy skill to have, and this still applies to the iPhone XS, XS Max, and iPhone XR. Force-restarting is usually the first tactic to employ.

Following closely behind the developer beta, Apple released the first public beta for iOS 12.1 to testers Thursday, Sept. 20. The update comes only two days after developers received their first look at 12.1. Both the developer and public betas surprisingly mark the return of Group FaceTime, allowing beta testers to chat with up to 31 other friends.

Facing mixed reviews for the Magic Leap One, Magic Leap has already returned to the lab to improve on the device's successor.

In an SEC filing published on Monday, Snap, the company behind Snapchat, disclosed that Imran Khan, its chief strategy officer and a member of the NR30, is leaving the company to "pursue other opportunities."

Royal Dutch Airlines (KLM) is making it easier for its passengers to travel by employing an incredibly practical new augmented reality feature included an update to its iOS app.

After parting ways with Papa John's, the National Football League has drafted Pizza Hut as its official pizza purveyor, and the company has hit the field with an augmented reality game to entertain hungry football fans.

A new app for iPhones and iPads gives developers a sandbox for testing their AR experiences and sharing them with the world.

You want whales? Ok, you'll get whales! That seems to be the unspoken message from Magic Leap via its latest update in the form of several new experiments posted inside its Helio app.

The fortunes of ARKit and ARCore are still in the hands of developers, who have been increasing the number of mobile augmented reality apps on the market, but perhaps not as fast as companies like Apple might have expected. But one new product is looking to literally kickstart mobile AR gaming by introducing a few key components that harness the traditional board game model.

Online shopping giant Shopify literally cannot wait for ARKit 2.0 to arrive via iOS 12 this fall to implement its latest augmented reality feature.

The roster of handsets supporting Google's augmented reality toolkit now includes 46 Android models as well as support for ARKit-compatible iPhones and iPads.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Less than two months after launching its augmented reality platform for casual gaming and shared experiences, Snapchat is ready to make Snappables available to advertisers.

New York-based startup CTRL-Labs has closed a $28 million Series A round of funding from Google parent Alphabet's GV and Amazon's Alexa Fund, among others, for its next-generation neural interface technology for AR/VR and robotics.

Department store chain Target is the latest retailer to offer an augmented reality cosmetics app for customers to virtually try on lipstick.

During Snap Inc.'s quarterly earnings report, released on Tuesday, the company disclosed that it snagged a revenue total of $230.8 million for the first quarter of 2018, an increase of 54% compared to last year, largely fueled by its augmented reality offerings and other advertising products.

With the heavily anticipated installment of the God of War game series arriving on April 20, PlayStation has taken the opportunity to make its first foray into mobile augmented reality with a companion app.

Fast-casual burger restaurant Bareburger expects to soon replace all of its paper menus with 3D models of its burgers and other items rendered in augmented reality, but for now, the company is preparing some rather interesting limited AR interactions.

Just weeks after being acquired by comedian turned producer Byron Allen for $300 million, The Weather Channel has tapped augmented reality studio The Future Group to integrate immersive augmented reality experiences into its broadcast content.

Update: Google's new Pixel models have been released! Check out our full guides on the Pixel 3 and Pixel 3 XL to see all the details, but we'll leave the rumor roundup intact below for posterity.

It's no secret that iOS 11 is one buggy piece of software. Remarkably, even after three major updates, we're still seeing issues with our iPhones. This time, the glitches have come for 3D Touch on iPhones running the new iOS 11.3 update.

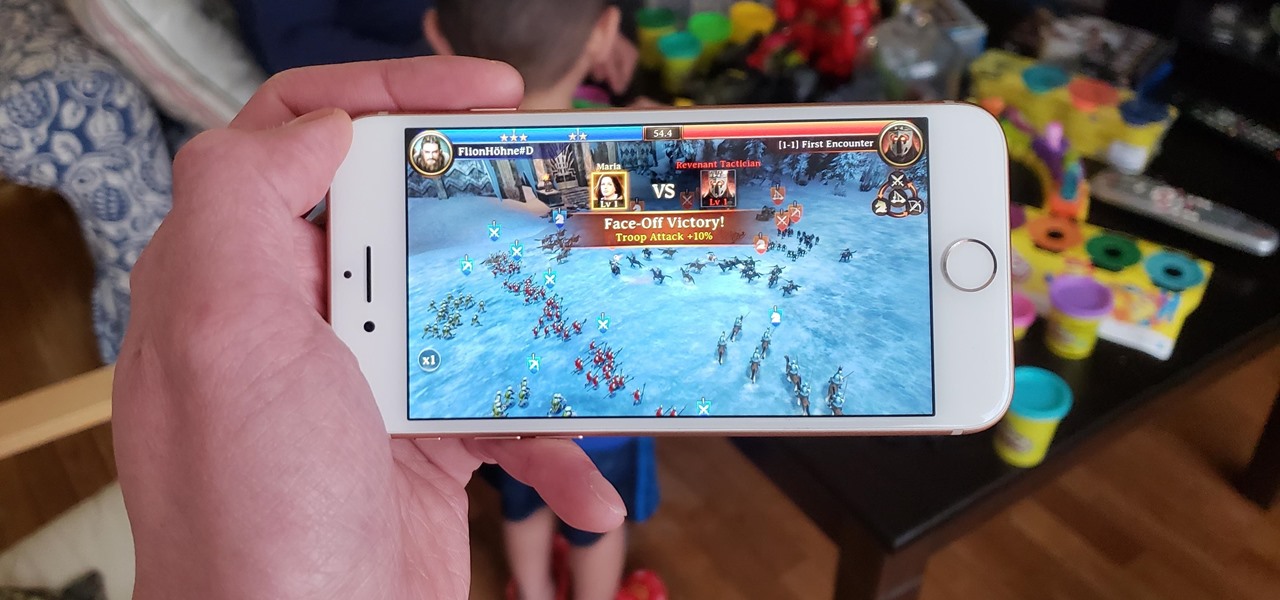
Netmarble has released a new MMORTS game called Firstborn: Kingdom Come to go up against competing games like Lords Mobile. Unfortunately, the game seems to be stuck in development as a soft launch in select countries, limiting its exposure to gamers worldwide. But don't let this hiccup deter you — we've found a simple workaround to play the game on your iPhone right now.