Hash browns are a breakfast staple and for good reason: they're simple, salty, and crispy, and so delicious that you can easily down several servings of them in one sitting. Basically, they're the French fries of breakfast.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)

Eggs bring life to almost any dish. Toast with avocado? Put an egg on it. The same old salad you eat for lunch everyday? Put an egg on it. Stir fry leftovers? Put an egg on it.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

It's no secret that cauliflower is good for you—but not nearly enough people know that the best part about cauliflower is its insane versatility. Because its cooked flavor is so mild, it can be incorporated into a crazy amount of dishes and preparations.

When a craving for crunchy tacos hits, it's undeniable. Don't Miss:

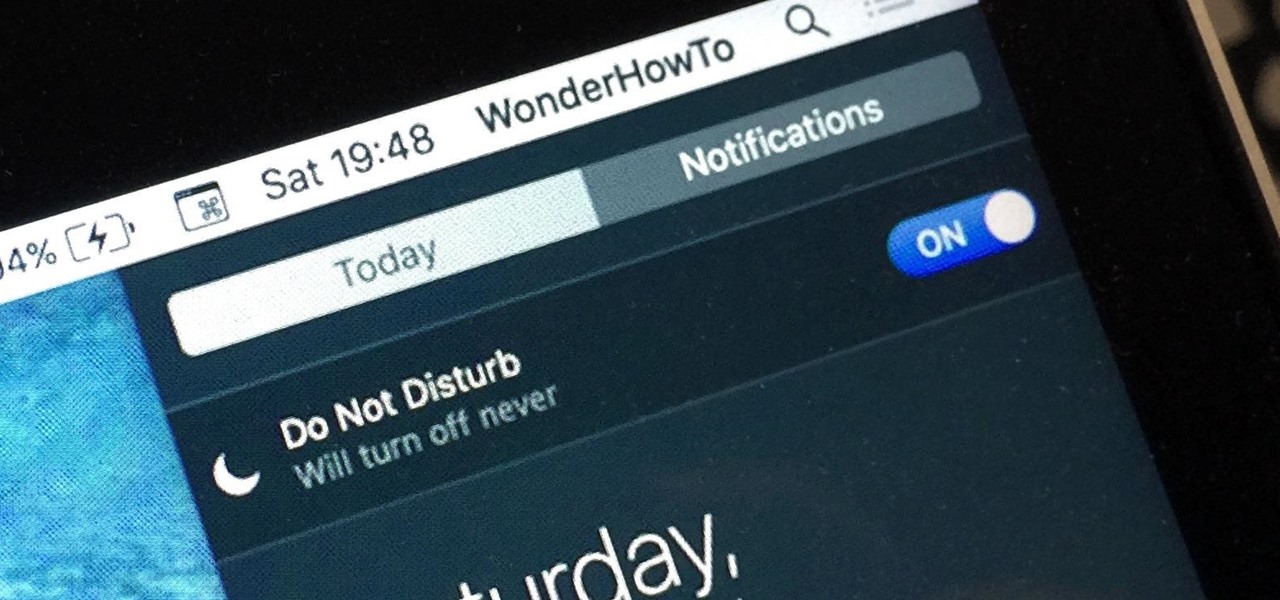
When Apple wanted to bring their Notification Center to Mac OS X, I loved the idea. But after using it since its integration in Mountain Lion, it's been more annoying and distracting than anything. More and more apps incorporate notifications, so I'm constantly getting sound alerts and banners in the top right corner that I don't want.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Amazon has completely changed the way we purchase household items, to the point where many of us haven't visited a big box, brick-and-mortar store like Walmart or Best Buy in years. And when you think about it, all of this success comes down to two main factors—convenience and price.

Dried spices and herbs seem to be immortal; a peek in your parents or grandparents' cupboards will likely unveil cinnamon, basil, and oregano older than you.

Mobile data is expensive. The internet connection that comes with your cell phone plan is generally limited to a certain amount of gigabytes that can be downloaded before your monthly cap kicks in, at which point you run the risk of incurring costly overage fees.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

The headline above may have some spice addicts shaking their heads, but, believe it or not, there are people out there who either don't like or can't handle a ton of spice.

Rich, creamy chocolate cups stuffed with smooth, salty-sweet peanut butter in a bite-sized package—yep, Reese's Peanut Butter Cups are an amazing fix for your sweet tooth at best, and a guilty pleasure at worst. It's easy enough to buy them on a whim at the local grocery store, but it's even easier than you might think to make them right at home.

Whenever I go to Jamba Juice, I usually gravitate towards either the Matcha Green Tea or Caribbean Passion smoothies. But when I learned about their secret menu a few years ago, I felt like a little kid all over again—especially with flavors like Pink Gummy Bear and Orange Dream Machine.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

Frozen fruit is always in season at your local grocery store, so you don't have to wait until the farmers market starts again to enjoy delicious baked fruit desserts. Peach pie, blueberry muffins, raspberry scones... all of these delicious baked goods can be just as delectable when using frozen fruit, too.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Obviously this is just a teaser, and who knows how soon we'll see something like this in real life, but just go ahead and watch the video first before you continue reading.

Samsung trademarked the name Gear 360 a few weeks ago, and today it has been confirmed that the Gear 360 is a spherical virtual reality camera that will accompany the much-anticipated Galaxy S7.

There's a good chance that your iOS device has become unresponsive at least once. It's usually at this point that you start thinking your device can no longer pass muster. You could upgrade to a newer model, but that's not always feasible, and often times, unnecessary.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

When roast chicken is concerned, perfection is hard to attain. The reason for this is surprisingly simple: the light meat and the dark meat should be cooked to different temperatures. Ideally, chicken legs should be cooked to at least 170°F, while breasts should be cooked to 150°F. Naturally, this poses a conundrum: how can you cook two parts of the chicken to two different temperatures, without taking the bird apart?

Hello, in this episode of In the Kitchen with Matt, we will continue with the Star Wars theme, last episode we made Star Wars Death Star Peanut Butter Cups, this episode we are making Star Wars Death Star Popsicles. So we are really getting great value out of our Death Star molds, because of the versatility they provide. These popsicles are super easy to make, if I can make them, you can make them! If you have any comments put them down below, and I will get back to you.

I was fortunate enough to be visiting one of my college classmates in Columbus, GA last spring and saw two large bags of onions in his kitchen... but not like the ones you get at the grocery store. Two standing 50 lb. bags!

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

If you're careless and tend to leave your knives lying around or in the sink, chances are you've struggled with rusty blades.

When you're young, utensils tend to be optional—and eating with your hands is optimal. One of the best examples of finger food for kids that has pervaded today's nostalgia-driven culture is tater tots.

Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment.

Any other person can make plain pancakes... but only the most awesome of cooks can make stuffed pancakes. Luckily, this isn't a tough technique—in fact, it's so easy that you'll find yourself getting bored of the run-of-the-mill pancakes and dreaming of all the things you can stuff pancakes with, instead.

Lemons are often displayed as a bright and beautiful pop of color in many home kitchen displays. They lend a lovely scent to the air and an aesthetic sense of freshness to any setting. Therefore, it would be easy to assume that lemons are best left at room temperature.

Few things are as frustrating as grabbing food from the fridge just to discover that your leftovers have gone bad. When it comes to cheese, you may have taken every last precaution to keep it as fresh as possible—sealed plastic containers, saran wrap, parchment paper—but to no avail.

Living on a budget often means compromising what you want for what you need—or at least, for what's affordable. But that doesn't necessarily mean you have to compromise on flavor, especially if you know the right tips and tricks to make something spectacular out of the ordinary.

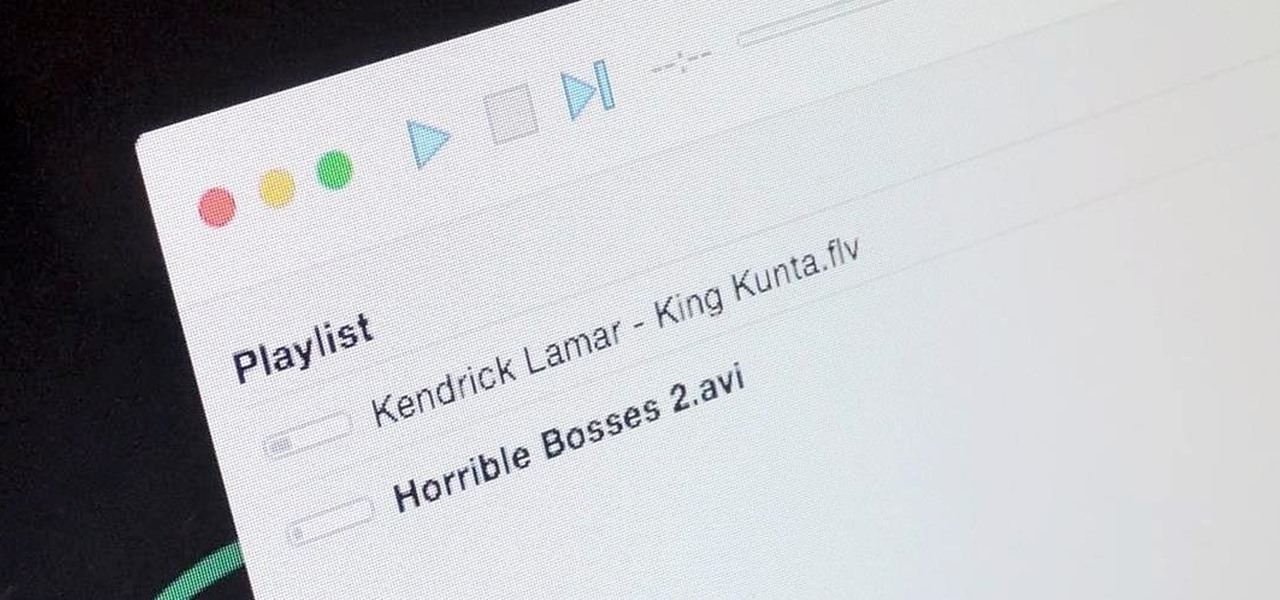
It's a breeze to send videos and music from your phone straight to your TV with an Apple TV or Chromecast, but these devices don't support all file types. While MP4 videos and MP3 music files are the norm these days, I still have a ton of AVI and FLV files that I'd like to watch on a big screen.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

Sadness won over the worried world with her downtrodden, mopey attitude in Inside Out, the widely popular animated film from Pixar and Disney. She's relatable, helping us to connect with all of our bouts of tears, sour attitudes, and blue feelings—and this Halloween, you can embody Sadness with this easy DIY makeup tutorial via Rotoscopers.

Tofu has been a staple food in Asia for over 2,000 years, but due to the health craze of recent years, it's enjoyed a surge of popularity in the Western world. Derived from the milk of soy beans and typically coagulated by calcium or magnesium salts, tofu can be found in consistencies ranging from extra-soft or silken to extra-firm. Based on which firmness you prefer, there are a myriad of ways to prepare your tofu for consumption.

After my hard drive crashed recently, I lost everything. Old college essays, half-written stories, short films, and most importantly, all of the photos that I had saved from the past five years... all gone.

There are a few key ingredients that you always need on hand when baking cookies and other desserts, but when you run out, you run out. You either have to stop what you're doing and go to the grocery store, find a good substitute, or scrap the project entirely. Chances are, you'll never accept defeat, and why go to the store if there's a good substitute on hand?

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.