All modern entrepreneurs know that your business is as strong as its SEO. Whether you want to Rank #1 on Google to increase your personal branding, traffic to your online storefront, or to add the skills to your resume, you can now get a Complete SEO Training course for just $14.99, in the Gadget Hacks Shop, 92% off the regular cost of $199.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.
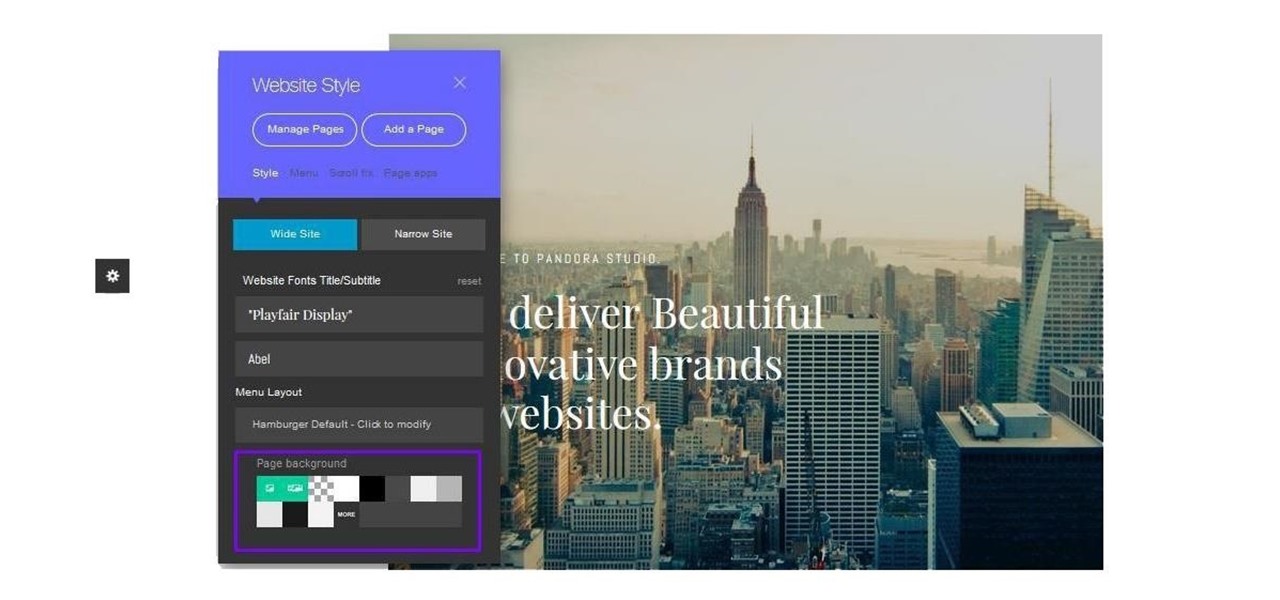
Cultivating a strong online presence can have a huge impact on your employment prospects or help you get that dream store up and running in no time. Whether you're looking for work or building a brand, being able to create and maintain a professional website is essential in the modern workforce.

While there are many advantages to working from home, properly managing your time can be a real issue. Working remotely requires a particular skill set, including an ability to focus, self-motivate, and communicate from a distance. Thankfully, all of these skills are teachable.

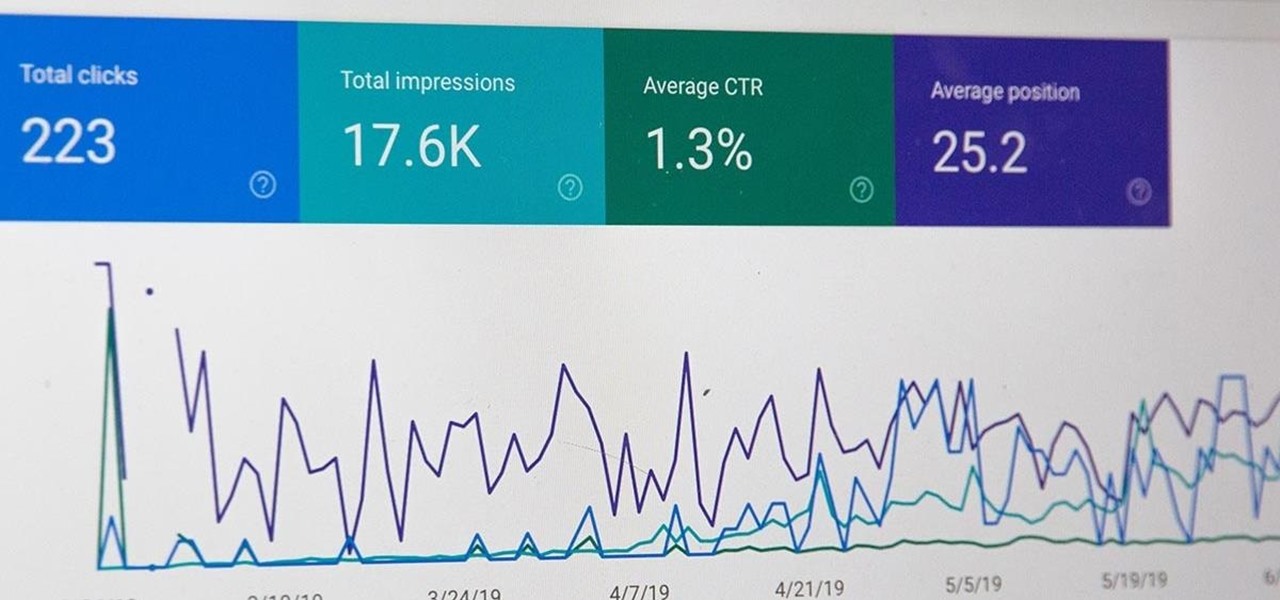
Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

Data analytics is one of the hottest fields around. With so much data at our fingertips, top companies are seeking experts to put all of this information to real-world use.

If you're considering purchasing Apple's new 2020 iPhone SE, which brings many modern components into the compact body of an iPhone 8, you should know what its dust and water resistance rating means. Just how dirty and wet can the iPhone SE get without breaking any functionality?

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

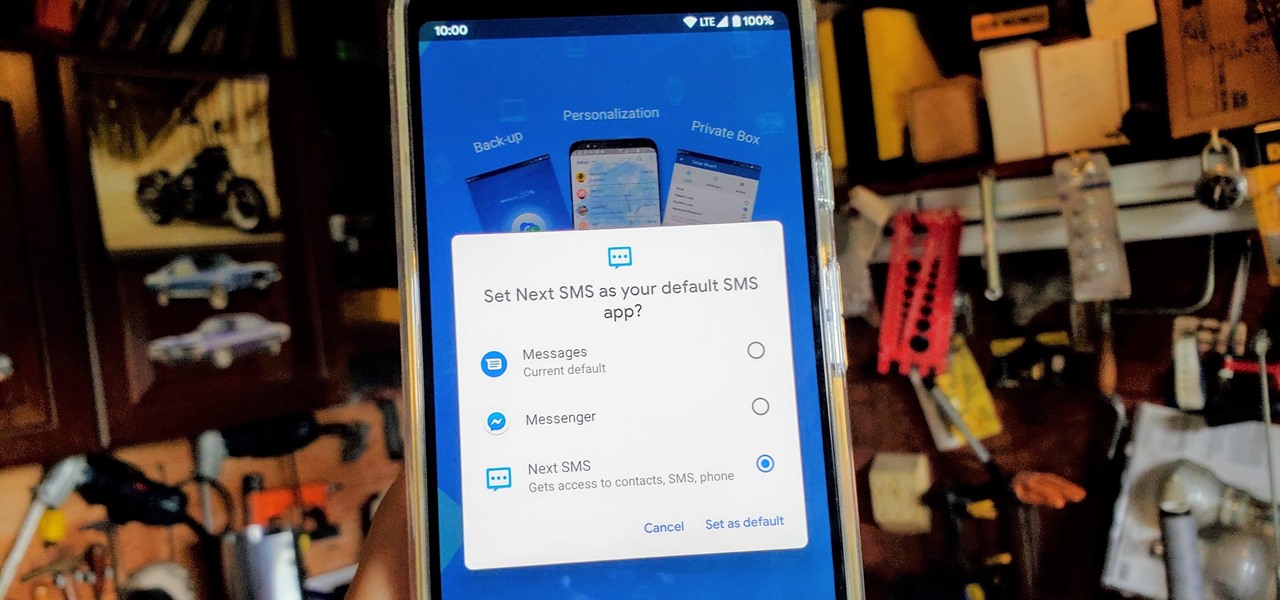
One of the best things about Android is being able to control everything you want, from your wallpaper down to the default apps you use for every action. Changing the default SMS app from the one that came with your device can drastically alter your messaging experience. Many SMS apps have loads of themes to pick from while also offering other features you can't find anywhere else.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

Developers and enterprise customers chomping at the bit to get their hands on HoloLens 2 may not have to wait much longer, as Microsoft passed one of the remaining hurdles needed to release their new tech into the wild.

Augmented reality gaming startup Tilt Five is ready to reinvent old school Dungeons & Dragons-style games for the modern age with its augmented reality headset and tabletop game system.

When it comes to augmented reality (AR) on Android, you might be wondering how you can get those cool new games and apps on your unsupported phone. Google has an officially supported device list for its ARCore platform, which usually consists of the more modern devices. You won't find very many older devices on the list for a reason, but that doesn't mean your "old" phone can't use ARCore still.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

They say home is where the heart is. So, the opportunity to view the inner sanctum of Magic Leap is like gaining access to what makes the company tick, just as the fruits of its labor make it into select AT&T stores.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs?

If you use the internet regularly, it's nearly impossible to avoid memes. They are the epitome of internet culture, demonstrating how jokes can spread and change like wildfire. While there are many different types, the most common ones you'll come across are images and GIFs with humorous text accompanying them, and we've found the best iOS apps to help you create your own.

Even with all the success HMD had with reviving the Nokia brand in 2017, it seems their second year is shaping up to be even better. Nokia has been steadily releasing sequels to last year's lineup, most with the new minimal bezel design language. The Nokia 7.1 is just their latest creation.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Earlier this year, Nokia released the Nokia 8 Sirrocco overseas. The new device served as an upgrade to the 2017 model with a minor specs bump and a more modern design. However, HMD isn't done with the 8 series. A rumored Pro version is coming later this year that brings innovations the iconic brand is known for.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

Android users have had access to live wallpapers since the Eclair days, but some newer apps have made this feature even more useful. Now, you have the ability to use GIFs as your wallpaper, and through the marvels of modern technology, you can even set a video as your home screen and lock screen background.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?

With their first attempt at the mobile market, Razer introduced a device that looks at the smartphone differently. Instead of focusing on minimal bezels or an amazing camera, Razer decided to make a phone for gamers. So how could Razer target the growing mobile gaming market, which is projected to generate $40.6 billion in global revenue in 2017? It starts with the IGZO LCD Display.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

The large, dome-shaped LiDARs that have become a fixture on driverless car prototypes are expensive and notably ugly. And yet, these unsightly devices should remain planted on driverless cars, even when they become available in commercial fleet services across the country in a couple of years.

For as long as 14,000 years, the First Nations people of the Heitsuk Nation have made their home along the Central Coast of the Canadian province of British Columbia. Among the territory's inlets, islands, rivers, and valleys lie a clay deposit on the north side of Kisameet Bay, near King Island. For as long as most can remember, the tribe has used the clay as medicine. Now science says microbes that live in that clay may have important antibacterial properties.

Unfortunately, the very places we go to receive health care put us at risk for becoming infected with superbugs, bacteria exposed to so many antibiotics that they have become immune to their effects. Clostridium difficile (C. diff) is one such bacteria. It causes inflammation of the colon and rampant diarrhea that can have life-threatening consequences. Part of its virulence lies in the tough spores formed by the bacteria. They are responsible for starting infections in the colon and for spre...

A week into my internship, I experienced pretty serious back pain and slight difficulty breathing. I scheduled a doctor's appointment to make sure nothing was wrong, and I got a surprising diagnosis: bad posture.

Everything from disposed of drugs to hormones and disease-causing bacteria — anything that is rinsed or flushed down the drain — can contaminate wastewater.