Microsoft's first venture into the tablet market, the Surface RT, combines many of the capabilities of a normal Windows 8 laptop into a super compact tablet, whose super-thin touch cover and kickstand can transform it into a functional mini-laptop, small and light enough to go anywhere you want. But like most tablets, the Surface comes with a rather limited amount of storage space. The tablet comes in either 32 GB or 64 GB, but we all know that's not the actual amount of storage space you can...

I chose to make this a Steampunk iPad case, but you can change the details and make it look as modern as you'd like. As I said earlier, Steampunks probably shouldn't buy iPhones or iPads, but if you're going to get one, you may as well make it look cool, right? The iPad pictured below was borrowed from a friend of mine, though I should add that this design will easily work with tablet computers of any variety, Apple, Android, or otherwise.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Most modern Chinese words contain more than one syllable and therefore require multiple characters to write out. However, a person knowing the meanings of individual characters can often infer the general meaning of a word. In this video series, our expert will teach you how to write and pronounce the Chinese symbols for body parts.

After years of being a PC technician and Windows System administrator, I had the blind hatred for Apple that I thought I was suppose to have. I swore that I'd never even touch an iPod, let alone buy an Apple product. But I found a new career that drug me out of the Windows server/PC tech room dungeon, and into the bright modern office of a web development firm. Then it happened. After a couple weeks with all this Apple stuff around me, my love for gadgets and (closet) Apple curiosity got the ...

I first heard the term molecular gastronomy while watching an episode of Bravo's Top Chef a few seasons back. Intrigued by the concept, I sought to find out more about this modern, deconstructed type of cookery. If you happen to be around foodies and the topic of molecular gastronomy comes up (which very likely will at some point) you'll want to have a few points to contribute and maybe even give them a run for their money.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Dungeon Defenders is the most exciting craft game on the Fall 2011 release schedule. I got a chance to play it at PAX in August and interviewed developers Trendy Entertainment last month. After more than a year of publishing difficulty and delay, the game finally came out on PSN, XBLA and Steam. I put about 20 hours into the XBLA version over the past weekend, beating all the campaign maps and racking up a huge pile of in-game money. It is not a perfect game. But it is a huge, challenging, an...

This week's 6-part series on Making Art on Your iOS Device comes to a close today with our last segment: a collection of useful apps for touring museums, galleries and street art. The apps below cover some of the world's greatest art meccas, so read on if you're planning an upcoming trip, if you live in one of the destinations listed below, or if you simply want to see what a faraway museum has to offer—from the comfort of your couch.

The moment many of the crypto savvy insiders in augmented reality and VR have been waiting for is here: we're finally getting our first big auction of NFT art that exists purely as a hologram.

Modern life is almost completely digital ... almost. While you can get by in many cases with just your iPhone, sometimes a situation requires a hard copy. In the past, there was really no convenient way for you to get a Reminders list from your iPhone onto paper, but iOS 14.5 changes that.

A surefire way to delight this holiday season is with the latest tech. Gadgets today aren't cheap, but we've got you covered with some useful gear that's perfect for practically everyone — at a price that won't break the bank. If you need a last-minute present, check out the best gadget gifts of 2020, on sale for less than $100.

The two primary design paradigms in Samsung's One UI Android skin are vertical padding and rounded UI elements. The extra empty space at the top of most menus moves touchable elements closer to your thumb, and the rounded UI elements match the curved corners of modern smartphone screens. While you can't add the vertical padding on other Android phones, you can now get the rounded corners.

It's not just iPhones. The entire smartphone market these days has a reputation for being expensive. Many flagship smartphones are advertised at $1,000 minimum. Looking for more storage space, or an extra camera or two? That price continues to rise. However, you don't need to take out a mortgage to buy a quality iPhone. In fact, when it comes to reasonable prices, you have more options than ever.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

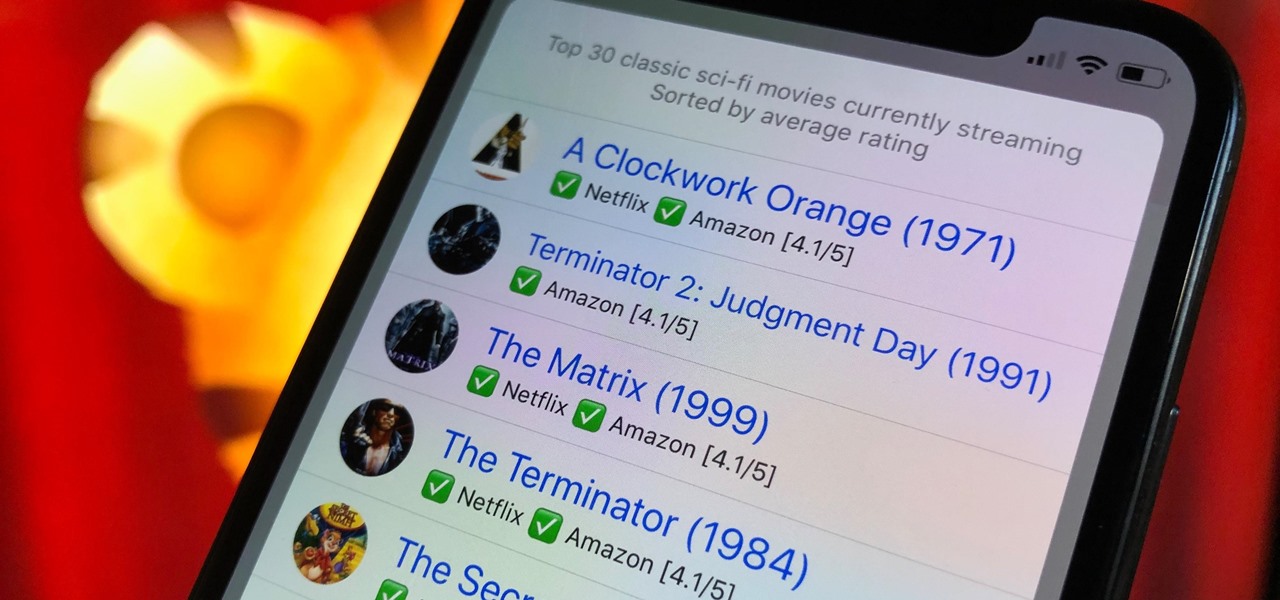
Choosing a movie to watch at home can be incredibly difficult when you don't already have one in mind. But there's a shortcut for your iPhone that can make it easier to browse your streaming media services for something good to play. More specifically, it lets you browse Netflix and Amazon Prime at the same time.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

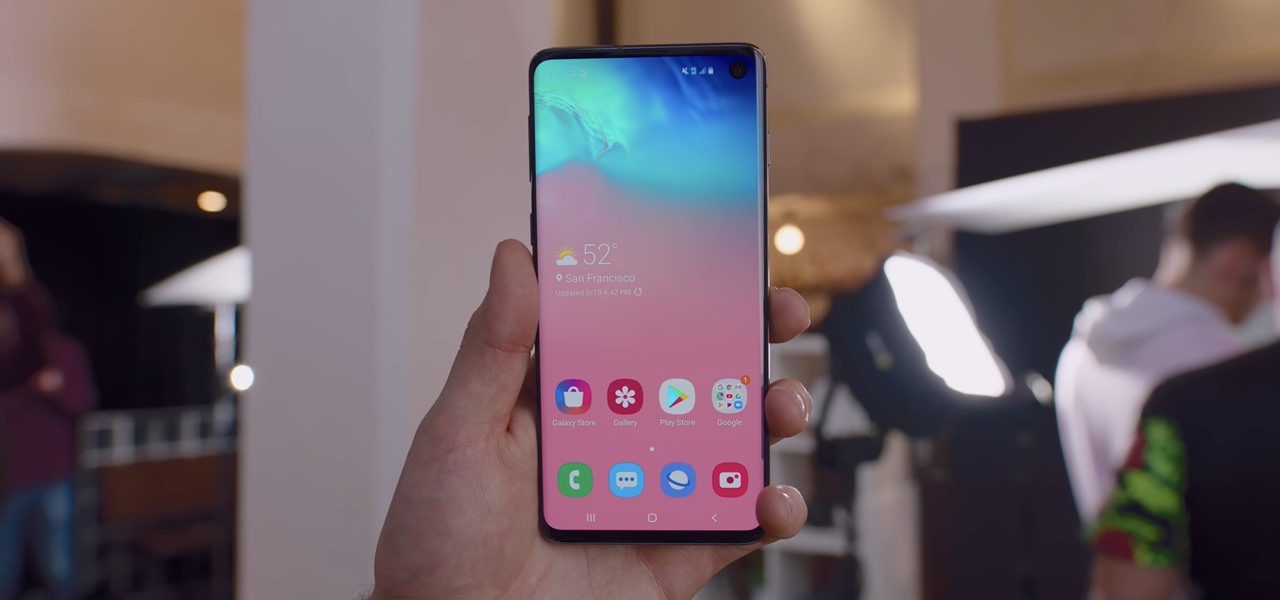
The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we'll be digging into the Create app, the experience that allows you to fill the real world with objects that transform the nature of your local reality.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

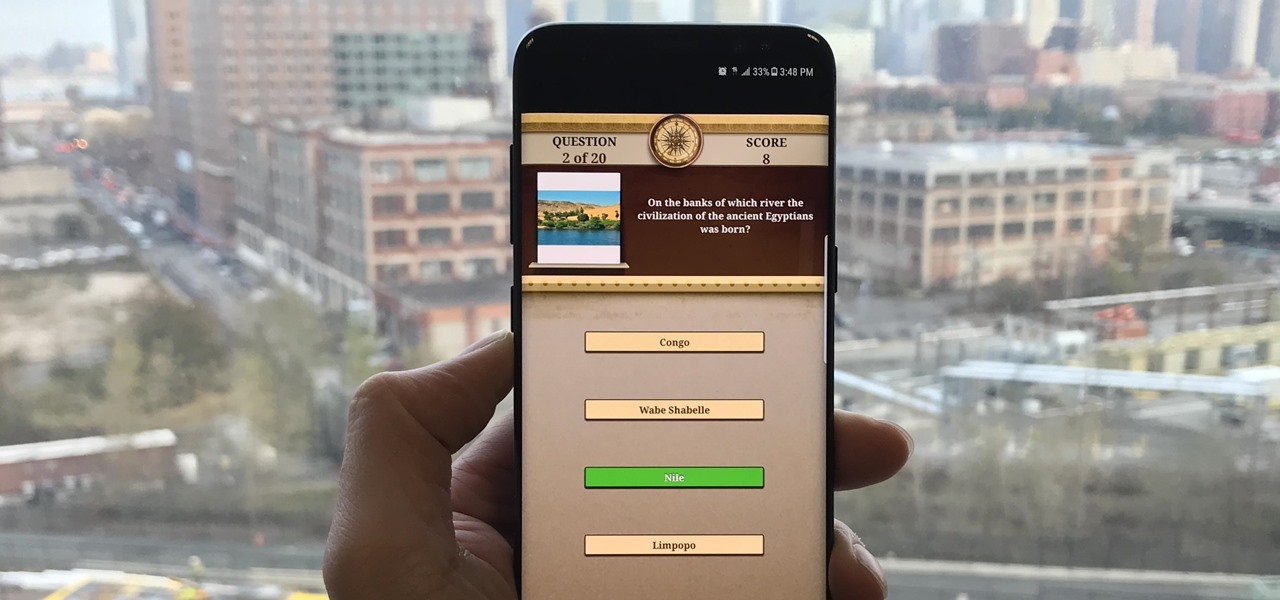
Trivia games are among the most entertaining ways to learn factoids and interesting info you may have never known about before. They're also the perfect genre to enjoy with friends and family, as they're particularly great at breaking the ice to make for a more memorable time together.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Thanks to ever more powerful smartphones — the iPhone X with its advanced A11 processor and the Galaxy Note 8 powered by Snapdragon's 835 come to mind — the mobile industry is fast closing in on consoles and PCs with regards to gaming. Game developers have been aware of this fact, and have ported many games once dedicated to computers onto our handheld devices.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.