The OnePlus 5 doesn't have too many weak spots, at least not when you consider the price. But you might feel that the company with the slogan, "Never Settle," might have actually settled a bit with its camera. The OnePlus 5 and 5T don't have bad imaging specs, but they could use a pick-me-up, which is what we're about to provide. There's a bit of a catch, though.

We already showed you the dark side of augmented reality in the form of a virtual girlfriend from Japan, but now the same country has given us something a lot less creepy that could be the future of virtual pop stars everywhere.
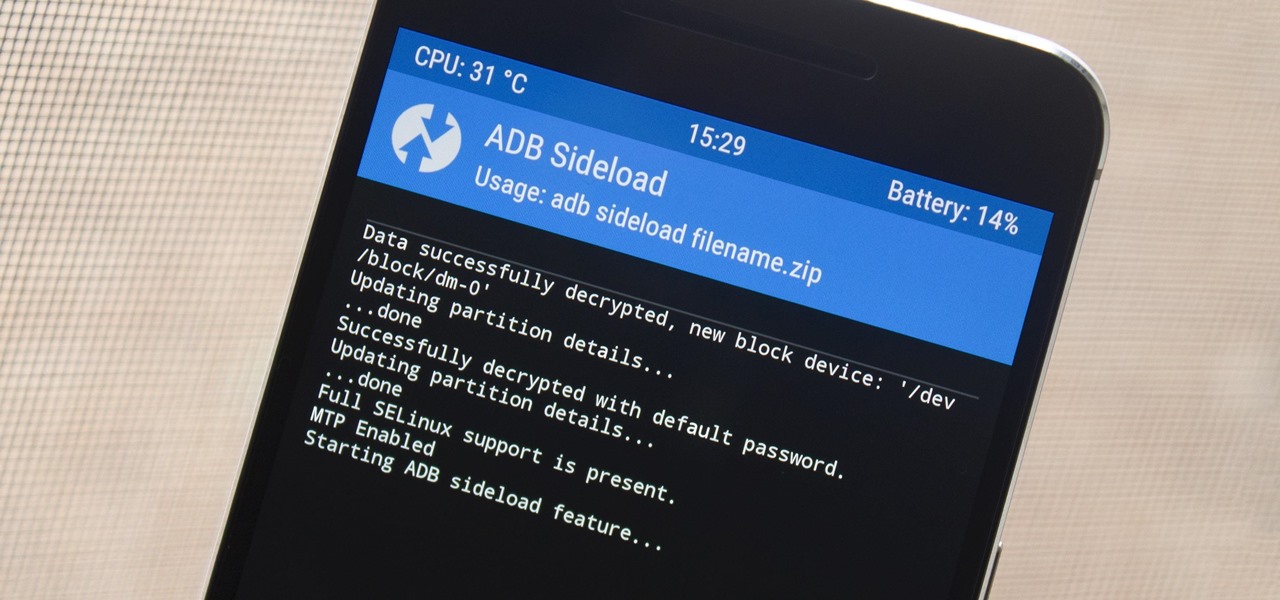
If you're one who likes to tinker with Android, TWRP is the first thing you should install. It replaces your phone's stock recovery mode interface and adds over a dozen advanced features to your device—most notably, the ability to flash ZIPs that can modify practically every aspect of your operating system. It's certainly one of the most powerful tools available for Android, and there's simply nothing capable of replacing it.

Overweight kids often become overweight adults. New research suggests a couple reasons why and suggested that there may be ways to intercept that fate.

The LG V20 is a true audiophile's phone when it comes to playing music through headphones, but it only has a single bottom-firing mono speaker. So even though the V20 has received plenty of praise for its overall audio experience, that single built-in speaker ruins the fun by putting out some shoddy and cheap-sounding audio.

The internet's an amazing place. The entirety of human knowledge is now accessible in an instant, and all sorts of media can be streamed directly to the palm of your hand. But, of course, that also includes the darker side of humanity, so there's plenty of NSFW content floating around out there that's certainly not suitable for children.

Even with today's high-powered devices, battery life is still an issue. We, as users, have to almost habitually check the current battery percentage, because otherwise, we might end up draining too much in the morning, then get stuck with a dead phone at night.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Many of Google's stock Android apps are some of the best options out there—especially now that they've all been made over with Material Design. But generally, as these are pre-installed system apps, they cannot be used on non-Nexus devices.

When it comes to app permissions, Android takes an "all or nothing" approach. You have no granular control over what data apps can access, so the only way to prevent an app from seeing your location or starting up on boot, for instance, is to not install the app in the first place.

Can't stand seeing your Facebook news feed full of peoples' good news and awesome accomplishments? Those oversharing friends are, in a sense, hampering their great news simply by sharing it. If you hold back and keep your accomplishments from friends, you might find even more success than if you'd shared with your support network.

If you've been keeping up with anything Android these days, you've no doubt heard about a little dandy called Xposed Framework kicking around. Xposed, by XDA developer rovo89, is a framework for Android devices that lets you easily modify your stock or custom ROM.

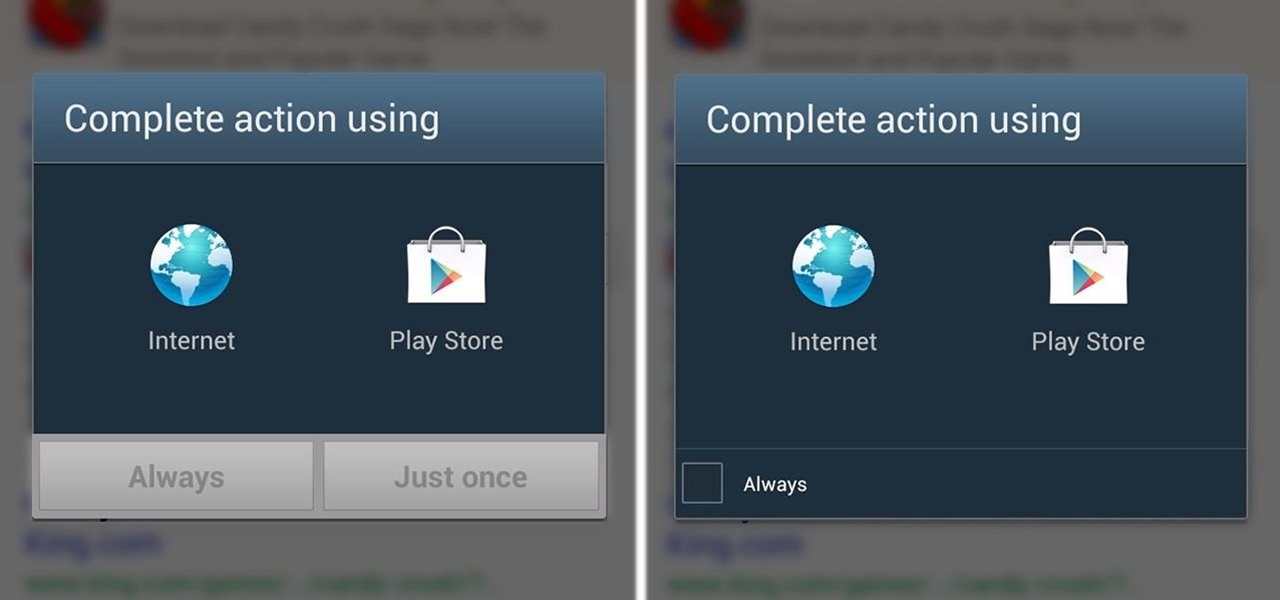
There's two things I'm always looking for in my Samsung Galaxy Note 2. Efficiency and quickness. So, like any other softModder, I tend to download a bunch of apps and tweaks that help speed up my device's overall performance. In doing so, I often come across the "Complete action using" popup, which is oddly enough, one of the most inefficient features ever. You'll see this popup whenever you click on something that can be opened with more than one option. If you click on a link in Google sear...

Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

We've gotten pretty close to a Google Experience before, and even played around with the actual Google Play Edition build. However, the devs over at XDA have a much better solution: actually converting your HTC One into a complete factory-fresh Google Play Edition.

The Google Phone app is one of the best dialers for Android today, especially with all of the unique and exciting features it brings to the table. Unfortunately, without owning a Pixel phone, you are unable to officially download the app, making a modified version your only option. However, this version of Google Phone is missing a few key features, such as spam protection and business search.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

The ongoing war between Apple and Samsung fans will rage on once again. With the release of the iPhone XS Max, Apple has presented a stronger adversary for the Samsung Galaxy Note 9, released earlier. Both stack up well against each other, providing two of the best experiences on their respective operating systems.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

When you hear people say the iPhone "just works," it's because of all the finishing touches Apple adds to iOS. A perfect example of this is the new QR-scanning feature in iOS 12 — by tapping a single button in the iPhone's Control Center, you can scan a QR code within seconds.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

Montezuma's revenge, the runs, the trots, or just diarrhea — everyone gets it sooner or later. What exactly is diarrhea good for, if anything?

A disease called "citrus greening" has devastated and permanently altered citrus production in the United States, but a vaccine that could protect orange trees may be part of a winning strategy to beat the bacteria that is killing the trees.

Potbellies don't have to happen as we age, according to two studies done on twins published online in the International Journal of Obesity.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

KNOX is a major pain for Samsung owners who like to modify their devices. Its combination of hardware and software security measures make things rather difficult when you're trying to modify system-level files and functions without voiding your warranty.

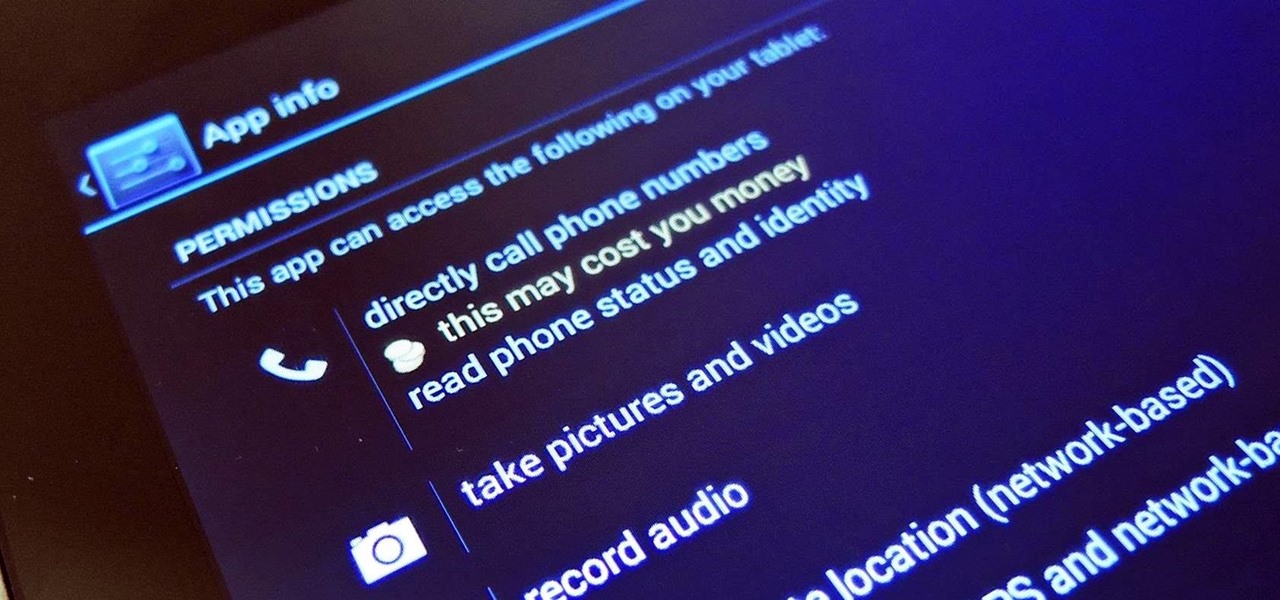
Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

This summer's going to be a hot one, so skip the water pistol this year and break out the big guns! In this project, I'll be showing you how to build a water balloon shotgun—a high-powered water balloon launcher that's capable of firing 17 water balloons at the same time!

Ever since the US Army awarded Microsoft's HoloLens a $480 million contract, the battle for enterprise augmented reality has heated up in earnest.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.