Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

It's become a routine for many of us to ring in the New Year with pledges to finally get our budgets and finances under control. Unfortunately, it's also quite difficult to to keep those promises. Some of us will just dive into our resolutions and wing it as we move forward, which usually ends in failure. But even for those of us who plan carefully, obstacles along the way can spell doom for New Year's resolutions.

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

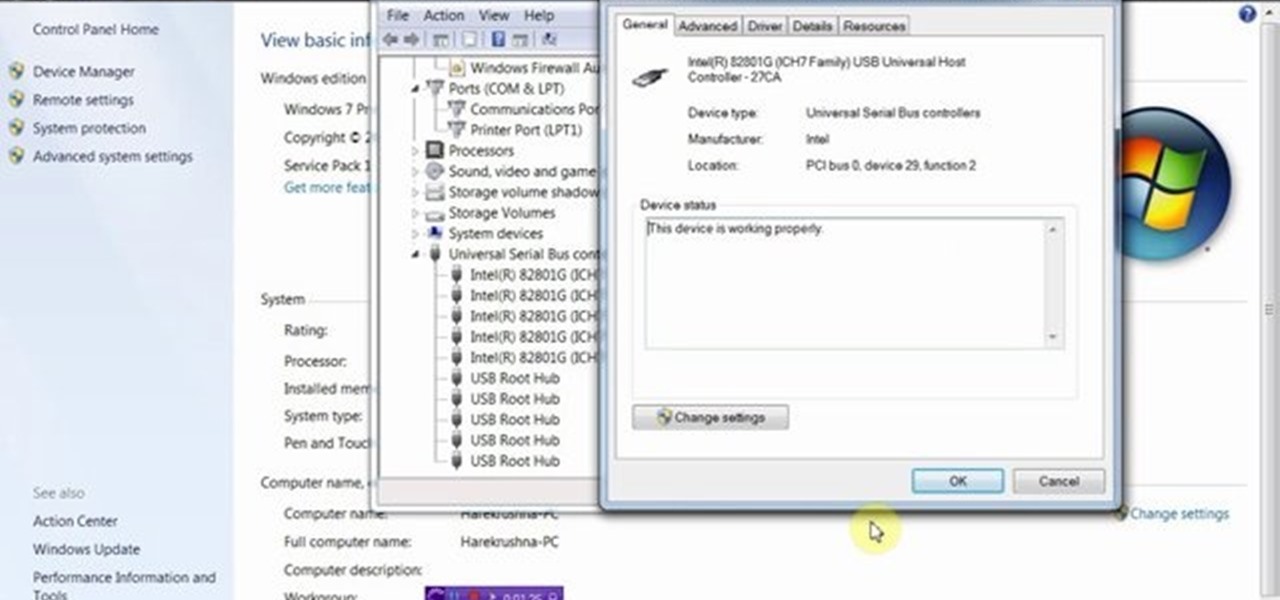
This video will show you how to enable or disable USB port in your PC. If you disable USB port nobody could insert a USB device on your computer and could not copy your data. You could enable the port whenever you needed. Watch the video and follow all the steps.

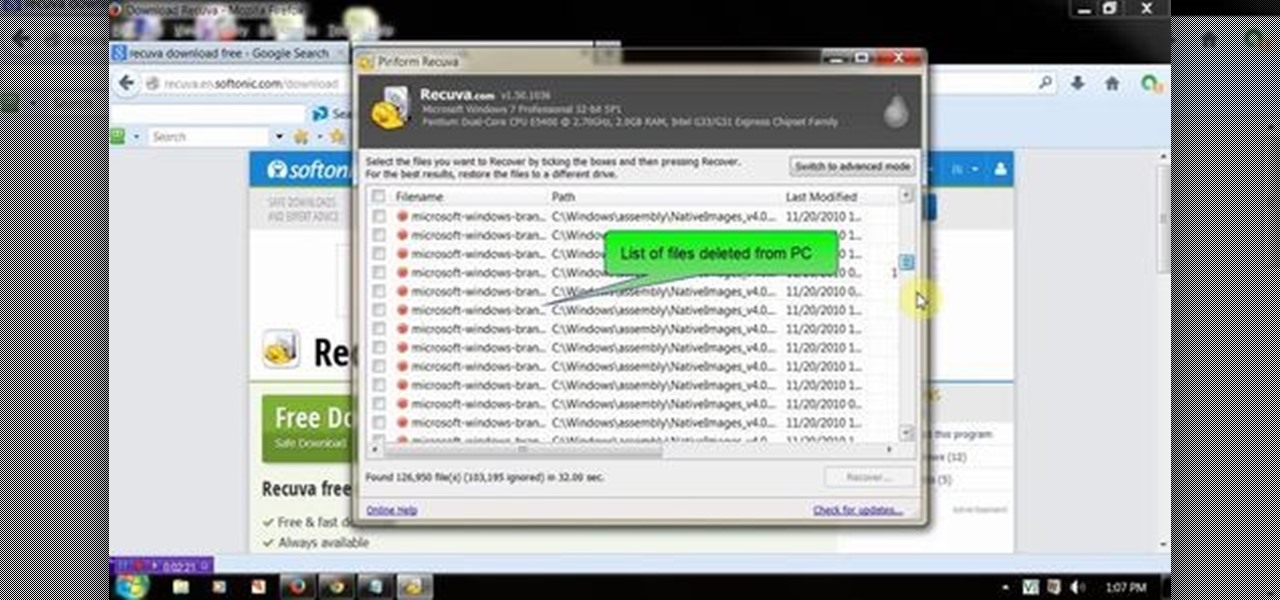
This video will show you how to recover permanently deleted file which you have deleted from recycle bin. But if any new file allocated to those positions then the files could not be recovered with this tool. Watch the video from the installation to execution of the tool to recover deleted data.

This video will provide an idea how to disable or enable the USB port on your PC. By disabling USB port will restrict people from copying your files into USB devices. This is a very effective trick to save your data. Watch the video and follow all the steps.

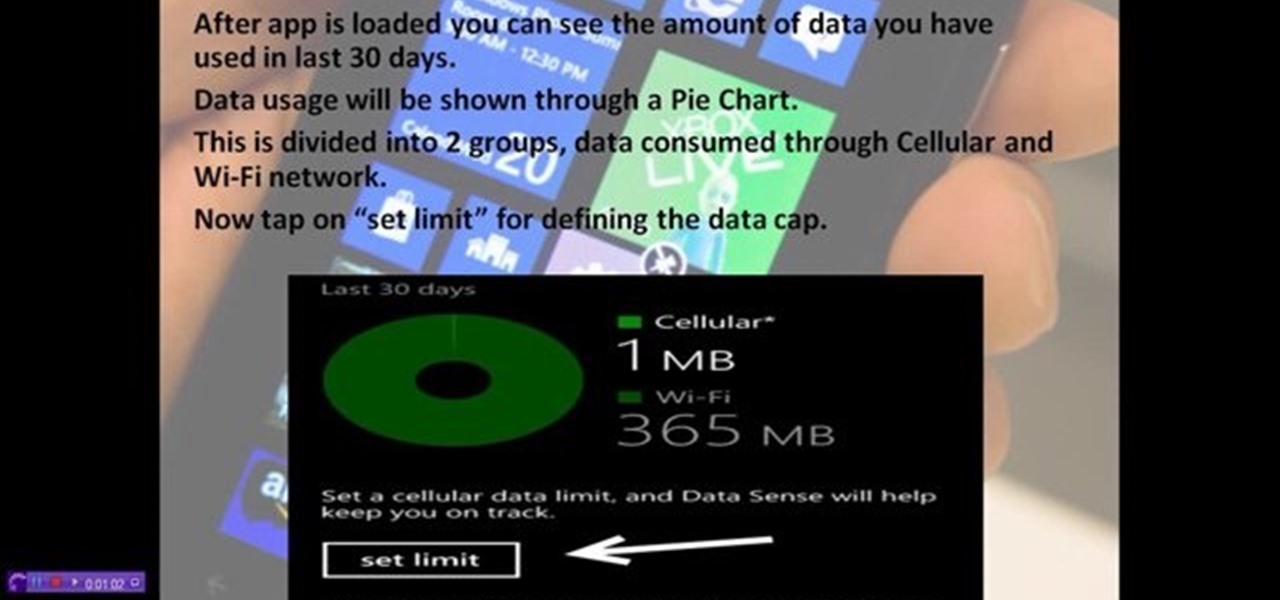
How to control and limit your internet usage in your windows 8 phone? You may want to restrict your internet usage and want to set limit for apps also. If you set your usage limit internet will stop automatically after reaching the limit. Follow the video to employ in your own phone.

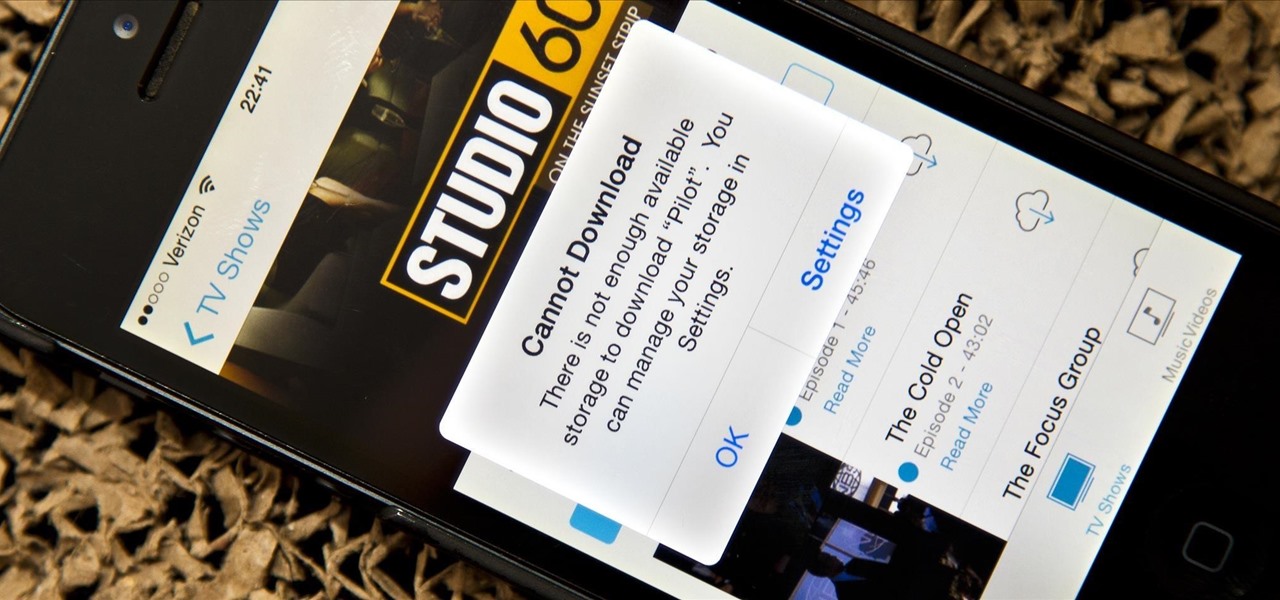
Running out of storage space on your iPhone is annoying, but trying to free some up is downright aggravating. Until they figure out a way to throw a terabyte of flash memory in there, you're going to have to do some spring cleaning every now and then, especially if you're trying to update to iOS 8.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Now that iOS 7 has rolled out to the general public, with an overwhelming fit of mass hysteria, it's only custom for people to start bitching about battery drain—and I don't blame them. I was experiencing some rapid battery drain after first updating my iPhone 5, as well.

Want to breathe some life into your Macbook Pro? Get an SSD! But how to swap your data over? Here's how!

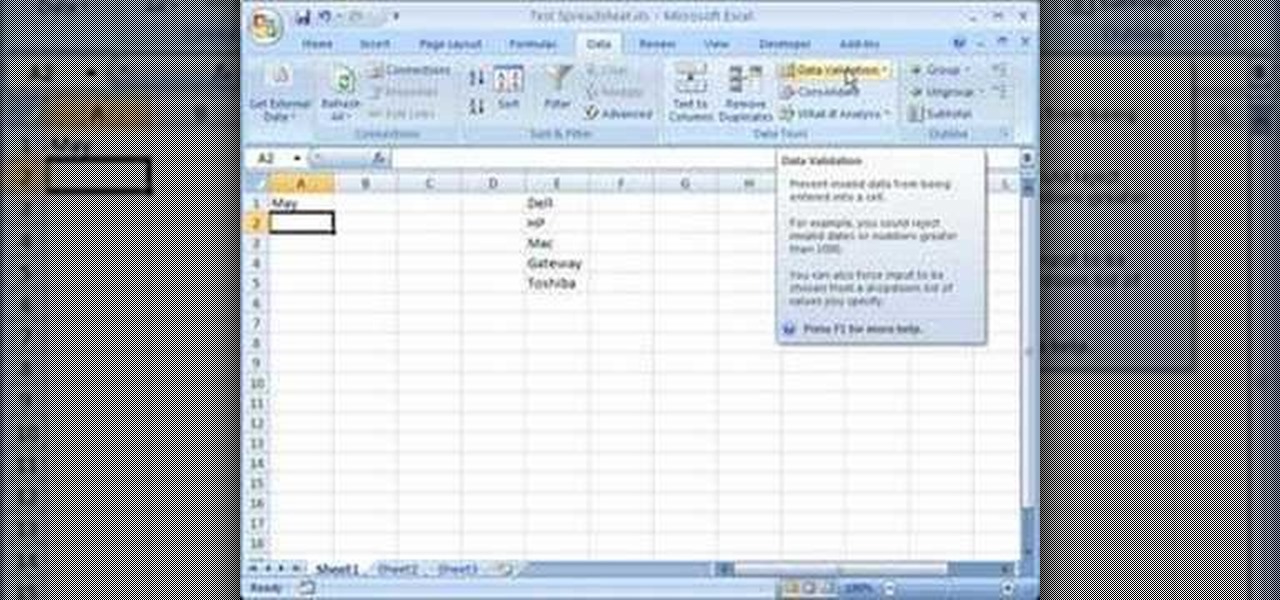
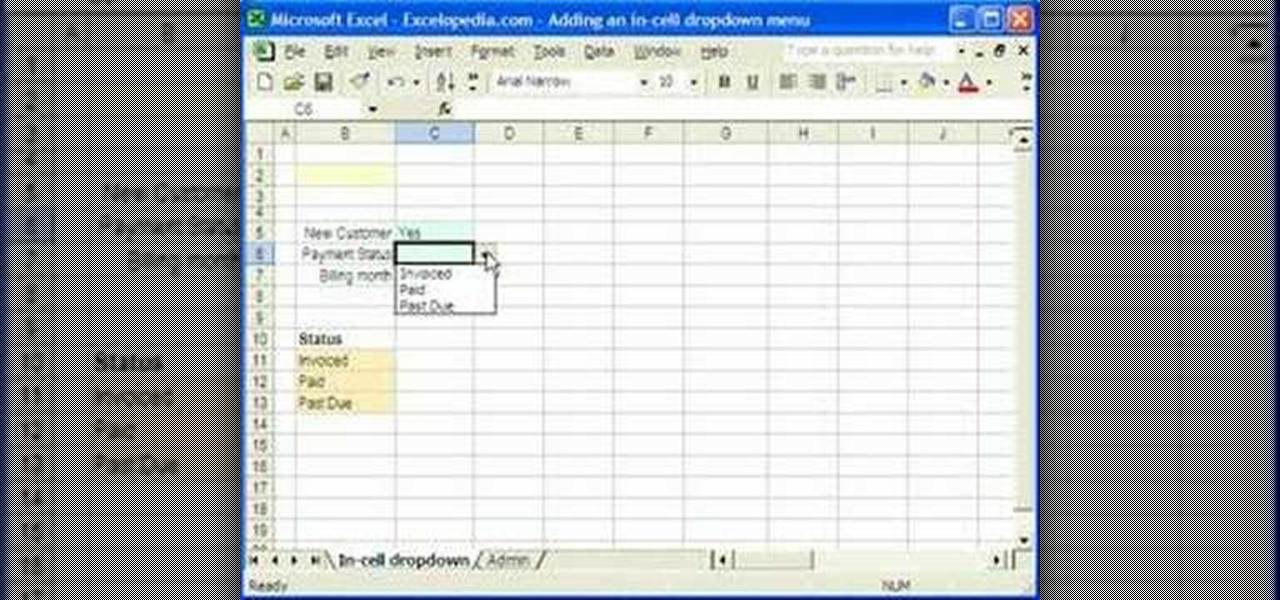
This video is a tutorial on how to create drop-down menus in Excel 2007. Select a cell on your spreadsheet and click on the “Data” tab. Go to the “Data Tools” section and select “Data Validation”. In the window that opens select "Allow" and choose "List". You will create a list of the values you want to allow. Type in the values, separated by commas, and click OK. Now you will see your selected cell has an icon to right that indicates there is a drop-down menu containing the value...

First of all launch the program "Nero 7". Now click on "cd" and then click on "cd-rom boot'. From the new screen choose ' image file' and then click on 'browse'.Now go to the 'drive d' and select 'windowsxp-boot image' folder and then select 'boot.ima' file. Now click on 'open'. Now click on 'advanced' and then click on 'no emulation'. Select the ‘number of loaded sectors' and increase it to '4'. Now click on 'ISO' and then make sure that all the data is same as that on the tutorial.

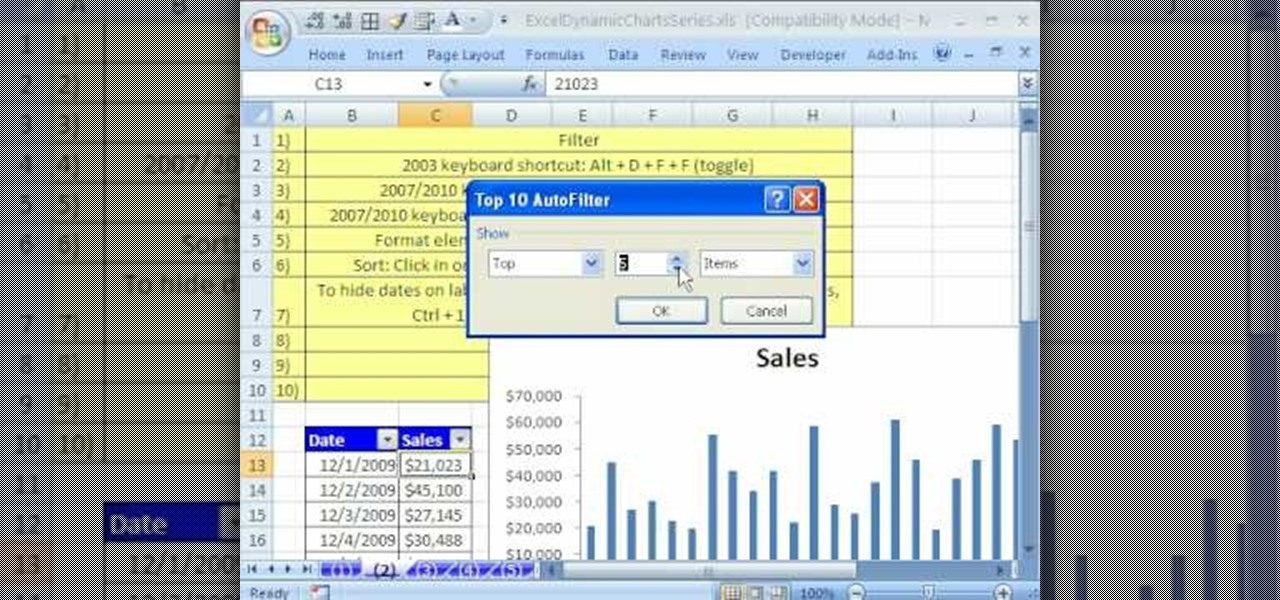
In this Software video tutorial you will learn how to use the filter & sort feature in Excel. First create a column chart on an excel sheet. In this example, it is a date and sales chart. Click alt+F1 and the chart is displayed. Then click and delete the legend and the horizontal lines. Now go back to the data set, click on a cell and click ctrl+shift+L and that will add the auto filter. ctrl+shift+L is for Excel 07. For earlier versions, see the commands listed in the video. This is a toggle...

1. Select the cell for which the dropdown menu is to be applied. 2. once the cell is selected goto DATA menu select VALIDATION.Data validation dialog box will be displayed.

MMS is disabled on some iPhones. To enable it go to settings, and go into the general settings. From the menu select network and select cellular data in the network menu. In the Cellular Data settings go down to MMS options. Now set the APN as wap:voicestream.com, MMSC as http://mms.MSG.eng.t-mobile.com, and MMS Proxy as 216.155.165.50:8080. Once you do these settings go to the message settings and make sure that the MMS messaging is turned on. Now go to messages and create a new message. Add...

In this Know Your PC video the instructors show how to perform a recovery on your computer by demonstrating it on the HP TouchSmart PC. This recovery process will work on any HP desktops, HP Pavilions, Compaq Presarios. Your PC might get corrupted if you recently made any changes to it or installed software that contained viruses and many other reasons. In such cases the best thing to do is perform a system recovery. Recovery will help you take your computer right back to the way it was out o...

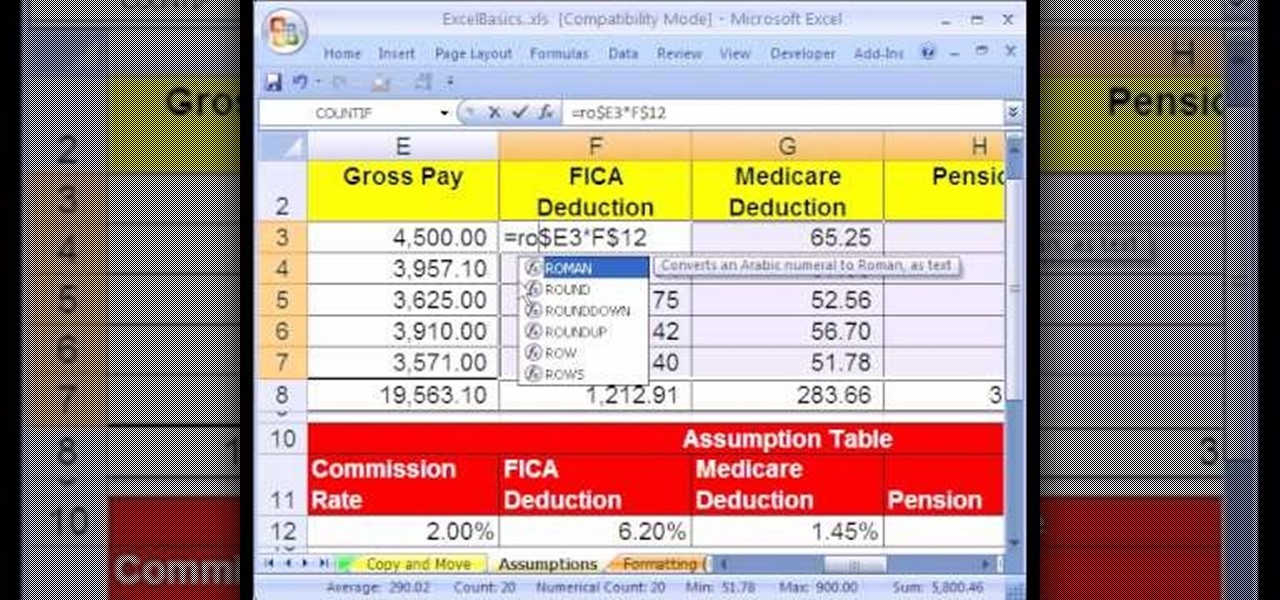
In this video the instructor shows how to use the Round function and also format numbers in Microsoft Excel. Normally while calculating formulas in Excel, the formatting of numbers can get you into a lot of trouble and to get around this problem you need to use the Round function. To do this take some sample data in a Excel work book and apply any formula that you want on the data to arrive at some calculation. Now because of this formatting some times you can arrive at a wrong result as show...

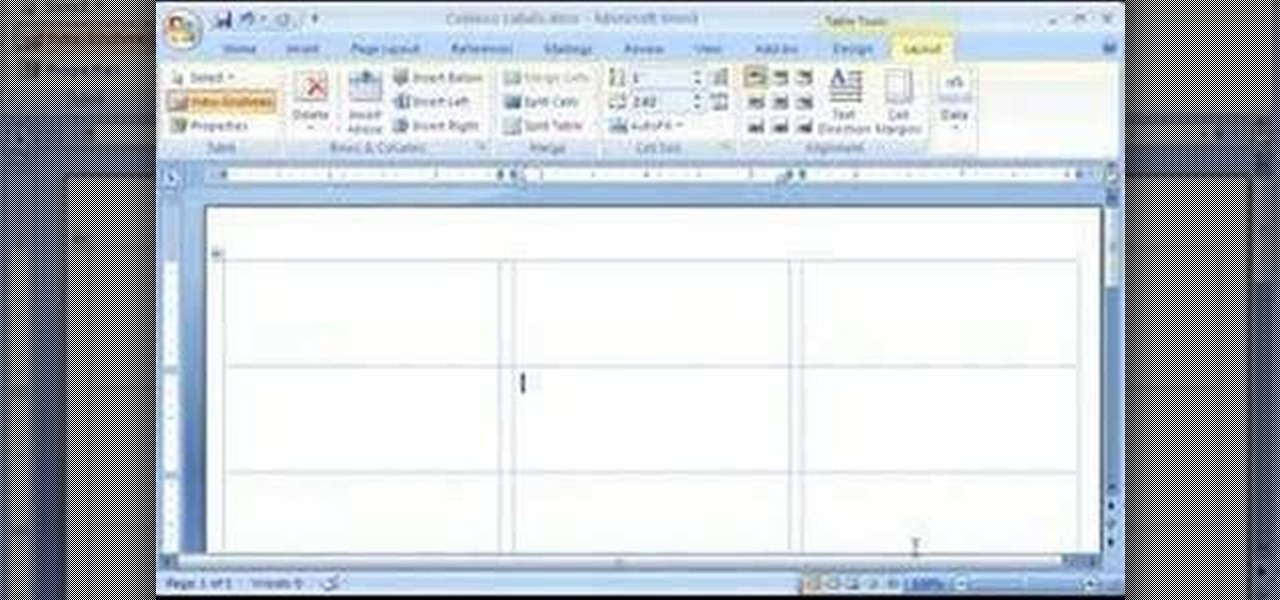
In this first demo of a 4-part series, learn how to set up labels for mass mailings using the Mail Merge feature in Word 2007.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

Sometimes you come across problems and glitches when you're playing FarmVille, FrontierVille, any of your facebook games, or even just using the internet for ordinary purposes! It might just be getting really slow, or you might start losing data or in-game items. As the Zynga customer support article will tell you, you sometimes need to clear you browser and flash cache! Here are some simple steps to do just that!

Losing your important data can be more painful than losing the hardware the data was stored on. Precious memories, files you don't often access but always want to have, there's so much you store on impermanent devices that you can't live without. Backing up your information to a secure, cloud-based location is the best way to stave off disaster here. Polar Backup Unlimited Cloud Backup Storage will give you an unlimited amount of cloud storage while making the process super easy.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

Do you believe you just don't have an intuitive sense of math? Sadly, this is the case for many people. The reality is that math is learned with practice. No one is born with a math gene making them more intuitive than others.

We've become accustomed to new models of learning over the past generation. What once required classrooms and chalkboards now only needs a laptop and an internet connection. At this moment, with much of the population staying inside, eLearning has never been more necessary than now.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

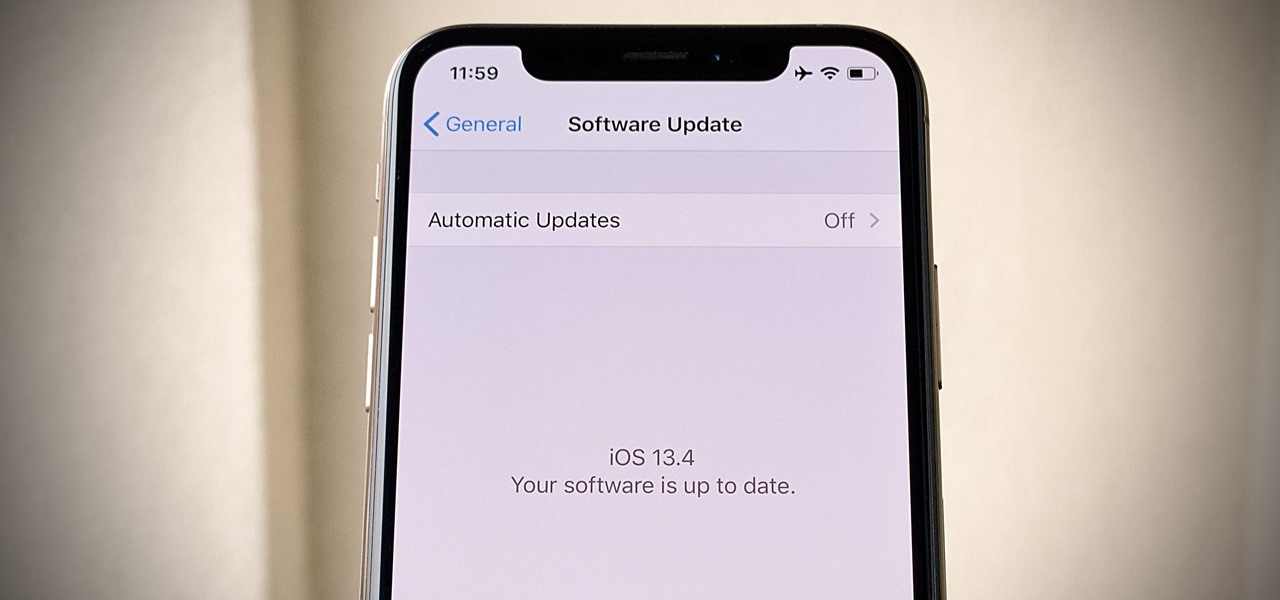
Last week, Apple released the first iOS 13.4 beta with fun and useful new features, such as new Memoji, an upgrade Mail toolbar, and the ability to control your NFC-compatible car via CarKey. To add to that, Apple just released iOS 13.4 developer beta 2, but does the update have any more new changes to be excited about?

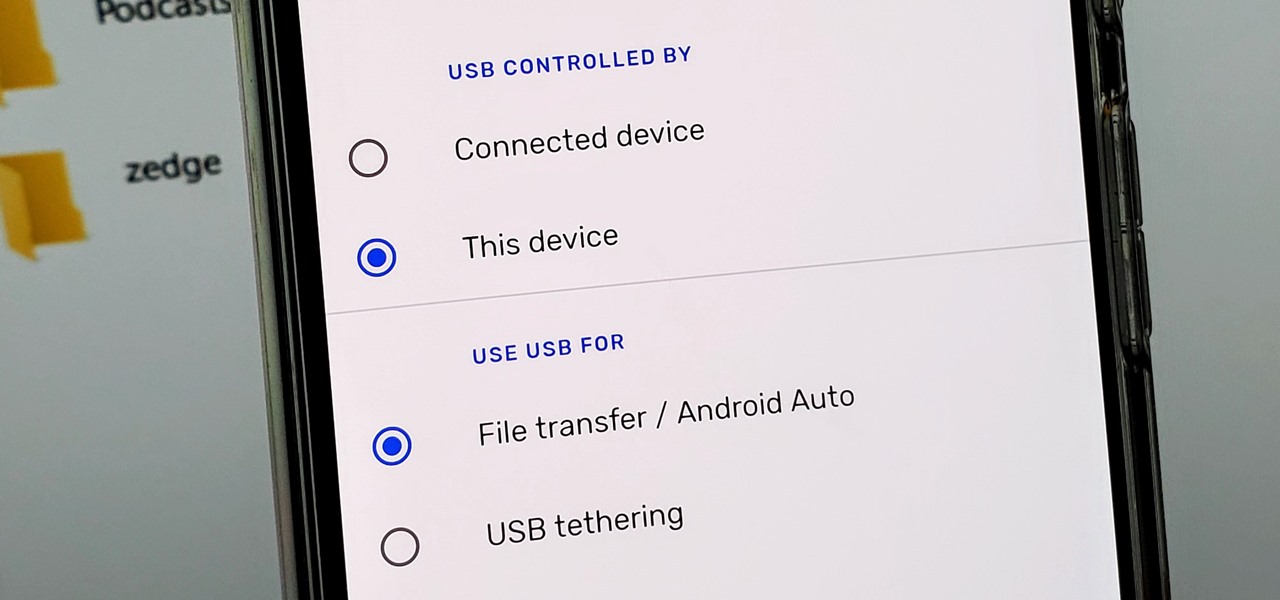
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.