Baidu signed a cooperation agreement on June 7, the first day of the CES Asia conference, with multiple companies in the autonomous vehicles industry. The companies listed in the press release include Desay SV, United Automotive Electronics, and Hangsheng Electronics, as well as possibly additional auto manufacturers. Baidu plans to "jointly develop" upcoming intelligent driving production plans.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

While it remains unknown how exactly augmented reality will make its way into the mainstream (the Microsoft HoloLens sitting at $3,000 isn't exactly accessible), many brands have been trying to integrate the tech into their mobile apps, mimicking the success of Snapchat and its popular AR filters. One of those brands going all in on augmented reality is Shazam.

Headphone drama has been all the rage in the past year, with Apple killing off the headphone jack and trying to force AirPods upon its users (Apple, stop trying to make tiny, expensive, easy-to-lose earbuds happen. It's not going to work).

When it published its 2016-2017 catalog last year, Savannah College of Art and Design (SCAD) became the first college to leverage augmented reality technology for a college catalog.

A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.

Ever since the update that turned Google Keyboard into Gboard rolled out, a lot of people have been noticing that word suggestions and auto-correct features are downright slow. The issue seems to affect users with multiple languages installed more than anyone, though it can also happen if you have a midrange phone or older device with only one language installed.

We've all been there... admit it. You sent a couple messages, but your friend had the "Read Receipts" option turned off in WhatsApp, so after a few minutes, you start wondering if they're away from their phone right now or just flat-out ignoring you.

If you're an Apple user and want an untethered virtual reality system, you're currently stuck with Google Cardboard, which doesn't hold a candle to the room scale VR provided by the HTC Vive (a headset not compatible with Macs, by the way). But spatial computing company Occipital just figured out how to use their Structure Core 3D Sensor to provide room scale VR to any smartphone headset—whether it's for an iPhone or Android.

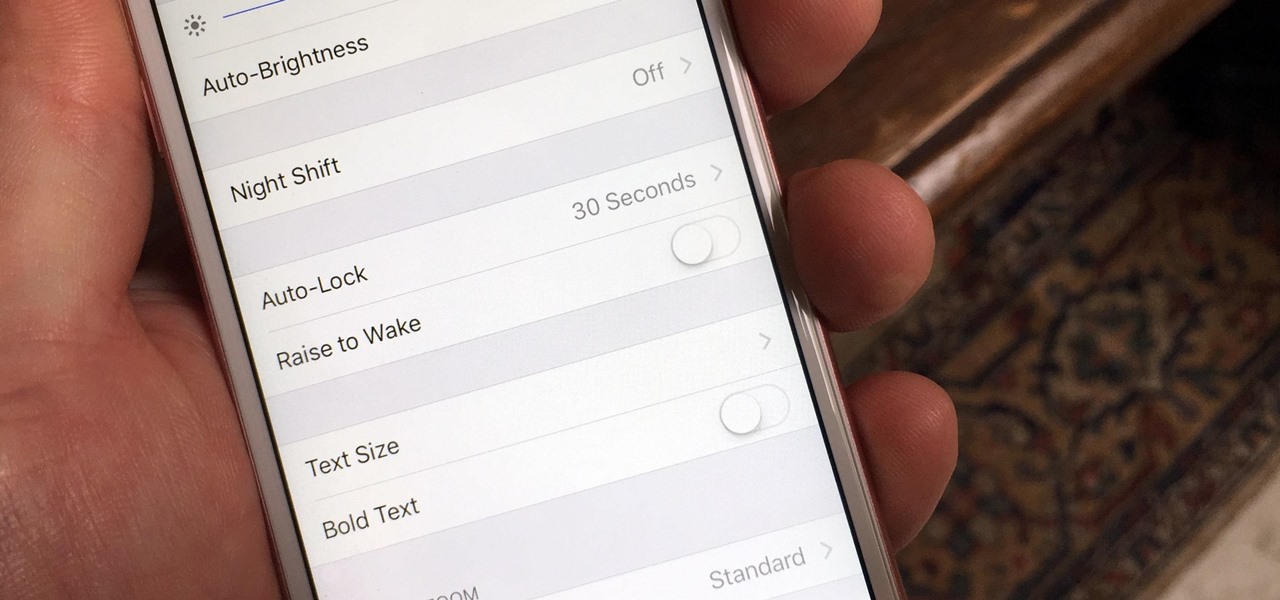
After updating your iPhone to iOS 10, you may have noticed that your screen will wake up whenever you pick up the device to look at it, or even when it's just in your pocket or dangling in your hand.

Apple announced their new iPhones today, and the 7 Plus features two camera lenses on its backside. That could push smartphone photography ahead in a major way. It may also serve as the basis for their foray into virtual, augmented, and mixed reality.

Sure, sites like SeatGuru can show you which seats are the best—but in a 2D graphical form that doesn't really show you what the plane actually looks like inside and out. Aircraft Explorer contains 3D models you can peer inside of to check out what the next plane you catch will actually look like.

The Microsoft HoloLens mixes the digital world with the physical one, allowing you to coexist with holograms of your choosing. But those worlds won't fully blend until we can experience it all together and create for each other. Vuforia could make that possible in the near future.

Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

With most augmented and mixed reality devices, you wear a purchased headset and use it alone, in a place of your choice—but not this one. Ben Sax decided to reinvent the binoculars to create a mixed reality experience that anyone can walk up to and try for free. He calls it the Perceptoscope.

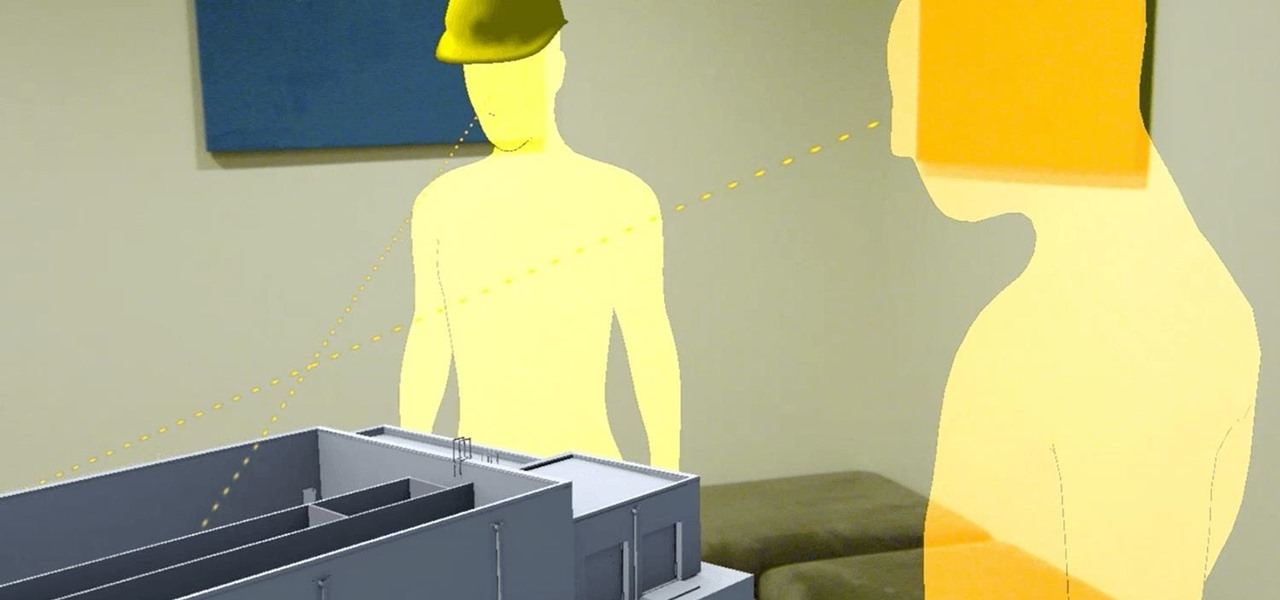
The headsets of tomorrow offer some amazing possibilities in both gaming and work, but what we've seen so far only begins to scratch the surface. The US Navy saw the potential to use augmented reality in a helmet to provide divers with an incredible amount of information we have so far only seen in Hollywood movies.

With developers already figuring out how to use the HoloLens for home improvement tasks, it's no surprise that the device has greater applications in construction. Tech blog Digital Trends points out that holograms are a natural evolution of the blueprint, and several other aspects of construction work.

Speeding tickets suck, and I don't know a single person that can tell me otherwise. But the reality is, most of us will break the speed limit for one reason for another, regardless of the pricey risk.

Google is reportedly working on an iOS keyboard that brings key features to the iPhone, including Google's image and text search functions. (GIFs, yay!) According to The Verge, the keyboard has been in development and testing for months, and will act much like the Android version.

Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

With the DOJ attempting to rip Apple a new one and an Apple attorney firing back, the President offered his opinion on the recent encryption debacle between the FBI and Apple at SXSW, amidst some talk about the direction of today's tech industry.

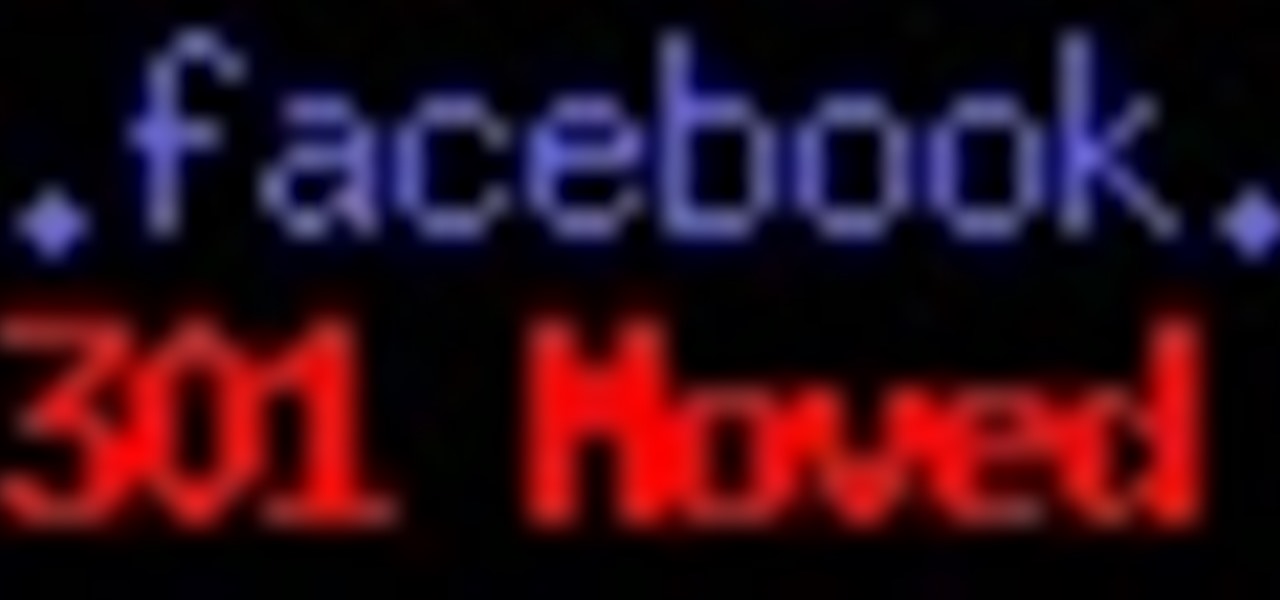
Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

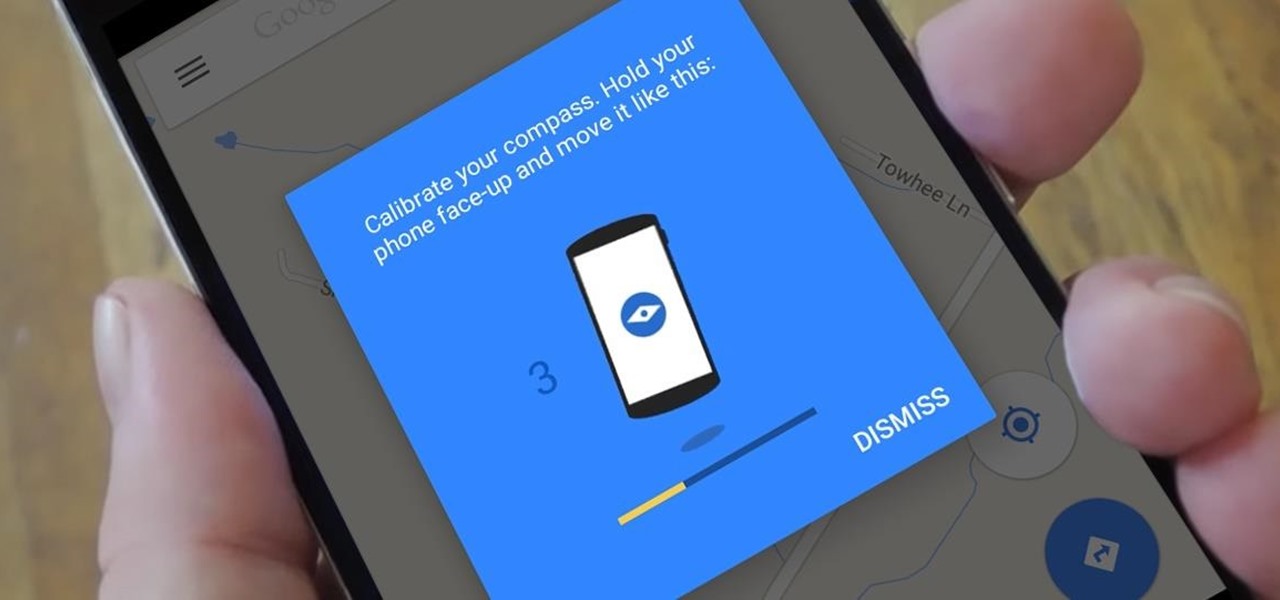
A lot of users with newer Android devices, particularly the Nexus 6P, have been complaining about issues with their device's compass. I've experienced the issue a few times myself—when you open Google Maps and try to get directions somewhere, you're prompted to calibrate your compass before you can proceed.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Taxi drivers and cab companies across the globe are in an uproar over Uber, and for good reason, too—you just can't compete with the low fares and ease of use that Uber brings to the table. The only downside is that the groundbreaking ride share service usually requires a smartphone—but that shouldn't be an issue anymore with one simple tip that I'll outline below.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

Although I am a loyal premium Spotify subscriber, I still regularly use Pandora in hopes of stumbling across new artists and songs. If I'm fortunate enough to come across something I enjoy, it's easy to use the Like feature in Pandora to locate the song later.
Hello Null-Byte community. First off: this my first post here on Null-Byte. Some of you may have already seen me in the comment section, to all others: Hi, I'm the new guy.

As many of you may have heard, Apple's new iOS 9 is "rootless", which supposedly would make jailbreaking much more difficult. However, it has been shown to be possible. ih8sn0w posted a youtube video of his jailbroken iphone running iOS 9 and even gave some hints about it in the video description section. However, he also stated that he will NOT be releasing it to the public. So it would be quite the feat and adventure to take his hints and comments and use that to figure out how to jailbreak...
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

Living in Southern California means I don't really have a need to check the weather all that often. But every now and then, I'm caught off guard by a particularly chilly or hot day—no one wants to be the only person walking around with a T-shirt and sandals on a rainy, 50-degree day.

Upon getting the new Samsung Galaxy S6 Edge here at the office, there are countless things we wanted to do before actually diving in and using the device. One of those things is removing all of the unnecessary pre-installed applications we never asked for.

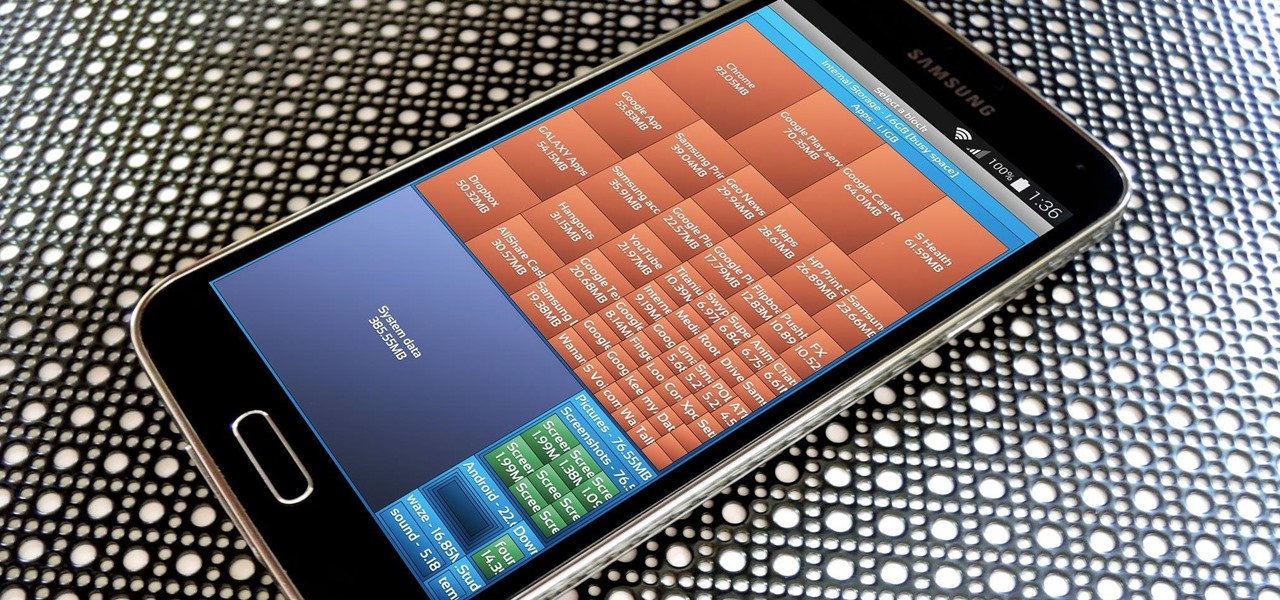
The more we use our smartphones, the more storage space becomes occupied—it's an inescapable fact. But as the data accumulates and chokes off our storage, it can become difficult to identify exactly which files are occupying the most space.

Before heading out on a hike, or any excursion for that matter, it would be wise to take a map with you just in case you get lost while on your quest.

As one of the most frequently used and popular applications available, Facebook is now attempting to be a little more considerate for those Android users that don't have a bleeding-edge device or fast data connections.